Incidents - Attack Map
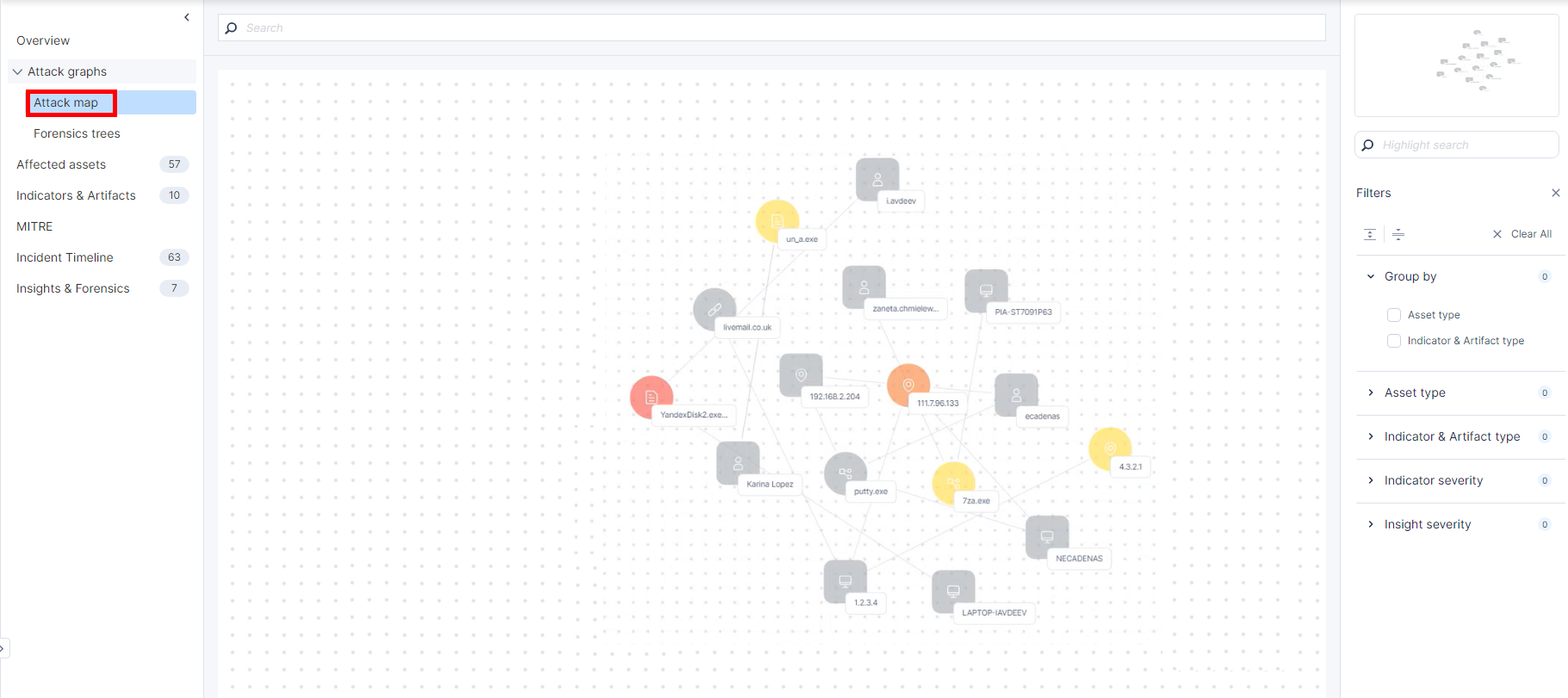
An Attack map shows the connections between assets and their associated artifacts and indicators in an incident.
To view the Attack map of an incident:
-
Access the Infinity XDR
 Extended Detection & Response/XPR
Extended Detection & Response/XPR Extended Prevention & Response Administrator Portal and click Incidents > Incidents.
Extended Prevention & Response Administrator Portal and click Incidents > Incidents. -
Click the incident title or hover over the incident and click >.
-
Click Attack graphs > Attack map.
Reading an Attack Map
Legend
|
Item |
Description |
||
|---|---|---|---|
|
|
Asset |
||
|
|
Artifact
|
To view the attack map of an asset:
-
Click the asset.
The system highlights all the artifacts and indicators connected to the asset.
You can drag and re-arrange the asset and the connected artifacts/indicators to view their connection in detail.
