
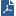

The following sections explain how to maintain the DLP gateway and captured files.
To use the DLP Portal and UserCheck, users must be allowed to access the DLP gateway. By default, users can only access the DLP gateway through its internal interfaces, but not through its external interfaces.
You can configure user access to the DLP gateway in SmartDashboard in the Accessibility section of the Data Loss Prevention page of the DLP gateway object. The options are:
|
Note - We do not recommend that you use "Through all interfaces" when the DLP gateway is deployed at the perimeter. |
This is the default option. This option is recommended to prevent unauthorized access to the DLP gateway from the external gateway interfaces. To make this option meaningful, make sure the topology of the internal and external interfaces of the DLP gateway are correctly defined.
Feature |
Service |
TCP Port |
|---|---|---|
DLP Portal |
TCP HTTP |
80 |
TCP HTTPS |
443 |
|
UserCheck |
TCP |
18300 |
TCP HTTPS |
443 |
|
Reply-to-email |
TCP HTTPS |
25 |
For example, to allow access from remote sites and/or remote users to the DLP gateway, add rules that allow access to the UserCheck service (port 18300) and HTTPS (port 443) from those VPN Communities to the DLP gateway. You can also define the source IP address from which SMTP communication is allowed. This would normally be the mail server that receives emails from users.
A dedicated DLP gateway enforces a predefined, fixed Internal firewall policy. This policy gives users access to the DLP gateway for the UserCheck services: DLP Portal, UserCheck, and SMTP. The policy is made up of implied rules.
The Internal Firewall Policy on a dedicated DLP gateway is not related to the Data Loss Prevention (DLP) Policy that is defined by the administrator in the Policy page of the Data Loss Prevention tab of SmartDashboard. It is also not related to the Firewall Policy which is explicitly defined by the administrator in the Firewall tab of SmartDashboard.
If you do an Install Policy:
|
Important - A dedicated DLP gateway does not enforce the Firewall Policy, Stateful Inspection, anti-spoofing or NAT. Check Point recommends that you place it behind a protecting Security Gateway or firewall. |
The Internal Firewall Policy lets users access these services and ports (and no others) on the DLP gateway:
Feature |
Service |
TCP Port |
|---|---|---|
DLP Portal |
TCP HTTP |
80 |
TCP HTTPS |
443 |
|
UserCheck |
TCP |
18300 |
TCP HTTPS |
443 |
|
WebUI |
TCP |
4434 |
Reply-to-email |
SMTP |
25 |
Secure Shell |
SSH |
22 |
ICMP |
ICMP requests |
|
You can change the time to expire for unhandled UserCheck incidents. This is done in the DLP configuration files. You must make sure that the expiration of incidents is greater than the expiration time for learning user actions, to ensure that you do not nullify the feature that learns user actions.
To change expiration time:
|
The default value is 604800
thread_cachingbackend
|
The value of backend:expiration:quarantine, backend:thread_caching:cache_expiration_in_days
By default, incident data is held in the gateway for 21 days after the incident actually expired. This extra time enables you to retrieve data for users who were on vacation, for example. You can change the removal interval.
backend:expiration:db
|
The DLP quota check ensures that users are not overloading the file system with unhandled UserCheck incidents. If a user has so many captured emails, or emails with large attachments, that the quota per user is exceeded, DLP handles the issue.
The email quota threshold has two values - minimum and maximum. If a user exceeds the maximum email quota, DLP deletes older emails until the user's file system folder size is lower than the minimum quota threshold.
To change quota behavior:
|
user_quota_active The remaining options are relevant only if user_quota_active=1
quota_size_per_user user_quota_upper_limituser_quota_lower_limitThis quota check ensures that users are not overloading the file system with unhandled UserCheck incidents using FTP or HTTP transmissions. If a user has so many captured HTTP posts, or large FTP upload attempts, that the quota per user is exceeded, DLP handles the issue.
To change quota behavior:
The default value is 85
When disk usage is greater than this value, incidents are not saved.
If you decrease this value, it is recommended that you decrease the age of FTP and HTTP incidents before deletion, to ensure that you have enough disk space to save incidents:
$FWDIR/conf/mail_security_config file > dlp_delete_redundant_files_age_group1_files
You can enable or disable email notifications that are sent to users when their captured DLP incidents or incident data are deleted from the gateway.
Notifications are especially important if incidents and data are deleted because of exceeding quota (may occur if the user's email storage exceeds the user-allowed limit), because:
On the other hand, if a user gets a notification that an incident expired because it wasn't handled in time, you can still retrieve the data of the incident (if needed). DLP deletes the data of expired incidents a number of days after the data expired.
You can decide which DLP automatic actions fire notifications in GuiDBedit. GuiDBedit, also known as the Check Point Database Tool, enables you to change Check Point configuration files in a GUI.
To activate or de-activate user notifications of DLP deletion:
C:\Program Files\CheckPoint\SmartConsole\R77\PROGRAM\GuiDBedit.exe This parameter determines the types of emails that are to be sent for exceeding quotas and for expiration of incidents.
If UserCheck incidents are not expiring, or the change in value of the quarantine parameter seems to have no effect, verify that expiration is enabled.
To enable expiration of UserCheck incidents:
|
The default value is 10
The /var/spool/mail directory may become full. This may occur if you de-activate the settings to delete incident data after expiration or on exceeding quota. It may also occur due to regular usage, depending on your environment. The quota for the DLP data to be held on the mail server is set in the configuration files.
DLP routinely checks the usage on the Mail Server /var/spool/mail directory against the DLP global_quota_percentage parameter. If usage on the Mail Server exceeds the global quota: no more emails are stored; all emails of UserCheck incidents are passed; and SmartView Tracker logs are issued.
To change the quota use percentage:
|
The default value is 80 (% of Mail Server used).
To change DLP behavior if global quota is exceeded:
|
block_on_engine_error (0)block_on_engine_error (1)
|
Important - For security and performance, it is recommended that you leave the Mail Server quota activated. However, if you do need to de-activate it, set the |
The complete data of UserCheck incidents are held in quarantine on the DLP gateway. Thus, if an email is caught, and it contains a large attachment, it takes up the required space on the gateway until the incident is handled or expires.
The DLP gateway automatically cleans itself of expired incident data. Incident data that is held for the backend:expiration:db
To change how often and when the gateway checks for data to delete:
|
expiration_intervalexpiration_execution_timeDLP automatically cleans its gateway periodically of temporary files, to make sure that disk use does not unduly build over time. But sometimes unnecessary files are left on the disk.
