Out of the Box
Default Deployment
The first stage of DLP deployment uses the Data Loss Prevention policy provided Out of the Box.
- Automatic inspection of data is based on built-in Check Point expert heuristics and compliance to various regulations.
- Users in your organization will transmit data as a part of their daily tasks. DLP will catch incidents that match rules of the policy. Rules in this stage will be set to Detect, allowing you to monitor usage and understand the specific needs of your organization without disrupting your users.
- You will audit the data, using experience-driven severity ratings, and SmartView Tracker tracking to find the key data leaks.
Data Loss Prevention in SmartDashboard
When you open the SmartDashboard to the Data Loss Prevention tab, these views are available.
|
|
Page
|
Function
|
Overview
|
Quick access to urgent tasks, commonly used features, and overview statistics.
|
Policy
|
Manage the rule base for Data Loss Prevention policy.
|
Gateways
|
Enable the Data Loss Prevention Software Blade on Check Point Security Gateways. You can define DLP gateways and Exchange Agents. An Exchange Agent lets you scan internal emails between Microsoft Exchange clients once you install the Exchange Security Agent on the Exchange Server. The table shows status, uptime, inspected items, version, CPU usage and comments for the gateways and Exchange Agents. You can see a graphical representation of this information in SmartView Monitor.
|
Data Types
|
Define representations of data assets to protect.
|
My Organization
|
Define the internal environment: networks, users, email addresses, and VPN communities.
|
Additional Settings:
|
Users
|
Define users, user groups, and AD/LDAP groups as network objects, to use in DLP and other Software Blades.
|
Network and Resources
|
Manage networks, hosts, servers, LDAP Account Units, and other network objects for use in DLP. Manage DLP and SmartDashboard administrators.
|
Protocols
|
Enable the protocols to be checked on individual DLP Gateways.
|
Mail Relay
|
Configure the mail server for DLP to send notification emails.
|
Email Addresses or Domains
|
Manage email address lists and domains for use in DLP rules and Data Types.
|
Advanced
|
|
Defining My Organization
The My Organization page shows what DLP recognizes as data movement in the internal network (where data leakage is not an issue) and what is external (where data transmission must be monitored).
By default, My Organization includes all hosts and networks that are behind the internal interfaces of the DLP gateway. My Organization also includes specific users, user groups, and all users in the LDAP groups defined in the Security Management Server.

|
Note - The SmartDashboard must be in the Active Directory domain to take advantage of the LDAP User List features.
|
Adding Email Addresses and Domains to My Organization
You define the DLP internal domains and specific email addresses that are included in My Organization. You can add domains to include your remote offices and branch offices as part of the definition of what is My Organization.

|
Important - If your organization uses cloud servers, you should not add them. The technology governing cloud servers makes them inherently insecure, taking the control of your data away from your administration and giving it to a third party. It is recommended to detect all sensitive data sent to and from cloud servers, rather than to trust a service provider to make sure that other clients do not have access to your data.
|
Add email addresses to include those that are safe for general data sharing. You should not add the private email addresses of any employees or managers. Taking home confidential data is a bad practice that you should discourage and eventually prevent.
Notes about Domains:
- When adding domains, do not use the @ sign. A valid domain example is:
example.com - If you add a domain, it will catch all sub domains as well. For example, if the domain is
example.com jsmith@uk.example.com - SMTP traffic is considered internal if the domain of the email is defined in My Organization and if the IP address of the sender is an interface/network defined in My Organization.

|
Important - Do not remove the default domain definition. You must have a domain in the My Organization definition, or an LDAP server defined. If you do not have the domain defined (either by Email Address Domain or LDAP Account Unit) for My Organization, DLP will not scan emails.
|
To add domains and email addresses to My Organization:
- In SmartDashboard, open the Data Loss Prevention tab.
- Click My Organization.
- In the Email Addresses area, enter a domain or specific email address.
- Click Add.
Defining Internal Users
Most organizations use an external LDAP server (for example, Active Directory) to manage users and user groups.
You can define an internal user account to use as a source or destination in the Rule Base when:
- Your organization does not use an LDAP server.
- You want to define a user that is not defined in the LDAP server.
You can add accounts for individual users from the Data Loss Prevention tab in SmartDashboard.
To define user accounts as internal users:
- Expand Additional Settings > Users.
- Click New > User.
