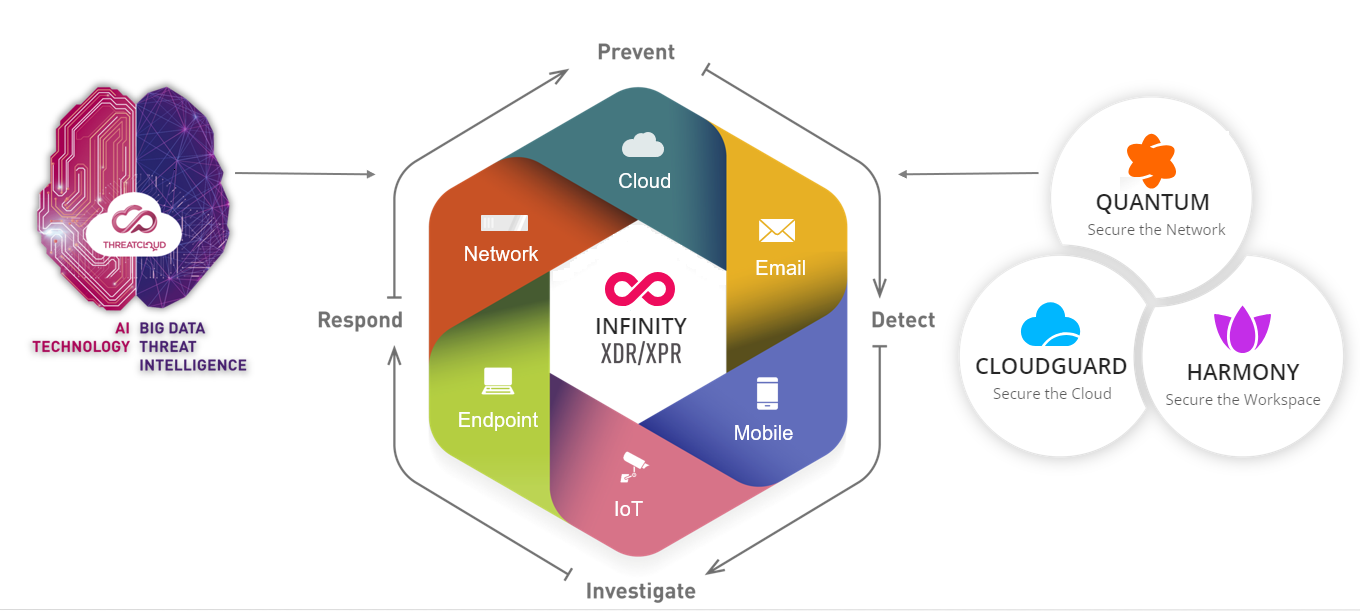
Introduction to Infinity XDR/XPR
Check Point Infinity XDR![]() Extended Detection & Response/XPR
Extended Detection & Response/XPR![]() Extended Prevention & Response is an Extended Detection Response (XDR) and Extended Prevention Response (XPR) tool that provides a unified view of all the security operations across onboarded products and helps you detect, respond to and prevent cyber attacks.
Extended Prevention & Response is an Extended Detection Response (XDR) and Extended Prevention Response (XPR) tool that provides a unified view of all the security operations across onboarded products and helps you detect, respond to and prevent cyber attacks.
Infinity XDR/XPR provides a consolidated security view across all connected products. It provides a focused and prioritized set of incidents that require operator attention. The application provides recommendations for the actions to be taken to address the incident and options to automate enforcement across the monitored deployment.
The primary benefits of Infinity XDR/XPR are:
-
Operator efficiency - Reduces operator workload by processing large numbers of events and alerts to create a small number of prioritized events for operator attention.
-
Unique Detections - Infinity XDR/XPR has a view across the network and for extended periods of time. This allows it to leverage Artificial Intelligence (AI), Machine Learning (ML) and correlation to generate detections beyond those that are generated by each of the connected products. This includes the following detection types:
-
Correlation - Connection of multiple events across connected products to identify a security incident. As additional logs are connected or correlated together, events with lower severity may be seen within context of a higher priority incident.
-
User Entity Behavioral Analytics (UEBA) - Uses ML to build models of the usual activities on the deployment. These can be leveraged to detect and flag any activities that do not match this expected model.
