Cooperative Enforcement
Cooperative Enforcement Solution
Cooperative Enforcement works with Check Point Endpoint Security servers. This feature utilizes the Endpoint Security server compliance capability to verify connections arriving from various hosts across the internal network.
Endpoint Security server is a centrally managed, multi-layered endpoint security solution that employs policy-based security enforcement for internal and remote PCs. Easily deployed and managed, the Endpoint Security server mitigates the risk of hackers, worms, spyware, and other security threats.
Features such as policy templates, an intuitive web-based management interface, and PC firewall and application privilege controls, enable administrators to develop, manage, and enforce Cooperative Enforcement quickly and easily.
Using Cooperative Enforcement, any host initiating a connection through a gateway is tested for compliance. This increases the integrity of the network because it prevents hosts with malicious software components from accessing the network.
This feature acts as a middle-man between hosts managed by an Endpoint Security server and the Endpoint Security server itself. It relies on the Endpoint Security server compliance feature, which defines whether a host is secure and can block connections that do not meet the defined prerequisites of software components.
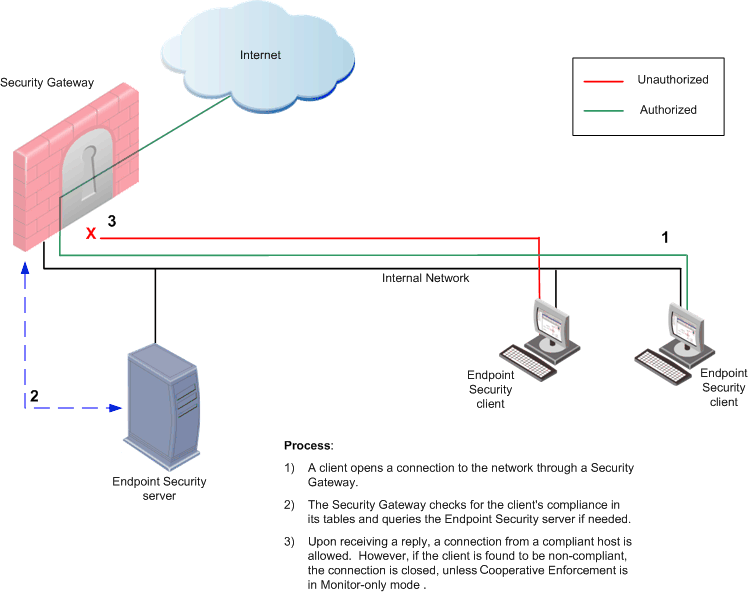
The following is a typical Cooperative Enforcement workflow:
- A host opens a connection to the network through a firewall gateway. The first packet from the client to the server is allowed. It is only on the first server's reply to the client that the Cooperative Enforcement feature begins to perform.
- The firewall checks for host compliance in its tables and queries the Endpoint Security server, if required.
- Upon receiving a reply, a connection from a compliant host is allowed, but if the Client is found to be non-compliant, the connection is closed unless this firewall feature is in Monitor-only mode.
For more in depth information about the Endpoint Security client and Cooperative Enforcement see the R76 Security Gateway Technical Administration Guide.
Enforcement Mode
In this mode, a non-compliant host's connection is blocked by the firewall's Cooperative Enforcement feature. If it is an HTTP connection, the host will get a notification page indicating that it is not compliant. The user will be able to perform the appropriate actions in order to become compliant. For example, in order to become compliant the user may upgrade the version of the Endpoint Security client.
Monitor Only Deployment Mode
In the monitor only deployment mode, hosts can connect while the firewall gateway grants authorization status. In addition, the firewall generates logs for unauthorized hosts. The administrator can either add unauthorized hosts to the host's exception list or perform the appropriate operations to make those hosts compliant.
The logs generated for both authorized and unauthorized hosts can be viewed in SmartView Monitor.
Non-Compliant Hosts by Gateway View
The SmartView Monitor Non-Compliant Hosts by Gateway view enables you to distinguish between Host IPs that have one of the following Endpoint Security server compliances:
- Authorized enables access to the Internet. If a gateway has an Authorized status it will not appear in the SmartView Monitor Non-Compliant Hosts by Gateway view.
- Unauthorized obstructs access to the Internet.
- No Endpoint Security client indicates that the gateway is not associated with an Endpoint Security client.
In addition, the SmartView Monitor Non-Compliant Hosts by Gateway view provides information about Host IPs with one of the following modes.
- Monitor Only indicates that an Endpoint Security client will have access to the Internet whether or not it is authorized.
- Blocked mode obstructs access to the Internet.
The figure below illustrates Endpoint Security client access to the Internet in association with the Gateway and Endpoint Security server.
Configuring a Cooperative Enforcement View
The following steps instruct you on how to run and read a Cooperative Enforcement view.
- In the Tree View select Cooperative Enforcement > Non-Compliant Hosts By Gateway.
The Select Gateway window appears.
- Select the gateway or cluster that you would like to review and select OK.
The information appears in the Cooperative Enforcement Results view.
- To refresh the view select the blue circular arrow on top of the Enforced On column.
The Cooperative Enforcement Results view contains the following information:
- Enforced On indicates the gateway associated with the information provided.
- IP indicates the specific gateway host.
- Action indicates the gateway mode (that is, Monitor Only or Blocked).
- Reason indicates the hosts Endpoint Security server compliance (that is, Unauthorized or No Endpoint Security client)
|