The User Properties window opens.
- Define the user account.
The most important field is the email address. This lets DLP recognize the user for email scans.
The user is added to the other Software Blades managed by SmartDashboard.
Defining Internal User Groups
DLP may require different user groups than those in the LDAP server. For example, you may want a group for new employees, whose rules are set to Ask User rather than Prevent, to give them time to become familiar with the organization guidelines. You may also want a group for temporary employees or terminating employees, to give them stricter rules.
To define user groups:
- Expand Additional Settings> Users.
- Click New > User Group.
The Group Properties window opens.
- Name the group.
- Select the users, user groups, or external user profiles that you want in this group and click .
- Click OK.
Excluding Users from My Organization
If the default option for the Users area is selected (Users, user groups and LDAP groups defined in the Security Management Server), you can define exclusions to this definition of My Organization.
For example, you can exclude the CEO. This lets the CEO send any data without having it scanned.
To exclude users from My Organization:
- Open Data Loss Prevention > My Organization.
- In the Users area, click Exclusions.
The User groups and Users window opens.
- Select the listed items that you want to exclude from My Organization.
- Click Add.
- Click OK.
Defining Internal Networks
By default, My Organization includes networks, network groups, and hosts that are defined as being behind the internal interface of the DLP gateway.
If you choose to define My Organization by naming specific networks or hosts, any internal networks or hosts that you did not name will not be considered internal by DLP.

|
Note - The networks and hosts must already be defined in the Objects Tree of SmartDashboard.
|
To define specific networks and hosts:
- In SmartDashboard, open the Data Loss Prevention tab.
- Click My Organization.
- In the Networks area, select These networks and hosts only.
- Click Edit.
- In the Networks and Hosts window, select items from the list of defined networks and hosts and then click Add.
- Add as many items as needed to define My Organization.
- Click OK.
Excluding Networks from My Organization
In large sites it is often more efficient to define exclusions to the internal interfaces than to define the internal environment piece by piece.
If the default option in My Organization is selected (Anything behind the internal interfaces of my gateways), you can define exclusions to internal Networks.
Any network, network group, or host that you define as an exclusion will be recognized by Data Loss Prevention as Outside My Org. To scan data sent from these networks, you must change the default Source of rules from My Org to the network object.
To exclude networks from My Organization:
- Open Data Loss Prevention > My Organization.
- In the Networks area, click Exclusions.
The Networks and Hosts window opens.
- Select the listed items that you want to exclude from My Organization.
- Click Add.
- Click OK.
Defining Internal VPNs
If your Check Point deployment includes Virtual Private Networks, allow dynamic VPN traffic to be included in your My Organization definition.
A DLP gateway is aware of the VPN communities in which it participates. A dedicated DLP gateway for example, is aware of the VPN communities in which its protecting Security Gateway participates. Even if other VPNs are configured in your SmartDashboard, only those that are relevant to the DLP gateway are included in the DLP My Organization.
Remote Access communities in VPN of My Organization are supported only in Office Mode.
To configure Office Mode for support of Remote Access communities:
- If Office Mode IP addresses are assigned from IP pool, nothing further is required.
- If addresses are assigned from RADIUS, DHCP, or ipassigment.conf:
- Open the properties of the gateway > IPSec VPN.
- Open Office Mode.
- Select Perform Anti spoofing on Office Mode addresses.
- Enter the IP address range.
To include VPN traffic in My Organization:
- In SmartDashboard, open the Data Loss Prevention tab.
- Click My Organization.
- In the VPN area, make sure the All VPN traffic checkbox is selected.
Excluding VPNs from My Organization
VPNs provide an encrypted tunnel between sites. If you have multiple VPNs in your deployment, you might want to exclude some from the My Organization definition.
For example, if you have a VPN with a third party, such as a business partner, you can configure a VPN community that joins the organizations together. All traffic between the two organizations would be seen as internal by the VPN gateway of each office. However, if you want DLP to prevent confidential data being passed to the business partner, you could exclude the VPN from My Organization and thus control the type of data that is passed.
Before you make this decision, you should know which VPNs defined in your SmartDashboard are relevant to the DLP gateway.
DLP can see only the VPNs in which its protecting VPN gateway participates. All defined gateways are listed in the VPN Communities window in which you define exclusions; but only the relevant VPNs can be manually excluded. The others are always excluded and cannot be included.
