Adding an RDP Zero Trust Application
Prerequisite
Make sure you have the credentials to access the application over RDP.
To add an RDP Zero Trust Application:
-
Access the Harmony SASE Administrator Portal and click Private Access > Applications.
-
Click Add Application.
The Add application window appears.
-
In the General Settings section, enter these:
-
Application Name - Name of the application.
-
Protocol - RDP
-
Icon - Icon for the application.
-
Host - Internal IP address of the server to which you want to connect.
-
Port - 3389
-
Network - Network that hosts the application.
-
Max number of connections - Maximum number of concurrent RDP sessions.
-
Ignore server certificate - Select Yes to ignore the SSL certificate, unless you activate RDP over SSL.
-
Admin console - Select the checkbox to connect directly to the console session on the Windows server.
-
(Optional) Display Application Icon at Login Screen - Displays the application icon for the member in the login page.
-
(Optional) Enable copy-paste from RDP to clipboard - Enables to copy data from RDP to clipboard.
-
(Optional) Enable printing from RDP - Enables to print data from RDP.
-
(Optional) URL Alias - URL for members to access the application.

Important - You cannot add a URL alias after you create the application.
-
In the External Domain (CNAME) field, enter a CNAME associated with your domain.
-
From the SSL Certificate list, select the application domain SSL certificate uploaded in Certificate Manager.
-
Go to your DNS administrator (for example, GoDaddy or R53 in AWS).
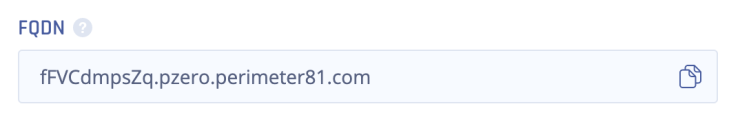
Under your domain, use the CMANE specified in the previous step and point it to the application FQDN. The FQDN appears in the application settings after you click Apply.
-
-
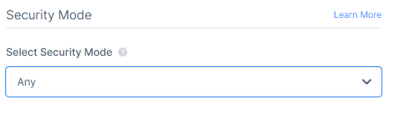
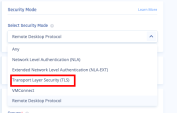
From the Select Security Mode list, select a security mode. It indicates the encryption and authentication mode.
-
Any (default) - Select the security mode automatically based on the security protocols supported by the client and the server.
-
Network Level Authentication (NLA) - Uses the TLS encryption and requires credentials to access the application. Also referred to as hybrid or CredSSP (the protocol that drives NLA).
-
Extended Network Level Authentication (NLA-EXT) - Sends Early User Authorization Result from the server to the client after the NLA handshake.
-
Transport Layer Security (TLS) - RDP authentication and encryption through TLS (RDPTLS). This is suitable for load balancing where the primary RDP server redirects the connection to secondary servers.
-
VMconnect - Selects a security mode supported by Hyper-V or VMConnect automatically based on the supported protocol by client and server.
-
Remote Desktop Protocol (RDP) - Suitable for machines running old Windows version where a login screen is required.
-
-
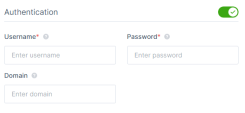
In the Authentication section, enter these:
-
Username and Password - Credentials of the server.
-
Domain - Your active directory FQDN.

Note - If you disable Authentication, then the member must enter the credentials when accessing the application.
-
-
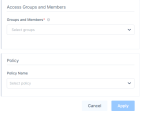
In the Access Groups and Members section, in the Groups and Members list, select the member groups that can access the application.
-
(Recommended) In the Policy Name list, select an application policy.
-
Click Apply.
The system lists the application in the Applications page and enables it by default.
-
For members to access the application, see Accessing an Application by a Member.
Additional Registry Configuration
Windows 7
-
Open the Registry Editor.
-
Navigate to HKEY_LOCAL_MACHINE > Software > Microsoft > Windows NT > Terminal Services.
-
Select fServerEnableRDP8.
-
Set the value type to REG_DWORD.
-
Set the value to 1.
-
Reboot the machine.
Windows Server 2016
-
Open the Registry Editor.
-
Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
-
Select SecurityLayer and change the value to 1.
-
Select UserAuthentication and change the value to 0.
Windows Server 2019
-
Open the Registry Editor.
-
Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
-
Select SecurityLayer and change the value to 0.
-
Reboot the machine.
Troubleshooting
Upstream Error
-
If Authentication is enabled (see Authentication ), verify the credentials.
If it is disabled, change the security mode to Transport Layer Security (TLS).
Additional Troubleshooting Steps
-
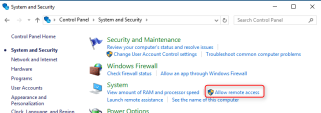
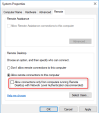
Disable NLA on the remote machine:
-
Go to the Remote tab and in the Remote Desktop section, clear the Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended) checkbox.
-
Click OK.