Multiple Entry Point for Remote Access VPNs

|
Note - The procedures in this section are relevant for SecureClient. For other clients, see the most updated documentation for that client.
|
The Need for Multiple Entry Point Security Gateways
The Security Gateway provides a single point of entry to the internal network. It is the Security Gateway that makes the internal network "available" to remote machines. If the Security Gateway fails, the internal network is no longer available. It therefore makes good sense to have Multiple Entry Points (MEP) to the same network.
The Check Point Solution for Multiple Entry Points
In a MEPed environment, more than one Security Gateway is both protecting and giving access to the same VPN domain. How a remote user selects a Security Gateway in order to reach a destination IP address depends on how the MEPed Security Gateways have been configured, which in turn depends on the requirements of the organization.
For more information, see Multiple Entry Point VPNs.
The Check Point solution for multiple entry points is based on a proprietary Probing Protocol (PP) that tests Security Gateway availability. The MEPed Security Gateways do not have to be in the same location; they can be widely-spaced, geographically.

|
Note - In a MEPed Security Gateway environment, the only remote client supported is the Check Point SecuRemote/SecureClient.
|
SecureClient Connect Profiles and MEP
There are three methods used to choose which Security Gateway will be used as the entry point for any given connection:
- First to reply. In a First to Reply MEP environment, SecureClient attempts to connect to the Security Gateway configured in the profile. If the configured Security Gateway does not reply, the first Security Gateway to respond is chosen.
- Primary/Backup. With this method, SecureClient attempts to connect to the Primary Security Gateway first. If the Primary Security Gateway does not reply, SecureClient attempts to connect to the Backup Security Gateway. If the Backup Security Gateway does not reply, there are no further attempts to connect.
- Random Selection. In a Load Sharing MEP environment, SecureClient randomly selects a Security Gateway and assigns the Security Gateway priority. The remote peer stays with this chosen Security Gateway for all subsequent connections to host machines within the VPN domain. Load distribution takes place on the level of "different clients", rather than the level of "endpoints in a connection". In addition, SecureClient ignores whatever Security Gateway is configured as the "connect to Security Gateway" in the profile.
Preferred Backup Security Gateway
Preferred Backup Security Gateway allows remote hosts to choose which Security Gateway in the MEP configuration will be the backup Security Gateway. All other Security Gateways in the MEP configuration will be ignored should the first two Security Gateways become unavailable.
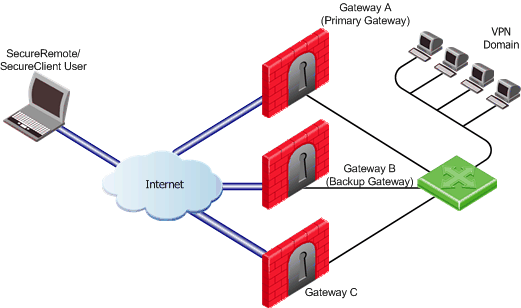
In this scenario:
- The VPN Domain is behind three Security Gateways: A, B and C.
- Security Gateway A is the Primary Security Gateway.
- Security Gateway B is the Backup Security Gateway when Security Gateway A is not available.
- Should Security Gateway A and Security Gateway B become unavailable, the remote host will not attempt to connect to Security Gateway C.
Visitor Mode and MEP
Since the RDP Security Gateway discovery mechanism used in a MEPed environment runs over UDP, this creates a special challenge for SecureClient in Visitor Mode, since all traffic is tunneled over a regular TCP connection.
In a MEPed environment:
- The RDP probing protocol is not used; instead, a special Visitor Mode handshake is employed.
- When a MEP failover occurs, SecureClient disconnects and the user needs to reconnect to the site in the usual way.
- In a Primary-Backup configuration, the connection will failover to the backup Security Gateway should the primary Security Gateway become unavailable. Even if the Primary Security Gateway is restored, the connection does not return to the primary Security Gateway.
- All the gateways in the MEP:
Must support visitor mode.
The user must be working with a Visitor Mode enabled profile.
Routing Return Packets
To make sure return packets are routed correctly, the MEPed Security Gateway makes use of IP pool NAT.
IP Pool NAT
IP pool NAT is a type of NAT in which source IP addresses from remote VPN domains are mapped to an IP address drawing from a pool of registered IP addresses. In order to maintain symmetric sessions using MEPed Security Gateways, the MEPed Security Gateway performs NAT using a range of IP addresses dedicated to that specific Security Gateway and should be routed within the internal network to the originating Security Gateway. When the returning packets reach the Security Gateway, the Security Gateway restores the original source IP address and forwards the packets to the source.