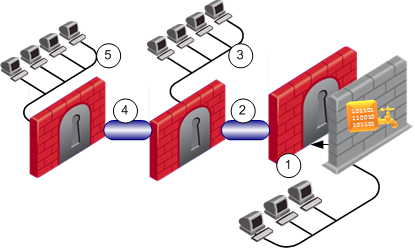
The organization behind the DLP gateway is protected by a VPN gateway (1). This gateway participates in a VPN community (2). Therefore, DLP sees the remote hosts in the VPN (3) as part of My Organization.
The protecting VPN gateway does not participate in the VPN community between the other sites (3 and 5), and is not aware of the VPN between them (4). Therefore, DLP considers the hosts in site 5 as external to My Organization.
To discover VPNs known to DLP:
- Find the protecting VPN gateway of the DLP gateway.
For an integrated DLP deployment, this is the DLP gateway itself. The protecting VPN gateway includes the IP address of the DLP gateway in its encryption domain.
- Double-click the VPN gateway in the Network Objects tree, to open the gateway properties.
- Open the IPSec VPN page.
The DLP gateway is aware of the VPN communities that are listed in the IPSec VPN page of the protecting VPN gateway.
To exclude VPNs from My Organization:
- Open the Data Loss Prevention tab > My Organization.
- In the VPN area, click Exclusions.
The VPN Communities window opens.
- Select the VPNs that you want to exclude from My Organization and click Add.
Ignore the VPNs that are not relevant to the protecting VPN gateway; they are excluded by default.
Data Loss Prevention Policies
The DLP policy defines which data is to be protected from transmission, including: email body, email recipients, email attachments (even if zipped), FTP upload, web post, web mail, and so on. The policy determines the action that DLP takes if a transmission is captured.
Manage the rules of the policy in the Data Loss Prevention > Policy page.
Overview of DLP Rules
A Data Loss Prevention rule is made up of:
- A Data Type to protect - some Data Types are complex, others are as simple as one word. You can make your rule base as long as needed.
- A transmission source - by default, your entire internal organization (the policy will check all data transmissions coming from any user in your organization containing the defined Data Type), or a selected user, group, segment, or network. It is recommended that you create user groups for data access. For example: users with access to highly sensitive data, newly hired employees, employees on notice of termination, managers with responsibilities over specific types of data.
- A destination - by default, anything that is outside of the internal organization. You may choose to make the destination any network object defined in the SmartDashboard to protect data transfer between groups of users inside your organization. You can make the destination a specific domain, such as Gmail or Hotmail for private emails.
- A protocol - by default Any, but you can choose to have the rule apply only to HTTP posts, or only to FTP uploads. To view the protocol column, right-click the heading line of the policy and select Protocol.
- An action to take - DLP response if a data transmission matches the other parameters of the rule: detect and log, inform sender or data owner, delay until user decides, or prevent the transmission.
- A tracking option - when data transmissions match Data Loss Prevention rules, they are logged as incidents in SmartView Tracker by default. You can add email notifications here and other tracking methods.
- A severity level - set the severity of the rules in your policy, to help in filtering and reporting while auditing Data Loss Prevention incidents through SmartEvent. High and Critical rules should be the first that you audit and, if you decide to keep this severity level, they should be moved from to as soon as your users understand what is expected of them.
- A time range - a period of time during which the DLP rule is enforced.
The rule base of the DLP gateway should look familiar if you have experience with the Check Point Firewall rule base, but there are differences.
- DLP rules are based on Data Types, created through an easy-to-use wizard. Protocols (services) used to transmit data and the people who transmit data are secondary, defining issues.
- DLP rules usually scan communications from the internal organization going out. Firewall rules usually scan communications from outside coming into the internal network.
- The method that DLP rules match data is different.
DLP and Identity Awareness
When Identity Awareness is enabled, you can create access role objects and use them in the DLP policy. When Identity Awareness is enabled, in DLP:
- Emails notifications can be sent when DLP violations occur using the FTP or HTTP protocols. (Before R76, DLP email notifications were only sent when the violation occurred on the SMTP protocol.)
- Access role objects can be used in the Source or Destination column of a DLP rule.
- The Action column of a DLP rule can redirect unknown users to the Identity Captive Portal for authentication.
- SmartEvent, SmartLog and SmartView Tracker logs identify users that violate the DLP policy.
