Intelligence
The Intelligence page shows the intelligence available for an indicator derived from internal (Check Point's ThreatCloud, Research and Threat Emulation![]() Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. services) and external sources (reliable closed and open third-party feeds). On this page, you can also upload a file to Check Point's Threat Emulation Sandbox for analysis.
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. services) and external sources (reliable closed and open third-party feeds). On this page, you can also upload a file to Check Point's Threat Emulation Sandbox for analysis.
To view the Intelligence page, access the Infinity XDR![]() Extended Detection & Response/XPR
Extended Detection & Response/XPR![]() Extended Prevention & Response Administrator Portal and click Intelligence.
Extended Prevention & Response Administrator Portal and click Intelligence.
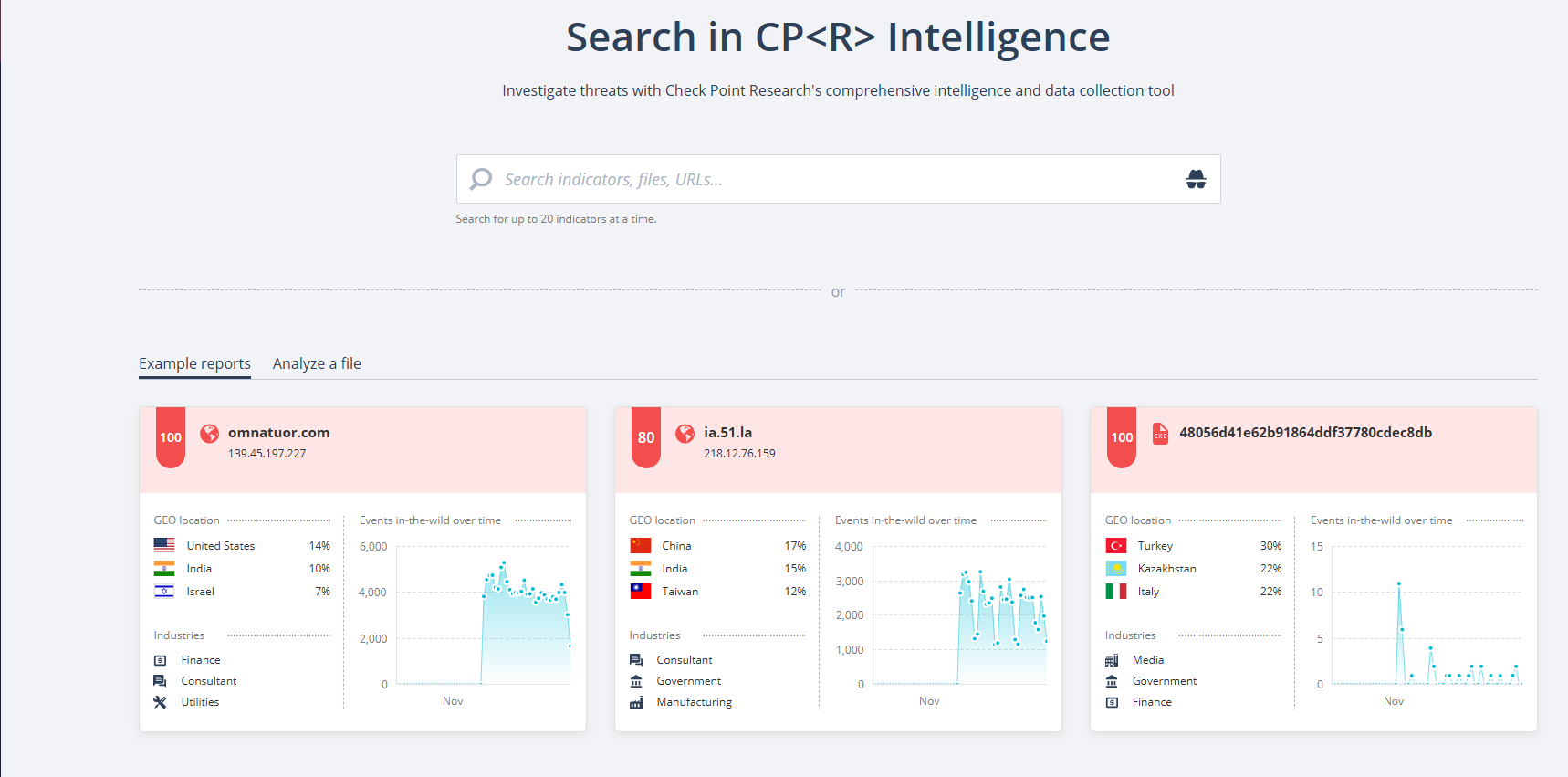
The Example reports tab shows examples of the available intelligence. Click the tiles to view the intelligence data.