-
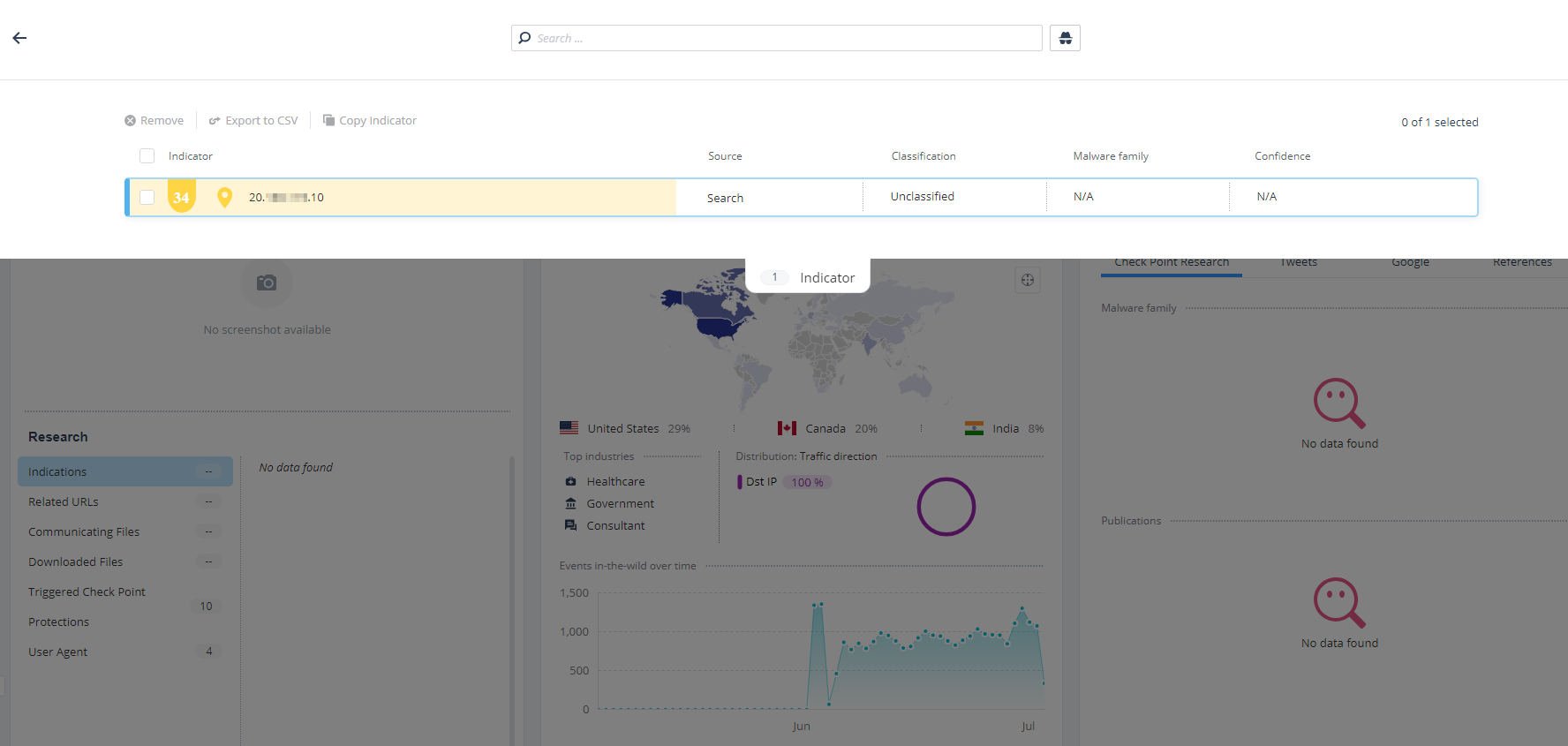
To view the artifact details, hover over it.
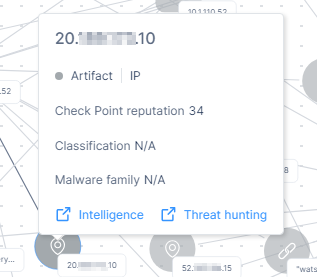
The card shows:
-
Check Point reputation score of the artifact.