-
-
Collaborative Enforcement - Coordinates and automates response actions across all connected products. Feeds containing Indicators of Compromise (IoCs) are leveraged for this enforcement.
Definitions and Concepts
Understanding Events, Alerts, and Incidents
In the context of Infinity XDR/XPR, the terms events, alerts, and incidents represent three key types of messages that indicate different levels of activity and potential risk. Understanding the distinction between these categories is important to understanding the XDR/XPR functionality.
-
Events
Event are records of normal or noteworthy activity that occur within a system, network, or application. They are often automatically generated by devices or software. Examples of such events include login events, file access and network connections. While most events are benign, they provide the foundational data used to detect issues or anomalies. For example, while all users must login to gain access, a login performed from an unusual location or time may be considered potentially anomalous. Events are also referred to as Logs.
-
Alerts
Alerts are notifications generated when specific conditions or thresholds are met, typically defined by detection rules or AI-based analysis. An alert signifies something that may require attention, such as unusual network traffic, failed login attempts, or a critical system error. Not all alerts indicate a real problem, but they warrant investigation.
-
Incidents
Incidents are confirmed or suspected breaches, disruptions, or threats that negatively affect operations or security. An incident often originates from one or more alerts but involves a validated issue that needs containment, resolution, and possibly reporting. Some examples of incidents are data exfiltration attempts and brute force login attempts.
Incidents are the primary set of items to be handled by the administrator. Each incident can be managed from the Infinity XDR/XPR management interface during its lifecycle. This allows an incident to be assigned to a specific administrator, have comments added to provide additional data as investigation progress until finally get assigned one of the multiple closure statuses to reflect the final incident resolution.
|
|
Note - Within the scope of incidents, alerts are currently displayed as Insights. However the terms Alerts and Insights can be considered synonymously and will eventually be consolidated and displayed as Alerts. |
Components of an Incident
The three primary components of an incident are:
-
Assets - Valuable resources within an organization that need protection and may be targeted or impacted during a security incident. In the context of Infinity XDR/XPR, monitored assets are users and devices.
-
Artifacts - Pieces of evidence of the entities associated with an event or alert that provide additional context. Examples of artifacts are files, processes, IP addresses and URLs.
-
Indicator - A type of artifact that has been identified as a meaningful sign of potential malicious activity. While all indicators are artifacts, not all artifacts qualify as indicators, only those that are known or suspected to signal a security threat or compromise.
Administrator can reclassify items between the indicator and artifact categories.
Alert Processing
There are multiple steps performed during the processing of an alert:
-
Grouping
-
Enrichment
-
Validation
-
Correlation
These are described in the following sections.
Grouping
Alerts for which all the key data elements are the same, except for the time of the alert, are grouped together. It is possible to display such alerts as grouped alerts, that are displayed as a single record together with the time of the first alert in the group, in addition to the time of the most recent alert.
Enrichment
Enrichment is the process of adding contextual information and threat intelligence to security alerts to provide deeper insights about potential threats, such as adding geolocation data, common usage, reputation scores, or historical patterns.
Validation
There are multiple sources for alerts:
-
Alerts generated by the connected products. These are sometimes referred to as parity alerts.
-
Alerts generated by AI/ML algorithms and Advanced User Entity Behavioral Analytics (UEBA
 User Entity and Behavior Analytics that uses Machine Learning to detect anomalies in the behavior of users and devices.) detections.
User Entity and Behavior Analytics that uses Machine Learning to detect anomalies in the behavior of users and devices.) detections.
In both cases, the alert goes through validation, which is the process of calculating a single score for the alert and its indicators, including the result of the different enrichment options. The validation workflow is used to confirm whether an alert represents a true security incident, a false positive, or something between that should continue to be monitored. It ensures the alert is legitimate, actionable, and prioritized correctly.
As a result of the validation process, each alert is assigned a verdict, along with a short textual justification. This verdict may determine whether the alert requires attention and will be included as part of an incident, or will continue to be monitored as additional events are received and correlated.