You can use the Intelligence page to perform these actions:
Viewing Intelligence for Indicators
You can view the intelligence for a specific:
-
URL
-
Domain
-
MD5, SHA1 or SHA256 hash of a file
-
IP address
To view the intelligence for an indicator:
-
Click Intelligence.
-
Enter the indicator name(s) in the Search field and press Enter.

Note - To search in Incognito mode, click the
 icon. This will disable actions that trigger activity on the searched websites.
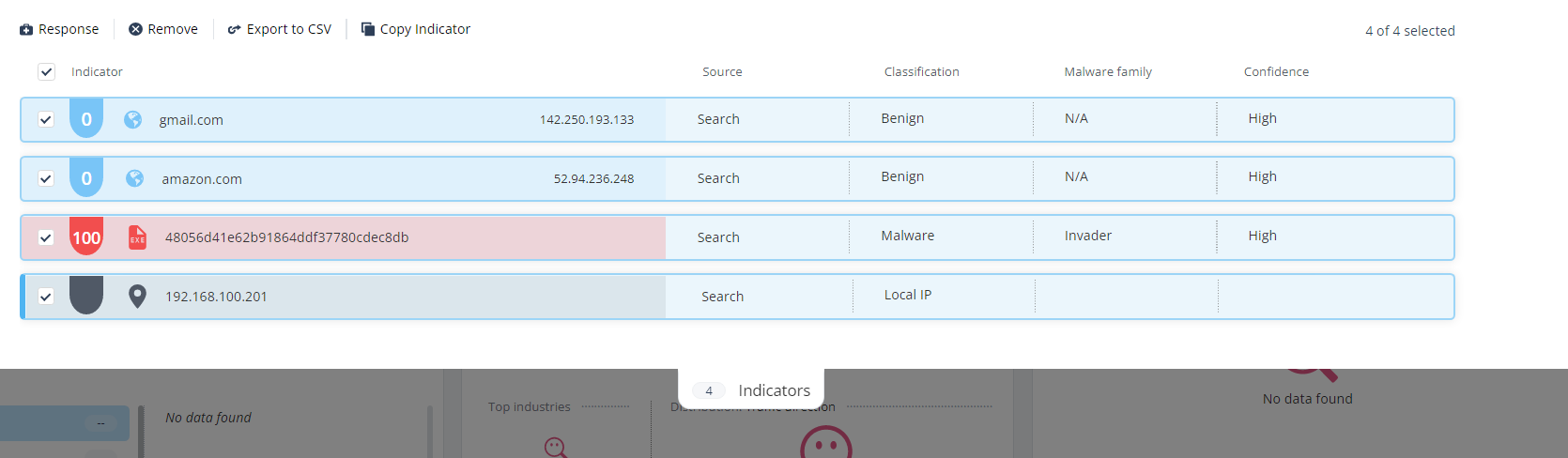
icon. This will disable actions that trigger activity on the searched websites.The search summary table is displayed. You can search for up to 20 indicators in a single search. The indicators can be of the same type or different types.
Item
Description
Risk
The indicator's risk level based on the Check Point reputation engine.
The higher the risk, higher the degree of maliciousness. Value ranges from 1 to 100, where 100 indicates a higher risk level and/or level of maliciousness.
Indicator
 A malicious artifact, such as domain, URL, IP address, and files. IP Address
A malicious artifact, such as domain, URL, IP address, and files. IP Address(For URLs and Domains)
IP address of the indicator.
File Type
(For files)
Type of the file.
For example, .exe, .dll.
Source
Indicates the source where you searched for the indicator.
Examples -
-
If you searched the indicator from the Search field, then the Source is displayed as Search.