-
Threat classification of the artifact (when available)
-
Malware family of the artifact (when available)
-
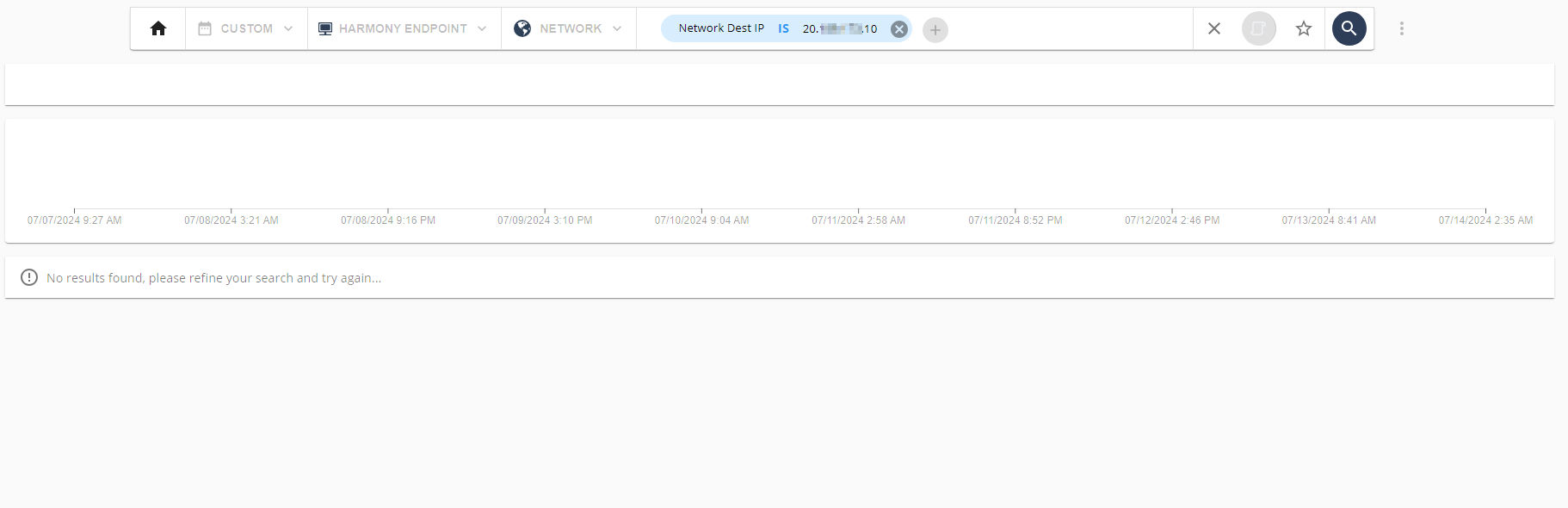
To view the Intelligence information about the artifact, click Intelligence. The system opens the Intelligence page and shows the data filtered by the artifact's IP address.
-
To view the Threat Hunting information about the artifact, click Threat hunting. The system opens the Threat Hunting page and shows the data filtered by the artifact's IP address.
-
-
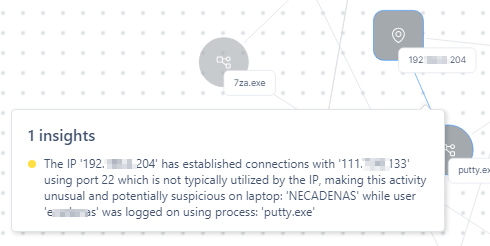
To view the insight summary of the connection, hover over the link.
-
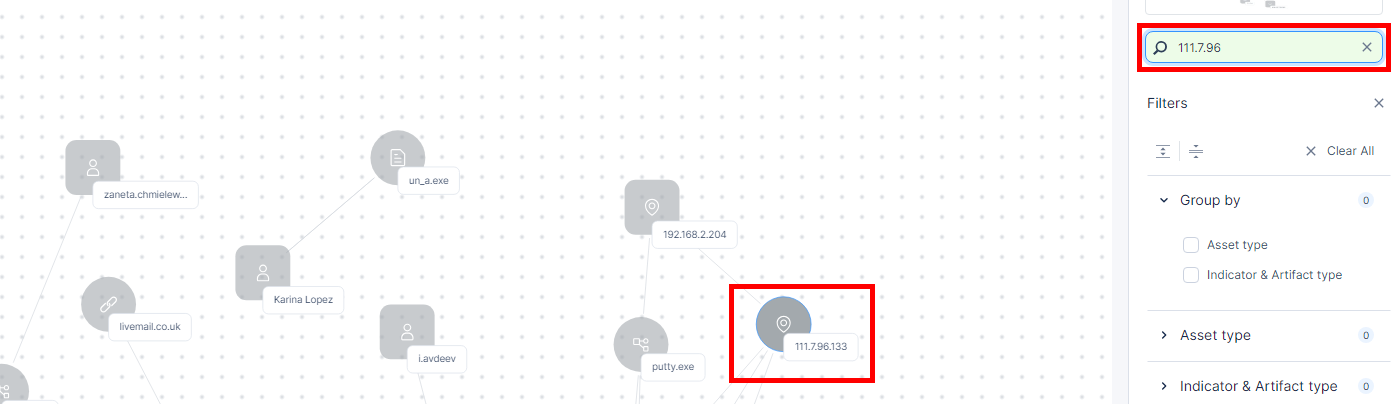
To find an asset, artifact or indicator on the attack map, on the right pane, in the Highlight search field, enter the value.
