Monitoring Gateway Status
Gateway Status
Status updates show for Security Gateways and Software Blades. The status of a gateway is the most serious status of its Software Blades. For example, if all the Software Blades statuses are OK except for the SmartReporter blade, which has a Problem status, then the Overall status will be Problem.
Status Icon
|
Description
|
 OK OK
|
The gateway and all its Software Blades are working properly.
|
 Attention Attention
|
At least one Software Blade has a minor issue, but the gateway works.
|
 Problem Problem
|
At least one Software Blade reported a malfunction, or an enabled Software Blade is not installed.
|
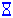 Waiting Waiting
|
SmartView Monitor is waiting for the Security Management Server to send data from Security Gateways.
|
 Disconnected Disconnected
|
Cannot reach the Security Gateway.
|
 Untrusted Untrusted
|
Cannot make Secure Internal Communication between the Security Management Server and the gateway .
|
Displaying Gateway Data
Gateway Status data shows for each Check Point or OPSEC gateway.
To see data about a gateway, click the gateway in the Gateway Results view. Details about the gateway show in the Gateway Details pane.
System Data
- Unified Package - the version number.
- SO Information - the name, the version name/number, the build number, the service pack and any additional information about the Operating System in use.
- CPU - the specific CPU parameters (for example, Idle, User, Kernel and Total) for each CPU.
Note: In the Gateways Results view the Average CPU indicates the average total CPU usage of all existing CPOS. - Memory - the total amount of virtual memory, what percentage of this total is being used. The total amount of real memory, what percentage of this total is being used and the amount of real memory available for use.
- Disk - displays all the disk partitions and their specific details (for example, capacity, used and free).
Note: In the Gateways Results view the percentage/total of free space in the hard disk on which the Firewall is installed. For example, if there are 2 hard drives C and D and the Firewall is on C, the Disk Free percentage represents the free space in C and not D.
Firewall
- Policy information - the name of the Security Policy installed on the gateway and the date and time that this policy was installed.
- Packets - the number of packets accepted, dropped and logged by the gateway.
- UFP Cache performance - the hit ratio percentage as well as the total number of hits handled by the cache, the number of connections inspected by the UFP Server.
- Hash Kernel Memory (the memory status) and ystem Kernel Memory (the OS memory) - the total amount of memory allocated and used. The total amount of memory blocks used. The number of memory allocations, as well as those allocation operations which failed. The number of times that the memory allocation has freed up, or has failed to free up. The NAT Cache, including the total amount of hits and misses.
Virtual Private Networks
VPN is divided into three main statuses:
- Current represents the current number of active output.
- High Watermark represents the maximum number of current output
- Accumulative data which represents the total number of the output.
This includes:
- Active Tunnels - this includes all types of active VPN peers to which there is currently an open IPsec tunnel. This is useful for tracking the proximity to a VPN Net license and the activity level of the VPN gateway. High Watermark includes the maximum number of VPN peers for which there was an open IPsec tunnel since the gateway was restarted.
- RemoteAccess - this includes all types of RemoteAccess VPN users with which there is currently an open IPsec tunnel. This is useful for tracking the activity level and load patterns of VPN gateways serving as a remote access server. High Watermark includes the maximum number of RemoteAccess VPN users with which there was an open IPsec tunnel since the gateway was restarted.
- Tunnels Establishment Negotiation - The current rate of successful Phase I IKE Negotiations (measured in Negotiations per second). This is useful for tracking the activity level and load patterns of a VPN gateway serving as a remote access server. High Watermark includes the highest rate of successful Phase I IKE Negotiations since the Policy was installed (measured in Negotiations per second). In addition, accumulative data includes the total number of successful Phase I IKE negotiations since the Policy was installed.
- Failed - the current failure rate of Phase I IKE Negotiations can be used for troubleshooting, for instance, denial of service, or for a heavy load of VPN remote access connections. High Watermark includes the highest rate of failed Phase I IKE negotiations since the Policy was installed. And finally, Accumulative is the total number of failed Phase I IKE negotiations since the Policy was installed.
- Concurrent - the current number of concurrent IKE negotiations. This is useful for tracking the behavior of VPN connection initiation, especially in large deployments of remote access VPN scenarios. High Watermark includes the maximum number of concurrent IKE negotiations since the Policy was installed.
- Encrypted and Decrypted throughput - the current rate of encrypted/decrypted traffic (measured in Mbps). Encrypted/decrypted throughput is useful (in conjunction with encrypted/decrypted packet rate) for tracking VPN usage and VPN performance of the gateway. High Watermark includes the maximum rate of encrypted/decrypted traffic (measured in Mbps) since the gateway was restarted. And finally, Accumulative includes the total encrypted/decrypted traffic since the gateway was restarted (measured in Mbps).
- Encrypted and Decrypted packets - the current rate of encrypted/decrypted packets (measured in packets per second). Encrypted/decrypted packet rate is useful (in conjunction with encrypted/decrypted throughput) for tracking VPN usage and VPN performance of the gateway. High Watermark includes the maximum rate of encrypted/decrypted packets since the gateway was restarted. And finally, Accumulative, the total number of encrypted packets since the gateway was restarted.
- Encryption and Decryption errors - the current rate at which errors are encountered by the gateway (measured in errors per second). This is useful for troubleshooting VPN connectivity issues. High Watermark includes the maximum rate at which errors are encountered by the gateway (measured in errors per second) since the gateway was restarted. And finally, the total number of errors encountered by the gateway since the gateway was restarted.