Correlation
Correlation refers to the process of connecting and analyzing alerts from multiple sources to identify threats that may not be evident from a single data point alone. Assets, Artifacts and Indicators are extracted when Infinity XDR/XPR process the Events and Alerts. These are the critical components that are leveraged in correlation across events from all the connected products by identifying the common components associated across the events and alerts. For example, cases where the same user or IP address is seen across multiple events. Correlated data is processed and, when sufficient correlating factors are identified, multiple events can be stitched together. These events are correlated into a single incident or attack, and may originate from the same product or across multiple products.
Alert Action Status
For every alert, it is determined whether the associated threat was only detected or fully blocked. This is reflected in the Action field associated with each alert as follows:
-
Detected - The threat was detected.
-
Blocked - Any impact from the threat was blocked.
Incident Prevented Status
The status of the incident is calculated from all the automatic actions done by Infinity XDR/XPR or the different products reporting to it, along with remaining actions that need to be done by the user or authorized by them.
This is reflected in the Prevented Status for each incident as follows:
-
Detected - The threat was detected but was not fully prevented. Detected alerts are displayed in the user interface as having Action Required and are prioritized for operator attention.
-
Prevented - The threat was blocked and addressed the identified source of the threat to prevent further alerts from the same source.
Collaborative Enforcement
A key capability of Infinity XDR/XPR is the ability for enforcement across all connected integrations. There are two key aspects of this capability:
-
IoCs - Indicators of Compromise, together with related management and data.
-
Policy Automation
IoCs
Indicators of Compromise (IoCs) are discrete data points such as an IP address, domain, URL, file hash, or malware signature, that is shared in real time or near real time to help organizations identify, detect, and defend against known threats.
Security vendors or communities often curate these IoCs to automatically update systems for proactive threat detection and response.
IoCs are the key component of the collaborative responses that can be performed across the managed network. Events that match on the IoC can be blocked across all connected products.
IoC Management
Customers who have access to Infinity XDR/XPR also have access to the Infinity IoC Management capabilities after they select the IoC Management option in the XDR/XPR menu.
The Infinity IoC is a centralized platform to manage Indicators of Compromise (IoCs) across products. It collects IoCs from various sources through feeds or inputs (manual or live) and also provides output feeds that can be consumed by security products.
You can define one or more IoC feeds. When there are multiple feeds defined, the administrator must assign priority between the various feeds. This allows for resolution of any conflicts in cases where the same IoC is included in multiple feeds. The feeds are evaluated in priority order, and the setting from the first feed containing the IoC is taken.
To enforce the IoCs on third-party systems, create the Output (Blends) within IoC Management, select the feeds to be included in the output and then copy the URL for this feed. This URL should then be integrated with every third-party product connected to Infinity XDR/XPR.
XDR Feed
In addition to any external inputs/feeds that are defined, there is an additional input/feed called XDR Feed, created automatically by default. This feed contains IoCs created from within Infinity XDR/XPR. These IoCs may be created either upon user request from the Infinity XDR/XPR user interface or automatically based on policy automation settings.
Policy Automation
In the Automations page, you can configure Infinity XDR/XPR to take prevention actions automatically when an incident is generated with a specified confidence and severity. Currently, the automatic response supports adding indicators to IoC Management.
The policy can be set to create the IoCs in Disabled state, to be subsequently manually reviewed and enabled. Alternatively, you can configure the IoCs to be enabled immediately upon creation.
Product Integrations
Infinity XDR/XPR gets a wider view and inputs across the monitored network through the supported product integrations. There are three types of supported product integrations:
-
Check Point products
-
Identity sources
-
Third-party products
For each of these supported integration types, three integration aspects should be considered:
-
Log integration
-
Response integration
-
IoCs integration
Response integration allows to perform the commands/responses on the integrated device using APIs.
Check Point Products
All supported Check Point products can be fully integrated, without additional configuration, in the following use cases:
-
Harmony Endpoint - Uses the Harmony Endpoint cloud management (EPMaaS).
When working with Harmony Endpoint, there are two data sources that will be seen in the application:
-
Harmony Endpoint - Endpoint Client
-
Harmony Endpoint Management - Endpoint Management
This ensures there is full coverage for all events from Harmony Endpoint. There may be some duplicated events reported from both sources that will be correlated and, where applicable, included in the same incident.