You can customize the cleanup with these configuration files:
$FWDIR/conf/mail_security_config$DLPDIR/config/dlp_cleanup_files_list.conf
|
Important - It is not recommended to de-activate the cleanup. If you must do so, set the value of |
mail_security_config Parameters |
Description |
dlp_delete_redundant_files_interval |
How often (in minutes) cleanup runs. Default = 1440 (24 hours) |
dlp_delete_redundant_files_execution_time |
Exact time (on 24 hour clock) when cleanup runs. Default = 4:45 (when gateway load is low) |
dlp_delete_redundant_files_age_group1_files |
Minimum age of UserCheck data files, which should be maintained on the disk until their handling expiration arrives. Default = 0 (use the expiration_time_in_days value) Note: This value does not change the expiration of incidents; it changes when data of expired incidents is removed. |
dlp_delete_redundant_files_age_group2_files |
Minimum age of files in /proc Default = 15 minutes |
dlp_delete_redundant_files_age_group3_files |
Minimum age of files in $FWDIR/tmp/dlp Default = 15 minutes |
The dlp_cleanup_files_list.conf file is a list of scan commands with the following syntax:
scan CHECK_DB -
|
Description |
CHECK_DB |
Tests files to see if they are in the DLP database, to prevent accidental deletion of UserCheck incident data: To clean up everything, even user captured data, change the flag to a dash ( - ): |
path |
Path to look for files to delete. May include shortcuts such as $DLPDIR or $FWDIR, but cannot contain spaces. |
mask |
Regular expressions for files to match: * = all files Default masks used include: |
scale |
Unit of measure for age parameter: |
age |
Minimal time since creation the file must have before it can be deleted |
|
Note - Contents of this file explain more options, such as how to use macros for file age. It is recommended that you read the file comments before changing anything here. |
The default age values of scan commands in the file are macros that pull values from mail_security_config. You can use numeric values instead of macros.
age Macros |
Description |
$2 |
group1 age (in days): UserCheck data files, value taken from |
$3 |
group2 age (in minutes): /proc files, value taken from |
$4 |
group3 age (in minutes): /tmp/dlp files, value taken from |
These procedures explain how to customize backend files to change the text of user-related notifications.
It is also possible to localize the files to a language other than US English.
To customize the DLP notification emails:
File |
Purpose |
|---|---|
dictionary_en_us.conf |
Basic dictionary |
about_to_expire_notification_tmplt_en_us.html |
Email notifications |
data_owners_mail_notification_tmplt_en_us.html |
|
detect_mail_notification_tmplt_en_us.html |
|
expired_owners_mail_tmplt_en_us.html |
|
expired_sender_mail_tmplt_en_us.html |
|
failure_mail_notification_en_us.html |
|
prevent_mail_notification_tmplt_en_us.html |
|
quarantine_mail_notification_tmplt_en_us.html |
|
quota_deleted_notification_tmplt_en_us.html |
|
released_mail_notification_tmplt_en_us.html |
To customize the UserCheck DLP notifications (Available from R71.10 DLP):
You can customize UserCheck notifications by editing files. For example, to edit the notification in the screenshot, you edit quarantine_smtp_uc_notification_tmplt_en_us.html
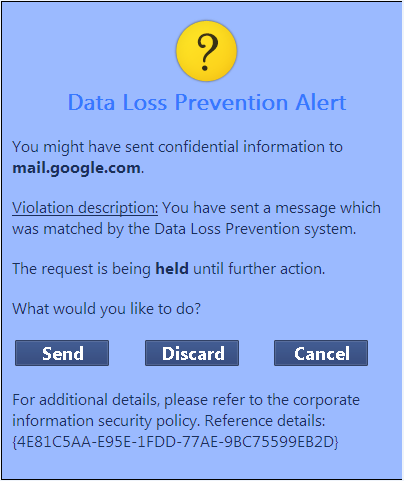
$DLPDIR/backend/confFile |
Purpose |
|---|---|
inform_ftp_uc_notification_tmplt_en_us.html |
ftp protocol when the action is inform |
inform_http_uc_notification_tmplt_en_us.html |
http protocol when the action is inform |
inform_smtp_uc_notification_tmplt_en_us.html |
smtp protocol when the action is inform |
prevent_ftp_uc_notification_tmplt_en_us.html |
ftp protocol when the action is prevent |
prevent_http_uc_notification_tmplt_en_us.html |
http protocol when the action is prevent |
prevent_smtp_uc_notification_tmplt_en_us.html |
smtp protocol when the action is prevent |
quarantine_ftp_uc_notification_tmplt_en_us.html |
ftp protocol when the action is ask |
quarantine_http_uc_notification_tmplt_en_us.html |
http protocol when the action is ask |
quarantine_smtp_uc_notification_tmplt_en_us.html |
smtp protocol when the action is ask |
To customize the DLP Portal:
|
Note - Never change the key as it may be used in more than one place, and a call for a missing key may result in runtime error. You should only change the textual content. Use these rules:
|
cpstop cpstart To customize notification text in SmartDashboard:
|
Important - Changes in the files will be lost when you upgrade to the next version. We recommend you maintain a copy of the all changes files, to overwrite upgraded files. |
You can localize the text of all user-related notifications to a language other than US English.
Change notification text in email, UserCheck, and portal backend files, and in SmartDashboard to the same language.
|
Note - DLP can detect Data Types in all languages |
By default, DLP supports LDAP users with English-language ASCII encoding only.
To support LDAP servers with UTF-8 user records:
trueYou can configure two options for extreme conditions in SmartDashboard that determine when to prefer connectivity:
These options are configured in SmartDashboard in the Data Loss Prevention tab > Additional Settings > Advanced > Extreme Conditions section.
Default values for extreme conditions exist in the GuiDBedit application. With GuiDBedit you can edit the default values for parameters related to extreme conditions (see fields below).
To edit Extreme Condition field values:
C:\Program Files\CheckPoint\SmartConsole\R77\PROGRAM\GuiDBedit.exe Field Name |
Description |
Default Value |
|---|---|---|
|
Threshold for stopping inspection on heavy load. When CPU load is more than the defined threshold, DLP bypasses the protocols set to True. |
90% |
|
Threshold for resuming inspection after the |
70% |
|
By default, DLP bypasses FTP traffic on heavy load. If you change this to false, FTP is inspected on heavy load. |
true |
|
By default, DLP bypasses HTTP traffic on heavy load. If you change this to false, HTTP is inspected on heavy load. |
true |
|
By default, DLP inspects SMTP traffic on heavy load. If you change this to true, SMTP is bypassed on heavy load. |
false |
Field Name |
Description |
Default Value |
|---|---|---|
|
The maximum number of files (attachments) in an FTP/HTTP/SMTP message. |
100 |
|
The maximum size in MB of an FTP/HTTP/SMTP message. |
150 |
|
How many recursion levels deep can be done for archived messages. |
6 |
|
Note - It is possible to either prefer connectivity or security upon cluster failover. You can set this in Gateway Cluster Properties > IPS > Upon Cluster Failover. |
You can edit default values for parameters related to the Exchange Security Agent in the GuiDBedit application.
To edit Exchange Security Agent values:
C:\Program Files\CheckPoint\SmartConsole\R77\PROGRAM\GuiDBedit.exe Field Name |
Description |
Default Value |
|---|---|---|
|
The Exchange Security Agent sends messages to the Security Gateway but does not wait for a response from the Security Gateway. For all rules with the detect or inform action, the Exchange Security Agent is automatically configured to work in tap mode. For other rules, the default is to not work in tap mode. If you want the system to always work in tap mode, change the value from false to true. |
False |
|
If to scan SMTP messages from a domain that is not in the organization's Exchange. By default this value is false. This means that it will only scan messages from your organization's Exchange. To scan messages from senders outside of the domain, change the value to true. |
False |
|
If to scan internal traffic.
|
True |
|
If to scan messages sent outside of the organization. |
True |
|
Scans messages received by the Exchange server in SMTP. This means that messages in SMTP arriving from the same domain will be scanned. |
False |
Field Name |
Description |
Default Value |
|---|---|---|
|
The time interval that the Exchange Security Agent sends statuses to the Security Gateway. |
10 |
|
If to send logs about messages that are not sent to the gateway because of the Inspection Scope settings. |
False |
Field Name |
Description |
Default Value |
|---|---|---|
|
The Exchange Security Agent sends traffic to the Security Gateway encrypted in TLS. |
True |
You can configure inspection of HTTP transmissions on all ports (standard HTTP ports 80, 8080, and other non-standard ports you might have configured).