The system highlights the node on the map.
-
To search and view only the nodes connected to the searched value, enter the value in the Search field at the top.
-
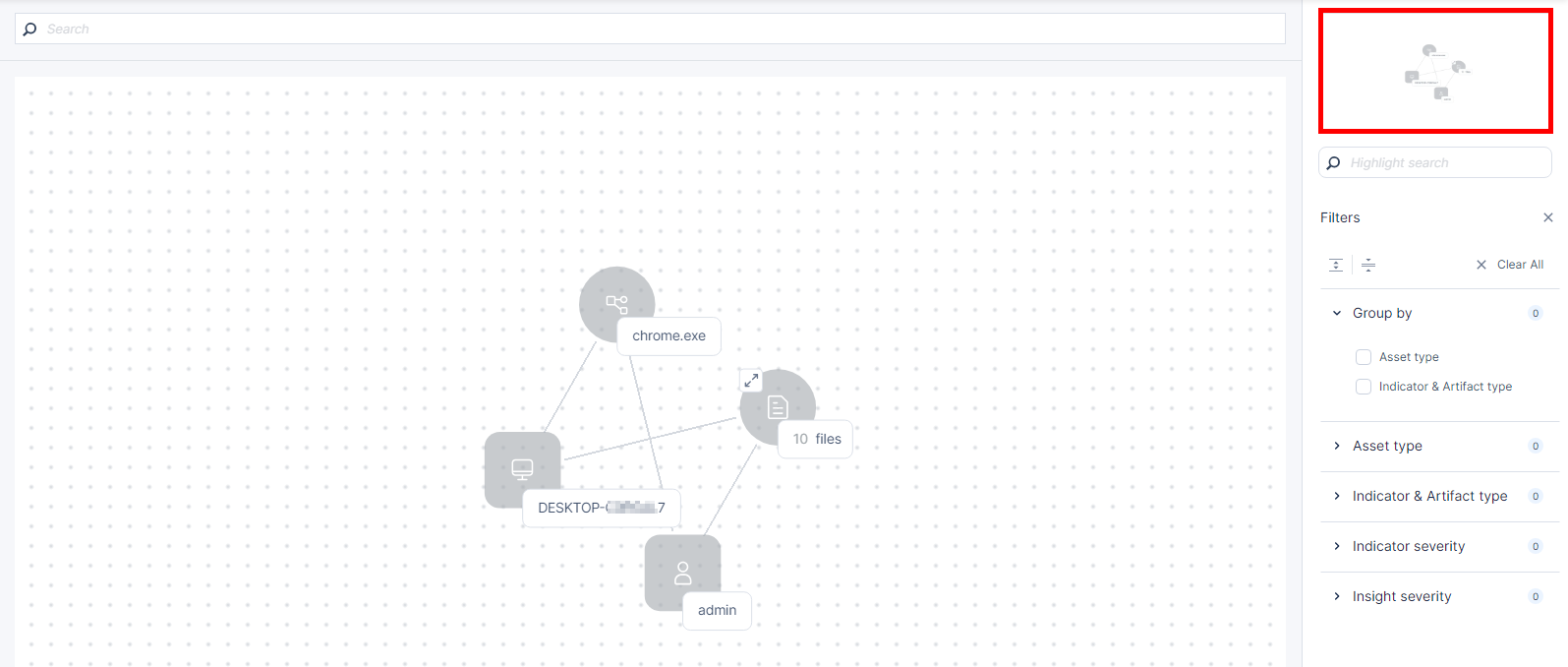
To view a miniature version of the attack map, see the mini-map at the top-right corner.