-
-
Quantum Security Gateway/CloudGuard Network - For Quantum Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., the Sharing SmartConsole Configuration and Logs with Infinity Portal option must be enabled to allow access by Infinity XDR/XPR.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., the Sharing SmartConsole Configuration and Logs with Infinity Portal option must be enabled to allow access by Infinity XDR/XPR.There are two data sources that may be seen for Quantum related events:
-
Quantum Gateway
-
Quantum Gateway Telemetry
-
-
Harmony Email & Collaboration - All deployments.
-
Harmony Mobile - All deployments. However, if you need to enable IoC support for a tenant, contact Harmony Mobile product team.
Identity Sources
Identity Sources provide enrichment of alerts providing asset related information. For example, in addition to IP information included, these will also be mapped to include the names of devices.
When working with Harmony Endpoint, you can define the Identity Connector on Harmony Endpoint to enrich the Endpoint logs sent for processing to Infinity XDR/XPR, with relevant identity information.
For Quantum Gateway, configure either Active Directory or Okta as an Identity Provider on the Identity & Access page in Infinity Portal. This allows enrichment of the logs from Quantum gateway and AI/ML analysis, detection of unusual user login activity and the creation of corresponding incidents.
Third-Party Integrations
Log Integration
Log integration for each third-party product is supported through one of the following integration methods:
-
Syslog - Logs are pushed to Infinity XDR/XPR.
-
API - Logs are pulled over the API interface.
In both cases, following successful integration, the logs from the product are stored in Check Point’s cloud infrastructure and are visible as events.
To enable such integrations, you must do the necessary configurations to enable access to relevant data sources. This is typically done using a certificate (commonly used for syslog integrations) or authentication keys and similar settings (commonly used for API).
Response Integration
To enable Infinity XDR/XPR to issue responses for a specific third-party integration, you must configure an access token or similar credential that allows access to the relevant API.
If log integration is performed over API, additional configuration for response integration may not be necessary. However, if Syslog is used for event integration and API is used for integrating responses, each requires separate configuration.
IOC
To configure the IoC feed to take effect on the third-party device, the administrator must set up an output integration in the IOC Management. This setup defines the location and format of the URL to be configured for processing on the third-party management. Sometimes, multiple URLs may be required for integration if different types of indicators use different feeds.
The table below shows the supported products, their log integration types, and whether they support response integration and IOC Management.
|
Product Family |
Product Name |
Log Integration |
Response Integration |
IOC Management Support |
|---|---|---|---|---|
|
Check Point |
Quantum Security Gateway
|
Check Point cloud |
Supported |
Supported |
|
CloudGuard Network |
Check Point cloud |
Supported |
Supported |
|
|
Harmony Endpoint (EPMaaS) |
Check Point cloud |
Supported |
Supported |
|
|
Harmony Email & Collaboration |
Check Point cloud |
Not supported |
Supported |
|
|
|
Harmony Mobile |
Check Point cloud |
Not supported |
Can be enabled upon user request |
|
Microsoft |
Microsoft 365 Defender for Endpoint |
API |
Supported |
Supported |
|
Fortinet |
FortiGate Next Generation Firewall |
Syslog |
Not supported |
Supported |
|
CrowdStrike |
Falcon |
API |
Supported |
Supported |
|
SentinelOne |
Singularity Endpoint |
Syslog |
Supported |
Supported |
|
Palo Alto Network |
Palo Alto Networks Next Generation Firewall |
Syslog |
Not supported |
Supported |
|
Trend Micro |
Trend Vision One |
API |
Supported |
Supported |
|
Cisco |
Cisco Firepower |
Syslog |
Not supported |
Supported |
|
Okta |
Okta |
Infinity Identity Providers Integration |
Supported |
Not supported |
|
Identity Service* |
Identity Sources supported by the Check Point Security Gateway |
Check Point cloud |
Not supported |
Not supported |
*Tracks unusual user activities, such as repeated failed logins, logins after office hours, and so on. Infinity XDR/XPR correlates this activity to security events from other sources and generates an incident.
Key Application Components
This section describes some of the key application components in Infinity XDR/XPR.
For all tables that contain data, you can filter the records displayed.
Integrations
From this page, you can view the status of the currently integrated products and integrate additional products by following the configuration guidelines.
The Connectivity widget in the Overview page reflects the status of integrated products and provides summary about the related events.