To enable HTTP inspection on all ports:
|
Note - When you set HTTP inspection on all ports there is a performance impact. |
You can define a Data Type based on a file type with the "File Attributes" Data Type. This Data Type offers several file type families.
To add a new file type to the File Data Type options:
ID |
File Type |
ID |
File Type |
||
|---|---|---|---|---|---|
1 |
Word for DOS 4.x |
2 |
Word for DOS 5.x |
||
3 |
Wordstar 5.0 |
4 |
Wordstar 4.0 |
||
5 |
Wordstar 2000 |
6 |
WordPerfect 5.0 |
||
7 |
MultiMate 3.6 |
8 |
MultiMate Advantage 2 |
||
9 |
IBM DCA/RFT |
10 |
IBM DisplayWrite 2 or 3 |
||
11 |
SmartWare II |
12 |
Samna |
||
13 |
PFS: Write A |
14 |
PFS: Write B |
||
15 |
Professional Write 1 |
16 |
Professional Write 2 |
||
17 |
IBM Writing Assistant |
18 |
First Choice WP |
||
19 |
WordMarc |
20 |
Navy DIF |
||
21 |
Volkswriter |
22 |
DEC DX 3.0 and below |
||
23 |
Sprint |
24 |
WordPerfect 4.2 |
||
25 |
Total Word |
26 |
Wang IWP |
||
27 |
Wordstar 5.5 |
28 |
Wang WPS |
||
29 |
Rich Text Format (RTF) |
30 |
Mac Word 3.0 |
||
31 |
Mac Word 4.0 |
32 |
Mass 11 |
||
33 |
MacWrite II |
34 |
XyWrite / Nota Bene |
||
35 |
IBM DCA/FFT |
36 |
Mac WordPerfect 1.x |
||
37 |
IBM DisplayWrite 4 |
38 |
Mass 11 |
||
39 |
WordPerfect 5.1/5.2 |
40 |
MultiMate 4.0 |
||
41 |
Q&A Write |
42 |
MultiMate Note |
||
43 |
PC File 5.0 Doc |
44 |
Lotus Manuscript 1.0 |
||
45 |
Lotus Manuscript 2.0 |
46 |
Enable WP 3.0 |
||
47 |
Windows Write |
48 |
Microsoft Works 1.0 |
||
49 |
Microsoft Works 2.0 |
50 |
Wordstar 6.0 |
||
51 |
OfficeWriter |
52 |
Mac Word 4.x Complex |
||
53 |
IBM DisplayWrite 5 |
54 |
Word for Windows 1.x |
||
55 |
Word for Windows 1.x complex |
56 |
Ami |
||
57 |
Ami Pro |
58 |
First Choice 3 WP |
||
59 |
Mac WordPerfect 2.0 |
60 |
Mac Works 2.0 WP |
||
61 |
Professional Write Plus |
62 |
Legacy |
||
63 |
Signature |
64 |
Wordstar for Windows |
||
65 |
Word for Windows 2.0 |
66 |
JustWrite 1.0 |
||
67 |
Wordstar 7.0 |
68 |
Windows Works WP |
||
69 |
JustWrite 2.0 |
70 |
Ami [Clip] |
||
71 |
Legacy [Clip] |
72 |
Pro Write Plus [Clip] |
||
73 |
Mac Word 5.x |
74 |
Enable WP 4.x |
||
75 |
WordPerfect 6.0 |
76 |
Word for DOS 6.x |
||
77 |
DEC DX 3.1 |
78 |
WordPerfect Encrypted |
||
79 |
Q&A Write 3 |
80 |
Mac WordPerfect 3.0 |
||
81 |
CEO Word |
82 |
Word 6.0 or 7.0 |
||
83 |
WordPerfect 5.1 Far East |
84 |
Ichitaro 3.x |
||
85 |
Ichitaro 4.x/5.x/6.x |
86 |
Word for Windows 1.2 J |
||
87 |
Word for Windows 5.0 J |
88 |
Matsu 4 |
||
89 |
Matsu 5 |
90 |
P1 Japan |
||
91 |
Rich Text Format Japan |
92 |
CEO Write |
||
93 |
Windows Works 3.0 WP |
94 |
Microsoft WordPad |
||
95 |
WP/Novell Unknown Format |
96 |
Word for Windows 2.0 Object |
||
97 |
WordPerfect 6.1 - 12.0 / X3 |
98 |
Fulcrum Document Format |
||
99 |
Europa Fulcrum 5 |
100 |
Europa Fulcrum 6 |
||
101 |
Internet HTML |
102 |
Word 7.0 |
||
103 |
Arehangeul |
104 |
Hana |
||
105 |
Windows Works 4.0 WP |
106 |
PerfectWorks for Windows |
||
107 |
WordPerfect 7.0/8.0/10.0 |
108 |
WordPro 96 |
||
109 |
HTML - Central European |
110 |
HTML - Japanese (ShiftJIS) |
||
111 |
HTML - Japanese (EUC) |
112 |
HTML - Chinese (Big5) |
||
113 |
HTML - Chinese (EUC) |
114 |
HTML - Chinese (GB) |
||
115 |
HTML - Korean (Hangul) |
116 |
HTML - Cyrillic (ANSI 1251) |
||
117 |
HTML - Cyrillic (KOI8-R) |
118 |
Text - Cyrillic (ANSI 1251) |
||
119 |
Cyrillic (KOI8-R) |
120 |
WWRITE - Japan SJIS |
||
121 |
WWRITE - Chinese GB |
122 |
WWRITE - Hangul |
||
123 |
WWRITE - Chinese BIG5 |
124 |
Digital WPS Plus |
||
125 |
Mac Word 6 |
126 |
Microsoft Word 97/98 |
||
127 |
Rainbow |
128 |
Interleaf 6 |
||
129 |
MIFF 3.0 |
130 |
MIFF 4.0 |
||
131 |
MIFF 5.0 |
132 |
Text Mail |
||
133 |
Mac Word 97 |
134 |
Interleaf Japan |
||
135 |
MIFF 3.0 Japan |
136 |
MIFF 4.0 Japan |
||
137 |
MIFF 5.0 Japan |
138 |
MIFF 5.5 |
||
139 |
WordPerfect 8.0/10.0 |
140 |
Ichitaro 8.x/9.x/10.x/11.x/12.x/13.x/2004 |
||
141 |
vCard |
142 |
HTML - Cascading Style Sheets |
||
143 |
MS Outlook |
144 |
Pocket Word |
||
145 |
WordPro 97/Millennium |
146 |
Microsoft Word 2000 |
||
147 |
Word 2000 HTML |
148 |
Excel 2000 HTML |
||
149 |
PowerPoint 2000 HTML |
150 |
Extensible Markup Language (XML) |
||
151 |
Wireless Markup Language (WML) |
152 |
WMLB |
||
153 |
HTML - Japanese (JIS) |
154 |
WML - Chinese (Big5) |
||
155 |
WML - Chinese (EUC) |
156 |
WML - Chinese (GB) |
||
157 |
WML - Cyrillic (ANSI 1251) |
158 |
WML - Cyrillic (KOI8-R) |
||
159 |
WML - Japanese (JIS) |
160 |
WML - Japanese (ShiftJIS) |
||
161 |
WML - Japanese (EUC) |
162 |
WML - Korean (Hangul) |
||
163 |
WML - Central European |
164 |
WML – CSS |
||
165 |
StarOffice 5.2 Writer |
166 |
MIFF 6.0 |
||
167 |
MIFF 6.0 Japan |
168 |
MIFF |
||
169 |
Java Script |
170 |
ASCII Text |
||
171 |
Handheld Device Markup Language (HDML) |
172 |
Compact HTML (CHTML) |
||
173 |
XHTML Basic |
174 |
AvantGo HTML |
||
175 |
Web Clipping Application (WCA) HTML |
176 |
SearchML |
||
177 |
Pocket Word - Pocket PC |
178 |
Wireless HTML |
||
179 |
Hangul 97 Word Processor |
180 |
Hangul 2002 - 2007 Word Processor |
||
181 |
Internet HTML – Unicode |
182 |
XML With Doctype HTML |
||
184 |