Email Notifications for FTP and HTTP DLP violations
In addition to email notifications on SMTP DLP violations, you can configure notifications to be sent when the violation occurs using the FTP or HTTP protocols. To send these notifications, you must:
- Enable Identity Awareness.
- In , select:
When you select or in the area, the and options are also selected in the area. This lets DLP learn how the user decides to handle a DLP incident and apply the same decision for subsequent messages.
Access Roles in the Source or Destination of a Rule
Access role objects can be used in the Source or Destination column of a DLP rule. The presence of access roles makes DLP user aware. The access role object identifies users, computers, and network locations as one object. You can select specified users, user groups, or user branches as the object.
Redirection to an Authentication Captive Portal
Captive Portal redirection only applies to the HTTP and HTTPS protocols. Redirection occurs when the sender is unknown (the IP address does not map to any user in the AD) and the of the DLP rule is and one of these conditions is also met:
- No access role objects are in the or column of the policy rule but the and do match those of the HTTP connection being examined by the DLP gateway.
- The column of the DLP rule contains an access role.
Redirecting to the Captive Portal lets DLP:
To Redirect HTTP traffic to the Captive Portal:
- Right-click the Action and select Identity Captive Portal.
- Select Redirect HTTP connections to an authentication Captive Portal.
- Click OK.
The Action column shows Identity Captive Portal.
Identifying Users Behind a Proxy
If your organization uses an HTTP proxy server behind the gateway, the identities of users behind the proxy will remain hidden unless you configure:
- The company proxy server to use an X-Forwarded-For HTTP Header
- The DLP gateway to use the X-Forward-For HTTP header.
You can also configure the DLP gateway to strip the X-Forward-For header in outgoing traffic. Without the header, internal IP addresses are not be shown in requests to the internet.
To use X-Forwarded-For HTTP header:
- Configure your proxy server to use X-Forwarded-For HTTP Header.
- In SmartDashboard, on the I page of the DLP gateway object, select .
- To configure the DLP gateway to stop the X Forwarded-For header showing internal IP addresses in requests to the internet, select .
- Install the policy.
Example DLP rule with Identity Awareness
These three rules show how Identity Awareness works with DLP:
Rule 1
Data
|
Source
|
Destination
|
Protocol
|
Action
|
PCI – Credit Card Numbers
|
Finance_Dept
(Access Role)
|
Outside My Org
|
Any
|
Prevent
|
In this rule:
- Access role objects are used in the Source column. This rule will prevent a known user in the Finance department from sending credit numbers outside of the organization. Known users that are not listed in the access role will not be prevented from sending credit card numbers outside of the organization.
- An unknown user (a computer with an IP address that is not mapped to any user in the Active Directory) attempting to send credit card numbers outside of the organization will not be stopped by this rule.
- A user that is known but not part of the access role will not be prevented from sending credit card numbers.
- There is also no redirect to the Captive Portal so that the unknown sender cannot be identified.
Rule 2
Data
|
Source
|
Destination
|
Protocol
|
Action
|
PCI – Credit Card Numbers
|
My Organization
|
Outside My Org
|
Any
|
Prevent
Identity Captive Portal
|
In this rule:
- Known users inside the organization will be prevented from sending out credit card data, and receive email notification of the policy violation.
- Unknown users inside the organization sending out all types of data will be directed to the Captive Portal for identification. Once identified, DLP scans the data for a possible violation.

|
Note - Enabling Identity Captive Portal on this rule means that HTTP or HTTPS connections passing from inside to outside of the organization must be identified with a user.
|
Rule 3
Data
|
Source
|
Destination
|
Protocol
|
Action
|
PCI – Credit Card Numbers
|
Finance_Dept
(Access Role)
|
Outside My Org
|
Any
|
Prevent
Identity Captive Portal
|
In this rule:
- A known user in the Finance department will be prevented from sending credit numbers outside of the organization.
- An access role in the Source (plus Captive Portal in the Action column) means that for HTTP connections there is a redirect if the source user is unknown and the destination matches the destination specified by the policy
- A user that is known but not part of the access role will not be:
- Prevented from sending out credit card numbers
- Redirected to the Captive Portal.
DLP Rule Matching Order
The DLP rule order does not matter. In this rule base, each transmission is checked against each rule.
Because the rule order does not matter, you can change the display of the DLP policy for your convenience.
