

In This Section: |
The Internal Certificate Authority is needed for strong authentication. Authentication for:
The ICA is a Certificate Authority which is an integral part of the Check Point product suite. It is fully compliant with X.509 standards for both certificates and CRLs. See the relevant X.509 and PKI documentation, as well as RFC 2459 standards for more information. You can read more about Check Point and PKI in the R77 VPN Administration Guide.
The ICA is located on the Security Management server. It is created during the installation process, when the Security Management server is configured.
The ICA issues certificates for:
The ICA issues Certificate Revocation Lists (CRLs) in order to publish a list of certificates that have been revoked. This revocation may be due to a number of factors: key compromise, certificate loss, etc. The CRLs are published on an HTTP server running on the Security Management server, and can be retrieved by any Check Point gateway for certificate validation.
ICA operations are performed using the following clients:
cpconfig on the Command Line. Using this tool, the ICA is created and a SIC certificate is issued for the Security Management server.The ICA generates audit logs when ICA operations are performed. These logs can be viewed in the SmartView Tracker.
Each certificate issued by the ICA has a defined validity period. When this validity period is over, the certificate becomes expired.
An administrator can revoke a certificate. This may be done for a number of reasons, for instance, when a user leaves the organization. If a certificate is revoked, the serial number of the certificate is published on the CRL indicating that the certificate has been officially revoked, and cannot be used or recognized by any entity in the system.
Certificates are created in different stages. SIC certificates, VPN certificates for gateways and User certificates are created in one step via SmartDashboard, although the latter can also be created in a two-step process using either SmartDashboard or the ICA Management Tool. If the User certificate is created in two steps, these steps include:
The advantages are:
Enhanced security
Pre-issuance automatic and administrator-initiated certificate removal
If a user does not complete the registration process within a given period of time (which is by default two weeks), the registration code is automatically removed. An administrator can remove the registration key before the user completes the registration process. After that, the administrator can revoke the user certificate.
Explicit or Automatic Renewal of User certificates ensuring continuous User connectivity
A user certificate of type PKCS12 can be renewed explicitly by the user or it can be set to be renewed automatically when it is about to expire. This renewal operation ensures that the user can continuously connect to the organization's network. The administrator can choose when to set the automatic revocation of the old user certificate.
Another added advantage is:
Automatic renewal of SIC certificates ensuring continuous SIC connectivity
SIC certificates are renewed automatically after 75% of the validity time of the certificate has passed. If, for example, the SIC certificate is valid for five years, 3.75 years after it was issued, a new certificate is created and downloaded automatically to the SIC entity. This automatic renewal ensures that the SIC connectivity of the gateway is continuous. The administrator can decide to revoke the old certificate automatically or after a set period of time. By default, the old certificate is revoked one week after the certificate renewal has taken place.
Certificates have these configurable attributes:
Attributes |
Default |
Comments |
|---|---|---|
validity |
5 years |
|
key size |
2048 bits |
For R76 and lower: set to 1024 bits For R77 and higher: set to 2048 bits |
KeyUsage |
5 |
Digital Signature and Key encipherment |
ExtendedKeyUsage |
0 (no KeyUsage) |
VPN certificates only |
To learn more about key size values, see RSA key lengths. If the gateway certificate is stored on a hardware token, configure the key size in the Objects_5_0.C file, using the dbedit utility.
Manage VPN certificates for gateways in the VPN tab of the related network object or in the ICA Management Tool.
VPN certificates have these attributes:
Attributes |
Default |
Configurable |
Comments |
|---|---|---|---|
validity |
5 years |
yes |
|
key size |
2048 bits |
yes |
See: RSA key lengths |
KeyUsage |
5 |
yes |
Digital Signature and Key encipherment |
ExtendedKeyUsage |
0 (no KeyUsage) |
yes |
|
All these attributes can be set in the ICA Management Tool.
|
Note - If the gateway certificate is stored on a hardware token, configure the key size in the |
Internally managed User Certificates can be managed (for example, operations such as initialization, revocation or the removal of registrations can be performed) either from the User Properties window in SmartDashboard or by using the ICA Management Tool.