EBCDIC encoded Text |
185 |
Microsoft Word 2002 |
||
186 |
Microsoft Word 2003/2004 |
187 |
Internet Message |
||
188 |
StarOffice 6 & 7 Writer |
189 |
Microsoft Outlook PST/OST 97/2000/XP |
||
190 |
XHTML |
191 |
Microsoft Works 2000 |
||
192 |
Internet Mail Message |
193 |
Internet News Message |
||
194 |
Outlook Express News Message |
195 |
Outlook Express Mail Message |
||
196 |
vCalendar |
197 |
Transport-Neutral Encapsulation Format(TNEF) |
||
198 |
MHTML(Web Archive) |
199 |
Search HTML |
||
200 |
Search Text |
201 |
PST Fields File |
||
202 |
Microsoft Outlook PST/OST 2003/2007 |
203 |
Microsoft Outlook PAB |
||
204 |
SearchML 20 |
205 |
SearchML 30 |
||
206 |
Yahoo! Messenger Archive |
207 |
Microsoft Word XML 2003 |
||
208 |
MS Office 12 Word format |
209 |
StarOffice 8/Open Office 2.x Writer |
||
210 |
SearchML 31 |
211 |
Outlook Form Template |
||
212 |
Microsoft Word 2007 |
213 |
Password Protected Microsoft Word 2007 |
||
214 |
Microsoft Word 2007 Template |
215 |
SearchML 32 |
||
216 |
DRM protected Unknown |
217 |
DRM protected Microsoft Word |
||
218 |
DRM protected Microsoft Word 2007 |
219 |
File sealed by Oracle IRM |
||
220 |
Extensible Metadata Platform |
221 |
SearchML 33 |
||
222 |
PHTML |
223 |
Open Office Writer 6 |
||
224 |
Open Office Writer 8 |
225 |
IBM Lotus Symphony Document |
||
226 |
SearchML 34 |
227 |
MS Office 12 (2007) Word - Macro Enabled XML format |
||
228 |
MS Office 12 (2007) Word Template - Macro Enabled XML format |
229 |
Microsoft Word Picture |
||
230 |
Smart DataBase |
231 |
DBase III |
||
232 |
DBase IV or V |
233 |
Framework III |
||
234 |
Microsoft Works DB |
235 |
DataEase 4.x |
||
236 |
Paradox 2 or 3 |
237 |
Paradox 3.5 |
||
238 |
Q&A Database |
239 |
Reflex |
||
240 |
R:Base System V |
241 |
R:Base 5000 |
||
242 |
R:Base File 1 |
243 |
R:Base File 3 |
||
244 |
First Choice DB |
245 |
Mac Works 2.0 DB |
||
246 |
Windows Works DB |
247 |
Paradox |
||
248 |
Microsoft Access |
249 |
CEO Decision Base |
||
250 |
Windows Works 3.0 DB |
251 |
Windows Works 4.0 DB |
||
252 |
Microsoft Access 7 |
253 |
Microsoft Project 98 |
||
254 |
Microsoft Project 2000/2002/2003 |
255 |
Microsoft Project 2002 |
||
256 |
MS Project 2007 |
257 |
Lotus Notes database |
||
258 |
Symphony |
259 |
Lotus 1-2-3 1.0 |
||
260 |
Lotus 1-2-3 2.0 |
261 |
Lotus 1-2-3 3.x |
||
262 |
Smart Spreadsheet |
263 |
Microsoft Excel 2.x |
||
264 |
Enable Spreadsheet |
265 |
Microsoft Works SS |
||
266 |
VP-Planner |
267 |
Mosaic Twin |
||
268 |
SuperCalc 5 |
269 |
Quattro Pro |
||
270 |
Quattro |
271 |
PFS: Plan |
||
272 |
First Choice SS |
273 |
Microsoft Excel 3.0 |
||
274 |
Generic WKS |
275 |
Mac Works 2.0 SS |
||
276 |
Windows Works SS |
277 |
Microsoft Excel 4.0 |
||
278 |
Quattro Pro for Windows |
279 |
Lotus 1-2-3 4.x / 5.x |
||
280 |
Quattro Pro Windows Japan |
281 |
CEO Spreadsheet |
||
282 |
Microsoft Excel 5.0/7.0 |
283 |
Multiplan 4.0 |
||
284 |
Windows Works 3.0 SS |
285 |
Quattro Pro 4.0 |
||
286 |
Quattro Pro 5.0 |
287 |
Quattro Pro Win 6.0 |
||
288 |
Lotus 123 Release 2 for OS/2 |
289 |
Lotus 123 for OS/2 Chart |
||
290 |
Windows Works 4.0 SS |
291 |
Quattro Pro Win 7.0/8.0 |
||
292 |
Quattro Pro Win 7.0/8.0 Graph |
293 |
Lotus 1-2-3 97 Edition |
||
294 |
Microsoft Mac Excel 4.0 |
295 |
Microsoft Mac Excel 5.0 |
||
296 |
Microsoft Excel 97/98/2004 |
297 |
MS Excel 3.0 Workbook |
||
298 |
MS Excel 4.0 Workbook |
299 |
MS Excel Mac 4.0 Workbook |
||
300 |
MS Excel Mac 4.0 Workbook |
301 |
Lotus 1-2-3 98/Millennium Edition |
||
302 |
Quattro Pro 8.0 |
303 |
Quattro Pro Win 9.0 / X3 |
||
304 |
Microsoft Excel 2000 |
305 |
Quattro Pro Win 10.0 |
||
306 |
Microsoft Excel 2002 |
307 |
StarOffice 5.2 Calc |
||
308 |
Quattro Pro Win 11.0 |
309 |
Microsoft Excel 2003 |
||
310 |
StarOffice 6 & 7 Calc |
311 |
Quattro Pro Win 12.0 |
||
312 |
StarOffice 8/Open Office 2.x Calc |
313 |
Microsoft Excel 2007 |
||
314 |
Password Protected Microsoft Excel 2007 |
315 |
Microsoft Excel 2007 Binary |
||
316 |
DRM protected Microsoft Excel 2007 |
317 |
DRM protected Microsoft Excel 2007 |
||
318 |
MS Works SS6 |
319 |
Open Office Calc 6 |
||
320 |
Open Office Calc 8 |
321 |
IBM Lotus Symphony Spreadsheet |
||
322 |
Excel Template 2007 |
323 |
Excel Macro Enabled |
||
324 |
Excel Template Macro Enabled 2007 |
325 |
Windows Bitmap |
||
326 |
Tagged Image File Format |
327 |
Paintbrush |
||
328 |
Compuserve GIF |
329 |
EPS (TIFF Header) |
||
330 |
CCITT Group 3 Fax |
331 |
Mac PICT2 |
||
332 |
WordPerfect Graphic |
333 |
Windows Metafile |
||
334 |
Lotus PIC |
335 |
Mac PICT |
||
336 |
Ami Draw |
337 |
Targa |
||
338 |
GEM Image |
339 |
OS/2 Bitmap |
||
340 |
Windows Icon |
341 |
Windows Cursor |
||
342 |
Micrografx product |
343 |
MacPaint |
||
344 |
Corel Draw 2.0 |
345 |
Corel Draw 3.0 |
||
346 |
HP Graphics Language |
347 |
Harvard 3.0 Chart |
||
348 |
Harvard 2.0 Chart |
349 |
Harvard 3.0 Presentation |
||
350 |
Freelance |
351 |
WordPerfect Graphic 2 |
||
352 |
CGM Graphic Metafile |
353 |
Excel 2.x Chart |
||
354 |
Excel 3.0 Chart |
355 |
Excel 4.0 Chart |
||
356 |
Candy 4 |
357 |
Hanako 1.x |
||
358 |
Hanako 2.x |
359 |
JPEG File Interchange |