Incident Management
Incidents provide a summarized, prioritized and focused list of items to be handled by the security team. There are two primary workflows that the administrator can follow to review all items:
-
Asset Incident Priority
Incident List
Provides a filtered list of all incidents. By default, the filter is set to show incidents that are new or in progress, assigned to the currently logged in administrator or those unassigned. The list is presented in descending order of priority to show those incidents that have Action Required.
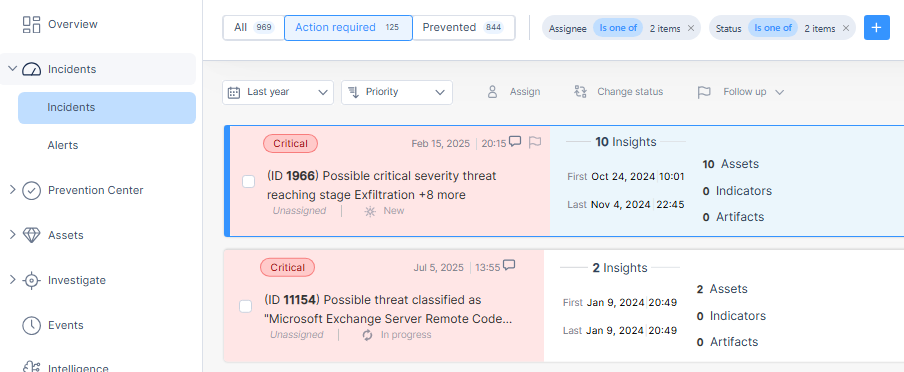
The set of incidents are also displayed in the Overview page in the form of a Kanban board, where incidents are displayed in a table format with columns representing the different incident statuses.
Asset Incident Priority
A widget on the Overview page presents an asset-centric view. All incidents have a defined priority and can be associated with one or more assets. The incident priority of an asset is derived from the incidents it is associated with, according to the following criteria:
-
Incidents that are not in Closed state and not marked as Prevented are considered to determine the Incident Priority. These are the incidents that require action by the user.
-
Some incidents that impact a large number of assets are excluded from determining the Incident Priority. Such incidents are considered as Filtered. An example of a filtered incident is a port scan that can be associated with a large number of assets.
The Incident Priority is set to the highest priority of the incidents that meet the above criteria. For example, if there are one or more associated incident(s) with Critical priority, then the Incident Priority of the asset is set to Critical.
The display also includes the Asset Incident Priority based on Unassigned incidents only. This allows any new incidents to be assigned, after which the unassigned count will be reset back to 0.
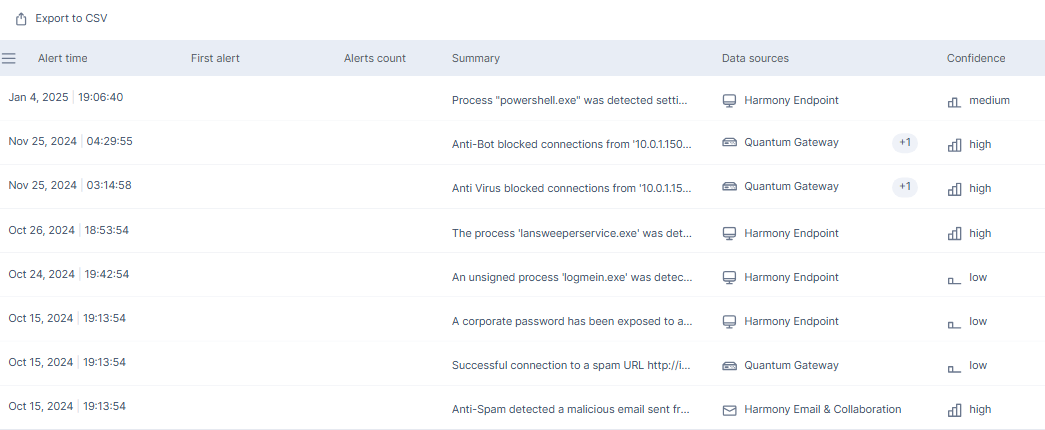
Alert Table
The Incident list is the primary mechanism for handling issues detected by Infinity XDR/XPR. The Alert table provides additional visibility to all the alerts processed by Infinity XDR/XPR and their associated verdict and justification. It can be used to audit and provide visibility into the validation on alerts performed by Infinity XDR/XPR.