User Certificates of users who are managed on an LDAP server can only be managed via the ICA Management Tool. User certificates have these attributes:
Attributes |
Default |
Configurable |
Comments |
|---|---|---|---|
validity |
2 years |
yes |
|
key size |
1024 bits |
yes |
Can be set to 2048 or 4096 bits |
DN of User certificates managed by the internal database |
CN=user name, OU=users |
no |
This DN is appended to the DN of the ICA |
DN of User certificates managed on an LDAP server |
|
yes |
Depends on LDAP branch |
KeyUsage |
5 |
yes |
Digital signature and Key encipherment |
ExtendedKeyUsage |
0 (no KeyUsage) |
yes |
|
All the operations in the previous table can be performed via the ICA Management Tool.
If the user completes the registration from the Remote Access machine, the key size can be configured in the Advanced Configuration page in SmartDashboard. This page can be accessed by selecting Policy > Global Properties > SmartDashboard Customization > Advanced. This is the recommended method.
Alternately you can edit the key size using the dbedit utility of the Objects_5_0.C by modifying the size of the key as it is listed in users_certs_key_size Global Property. The new value is downloaded when the user updates his site.
In SmartDashboard or in the dbedit utility:
ica_key_size to one of the following values: 1024, 2048 or 4096.fwm sic_reset.cpconfig and define the CA name in the Certificate Authority tab.cpstart.By default, the CRL is valid for one week. This value can be configured. Fresh CRLs are issued:
It is possible to recreate a specified CRL via the ICA Management Tool. This acts as a recovery mechanism in the event that the CRL is deleted or corrupted. An administrator can download a DER encoded version of the CRL using the ICA Management Tool.
The ICA is able to issue multiple CRLs. The purpose of multiple CRLs is to eliminate any CRL from becoming larger than 10K. If the CRL exceeds 10K, IKE negotiations may fail when trying to establish VPN tunnels.
Multiple CRLs are achieved by attributing every certificate which is issued to a specific CRL. If revoked, the serial number of the certificate appears in this specific CRL.
The CRL Distribution Point (CRLDP) extension of the certificate contains the URL of the specific CRL. This ensures that the correct CRL is retrieved when the certificate is validated.
The ICA is created with a key of size 2048 bits. There are certain cases in which a key of a different size is required (of either 1024 or 4096 bits). In such a case, the ICA must be re-created. This can be done using the command lines and the ICA Configuration file.
The ICA Management Tool is a user-friendly tool that allows an administrator to perform multiple operations on and for the ICA, such as:
|
Note - The ICA Management Tool is supported by SSL version 3 and TLS. |
The Interface is divided into three panes:
The ICA Management Tool is operational from any browser on any platform. Using HTTPS it is possible to connect securely from the ICA Management Tool to the ICA provided that an administrator certificate is added to the browser.
|
Note - The ICA Management Tool can connect to the ICA in clear, however for the sake of security it is recommended to work encrypted in HTTPS. |
The ICA Management Tool can be used to send mail to users to notify them about certificate initialization. In order to send mail notifications, the administrator must configure:
From" address.To' address, which can be used if the users' address is not known. In this case, when the certificates are issued, the administrator can get the mails and forward them to the corresponding address.In order to ease the management of user certificates the ICA Management Tool can perform multiple simultaneous operations. For example, it is possible to:
The following are the types of operations that can be performed simultaneously:
The ICA Management Tool supports administrators with reduced privileges. These administrators can make basic searches and initialize certificates for new users. Multiple concurrent operations cannot be executed by these administrators. These administrators may typically be help desk operators who are charged with the handling of new employees.
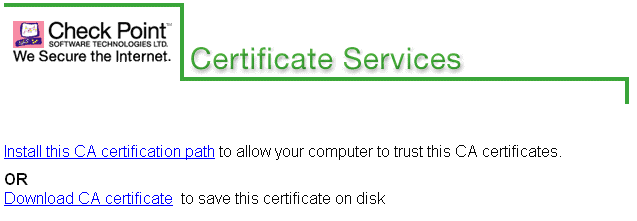
In certain scenarios it is required to obtain the ICA certificate. Peer gateways that are not managed by the Security Management server need to use it for Trust purposes. Also, clients using Clientless VPN, as well as the machine on which the ICA Management Tool is run, require this certificate. In this case, these peers are requested to proceed as follows:
http://<smart_dns_name>:18264)The Certificate Services window is displayed.