-
If you search for amazon.com and added an indicator from Research > Communicating Files, the Source is displayed as amazon.com > Communicating Files.
Classification
Threat classification determined by Check Point engines.
For example, Malware or Benign.
Malware family
The malware family associated with the indicator, determined by Check Point engines.
For example, Invader.
Confidence
The confidence level of the indicator's classification, determined by Check Point engines.
-
-
To view the Intelligence Dashboard for the indicator, click the indicator row.
Intelligence Dashboard
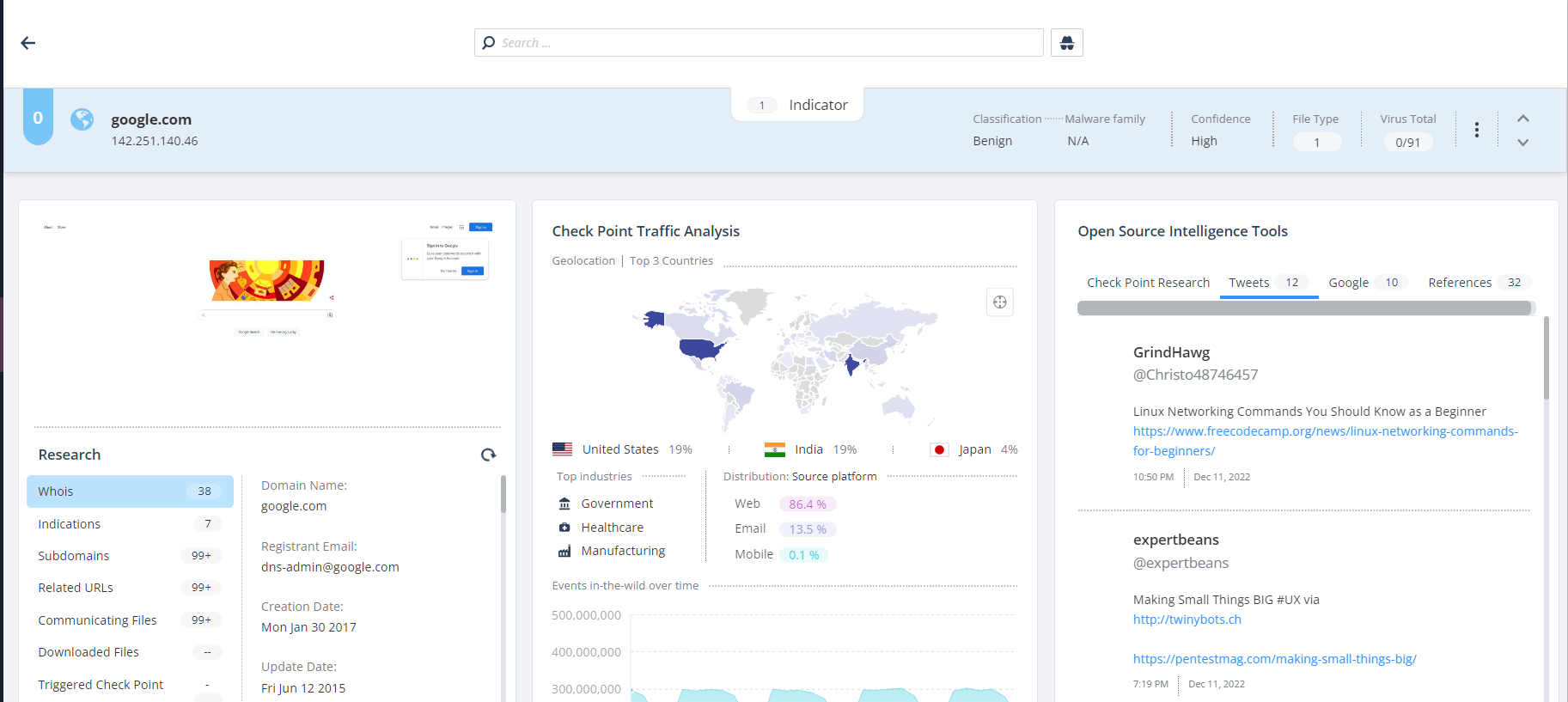
The Intelligence dashboard shows:
Indicator Information
The Indicator Information widget displays a high level overview of the analyzed indicator.
