Introduction to Harmony SASE IPsec Site to Site VPN
This guide provides the procedures to integrate Harmony SASE with your on-premises or cloud-based resources through the IPSec Site-2-Site VPN tunnel to provide secure network or application access. For more information, see the .
IPSec Handshake
The IPSec Site-2-Site VPN tunnel employs a two-phase handshake.
Phase I (IKE or Gateway)
This is the security association responsible for the external IP communication between the Harmony SASE network and the remote IP through the port 500/4500. The following information is required for Phase I. This information must match in both Harmony SASE and the remote side of the tunnel:
-
Shared Secret
-
Public IP
-
Remote ID
-
IKE Version
-
IKE Lifetime
-
Encryption (Phase I)
-
Integrity (Phase I)
-
Diffie-Hellman Groups (Phase I)
Phase II (ESP or Tunnel):
This is the security association in responsible for the internal LAN range or subnet handshake after establishing the IKE SA .
The following information is required for Phase II. This information must match in both Harmony SASE and the remote side of the tunnel:
-
Harmony SASE Gateway Proposal Subnets
-
Remote Gateway Proposal Subnets
-
Tunnel Lifetime
-
Dead Peer Detection (DPD)
-
Encryption (Phase II)
-
Integrity (Phase II)
-
Diffie-Hellman Groups (Phase II)
Policy-Based and Route-Based IPSec Connection
Policy-based connection is easier to set up but is more vulnerable to IPSec tunnel value mismatch.
Depending on your device, a single missing subnet may cause the Phase II negotiation to fail.
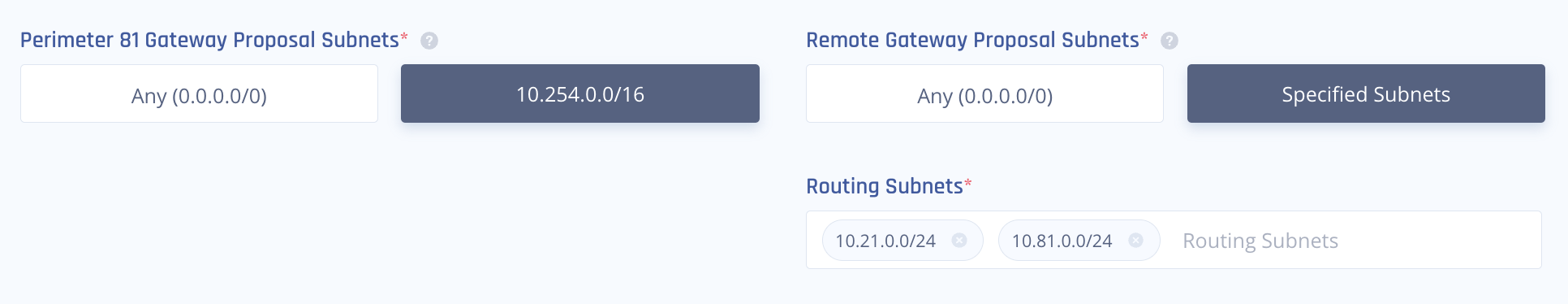
Route-based connection is also known as a Tunnel Interface or VTI.
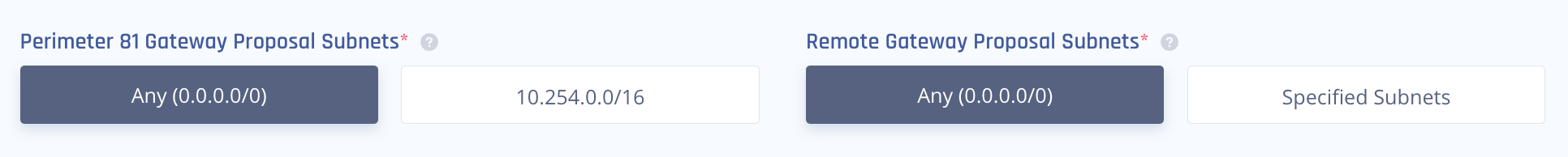
It is a more modern and stable method of IPSec tunneling. Once established, it uses one subnet (0.0.0.0/0) for the handshake, thereby reducing the chances of an error during renegotiation.
Supported Integrations
|
On-premises SD-WAN |
Cloud-based SD-WAN |
|
|---|---|---|
|
Firewall |
Router |
|
|
|
Single Tunnel Redundant Tunnels Other Cloud Options |
|
High-Level Procedure
-
Configure any of these:
On-premises
Cloud-based Resource
Firewall
Router
Single Tunnel
Redundant Tunnels
Other Cloud Options