- To show rules in a different order, click a column header. The rules are sorted by the selected column.
- To show rules in groups, select an option from the Grouping menu in Data Loss Prevention > Policy.
- To show or hide columns, right-click the policy column header and select an item.
- To change the arrangement of columns, drag a column to a new position.
DLP Rule Matching with Exceptions
If data matches a rule, and the rule has exceptions, the exceptions to a rule are checked. If the data matches any exception, DLP allows the transmission.
For example, consider a rule that captures emails containing more than fifteen employee names in the body of a message. If a user in the HR department sends a list of twenty employees to an outside address (such as their contractor), the email will be allowed without incident logging or any Data Loss Prevention action taken - because the same rule has an exception that allows users in the HR group to send lists of employee names outside your organization.
If the data matches multiple rules, one with an exception and one without exceptions, the rule without exceptions is used.
DLP Rule Matching with Multiple Matches
If the data matches multiple rules, the most restrictive rule is applied.
For example, if a user sends an email with an attached unencrypted PDF, the email can match two rules. One rule is : detect emails to an external destination that contain PDF files. A second rule is : delay emails with PDF files that are unencrypted, until the user specifies that it is good to send. An administrator with full permissions or the View/Release/Discard DLP messages permission can also send/discard this mail from SmartView Tracker. This rule will also inform the Marketing and Technical Communications manager that the PDF was released from the company to an external destination.
In this case:
- The email is quarantined.
- The user gets a notification and has to make a decision relating to what to do.
- The data owner gets a notification.
- The rule violations (one for and one for ) are logged.
- An administrator can send/discard this email from SmartView Tracker. Notification is sent to the user.
Rule Actions
For each DLP rule that you create for a Data Type, you also define what action is to be taken if the rule matches a transmission.
Action
|
Description
|
Detect
|
The transmission is passed. The event is logged in SmartView Tracker and is available for your review and analysis in SmartReporter and SmartEvent. The data and the email itself, or the properties of the transmission if not email, are saved in storage for future reference.
You can choose to notify Data Owners of the event.
This is true for all the following actions as well.
|
Inform User
|
The transmission is passed, but the incident is logged and the user is notified.
|
Ask User
|
The transmission is held until the user verifies that it should be sent. A notification, usually with a remediation link to the Self Incident Handling portal, is sent to the user. The user decides whether the transmission should be completed or not. The decision itself is logged in SmartView Tracker under the User Actions category.
Administrators with full permissions or with the View/Release/Discard DLP messages permission can also decide whether the transmission should be completed or not from SmartView Tracker. This can be useful in the event that a user is not available to make sure if it should be sent.
|
Prevent
|
The data transmission is blocked.
Note: Check Point does not recommend using the Prevent action as a first choice. The action may prove disruptive. To improve the accuracy of rule matches, set rules to Prevent only when you have tested them with the less strict actions over a reasonable amount of time.
|
Watermark
|
Tracks outgoing Microsoft Office documents (Word, Excel, or PowerPoint files from Office 2007 and higher) by adding visible watermarks or invisible encrypted text.
- By default, all rules are created without a watermark action.
- Watermarks can be created and edited without having to apply them.
- Once a watermark object is created, it can be reused in multiple rules.
|

|
Note - If data matches multiple rules, the rule of the most restrictive action is applied. The order from most restrictive to least is: Prevent, Ask User, Inform User, Detect.
|
Managing Rules in Detect
The Detect action is set to rules by default because it is the least disruptive of the action options. When Data Loss Prevention discovers a transmission containing protected data, an incident is logged in SmartView Tracker and other logging actions (if any) are taken.
You might want to leave all your rules in Detect at first. Then you can review the logs and decide which rules are needed according to your organization's actions. This could save you and your users a lot of time and make your explanations of what they need to know and what to do much more specific to their needs.
Setting Rule Tracking
A primary consideration for creating Data Loss Prevention rules is how to audit incidents.
