Directional VPN Enforcement
Overview of Directional VPN
When a VPN community is selected in the VPN column of the Security Policy Rule Base, the source and destination IP addresses can belong to any of the Security Gateways in the community. In other words, the traffic is bidirectional; any of the Security Gateways can be the source of a connection, any of the Security Gateways can be the destination endpoint. But what if the administrator (in line with the company's security policy) wished to enforce traffic in one direction only? Or to allow encrypted traffic to or from Security Gateways not included in the VPN community? To enable enforcement within VPN communities, VPN implements Directional VPN.
Directional VPN specifies where the source address must be, and where the destination address must be. In this way, enforcement can take place:
- Within a single VPN community
- Between VPN communities
Directional Enforcement within a Community
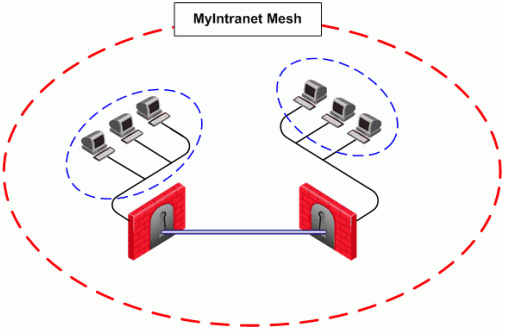
The figure shows a simple meshed VPN community called MyIntranet. VPN traffic within the MyIntranet Mesh is bidirectional; that is, either of the Security Gateways (or the hosts behind the Security Gateways in the VPN domains) can be the source or destination address for a connection.
Source
|
Destination
|
VPN
|
Service
|
Action
|
Track
|
Any
|
Any
|
MyIntranet => MyIntranet
MyIntranet =>internal_clear
internal_clear => MyIntranet
|
telnet
|
accept
|
log
|
Any
|
Any
|
MyIntranet
|
telnet
|
accept
|
log
|
The match conditions are represented by a series of compound objects. The match conditions enforce traffic in the following directions:
- To and from the VPN Community via VPN routing (MyIntranet => MyIntranet)
- From the Community to the local VPN domains (MyIntranet =>internal_clear)
- From the local VPN domains to the VPN community (internal_clear => MyIntranet)
Configurable Objects in a Direction
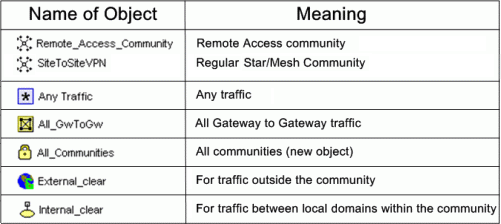
The table shows all the objects that can be configured in a direction, including three new objects created for Directional VPN:

|
Note - Clear text connections originating from the following objects are not subject to enforcement:
- Any Traffic
- External_clear
- Internal_clear
|
There is no limit to the number of VPN directions that can be configured on a single rule. In general, if you have many directional enforcements, consider replacing them with a standard bidirectional condition.
Directional Enforcement between Communities
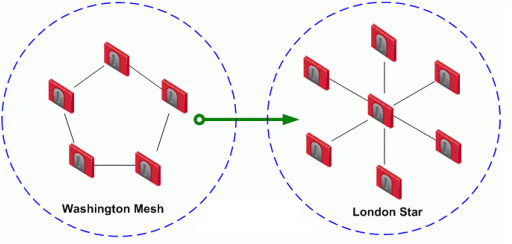
VPN Directional enforcement can take place between VPN communities. Consider two VPN communities, Washington and London:
Source
|
Destination
|
VPN
|
Service
|
Action
|
Any
|
Any
|
Washington => London
|
Any
|
accept
|
Washington is a Mesh community, and London is a VPN Star. In the VPN column of the Security Policy Rule Base, a directional VPN rule has been implemented. This means that for a VPN connection to match this rule, the source of the connection must be in the Washington Mesh, and the destination host must be within the London Star.
This does not mean that "return" or "back" connections are not allowed from London to Washington (the three-way handshake at the start of every TCP connection demands return connections), only that the first packet must originate within the Washington Mesh. If a host within the London Star tries to open a connection to a host in the Washington Mesh, the connection is dropped.
This directional enforcement does not affect the topology of either Washington or London. The enforcement can be thought of as taking place somewhere between the two communities.
Configuring Directional VPN Within a Community
To configure Directional VPN within a community:
- In Global Properties > VPN page > Advanced > Select Enable VPN Directional Match in VPN Column.
- In the VPN column of the appropriate rule, right-click on the VPN community. From the pop-up menu, select Edit Cell....
The VPN Match Conditions window opens.
- Select Match traffic in this direction only, and click Add...
The Directional VPN Match Condition window opens.
- In the Match on traffic reaching the Security Gateway from: drop-down box, select the object for internal_clear. (the source).
- In the Match on traffic leaving the Security Gateway to: box, select the relevant community object (the destination).
- Add another directional match in which the relevant community object is both the source and destination.
This allows traffic from the local domain to the community, and within the community.
- Click OK.
Configuring Directional VPN Between Communities
To configure Directional VPN between communities:
- In Global Properties > VPN page > Advanced > Select Enable VPN Directional Match in VPN Column.
- Right-click inside the VPN column of the appropriate rule. From the pop-up menu, select Edit Cell... or Add Direction...
The VPN Match Conditions window opens.
- Click Add...
The Directional VPN Match Conditions window opens:
- From the drop-down box on the left, select the source of the connection.
- From the drop-down box on the right, select the connection's destination.
- Click OK.
|