||
360 |
Excel 5.0/7.0 Chart |
361 |
Corel Draw 4.0 |
||
362 |
PowerPoint 4.0 |
363 |
Multipage PCX |
||
364 |
PowerPoint 3.0 |
365 |
Corel Draw 5.0 |
||
366 |
OS/2 Metafile |
367 |
PowerPoint 7.0 |
||
368 |
AutoCAD DXF (ASCII) |
369 |
AutoCAD DXF (Binary) |
||
370 |
AutoCAD DXB |
371 |
Freelance 96/97/Millennium Edition |
||
372 |
Mac PowerPoint 3.0 |
373 |
Mac PowerPoint 4.0 |
||
374 |
WordPerfect Presentations |
375 |
OS/2 Warp Bitmap |
||
376 |
AutoCAD Drawing 12 |
377 |
AutoCAD Drawing 13 |
||
378 |
Adobe Illustrator |
379 |
Corel Presentations 7.0 - 12.0 / X3 |
||
380 |
WordPerfect Graphic 7.0/8.0/9.0 |
381 |
Adobe Acrobat (PDF) |
||
382 |
Framemaker |
383 |
RAS - Sun Raster |
||
384 |
AutoShade Rendering |
385 |
Kodak Photo CD |
||
386 |
PowerPoint 4.0 (extracted from docfile) |
387 |
Mac PowerPoint 4.0 (extracted from docfile) |
||
388 |
Enhanced Windows Metafile |
389 |
GEM |
||
390 |
Mac PowerPoint 3.0 |
391 |
Mac PowerPoint 4.0 |
||
392 |
Harvard Graphics for Windows |
393 |
IGES Drawing File Format |
||
394 |
IBM Picture Interchange Format |
395 |
X-Windows Bitmap |
||
396 |
X-Windows Pixmap |
397 |
CALS Raster File Format |
||
398 |
Portable Network Graphics Format |
399 |
X-Windows Dump |
||
400 |
CorelDraw ClipArt |
401 |
HP Gallery |
||
402 |
Graphics Data Format |
403 |
Micrografx Designer |
||
404 |
Post Script |
405 |
Microsoft PowerPoint 97-2004 |
||
406 |
Corel Draw 6.0 |
407 |
Corel Draw 7.0 |
||
408 |
PDF MacBinary Header |
409 |
AutoCAD Drawing - Unknown Version |
||
410 |
Visio 4.x |
411 |
AutoCAD Drawing 14 |
||
412 |
PBM (Portable Bitmap) |
413 |
PGM (Portable Graymap) |
||
414 |
PPM (Portable Pixmap) |
415 |
Adobe Photoshop |
||
416 |
Microsoft PowerPoint Dual 95/97 |
417 |
Paint Shop Pro |
||
418 |
Kodak FlashPix |
419 |
Visio 5.x |
||
420 |
Corel Draw 8.0 |
421 |
Visio 6.x |
||
422 |
Corel Draw 9.0 |
423 |
Progressive JPEG |
||
424 |
Microsoft PowerPoint 2000/2002 |
425 |
Bentley Microstation DGN |
||
426 |
Windows 98/2000 Bitmap |
427 |
Wireless Bitmap |
||
428 |
MIFF Graphic |
429 |
Microsoft PowerPoint 2 |
||
430 |
WordPerfect Graphic 10.0 |
431 |
Visio 3.x |
||
432 |
Micrografx Designer |
433 |
PDF Image |
||
434 |
StarOffice 5.2 Impress |
435 |
Adobe Illustrator 9 |
||
436 |
AutoCAD 2000/2002 Drawing |
437 |
AutoCAD 2.5 Drawing |
||
438 |
AutoCAD 2.6 Drawing |
439 |
AutoCAD 9 Drawing |
||
440 |
AutoCAD 10 Drawing |
441 |
QuarkXPress 3.0 For Macintosh |
||
442 |
QuarkXPress 3.1 For Macintosh |
443 |
QuarkXPress 3.2 For Macintosh |
||
444 |
QuarkXPress 3.3 For Macintosh |
445 |
QuarkXPress 4.0 For Macintosh |
||
446 |
QuarkXPress 3.3 For Windows |
447 |
QuarkXPress 4.0 For Windows |
||
448 |
QuarkXPress 5.0 For Windows |
449 |
Export Image |
||
450 |
StarOffice 6 & 7 Draw |
451 |
StarOffice 6 & 7 Impress |
||
452 |
JBIG2 Bitmap |
453 |
Corel Draw 10.0 |
||
454 |
Corel Draw 11.0 |
455 |
Microsoft Visio 2003 |
||
456 |
StarOffice 8 Draw |
457 |
StarOffice 8/Open Office 2.x Impress |
||
458 |
AutoCAD 2004/2005/2006 Drawing |
459 |
Microsoft PowerPoint 2007 |
||
460 |
Microsoft XML Paper Specification |
461 |
Password Protected Microsoft Powerpoint 2007 |
||
462 |
AutoCAD 2007 Drawing |
463 |
OS/2 v.2 Bitmap |
||
464 |
StarView Metafile |
465 |
eFax Document |
||
475 |
DRM protected Microsoft Powerpoint |
476 |
DRM protected Microsoft Powerpoint 2007 |
||
477 |
AutoDesk DWF |
478 |
Corel Draw 12.0 |
||
479 |
JPEG 2000 |
480 |
Adobe Indesign |
||
481 |
JPEG 2000 jpf Extension |
482 |
JPEG 2000 mj2 Extension |
||
483 |
WordPerfect Informs 1.0 |
484 |
Lotus Screen SnapShot |
||
485 |
Lotus Screen Snapshot |
486 |
Interchange Format |
||
487 |
Microsoft Escher Graphics |
488 |
Windows Sound |
||
489 |
Windows Video |
490 |
MIDI File |
||
491 |
Macromedia Director |
492 |
Macromedia Flash |
||
493 |
Macromedia Flash |
494 |
Quicktime Movie |
||
495 |
MPEG Layer3 ID3 Ver 1.x |
496 |
MPEG Layer3 ID3 Ver 2.x |
||
497 |
ID3 Ver 1.x |
498 |
ID3 Ver 2.x |
||
499 |
MPEG-1 audio - Layer 3 |
500 |
MPEG-1 audio - Layer 1 |
||
501 |
MPEG-1 audio - Layer 2 |
502 |
MPEG-2 audio - Layer 1 |
||
503 |
MPEG-2 audio - Layer 2 |
504 |
MPEG-2 audio - Layer 3 |
||
505 |
Advanced Systems Format |
506 |
Windows Media Video (ASF subtype) |
||
507 |
Windows Media Audio (ASF subtype) |
508 |
Microsoft Digital Video Recording (ASF subtype) |
||
509 |
Real Media (both Real Audio and Real Video) |
510 |
MPEG-1 video |
||
511 |
MPEG-2 video |
512 |
ISO Base Media File Format |
||
513 |
MPEG-4 file |
514 |
MPEG-7 file |
||
515 |
EXE / DLL File |
516 |
.COM File |
||
517 |
.ZIP File |
518 |
Self UnZIPping .EXE |
||
519 |
.ARC File |
520 |
MS Office Binder |
||
521 |
UNIX Compress |
522 |
UNIX Tar |
||
523 |
Envoy |
524 |
QuickFinder |
||
525 |
Windows Clipboard File |
526 |
Envoy 7 |
||
527 |
StuffIt |
528 |
LZH Compress |
||
529 |
Self-Extracting LZH |
530 |
UNIX GZip |
||
531 |
Java Class File |
532 |
mbox(RFC-822 mailbox) |
||
533 |
Lotus Notes Database R6.x |
534 |
Generic Password Protected Microsoft Office 2007 Document |
||
535 |
Microsoft Cabinet File |
536 |
.RAR File |
||
537 |
Self extracting RAR File |
538 |
Microsoft InfoPath |