In the rule base of the Data Loss Prevention policy, the column offers these options:
Option
|
Meaning
|
|
|
Sends an email to a configured recipient
|
|
|
Records the incident in SmartView Tracker or SmartEvent. (All the other tracking options also log an incident.)
|
|
|
Opens a pop-up window in the SmartView Monitor.
|
|
|
Sends an SNMP alert to the SNMP GUI. This uses the fwd process, to run the internal_snmp_trap
|
|
|
Sends one of three possible customized alerts. The alerts are defined by the scripts specified in Policy > Global Properties > Log and Alert > Alert Commands. The alert process on the Log server runs the scripts.
|
|
|
Determines how the data should be stored and deleted (if at all). The options are:
- Yes
- Only as text
- Don't store (depending on other conditions)
- Delete
|
Store Incident
tracking options determine how data that matches a DLP rule is stored (or not stored). These options are available:
Store Option
|
Meaning
|
|
|
- Email data is stored as an
.eml - FTP data is stored in the
.zip - HTTP
- Text entered onto a web page is saved as HTML and viewed in the default browser when the data is opened through a link in SmartView Tracker or SmartEvent.
- An uploaded file is stored in the
.zip
Note: For FTP and HTTP, only those elements of the message that violate DLP rules are stored.
|
|
|
- Textual data extracted from the email (header and body) and the attachment is stored as HTML, but only those sections that triggered the violation.
- FTP data is stored in the
.zip - HTTP
- Text entered onto a web page is saved as HTML and viewed in the default browser when the data is opened through a link in SmartView Tracker or SmartEvent.
- An uploaded file is stored in the
.zip
Note: For FTP and HTTP, only those elements of the message that violate DLP rules are shown in the HTML page presented by SmartView Tracker or SmartEvent.
|
|
|
When the rule is matched, the incident is logged and the data deleted so that it cannot be viewed in SmartView Tracker or SmartEvent.
Note: The deletion of the data can be prevented by other store options. If a scanned message matches a number of store incident options, the option with highest priority has precedence:
Store Incident option
|
Priority
|
|
|
1
|
|
|
2
|
|
|
3
|
|
|
4
|
|
|
|
Logs the incident and immediately deletes the data. Select this example for sensitive data such as credit card numbers.
Note: If the email that contains the sensitive data also has an attachment that must be watermarked, the email is not deleted. The email is saved but cannot be viewed using SmartView Tracker or SmartEvent.
|
Resolving Store Incident Conflicts
If a scanned message matches a number of different DLP rules, and each rule has a different store option, the option with highest priority has precedence. For example, if an email matches these rules:
Rule
|
Store Incident Option
|
Priority
|
Rule_1
|
|
3
|
Rule_2
|
|
2
|
Rule_3
|
|
4
|
The store incident option related to Rule_2 has the highest priority. The data will be stored even though the email matched a rule (Rule_3) configured to delete the data.
Changing the Priority
The store option can be configured to have a higher priority than To change the priority:
- On the gateway, open:
$DLPDIR/config/dlp.confEach message protocol has its own section. For example:
)
:ftp (
:enabled (1)
:maximum_words_to_log (14)
:maximum_chars_to_words_in_log (490)
:cleanup_session_files (1)
:save_incident_quota_percentage (85)
:allow_append_cmd (0)
:view_incident_dispute_option (yes)
)
|
- Search for:
view_incident_dispute_optionThe default value is Yes.
- For all protocols (SMTP, FTP, HTTP), change
YesText - Save and close
dlp.conf
Setting a Time Restriction
The column in the DLP Rule table holds a time object or group of time objects. The time object is the same time object as used in the Firewall Rule Base.
- A time object defines:
- A time period during which the DLP rule is enforced (in hours) or
- A time period defined by activation and expiration dates.
- Time objects apply for each rule.

|
Notes -
- A DLP rule that incorporates a time object will not be enforced once the time object expires.
- Time objects are not supported for UTM-1 Edge appliances and QoS. Installing a DLP policy that contains a time object in a rule will result in failure.
- An object that does not have an activation or expiration date is always active.
|
To create a time object:
- Open the tab > page.
- Right click in the column of a rule.
- From the pop-up menu, select .
A window opens showing a list of existing time objects. You can select an existing time or create a new one.

|
Note - Existing time object can be reused.
|
- Click .
- The window opens.
- On the page, enter a name for the object
- On the page:
- In the section, configure when the time object activates and expires.
- In the section, specify up to 3 ranges when the time object enforces the DLP rule. During these periods, the related DLP rule is enforced. The time specified here refers to the local time on the Security Gateway.
- .
The days when the time object enforces the DLP rule. The time object can be enforcing the DLP rule each day, specified days of the week, a specified month or all months.
- Click .
