

Included Topics |
You can configure cluster virtual IP addresses in different subnets than the members. The cluster virtual interfaces must have routable IP addresses that connect to internal and external networks.
The network "sees" the cluster as one Security Gateway that operates as a network router. The network is not aware of the internal cluster structure and member addresses.
Advantages of using different subnets:
Note - This capability is available only for ClusterXL Clusters. For details about OPSEC certified clusters, see the vendor documentation.
Traffic sent from cluster members to internal or external networks is hidden behind the cluster virtual IP addresses and MAC addresses. The MAC address assigned to cluster interfaces is the:
The use of different subnets with cluster objects has some limitations.
These are the steps necessary to configure a cluster with different subnets:
You can do this with operating system commands or with the Check Point cpconfig utility,
Usually, cluster virtual IP addresses are automatically related to an interface based on membership in the same subnet. When the subnets are different, you must explicitly define the relationship between a member interface and a cluster virtual IP address.
When using a cluster with the cluster virtual IP and members on different subnets, it is necessary to manually define the member.
To manually define the member network.
For more details, see the Configuring Cluster Objects chapter.
Use this procedure to configure a static route on all Gaia members. If you do not define the static routes correctly, the member interface IP address is not routable.
|
Note - It is not necessary to configure on a Gaia Security Gateway in the VSX mode. This is done automatically when you configure routes in SmartDashboard. |
To configure a static route on a member - clish:
set static-route <VIP-subnet/mask> nexthop gateway logical <interface> on.<VIP-subnet> - Cluster Virtual IP address and subnet mask for the cluster interface.
<interface> - Member interface name.
set static-route <VIP-subnet> scopelocal on.<VIP-subnet> - Subnet virtual IP address for the cluster interface.
scopelocal attribute is set correctly, run:cat /etc/routed.conf
Sample output:
static {
10.16.6.0 masklen 24 gateway eth1 scopelocal; default gateway 192.168.2.11; }; |
||
|
Important - For R75.40, R75.40VS, and R75.45, you must download and install a Gaia Hotfix. This Hotfix includes a new configuration attribute ' |
|
To configure a static route on a member - WebUI:
Use this procedure to configure a static route on all SecurePlatform members. If you do not define the static routes correctly, the member interface IP address is not routable.
|
Note - It is not necessary to configure static routes the Advanced Dynamic Routing Suite is installed on your members. Advanced Dynamic Routing Suite automatically adds the static routes to the cluster network. |
To configure a static route on a member:
sysconfig. scopelocal attribute is set correctly:cat /etc/routed.conf
Sample output:
static {
10.16.6.0 masklen 24 gateway eth1 scopelocal; default gateway 192.168.2.11; }; |
To configure a static route in other operating systems, refer to the documentation for those systems. For more assistance, contact Check Point Support.
In this example, a one-Security Gateway firewall separating network 172.16.6.0 (Side "A") from network 172.16.4.0 (Side "B") is to be replaced with a ClusterXL cluster. The cluster members, however, will use networks 192.168.1.0 for Side "A", 192.168.2.0 for Side "B" and 192.168.3.0 for the synchronization network (all network addresses given in this example are of class "C"). The addresses in italics are the cluster Virtual IP addresses.
In this example, cluster protects two networks, Network A and Network B.
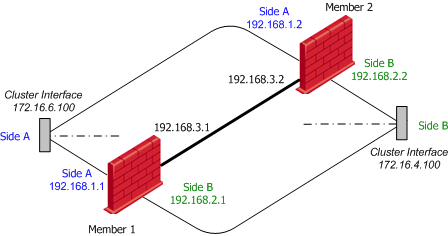
Configure each cluster member with these static routes:
For more on static route configuration, see sk32073.
To configure the cluster interface IP addresses:
|
Cluster Interface A |
Cluster Interface B |
|---|---|---|
General tab |
172.16.6.100 |
172.16.4.100 |
Member Networks tab |
192.168.1.0 |
192.168.2.0 |
|
Note - Do not define Cluster IP addresses for the synchronization interfaces. The synchronization interfaces are also defined in the Edit Topology page of the Cluster object. |
This new feature does not yet support all the capabilities of ClusterXL. Some features require additional configuration to work properly, while others are not supported.
Since ARP requests issued by cluster members are hidden behind the cluster IP and MAC, requests sent by one cluster member to the other may be ignored by the destination computer. To allow cluster members to communicate with each other, a static ARP should be configured for each cluster member, stating the MAC addresses of all other members in the cluster. IP packets sent between members are not altered, and therefore no changes should be made to the routing table.
|
Note - Static ARP is not required in order for the members to work properly as a cluster, since the cluster synchronization protocol does not rely on ARP. |
Although not all types of network hardware work with multicast MAC addresses, some routers can pass such packets, even though they are unable to handle ARP replies containing a multicast MAC address. Where a router semi-supports Load Sharing Multicast mode, it is possible to configure the cluster MAC as a static ARP entry in the router internal tables, and thus allow it to communicate with the cluster.
When different subnets are used for the cluster IPs, static ARP entries containing the router MAC need to be configured on each of the cluster members. This is done because this kind of router will not respond to ARP requests containing a multicast source MAC. These special procedures are not required when using routers that fully support multicast MAC addresses.
When using static NAT, the cluster can be configured to automatically recognize the hosts hidden behind it, and issue ARP replies with the cluster MAC address, on their behalf. This process is known as Automatic Proxy ARP.
However, if you use the ClusterXL VMAC mode or different subnets for the cluster IP addresses, this mechanism will not work, and you must configure the proxy ARP manually. To do so, in SmartDashboard, select Policy menu > Global Properties > NAT Network Address Translation, and disable Automatic ARP Configuration. Then create a file called local.arp in the firewall configuration directory ($FWDIR/conf).
Each entry in this file is a triplet, containing the:
The MAC address that should be used is the cluster multicast MAC defined on the responding interface, when using multicast LS, or this interface unique IP, for all other modes.
Since the unique IP addresses may be chosen arbitrarily, there is no guarantee that these addresses are accessible from the subnet of the cluster IP address. In order to access the members through their unique IP addresses, you must configure routes on the accessing cluster member, such that the cluster IP is the Default Gateway for the subnet of the unique IP addresses.
In the example, suppose Side "A" is the external network, and Side "B" is the internal network.