|
Note - When Office Mode is enabled, there is no need to configure IP Pool NAT since Office Mode dynamically assigns IP's to remote hosts.
|
Disabling MEP
When MEP is disabled, MEP RDP probing and fail over will not be performed. As a result, remote hosts will connect to the Security Gateway defined without considering the MEP configuration.
Configuring MEP
To configure MEP, decide on the MEP selection method:
- First to Respond
- Primary/Backup
- Load Distribution
First to Respond
When more than one Security Gateway leads to the same (overlapping) VPN domain, they are considered MEPed by the remote peer, and the first Security Gateway to respond to the probing protocol is chosen. To configure first to respond, define that part of the network that is shared by all the Security Gateways into a single group and assign that group as the VPN domain.
On the Properties window of each Security Gateway network object, Topology page > VPN Domain section, select Manually defined, and define the same VPN domain for all Security Gateways.
Primary-Backup
- In the Global Properties window, VPN > Advanced page, select Enable Backup Security Gateway.
- In the network objects tree, Groups section, create a group consisting of the Security Gateways that act as backup Security Gateways.
- On the VPN page of the network object selected as the Primary Security Gateway, select Use Backup Security Gateways, and select the group of backup Security Gateways from the drop-down box. This Security Gateway now functions as the primary Security Gateway for a specific VPN domain.
- Define the VPN for the backup Security Gateway(s). Backup Security Gateways do not always have a VPN domain of their own. They simply back-up the primary.
- If the backup Security Gateway does not have a VPN domain of its own, the VPN domain should include only the backup Security Gateway itself:
- On the Properties window of the backup network object, Topology page > VPN Domain section, select Manually defined.
- Select a group or network that contains only the backup Security Gateway.
- If the backup does have a VPN domain:
- Verify that the IP address of the backup Security Gateway is not included in the VPN domain of the primary.
- For each backup Security Gateway, define a VPN domain that does not overlap with the VPN domain of any other backup Security Gateway.
Note - There must be no overlap between the VPN domain of the primary Security Gateway and the VPN domain of the backup Security Gateway(s); that is, no IP address can belong to both.
- Configure IP pool NAT to handle return packets. See: Configuring Return Packets.
Load Distribution
- In the Global Properties window, Remote Access > VPN Basic page, Load distribution section, select Enable load distribution for Multiple Entry Point configurations (Remote Access connections).
- Define the same VPN domain for all Security Gateways.
Checking this option also means that load distribution is dynamic, that is the remote client randomly selects a Security Gateway.
Configuring Return Packets
Return packets are handled with IP pool NAT addresses belonging to the Security Gateway.
Configuring IP pool NAT
In Global Properties > NAT page, select Enable IP Pool NAT for SecuRemote/SecureClient and Security Gateway to Security Gateway connections. Then:
- For each Security Gateway, create a network object that represents the IP pool NAT addresses for that Security Gateway. The IP pool can be a network, group, or address range. For an address range, for example:
- On the network objects tree, right-click Network Objects branch > New > Address Range... The Address Range Properties window opens.
- On the General tab, enter the first IP and last IP of the address range.
- Click OK. In the network objects tree, Address Ranges branch, the new address range appears.
- On the Security Gateway object where IP pool NAT translation is performed, Security Gateway Properties window, NAT page, IP Pools (for Security Gateways) section, select either (or both):
- Use IP Pool NAT for VPN client connections.
- Use IP Pool NAT for Security Gateway to Security Gateway connections.
- In the Allocate IP Addresses from field, select the address range you created.
- Decide after how many minutes unused addressees are returned to the IP pool.
- Click OK.
- Edit the routing table of each internal router, so that packets with an a IP address assigned from the NAT pool are routed to the appropriate Security Gateway.
Configuring Preferred Backup Security Gateway
In SmartDashboard:
- Click Manage > Remote Access > Connection Profiles.
- Select existing profile and click Edit or click New > Connection Profile.
The Connection Profile Properties opens.
- In the Connect to Security Gateway and Backup Security Gateway fields, use the drop down menu to select the Security Gateways that will function as the primary and backup Security Gateways for this profile.
- Click OK.
Disabling MEP
Disabling MEP is configured by setting the following command to true in , the Check Point database tool:
|
|