- Hardware - the name of the VPN Accelerator Vendor, and the status of the Accelerator. General errors such as the current rate at which VPN Accelerator general errors are encountered by the gateway (measured in errors per second). The High Watermark includes the maximum rate at which VPN Accelerator general errors are encountered by the gateway (measured in errors per second) since the gateway was restarted. And finally the total number of VPN Accelerator general errors encountered by the gateway since it was restarted.
- IP Compression - Compressed/Decompressed packets statistics and errors.
QoS
- Policy information - the name of the QoS Policy and the date and time that it was installed.
- Number of interfaces - the number of interfaces on the Check Point QoS gateway. Information about the interfaces applies to both inbound and outbound traffic. This includes the maximum and average amount of bytes that pass per second, as well as, the total number of conversations, where conversations are active connections and connections that are anticipated as a result of prior inspection. Examples are data connections in FTP, and the "second half" of UDP connections.
- Packet and Byte information, the number of packets and bytes in Check Point QoS queues.
ClusterXL
- The gateway working mode as a cluster member, active or not, and its place in the priority sequence. Working modes are: ClusterXL, Load Sharing, Sync only. Running modes: active, standby, ready and down.
- Interfaces - Interfaces recognized by the gateway. The interface data includes the IP Address and status of the specified interface: if the connection passing through the interface is verified, trusted or shared.
- Problem Notes - Descriptions of the problem notification device such as its status, priority and when the status was last verified.
OPSEC
- The version name/number and build number of the Check Point OPSEC SDK and OPSEC product. The amount of time (in seconds) since the OPSEC gateway has been up and running.
- The OPSEC vendor may add additional fields to their OPSEC Application gateway's details.
Check Point Security Management
- The synchronization status indicates the status of the peer Security Management Servers in relation to that of the selected Security Management Server. This status can be viewed in the Management High Availability Servers window, whether you are connected to the Active or Standby Security Management Server. The possible synchronization statuses are:
- Never been synchronized - immediately after the Secondary Security Management Server has been installed, it has not yet undergone the first manual synchronization that brings it up to date with the Primary Management.
- Synchronized - the peer is properly synchronized and has the same database information and installed Security Policy.
- Advanced - the Security Management Server is more advanced than the standby server, it is more up-to-date.
- Lagging - the Security Management Server has not been synchronized properly.
- Collision - the active Security Management Server and its peer have different installed policies and databases. The administrator must perform manual synchronization and decide which of the Security Management Servers to overwrite.
- Clients - the number of connected clients on the Security Management Server, the name of the SmartConsole, the administrator responsible for administering the SmartConsole, the name of the SmartConsole host, the name of the locked database and the type of SmartConsole application, such as SmartDashboard, User Monitor etc.
UserAuthority WebAccess
- Plug-in Performance - the number of http requests accepted and rejected.
- Policy info - the name of the WebAccess policy and the last time that the policy was updated.
- UAS info - the name of the UA Server host, the IP Address and port number of the UAG Server. The number of requests sent to the UA Server and the time it took for the request to be handled.
- Global UA WebAccess - the number of currently open sessions and the time passed since the last session was opened.
SmartConsole Server
The number of licensed users who are currently connected.
Log Server
Indicates whether or not the Security Management Server is active and the number of licensed users who are currently connected. The Log Server includes elaborate details about the named connected client, including, then name of the administrator, managing the selected Log Server, the host of the Log Server and the name of the database if it is locked. The Log Server also indicates the type of application that can be tracked by the Log Server.
Correlation Unit and SmartEvent
SmartView Monitor reads statuses from the SmartEvent Correlation Unit and SmartEvent server.
Correlation Unit status examples:
- is the SmartEvent Correlation Unit active or inactive
- is the SmartEvent Correlation Unit connected to the SmartEvent server
- is the SmartEvent Correlation Unit connected to the log server
- SmartEvent Correlation Unit and log server connection status
- offline job status
- lack of disk space status
SmartEvent Server status examples:
- last handle event time
- is the SmartEvent Server active or inactive
- a list of correlation units the SmartEvent Server is connected to
- how many events arrived in a specific time period.
The SmartEvent Correlation Unit should be connected to the log server(s) so that it can read logs. It also needs to be connected to the SmartEvent Server so that it can send events to it. If problems occur in the SmartEvent Correlation Unit Unit's connection to other components (for example, SIC problems) the problems are reported in the SmartEvent Correlation Unit Unit's status.
For the same reasons, the SmartEvent server contains statuses that provide information about its connect to all the SmartEvent Correlation Unit Unit(s) that it is currently connected to.
Anti-Virus and URL Filtering
SmartView Monitor can now provide statuses and counters for gateways with Anti-Virus and URL Filtering.
The statuses are divided into the following two categories:
- Current Status
- Update Status (for example, when was the signature update last checked)
Anti-Virus statuses are associated with signature checks and URL Filtering statuses are associated with URLs and categories.
In addition, SmartView Monitor can now run Anti-Virus and URL Filtering counters.
For example:
- Top five attacks in the last hour
- Top 10 attacks since last reset
- Top 10 http attacks in the last hour
- HTTP attacks general info
Multi-Domain Security Management
SmartView Monitor can now be used to monitor Multi-Domain Servers. This information can be viewed in the Gateway Status view. In this view it is now possible to view Multi-Domain Security Management counter information (for example CPU or Overall Status).
Starting and Stopping Cluster Members
To stop and start one member of a cluster from SmartView Monitor:
- Open a view.
- Right-click the cluster member and select > or .
|
|