If you have more than one time object, you can merge them into a group. When a condition in one of the time objects in the group is met, the DLP rule is enforced.
To create a time group object:
- Open the tab > page.
- Right click in the column of a rule.
- From the pop-up menu, select .
The window opens.
- Enter a name for the group.
- or time objects from the group.
- Click .
Supported Archive Types
The DLP blade supports the extraction and scanning of these compressed archive types:
- zip
- zip-exe
- gzip
- rar
- tar
- jar
- 7z
Selective Deployment - Gateways
For any rule in the policy, you can choose that it be deployed on specific Enforcing Gateways.
To deploy a rule on specific Enforcing DLP Gateways:
- In SmartDashboard, open Data Loss Prevention > Policy.
- In the rule you want, click in the plus in the Install On column.
Defined DLP Gateways appear in a menu.
- Select the Gateways on which you want this rule to be deployed.
- Run Install Policy on the DLP gateway.
Selective Deployment - Protocols
Check Point Data Loss Prevention supports various data transmission protocols.
It is recommended that you enable protocols as needed in your deployment. Start with only SMTP. Observe the logs on detected emails and user actions for handling them. Later, add FTP to the policy. For emails and large uploads, users do not expect instant responses. They can handle incidents in the Portal or UserCheck client for emails and uploads without disturbing their work, especially if your users know what to expect and how to handle the incidents.
HTTP, which includes posts to web sites, comments on media sites, blogging, and web mail, is another matter. Users do expect that when they press Enter, their words are sent and received instantly. If an employee uses HTTP for mission-critical work, having to decide whether a sentence is OK to send or not every instance is going to be extremely disruptive. Therefore, it is recommended that you enable HTTP only after you have run analysis on usage and incidents.
You can also enable inspection for Exchange Agent emails and the HTTPS protocol.
To select protocol deployment for all gateways:
- In SmartDashboard, open Data Loss Prevention.
- Expand Additional Settings and click Protocols.
- Clear the checkbox of any of the protocols that you do not want to inspect.

|
Important - If you clear all of the protocol checkboxes, Data Loss Prevention will have no effect.
|
To select protocol deployment per gateway:
- In SmartDashboard, open the Firewall tab.
- In the Network Objects list, double-click the gateway.
The properties window of the gateway opens.
- In General Properties > Software Blades > Network Security, make sure Data Loss Prevention is selected.
- Open the Data Loss Prevention page.
- In the Protocols area, select one of the following:
- Apply the DLP policy on the default protocols - as selected in the Data Loss Prevention tab, according to the previous procedure.
- Apply the DLP policy to these protocols only - select the protocols that you want this gateway to check for the Data Loss Prevention policy.
Auditing and Analysis
In the process of Data Loss Prevention, analysis of incidents is essential.
Before you begin, make sure that the severity of rules in the policy is accurate.
While auditing rules with SmartView Tracker and SmartEvent, use the Follow Up flag. If you find an incident or a set of incidents that you want to fine-tune, or for which you doubt whether the action is best, you can set the Data Type or the rule to Follow Up.
The Overview page of Data Loss Prevention in SmartDashboard provides a quick link to Data Types and rules that are marked for Follow Up.
Using SmartView Tracker
The DLP gateway issues logs for various events.
To open SmartView Tracker:
- In SmartDashboard, select SmartConsole > SmartView Tracker.
- In the Network & Endpoint tab, select Predefined > Data Loss Prevention Blade.
The Data Loss Prevention logs are categorized for filtering.
To see more information:
- Double-click an item in the log window.
The Record Details window opens.
- Click DLP Log.
The DLP Record Details window opens, displaying more information about the incident in an easy-to-read format, with links back to the Data Loss Prevention tab in SmartDashboard or to specific information on the Data Type.
From the log of a specific incident you can open the actual data that caused the incident. You should not have to review most of the incidents manually, but the original transmission (for example, the email or its attachment) is kept for you if there is a question from the sender or the data owners.
Because personal emails and web posts may be captured and stored for viewing, you must let the users know that this may happen. Failure to do so may cause your organization issues with local privacy laws.