SIC certificates are managed using SmartConsole.
VPN certificates are managed in the VPN page of the corresponding network object. These certificates are issued automatically when the IPSec VPN blade is defined for the Check Point gateway or host. This definition is specified in the General Properties window of the corresponding network object.
If a VPN certificate is revoked, a new one is issued automatically.
The user certificates of users that are managed on the internal database are managed using SmartConsole. For more information, see User Certificates in the R77 VPN Administration Guide.
The ICA Management Tool is disabled by default, and can be enabled via the command line.
Usage
cpca_client [-d] set_mgmt_tool on|off [-p <ca_port>] [-no_ssl] [-a|-u "administrator|user DN" ... ]
where:
on means to start the ICA Management Tool (by opening port 18265)off means to stop the ICA Management Tool (by closing port 18265)-p changes the port used to connect to the CA (if the default port is not being used)-no_ssl configures the server to use clear HTTP rather than HTTPS-a "administrator DN" ... - sets the DNs of the administrators that will be allowed to use the ICA Management Tool-u "user DN" ... - sets the DNs of the users that will be allowed to use the ICA Management Tool. This option is intended for administrators with limited privileges.
|
Note - If |
Open the browser and type the location: https://<Management_Host_Name>:18265
You will be requested to authenticate.
|
Note - The ICA Management Tool should not be on the same subnet as the Security Management server. |
This is performed in the Create Certificates - Operations Pane.
There are two search options, a basic search that includes only the user name, type, status and serial number fields, as well as an advanced search that includes all the search fields. The second option can only be performed by administrators with unlimited privileges.
This search includes all of the attributes described for the Basic Search, as well as the following:
The results of the search are displayed in the Search Results pane. This pane consists of a table with a list of searched certificate attributes such as:
Search statistics will be displayed in the status bar after every search is performed.
Click on the DN link in the Search Results pane in order to display certificate details.
Certificate operations (such as certificate creation) when done via the ICA Management Tool can only be used for user certificates.
|
Important - SIC certificates and VPN certificates should not be modified using the ICA Management Tool, but via SmartDashboard. |
Check the certificates on which you would like to perform the operations.
There are three methods of submitting certificates:
To initiate a certificate, proceed as follows:
To generate a certificate, proceed as follows:
To create a PKCS#10 certificate, proceed as follows:
Bulk certificate initialization can be done as follows:
The format of the file initiated by the LDAP search is as follows:
mail=" the string after contains the mail of that user. When no email is given the email address will be taken from the ICA's "Management Tool Mail To Address" attribute.not_after then the value at the next line is the Certificate Expiration Date in seconds from now. otp_validity then the value at the next line is the Registration Key Expiration Date in seconds from now.Example of Output of an LDAP Search
|
For more information, see User Directory.
It is possible to create a simple (non-LDAP) query by configuring the DN + email in a file in the following format:
|
In the Menu pane, select Manage CRL and:
On the Manage CRLs page, select Clean the CA's Database and CRLs from expired certificates. This operation gets rid of all expired certificates. Before performing this operation, make sure that the time set on the Security Management server is accurate.
In the Menu pane, select Configure the CA. The Configure the CA - Operations pane displays all the configurable fields of the CA. There are three possible operations that can be performed:
Entering the string Default in one of the attributes will also reset it to the default after pressing Configure. Values that are valid will be changed as requested and others will change to default values.
Edit the CA data by modifying the values displayed in the Configure the CA - Operations Pane. The CA data types can be any of the following:
<number> days <number> seconds. For example: CRL Duration: 7 days 0 seconds.When changing the attribute, it can be entered as <number> days <number> seconds or just as a single number of seconds.