-
For domains and URLs, this widget shows a live screenshot of the website.
-
For files, the widget shows:
-
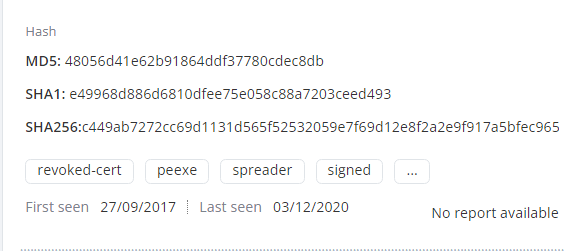
File hash details - MD5, SHA1, and SHA256
-
Tags - The file tags from VirusTotal. Indicates the different characteristics about the file.
For example, the signed tag indicates that the file is signed by a valid authority.
-
First seen - Date the file was first seen.
-
Last seen - Date the file was last seen.
-
Report - Check Point Threat Emulation Report (if available).
-
Research
The Research widget displays technical information about the indicator.
-
For domain and URLs, the widget shows:
Item
Description
Whois data
Shows registered users or assignees of an Internet resource such as a domain name or IP address block.
Indications
Summarized reputation data on this domain.
Subdomains
Sub-domains for this domain.
Related URLs
URLs under this domain.
Communicating Files
Files that were seen communicating with the searched domain.
Downloaded Files
Files downloaded from this domain.
Triggered Check Point Protections
Check Point protections triggered by the domain in:
User Agent
The user agent used to contact this domain during a malicious event.
-
For files, the widget shows:
Item
Description
File Names
The file names observed by Check Point for this file.
Network Activity
The network traffic the file created during Check Point Threat Emulation.
DNS Resolutions
DNS requests the file created during Check Point Threat Emulation.
Parent Process
The process that created the file. Parent Archive The hash of the available file archive. Source URLs URLs from which the file was downloaded. Email Subjects Email subjects that contains this file as an attachment.
Check Point Traffic Analysis
The Check Point Traffic Analysis widget shows a global view of the indicator's network traffic based on Check Point's global sensors. It gives a comparative view of the network traffic across different geographies. The widget shows:
|
Item |
Description |
|---|---|
|
Geolocation |
The indicator's usage in different geographic locations.
|
|
Top industries |
Top 3 industries where this indicator was seen. |
|
Distribution |
Types of platforms that accessed the indicator. For example, Web, Email. |
|
Events in-the-wild over time |
The number of events over time for the indicator. |
Open Source Intelligence Tools
The Open Source Intelligence Tools widget shows the indicator information from Open Source Intelligence (OSINT![]() Open-Source Intelligence (OSINT) refers to data available from public sources.). The widget has these tabs:
Open-Source Intelligence (OSINT) refers to data available from public sources.). The widget has these tabs:
|
Tab |
Description |
|---|---|
|
Check Point Research |
Articles published by Check Point Research that mention this indicator and/or malware family. |
|
Tweets |
Any tweets that mention the indicator, based on Check Point Research's social media crawler. |
|
|
Google Search results for the indicator. |
|
References |
Web page links that contains the indicator. |
Exporting the Search Summary to a CSV
-
Click Intelligence.
-
Enter the indicator name(s) in the Search field and press Enter.
-
In the Search Summary table, select the indicators you want to export.
By default, all the searched indicators are selected.
-
At the top, click Export to CSV.
The system downloads a .csv file in the name format Exported Summary Report Date Time.
For example, Exported Summary Report 2022-12-08 12-33-37.csv
Copying and Removing an Indicator from the Search Summary
-
To copy an indicator, select the indicator in the Search Summary table and at the top, click Copy Indicator.
You can copy the indicator name and search for the indicator in any external or internal resources, or share the indicator name with other applications.
-
To remove an indicator, select the indicator in the Search Summary table and at the top, click Remove.
Analyzing a File
You can upload a file to Check Point's Threat Emulation Sandbox for analysis. For the supported file types, see sk106123.
To analyze a file:
-
Go to Intelligence > Analyze a file.