Prevention Center
The Prevention Center provides a summary of prevention activities performed across all data processed in your account.
It consists of the following sections:
-
Prevention Status - Shows the statistics of prevention actions in your account, that includes pending, active and expired actions.
-
Executions - Provides visibility into how Infinity XDR/XPR processes alerts and executes actions in response to the alerts.
Assets
The Assets tables provide asset-centric view on Users and Devices protected by Infinity XDR/XPR.
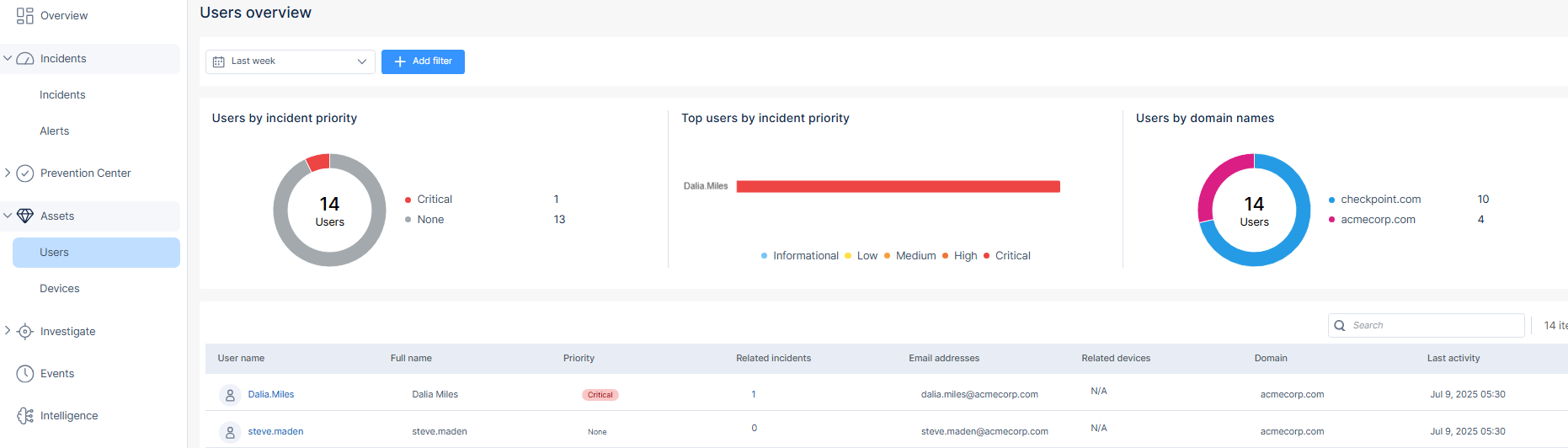
For each asset, information is collected and displayed in one of the following categories:
-
Asset operational configuration (such as Asset Name, Operating System and Version)
-
Visibility into any associated Groups and Organization Units (OU)
-
Incident Priority and Related Incidents
-
Related Assets - There are interrelations between users and devices. For example, users access a network through one or more device. These relationships are displayed in the Related Devices / Usernames field.
-
Activity Time - The Last Activity time is updated whenever data is received for an asset. When you select a time filter for asset display, filtering is done based on the Last Activity time of the assets.
Threat Hunting
Threat Hunting is an investigative tool which allows for advanced querying on all malicious and benign forensics events collected from the onboarded Harmony Endpoint and Quantum Gateway.
The information collected lets you to:
-
Investigate the full scope of an attack.
-
Discover stealth attack by observation of a suspicious activity.
-
Remediate the attack before it causes further damage.
-
Proactively hunt for advanced attacks by searching for anomalies, and using hunting leads and enrichment.
Events
A view of all the raw events processed on the tenant. This is the standard Events widget included in most of the applications in Infinity portal and may include events from products that are not integrated with Infinity XDR/XPR.
Notifications
You can configure and enable notifications to be sent when new a new incident is created. The related configuration includes:
-
Conditions for when a notification is to be sent.
-
Notification contents.
-
Recipients and channels on which the notification is to be sent.