||
549 |
Flexiondoc 1 (original) schema |
550 |
Flexiondoc 2 schema |
||
551 |
Flexiondoc 3 schema |
552 |
Flexiondoc 4 schema |
||
553 |
Flexiondoc 5 schema |
554 |
Flexiondoc 5.1 schema |
||
555 |
OASIS OpenDocument v1.0 |
556 |
Flexiondoc 5.2 schema |
||
557 |
Domino XML schema |
558 |
Adobe Indesign Interchange |
||
559 |
XML Visio |
560 |
Mail archive DXL |
||
561 |
Mail message DXL |
562 |
Generic DXL |
||
564 |
AutoCAD DWG 2008 |
565 |
Publisher 2003 |
||
566 |
Publisher 2007 |
567 |
Open Office Impress 6 |
||
568 |
Open Office Impress 8 |
569 |
IBM Lotus Symphony Presentations |
||
570 |
Open Office Draw 6 |
571 |
Open Office Draw 8 |
||
572 |
PowerPoint 2007 Template |
573 |
PowerPoint 2007 Macro Enabled |
||
574 |
PowerPoint 2007 Template Macro Enabled |
575 |
PowerPoint 2007 Slideshow file |
||
576 |
PowerPoint 2007 Template Macro Enabled |
577 |
Oracle Multimedia internal raster format |
||
578 |
TK thesaurus |
579 |
TK abbrev |
||
580 |
TK dictionary |
581 |
TK quote |
||
582 |
TK written word |
583 |
TK culturelit |
||
584 |
TK grammar |
585 |
TK thessyn |
||
586 |
Text - (ASCII) |
587 |
Text - (Hex) |
||
588 |
Text - (ANSI) |
589 |
Text - (Unicode) |
||
590 |
Text - (ASCII) |
591 |
Text - (ANSI 8) |
||
592 |
Text - Unknown format |
593 |
Text - MAC - 7bit |
||
594 |
Text - MAC - 8bit |
595 |
Text - Japanese (ShiftJIS) |
||
596 |
Text - Chinese (GB) |
597 |
Text - Korean (Hangul) |
||
598 |
Text - Chinese (Big 5) |
599 |
Code page 852 - MS DOS Slavic |
||
600 |
Text - Japanese (EUC) |
601 |
Text - Hebrew (7-bit) |
||
602 |
Text - Hebrew (IBM PC8) |
603 |
Text - Hebrew (VAX E0) |
||
604 |
Text - Hebrew (Windows ANSI 1255) |
605 |
Text – Arabic 710 |
||
606 |
Text – Arabic 720 |
607 |
Text - Arabic (Windows ANSI 1256) |
||
609 |
Text - Japanese (JIS) |
610 |
Text - Central European |
||
611 |
UTF-8 encoded Text |
612 |
Text - U.S. English/Portuguese (EBCDIC 37) |
||
613 |
Text - Austrian/German (EBCDIC 273) |
614 |
Text - Danish/Norwegian (EBCDIC 277) |
||
615 |
Text - Finnish/Swedish (EBCDIC 278) |
616 |
Text - Italian (EBCDIC 280) |
||
617 |
Text - Spanish (EBCDIC 284) |
618 |
Text - U.K. English (EBCDIC 285) |
||
619 |
Text - French (EBCDIC 297) |
620 |
Text - Belgian/International (EBCDIC 500) |
||
621 |
Text - Eastern European (EBCDIC 870) |
622 |
Text - Icelandic (EBCDIC 871) |
||
623 |
Text - Turkish (EBCDIC 1026) |
624 |
HTML - U.S. English/Portuguese (EBCDIC 37) |
||
625 |
HTML - Austrian/German (EBCDIC 273) |
626 |
HTML - Danish/Norwegian (EBCDIC 277) |
||
627 |
HTML - Finnish/Swedish (EBCDIC 278) |
628 |
HTML - Italian (EBCDIC 280) |
||
629 |
HTML - Spanish (EBCDIC 284) |
630 |
HTML - U.K. English (EBCDIC 285) |
||
631 |
HTML - French (EBCDIC 297) |
632 |
HTML - Belgian/International (EBCDIC 500) |
||
633 |
HTML - Eastern European (EBCDIC 870) |
634 |
HTML - Icelandic (EBCDIC 871) |
||
635 |
HTML - Turkish (EBCDIC 1026) |
636 |
UUE Encoded Text |
||
637 |
UUE Encoded Continued Part |
638 |
XXE Encoded Text |
||
639 |
XXE Encoded Continued Part |
640 |
YEnc Encoded Text |
||
641 |
YEnc Encoded Continued Part |
642 |
BinHex Encoded Text |
||
643 |
BinHex Encoded Continued Part |
644 |
Text - Arabic (ASMO-708) |
||
645 |
Text - Arabic (DOS OEM 720 TRANSPARENT ASMO) |
646 |
Text - Arabic (ISO 8859-6) |
||
647 |
Text - Arabic (Mac) |
648 |
Text - Baltic (ISO 8859-4) |
||
649 |
Text - Baltic (Windows ANSI 1257) |
650 |
Text - Central European (DOS OEM 852 Latin II) |
||
651 |
Text - Central European (ISO 8859-2) |
652 |
Text - Central European (Mac) |
||
653 |
Text - Central European (Windows ANSI 1250) |
654 |
Text - Chinese Simplified (Windows ANSI 936 [GB2312]) |
||
655 |
Text - Chinese Traditional (Windows ANSI 950 [BIG5]) |
656 |
Text - Cyrillic (DOS OEM 855) |
||
657 |
Text - Cyrillic (ISO 8859-5) |
658 |
Text - Cyrillic (KOI8-R) |
||
659 |
Text - Cyrillic (Mac) |
660 |
Text - Cyrillic (Windows ANSI 1251) |
||
661 |
Text - Greek (ISO 8859-7) |
662 |
Text - Greek (Mac) |
||
663 |
Text - Greek (Windows ANSI 1253) |
664 |
Text - Hebrew (DOS OEM 862) |
||
665 |
Text - Hebrew (ISO 8859-8) |
666 |
Text - Japanese (Mac) |
||
667 |
Text - Korean (Windows ANSI 1361 [Johab]) |
668 |
Text - Korean (Windows ANSI 949) |
||
669 |
Text - Russian (DOS OEM 866) |
670 |
Text - Thai (Windows ANSI 874) |
||
671 |
Text - Turkish (DOS OEM 857) |
672 |
Text - Turkish (ISO 8859-9) |
||
673 |
Text - Turkish (Mac) |
674 |
Text - Turkish (Windows ANSI 1254) |
||
675 |
Text - Vietnamese (Windows ANSI 1258) |
676 |
Text - Western European (ISO 8859-1) |
||
677 |
Text - Western European (Mac) |
678 |
Text - Western European (Windows ANSI 1252) |
||
679 |
HTML - Arabic (ASMO-708) |
680 |
HTML - Arabic (DOS OEM 720 TRANSPARENT ASMO) |
||
681 |
HTML - Arabic (ISO 8859-6) |
682 |
HTML - Arabic (Mac) |
||
683 |
HTML - Arabic (Windows ANSI 1256) |
684 |
HTML - Baltic (ISO 8859-4) |
||
685 |
HTML - Baltic (Windows ANSI 1257) |
686 |
HTML - Central European (DOS OEM 852 Latin II) |
||
687 |
HTML - Central European (ISO 8859-2) |
688 |
HTML - Central European (Mac) |
||
689 |
HTML - Central European (Windows ANSI 1250) |
690 |
HTML - Chinese Simplified (EUC) |