The following attributes are listed in alphabetical order:
Attribute |
Comment |
Values |
Default |
|---|---|---|---|
Authorization Code Length |
The number of characters of the authorization codes. |
min-6 max-12 |
6 |
CRL Duration |
The period of time for which the CRL is valid. |
min-5 minutes max-1 year |
1 week |
Enable Renewal |
For User certificates. This is a Boolean value setting which stipulates whether to enable renewal or not. |
true or false |
true |
Grace Period Before Revocation |
The amount of time the old certificate will remain in Renewed (superseded) state. |
min-0 max-5 years |
1 week |
Grace Period Check Period |
The amount of time between sequential checks of the Renewed (superseded) list in order to revoke those whose duration has passed. |
min-10 minutes max-1 week |
1 day |
IKE Certificate Validity Period |
The amount of time an IKE certificate will be valid. |
min-10 minutes max-20 years |
5 years |
IKE Certificate Extended Key Usage |
Certificate purposes for describing the type of the extended key usage for IKE certificates. Refer to RFC 2459. |
|
means no KeyUsage |
IKE Certificate Key usage |
Certificate purposes for describing the certificate operations. Refer to RFC 2459. |
|
Digital signature and Key encipherment |
Management Tool DN prefix |
Determines the DN prefix of a DN that will be created when entering a user name. |
possible values CN= UID= |
CN= |
Management Tool DN suffix |
Determines the DN suffix of a DN that will be created when entering a user name. |
|
ou=users |
Management Tool Hide Mail Button |
For security reasons the mail sending button after displaying a single certificate can be hidden. |
true or false |
false |
Management Tool Mail Server |
The SMTP server that will be used in order to send registration code mails. It has no default and must be configured in order for the mail sending option to work. |
|
- |
Management Tool Registration Key Validity Period |
The amount of time a registration code is valid when initiated using the Management Tool. |
min-10 minutes max-2 months |
2 weeks |
Management Tool User Certificate Validity Period |
The amount of time that a user certificate is valid when initiated using the Management Tool. |
min-one week max-20 years |
2 years |
Management Tool Mail From Address |
When sending mails this is the email address that will appear in the from field. A report of the mail delivery status will be sent to this address. |
|
- |
Management Tool Mail Subject |
The email subject field. |
|
- |
Management Tool Mail Text Format |
The text that appears in the body of the message. 3 variables can be used in addition to the text:
|
|
Registration Key:
|
Management Tool Mail To address |
When the send mail option is used, the emails to users that have no email address defined will be sent to this address. |
|
- |
Max Certificates Per Distribution Point |
The maximum capacity of a CRL in the new CRL mode. |
min-3 max-400 |
400 |
New CRL Mode |
A Boolean value describing the CRL mode. |
0 for old CRL mode 1 for new mode |
true |
Number of certificates per search page |
The number of certificates that will be displayed in each page of the search window. |
min-1 max-approx 700 |
approx 700 |
Number of Digits for Serial Number |
The number of digits of certificate serial numbers. |
min-5 max-10 |
5 |
Revoke renewed certificates |
This flag determines whether to revoke an old certificate after it has been renewed. The reason for not revoking this is to prevent the CRL from growing each time a certificate is renewed. If the certificate is not revoked the user may have two valid certificates. |
true or false |
true |
SIC Key Size |
The key size in bits of keys used in SIC. |
possible values: 1024 2048 4096 |
1024 |
SIC Certificate Key usage |
Certificate purposes for describing the certificate operations. Refer to RFC 2459. |
|
Digital signature and Key encipherment |
SIC Certificate Validity Period |
The amount of time a SIC certificate will be valid. |
min-10 minutes max-20 years |
5 years |
User Certificate Extended Key Usage |
Certificate purposes for describing the type of the extended key usage for User certificates. Refer to RFC 2459. |
|
means no KeyUsage |
User Certificate Key Size |
The key size in bits of the user's certificates. |
Possible values are 1024 2048 4096 |
1024 |
User Certificate Key usage |
Certificate purposes for describing the certificate operations. Refer to RFC 2459 |
|
Digital signature and Key encipherment
|