Notifications can be sent by email, Slack and over Microsoft Teams. Notifications allow administrators to get initial details of new incidents without connecting to the application. Notification contents also include a URL to view the full incident details within the application.
XDR Detections
This section provides an overview of the Infinity XDR/XPR unique detection capabilities, explaining each detection category implemented in our security platform. Infinity XDR/XPR integrates multiple security layers to provide comprehensive threat detection, investigation, and response across endpoints, networks, cloud workloads, and applications.
The Power of AI in Infinity XDR/XPR
The Infinity XDR/XPR solution leverages cutting-edge artificial intelligence to transform security operations. Through multiple AI technologies working in concert, the platform delivers detections of the following types:
-
Autonomous Threat Detection - AI algorithms continuously analyze vast amounts of data across all security layers to identify threats that would be impossible to detect with manual analysis or rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.-based systems.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session.-based systems. -
Predictive Threat Intelligence - Machine learning models predict emerging threats based on subtle behavior patterns before traditional IoCs become visible.
-
Adaptive Security Posture - The AI engine dynamically adjusts detection parameters as it learns your environment, becoming more accurate and effective over time.
-
Automated Contextual Analysis - Advanced algorithmics and AI technologies automatically contextualize alerts, reducing the number of false alarms and providing security analysts with comprehensive attack narratives rather than isolated data points.
-
Cognitive Response Automation - AI-driven decision-making enables intelligent, context-aware automated responses that adapt to the specific nature of each threat.
XDR Unique Detection Method
User and Entity Behavior Analytics (UEBA) is a cybersecurity technology that uses machine learning and advanced analytics to detect abnormal behavior by users and entities (such as devices or applications) that may indicate security threats, such as insider attacks, compromised accounts, or data exfiltration. It establishes baselines of normal activity and flags deviations for investigation. Infinity XDR/XPR leverages UEBA which enables detection of novel threats and sophisticated attacks that evade conventional defences.
By continuously learning and adapting to our environment, baseline analysis provides context-aware security that reduces false positives while improving detection of true threats. This capability is uniquely powerful within Infinity XDR/XPR due to its holistic visibility across multiple security layers and data sources.
Detection Catalog
This section provides details about the specific detection categories provided in Infinity XDR/XPR.
|
Category |
Description |
|---|---|
|
Anonymization and Proxy Services |
Detects the use of anonymization tools, VPNs, or proxy services that may indicate attempts to hide malicious activity or evade geographic restrictions. These technologies can be used legitimately but also serve as methods for attackers to mask their origin. |
|
Abnormal Application Data Usage |
Identifies unusual patterns in how applications access, process, or transfer data. This includes detecting when applications exceed normal data processing thresholds or access sensitive data they typically do not interact with. |
|
Authentication and Access Patterns |
Monitors for unusual authentication flows or access patterns that deviate from established baselines, which could indicate account takeover or unauthorized access attempts. |
|
Brute Force Detection |
|
|
Insider and Credential Attacks |
|
|
Command & Control Communication |
Detects communication with known malicious infrastructure or unusual communication patterns that may indicate malware connecting to command-and-control servers through non-standard channels. |
|
Network Traffic Patterns |
Identifies anomalous network traffic that deviates from established baselines, including unusual protocols, timing patterns, or volumes. |
|
Data Exfiltration |
Detects unusual outbound data transfers that could indicate sensitive information being removed from the organization, including large data transfers or communications with suspicious destinations. |
|
Vulnerability Sonar |
Identifies reconnaissance activities from external sources attempting to discover vulnerabilities in internet-facing assets, and determine which systems were found vulnerable, which vulnerability was found and if there are undetected systems successfully accessed from the same scanner. |
|
Initial Access |
Detect techniques used by threat actors to gain their first foothold in a network, including exploitation of vulnerabilities in public-facing applications, drive-by downloads, or supply chain compromises, open ports and available services. |
|
Internal Discovery and Information Collection |
Monitors for systematic attempts to gather information about the internal environment such as Accounts & Groups, Local System Information, Network & Shares, Location, Security Products, Software and system configurations. |