||
691 |
HTML - Chinese Simplified (Windows ANSI 936 [GB2312]) |
692 |
HTML - Chinese Traditional (Windows ANSI 950 [BIG5]) |
||
693 |
HTML - Cyrillic (DOS OEM 855) |
694 |
HTML - Cyrillic (ISO 8859-5) |
||
695 |
HTML - Cyrillic (KOI8-R) |
696 |
HTML - Cyrillic (Mac) |
||
697 |
HTML - Cyrillic (Windows ANSI 1251) |
698 |
HTML - Greek (ISO 8859-7) |
||
699 |
HTML - Greek (Mac) |
700 |
HTML - Greek (Windows ANSI 1253) |
||
701 |
HTML - Hebrew (DOS OEM 862) |
702 |
HTML - Hebrew (ISO 8859-8) |
||
703 |
HTML - Hebrew (Windows ANSI 1255) |
704 |
HTML - Japanese (Mac) |
||
705 |
HTML - Japanese (Windows Shift-JIS ANSI 932) |
706 |
HTML - Korean (Windows ANSI 1361 [Johab]) |
||
707 |
HTML - Korean (Windows ANSI 949) |
708 |
HTML - Russian (DOS OEM 866) |
||
709 |
HTML - Thai (Windows ANSI 874) |
710 |
HTML - Turkish (DOS OEM 857) |
||
711 |
HTML - Turkish (ISO 8859-9) |
712 |
HTML - Turkish (Mac) |
||
713 |
HTML - Turkish (Windows ANSI 1254) |
714 |
HTML - Vietnamese (Windows ANSI 1258) |
||
715 |
HTML - Western European (ISO 8859-1) |
716 |
HTML - Western European (Mac) |
||
717 |
HTML - Western European (Windows ANSI 1252) |
718 |
Plugin |
||
719 |
Text - Japanese (ShiftJIS) |
720 |
Windows Metafile [5000] |
||
721 |
WordPerfect Graphic [B] |
722 |
Ami (internal bitmap) |
||
723 |
Word (internal bitmap) |
724 |
Mac PICT2 Binary |
||
725 |
Windows Metafile [5005] |
726 |
Windows Metafile [5006] |
||
727 |
PerfectWorks Picture |
728 |
WPG2 (internal bitmap) |
||
729 |
Windows DIB |
730 |
WPG1 (internal bitmap) |
||
731 |
Embedded Bitmap |
732 |
Embedded Bitmap |
||
733 |
IAF (internal bitmap) |
734 |
IAF (internal bitmap) |
||
735 |
PICT (internal bitmap) |
736 |
Export OCR data as Text, no formatting |
||
737 |
Export OCR data as RTF, yes formatting |
738 |
Export OCR data as HTML |
||
739 |
EDRM export |
753 |
Open Office 3.x Writer (ODF 1.2) |
||
754 |
StarOffice 9 Writer (ODF 1.2) |
755 |
Oracle Open Office 3.x Writer (ODF 1.2) |
||
756 |
Samsung Jungum File |
757 |
Kingsoft Office Writer File |
||
758 |
Microsoft Word 2010 |
759 |
Microsoft Word 2010 Template |
||
760 |
Microsoft Word 2010 Macro Enabled Document |
761 |
Microsoft Word 2010 Macro Enabled Template |
||
764 |
Microsoft Project 2010 |
765 |
Microsoft Excel XML 2003 |
||
766 |
Open Office 3.x Calc (ODF 1.2) |
769 |
Microsoft Excel 2007 Excel Add-in Macro File |
||
770 |
Lotus Data Interchange Format |
771 |
StarOffice 9 Calc (ODF 1.2) |
||
772 |
Oracle Open Office 3.x Calc (ODF 1.2) |
773 |
Kingsoft Office Spreadsheet File |
||
774 |
Corel Presentations X4 |
775 |
Microsoft Excel 2010 Macro Enabled Workbook |
||
776 |
Microsoft Excel 2010 Template |
777 |
Microsoft Excel 2010 Macro Enabled Template |
||
778 |
Microsoft Excel 2010 Excel Add-in Macro File |
779 |
Microsoft Excel 2010 Binary |
||
782 |
Resource Interchange File Format |
783 |
Microsoft OneNote 2007 |
||
784 |
Windows Media Player Playlist |
786 |
Flexiondoc v5.4 (XML) |
||
790 |
Open Office 3.x Impress (ODF 1.2) |
791 |
Open Office 3.x Draw (ODF 1.2) |
||
792 |
Corel Presentations X4 |
793 |
Microsoft Access Report Snapshot 2000 - 2003 |
||
794 |
StarOffice 9 Impress (ODF 1.2) |
795 |
StarOffice 9 Draw (ODF 1.2) |
||
796 |
Oracle Open Office 3.x Impress (ODF 1.2) |
797 |
Oracle Open Office 3.x Draw (ODF 1.2) |
||
798 |
Microsoft PowerPoint 2010 |
799 |
Microsoft PowerPoint 2010 Template |
||
800 |
Microsoft PowerPoint 2010 Macro Enabled Template |
801 |
Microsoft PowerPoint 2010 Slideshow |
||
802 |
Microsoft PowerPoint 2010 Macro Enabled Presentation |
803 |
Microsoft PowerPoint 2010 Macro Enabled Slideshow |
||
804 |
Macromedia Flash 9 |
805 |
Macromedia Flash 10 |
||
806 |
Microsoft Windows Explorer Command File |
807 |
7z Archive File |
||
808 |
Trillian Text Log File |
809 |
Trillian XML Log File |
||
810 |
Microsoft Live Messenger Log File |
811 |
AOL Messenger Log File |
||
812 |
Windows Help File |
813 |
Windows Compiled Help File |
||
814 |
Windows shortcut |
815 |
TrueType Font File |
||
816 |
TrueType Font Collection File |
817 |
TrueType (MAC) Font File |
||
818 |
MS Outlook Mail File |
819 |
Outlook Mail Form Template |
||
820 |
MS Outlook Appointment File |
821 |
Outlook Appointment Form Template |
||
822 |
MS Outlook Journal File |
823 |
Outlook Journal Form Template |
||
824 |
MS Outlook Contact File |
825 |
Outlook Contact Form Template |
||
826 |
MS Outlook Note File |
827 |
Outlook Note Form Template |
||
828 |
MS Outlook Task File |
829 |
Outlook Task Form Template |
||
830 |
Apple Mail 2.0 Message |
831 |
Self extracting 7z Archive File |
||
832 |
AutoCAD 2010/2011/2012 Drawing |
833 |
Microsoft Access 2000/2002/2003 |
||
834 |
Microsoft Access 2007/2010 |
835 |
Microsoft Access Web Database |
||
836 |
Microsoft Access 2007/2010 Template File |
837 |
Outlook Non Delivery Report
|
||
838 |
Outlook Non Delivery Report Form Template |
839 |
Outlook Post |
||
840 |
Outlook Post Form Template |
841 |
Outlook Distribution List |
||
842 |
Outlook Distribution List Form Template |
843 |
Outlook Clear Signed Email |
||
844 |
Outlook Clear Signed Email Form Template |
846 |
Outlook Opaque Signed Email Form Template |