-
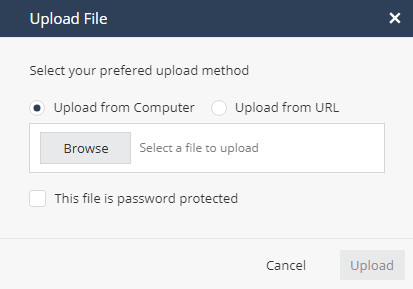
Click Upload file.
The Upload File window appears.
-
Do one of these:
-
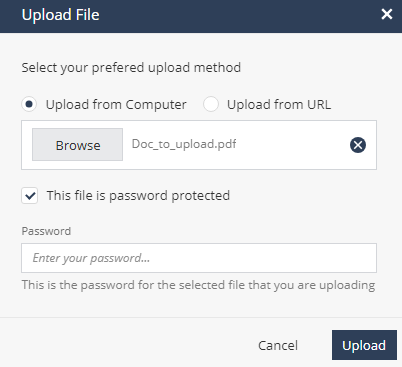
If the file is protected with a password, select the This file is password protected checkbox and enter the password.
-
Click Upload.
The file is added to the summary table.
-
To refresh the summary table, click Refresh.
-
To search for a file in the summary table, enter the file name in the Search field and press Enter.
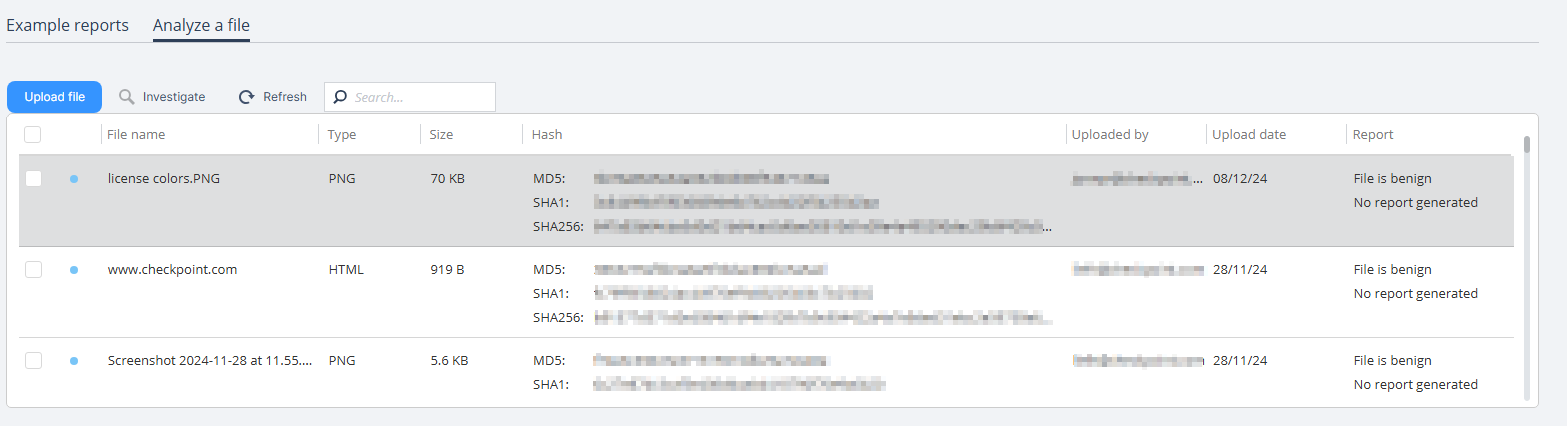
The summary table shows these file parameters:
Item
Description
File name Name of the file. Type Type of the file.
For example, EXE, DLL, CSV.
Size File size. Hash File hash details:
-
MD5
-
SHA1
-
SHA256
Upload by
Email address of the user who uploaded the file.
Upload date
The date on which the file was uploaded.
Report
The verdict returned by Check Point Threat Emulation analysis.
If the file was determined as malicious, the Threat Emulation report is available to download.
-
Investigating a File
You can view the intelligence information for a file and investigate it from the Intelligence dashboard.
To investigate about a file:
-
Go to Intelligence > Analyze a file.
-
In the summary table, select the file to investigate. Click Investigate.
The intelligence information for the file is displayed.