|
Note - To view DLP incidents in the SmartView Tracker or SmartEvent SmartConsole application on a Windows 7 computer, Microsoft Office 2010 is required. DLP incidents may not show if the incidents (which are in EML file format) are associated with any other application.
|
DLP Actions
SmartView Tracker actions for DLP incidents include:
DLP Action
|
Description
|
Ask User
|
DLP incident captured and put in Quarantine, user asked to decide what to do.
|
Do not Send
|
User decided to drop transmission that was captured by DLP. An administrator with full permissions or with the View/Release/Discard DLP messages permission can also drop these transmissions. Email notification is sent to the user.
|
Send
|
User decided to continue transmission after DLP notified that it may contain sensitive data. An administrator with full permissions or with the View/Release/Discard DLP messages permission can also decide to continue transmission. Email notification is sent to the user.
|
Quarantine Expired
|
DLP captured data transmission cannot be sent because the user did not make a decision in time. Expired incidents may still be viewed, until they are deleted (routine cleanup process).
|
Prevent
|
DLP transmission was blocked.
|
Allow
|
DLP transmission was allowed; usually by exception to rule.
|
Inform User
|
DLP transmission was detected and allowed, and user notified.
|
Deleted Due To Quota
|
DLP incidents are deleted from gateway for disk space.
|
DLP General Columns
DLP incidents can show some or all of these columns and are available to all administrators.
DLP Columns
|
Description
|
Incident UID
|
Unique ID of the incident.
|
DLP Action Reason
|
Reason for the action. Possible values: Rule Base, Internal Error, Prior User Decision
|
Related Incident
|
Internal incident ID related to the current log.
|
DLP Transport
|
Protocol of the traffic of the incident: HTTP, FTP, Email.
|
Using the Incident UID as a key between multiple logs:
Each DLP incident has a unique ID included in the log and sent to the user as part of an email notification. User actions (Send, Do not Send) are assigned the same Incident UID that was assigned to the initial DLP incident log.
If a user/administrator sends an email with a DLP violation and then decides to discard it, two logs are generated. The first log is a DLP incident log with action and is assigned an Incident UID. On the user action, the second log is generated with the same UID, with the Do not Send action.
Each matched Data Type generates its own log. The gateway makes sure that all the Data Type logs of one incident show the same unique Incident UID and rule action (Prevent, Ask, Inform, or Detect). This happens also if Data Types were matched on different rules. The same action shown for an incident is the most restrictive.
For example, in a case that a transmission matches two Data Types. Each Data Type is used in a different rule. The action of one rule is Prevent. The action in the second rule is Detect. The two logs that are generated will show Prevent as the action. The action implemented will be Prevent. The log of the Detect rule will show Rule Base in the column.
DLP Restricted Columns
These columns are restricted to administrators with permissions.
Restricted Filters
|
Description
|
DLP Rule Name
|
Name of the DLP rule on which the incident was matched.
|
DLP Rule UID
|
Internal rule ID of the DLP rule on which the incident was matched.
|
Data Type UID
|
Internal ID of the Data Type on which the incident was matched.
|
Data Type Name
|
Name of the matched Data Type.
|
User Action Comment
|
Comment given by user when releasing the incident from the Portal.
|
DLP Recipients
|
For SMTP traffic, list of recipients of captured email.
|
Scanned Data Fragment
|
Captured data itself: email and attachment of SMTP, file of FTP, or HTTP traffic.
|
Message to User
|
Message sent, as configured by administrator, for the rule on which the incident was matched.
|
DLP Categories
|
Category of Data Type on which the incident was matched.
|
DLP Words List
|
If the Data Type on which the incident was matched included a word list (keywords, dictionary, and so on), the list of matched words.
|
Mail Subject
|
For SMTP traffic, the subject of captured email.
|
Using SmartEvent
SmartEvent provides advanced analysis tools with filtering, charts, reporting, statistics, and more, of all events that pass through enabled Security Gateways. SmartEvent combines all DLP logs of the same incident (all matching rules and Data Types and user action if applicable) to a single event.
You can filter out the specific Data Loss Prevention information for efficient monitoring and relevant reporting on DLP incidents.
- Real-time and history graphs and reports of Data Loss Prevention incidents
- Graphical incident timelines for rapid information retrieval
- Easily configured custom views to quickly answer specific queries
- Incident management workflow
- Reports to data owners on a scheduled basis
To open SmartEvent:
- In SmartDashboard, select Window > SmartEvent.
- When SmartEvent is open, open Events.
- Select Predefined > DLP or any of the analysis data categories under DLP.
|
|