||
847 |
Apple iWork Pages File |
848 |
Apple iWork Pages File Preview |
||
849 |
S/MIME (Secure/MIME) |
850 |
Clear Signed S/MIME (Secure/MIME) |
||
851 |
Microsoft Word 2013 |
852 |
Microsoft Word 2013 Template |
||
853 |
Microsoft Word 2013 Macro Enabled Document |
854 |
Microsoft Word 2013 Macro Enabled Template |
||
855 |
Quattro Pro Win X5 |
856 |
Apple iWork Numbers File |
||
857 |
Apple iWork Numbers File Preview |
858 |
Microsoft Excel XML 2007/2010 |
||
859 |
Microsoft Excel 2013 Workbook |
860 |
Microsoft Excel 2013 Macro Enabled Workbook |
||
861 |
Microsoft Excel 2013 Template |
862 |
Microsoft Excel 2013 Excel Add-in Macro File |
||
863 |
Microsoft Excel 2013 Binary |
864 |
Microsoft OneNote Table of Contents File |
||
865 |
Microsoft OneNote Package |
866 |
Corel Presentations X5 |
||
867 |
Apple iWork Keynote File |
868 |
Apple iWork Keynote File Preview |
||
869 |
Scalable Vector Graphics File |
870 |
AutoDesk DWF Archive File |
||
871 |
Microsoft PowerPoint 2013 |
872 |
Microsoft PowerPoint 2013 Template |
||
873 |
Microsoft PowerPoint 2013 Macro Enabled Template |
874 |
Microsoft PowerPoint 2013 Slideshow |
||
875 |
Microsoft PowerPoint 2013 Macro Enabled Presentation |
876 |
Microsoft PowerPoint 2013 Macro Enabled Slideshow |
||
877 |
Microsoft Office Theme File |
878 |
Adobe Photoshop Large Document Format |
||
879 |
Digital Imaging and Communications in Medicine (DICOM) File |
|
|
||
For secure SSL communication, gateways must establish trust with endpoint computers by showing a Server Certificate. This section discusses the procedures necessary to generate and install server certificates.
Check Point gateways, by default, use a certificate created by the Internal Certificate Authority on the Security Management Server as their server certificate. Browsers do not trust this certificate. When an endpoint computer tries to connect to the gateway with the default certificate, certificate warning messages open in the browser. To prevent these warnings, the administrator must install a server certificate signed by a trusted certificate authority.
All portals on the same Security Gateway IP address use the same certificate.
To be accepted by an endpoint computer without a warning, gateways must have a server certificate signed by a known certificate authority (such as Entrust, VeriSign or Thawte). This certificate can be issued directly to the gateway, or be a chained certificate that has a certification path to a trusted root certificate authority (CA).
The next sections describe how to get a certificate for a gateway that is signed by a known Certificate Authority (CA).
Related Topics |
First, generate a Certificate Signing Request (CSR). The CSR is for a server certificate, because the gateway acts as a server to the clients.
|
Note - This procedure creates private key files. If private key files with the same names already exist on the computer, they are overwritten without warning. |
cpopenssl req -new -out <CSR file> -keyout <private key file> -config $CPDIR/conf/openssl.cnf
This command generates a private key. You see this output:
Generating a 2048 bit RSA private key.+++...+++writing new private key to 'server1.key'Enter PEM pass phrase:
Fill in the data.
portal.example.com.keyAfter you get the Signed Certificate for the gateway from the CA, generate a P12 file that has the Signed Certificate and the private key.
If the signed certificate is in P12 or P7B format, convert these files to a PEM (Base64 encoded) formatted file with a CRT extension.
Usually you get the certificate chain from the signing CA. Sometimes it split into separate files. If the signed certificate and the trust chain are in separate files, use a text editor to combine them into one file. Make sure the server certificate is at the top of the CRT file.
*.crt *.keycpopenssl pkcs12 -export -out <output file> -in <signed cert chain file> -inkey <private key file>
For example:cpopenssl pkcs12 -export -out server1.p12 -in server1.crt -inkey server1.key
Install the Third Party signed certificate to create Trust between the Mobile Access Software Blade and the clients.
All portals on the same IP address use the same certificate. Define the IP address of the portal in the Portal Settings page for the blade/feature.
In the Certificate section, click Import or Replace.
|
Note - The Repository of Certificates on the IPsec VPN page of the SmartDashboard gateway object is only for self-signed certificates. It does not affect the certificate installed manually using this procedure. |
To see the new certificate from a Web browser:
The gateway uses the certificate when you connect with a browser to the portal. To see the certificate when you connect to the portal, click the lock icon that is next to the address bar in most browsers.
The certificate that users see depends on the actual IP address that they use to access the portal- not only the IP address configured for the portal in SmartDashboard.
To see the new certificate from SmartDashboard:
From the Gateway Properties > Data Loss Prevention page, click the View button in the Certificate section.