|
Lateral Movement |
Detects attempts to move through the network after initial compromise, for example, Executable and File Transfer, unusual remote executions, unusual access or mounting of network shares. |
|
Ransomware, Wiper, or Data Destruction |
Detects behaviors that are associated with encrypting files for ransom, wiping data, or other destructive activities targeting information assets. |
|
Security Control Evasion |
Identifies techniques used to bypass security controls. Examples - Injection, File Format Tampering, Hidden Artifacts, Indirect Executions, Masquerading, Obfuscation, Script Execution. |
|
Supply Chain Distortion |
Identifies IoCs related to trusted software updates or third-party components. |
|
Suspicious Executions |
Monitors for unusual execution patterns, commonly used by attackers. Examples - Long Execution Chain, Execution During Remote Connection, Execution During Remote Connection, Unusual LOLBin Execution. |
|
System Behavior |
Monitors for changes to system configuration and behavior:
|
|
Security Product Tampering |
Identifies attempts to disable or bypass security tools:
|
|
Suspicious File Operation |
Detects suspicious file characteristics or behaviors that may indicate malware. |
|
Suspicious Trace Removal |
Identifies attempts to clear logs, delete files, or otherwise remove evidence of compromise. |
|
Time-Based Anomalies |
Detects activities occurring at unusual times or with suspicious timing patterns. |
|
Unsolicited External Access |
Identifies unexpected inbound connections or data transfers from external sources. |
Licensing
At least one valid license is required to entitle the Infinity XDR/XPR application to operate and perform processing. There are three different aspects of entitlement associated with a license:
-
Data Processing Entitlement
-
Connected Product Entitlement
-
Expiry Date
Data Processing Entitlement
Infinity XDR/XPR performs extensive analysis and processing of all the data that it receives. Therefore, the entitlement to Infinity XDR/XPR processing is based on the total amount of data from all connected products that is analyzed and processed.
There are two types of licenses that can contribute to this entitlement:
-
License with a per-user Entitlement - License is purchased for a specific number of users. Each user is assigned a data entitlement as defined in the product catalog. The total data entitlement of the license is calculated by multiplying the number of users and the per-user entitlement.
-
Volume Entitlement - License that gives entitlement directly as a number of gigabytes (GB).
It is possible to have multiple active licenses, including a mix of both license types. The total data processing entitlement is the sum of the entitlements provided by all active licenses.
To track the current volume of data being processed, compared to the entitlement, go to Settings > Log Processing. The current volume of data being processed is calculated as the average volume of data processed daily, during the last seven days.
Connected Product Entitlement
There are two types of licenses in terms of connected product entitlement:
-
Harmony Endpoint only - Licenses that are purchased together with Harmony Endpoint (HEP). With this license, Infinity XDR/XPR is operational as Endpoint Detection and Response (EDR).
-
All Products - All products can be connected.
There must be at least one active license for All Products to integrate additional products.
License Expiration
Each individual license has an expiry date. When this date is reached, the license expires and the corresponding entitlement associated with the license is no longer active. When all active licenses have expired, Infinity XDR/XPR enters a Grace Period before all processing of data is stopped. The current Grace Period after expiry of production licenses is 30 days but this duration is subject to change.
Data Retention
The raw events from all connected products, including third-party products, are retained for a default period of 3 months. To extend this duration to 6 or 12 months, you can purchase additional licenses as part of Infinity Events - Logging & Analytics.
These retention periods also apply to any data derived or retrieved by Infinity XDR/XPR. This includes incidents and report files, such as forensic reports, that are retrieved from other systems and stored in Infinity XDR/XPR.
Supported Regions
Infinity XDR/XPR is supported only for the Infinity Portal tenants (accounts) residing in these regions:
-
EU
-
US
-
India (Infinity AI Copilot and Infinity Playblocks are not available)
-
UAE (Infinity AI Copilot and Infinity Playblocks are not available)
When leveraging Infinity XDR/XPR with other Check Point products, the region selected for Infinity XDR/XPR account creation must match the region to which the other products are sending data.
API Support
The following suites of APIs are available for interaction with Infinity XDR/XPR. They are available for use with a valid Infinity XDR/XPR license:
-
XDR/XPR API - Operations related to incidents, alerts, actions and exceptions.
See XDR/XPR API.
-
Threat Hunting API - Retrieves Threat Hunting records.
See TH API Docs.
-
Infinity Events API - Retrieves raw Event logs as displayed in the Events tab.
See Infinity Events API.