Filtering an Attack Map
You can filter an Attack map by:
-
Groups
-
By Asset type:
-
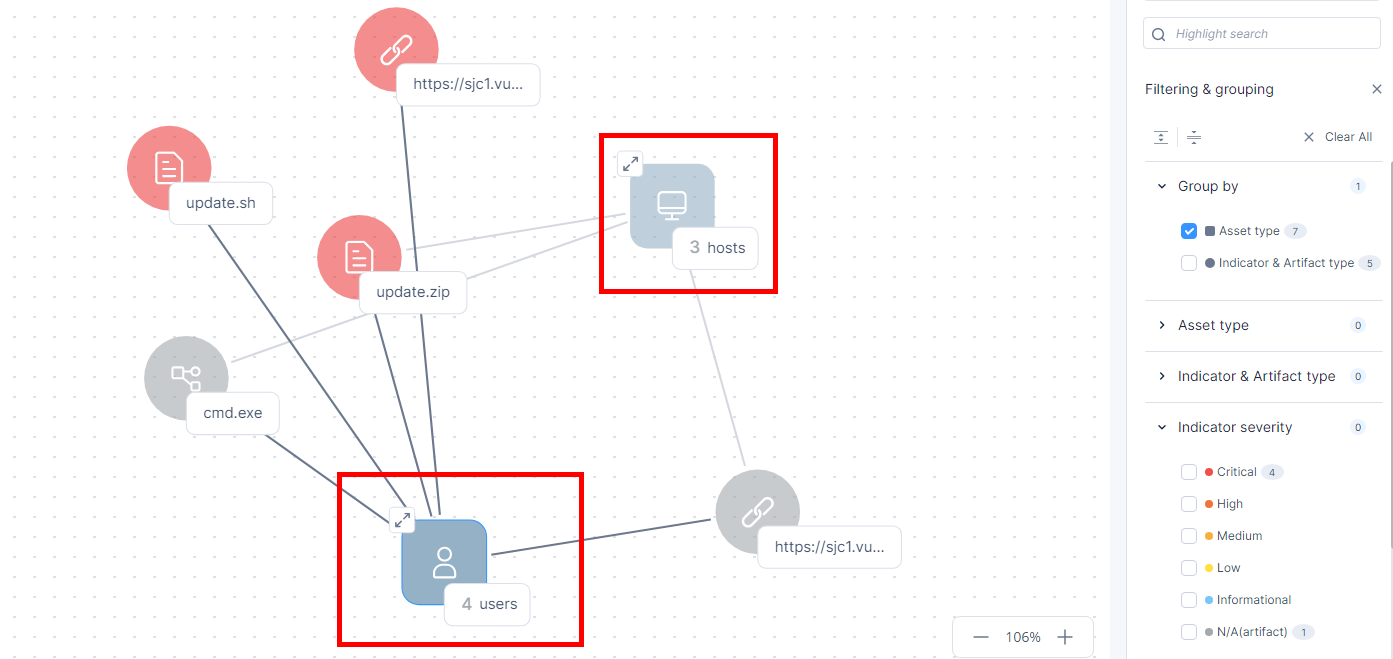
In the Group by section, select the Asset type checkbox.
The system shows the attack map grouped by asset type.
-
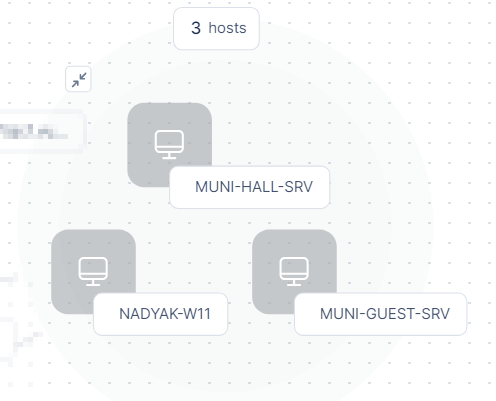
To view the assets in a group, click the
 icon or the grouped node.
icon or the grouped node. -
To go back to the grouped view, click
 or click anywhere within the group.
or click anywhere within the group. -
By Indicators and Artifacts type:
In the Group by section, select the Indicator & Artifact type checkbox.
The system shows the attack map grouped by indicator/artifact type.
-
-
Asset type
-
Machine
-
User
-
IP Address
-
-
Indicator and Artifact type
-
Registry
-
Process
-
URL
-
IP Address
-
File
-
-
Indicator severity
-
Critical
-
High
-
Medium
-
Low
-
Informational
-
N/A (artifact)
-
-
-
Critical
-
High
-
Medium
-
Low
-
Informational
-