Ping Identity
Use these steps to configure the SSO![]() Single Sign-On (SSO) - A session/user authentication process that permits a user to enter one name and password in order to access multiple applications. authentication with Ping Identity.
Single Sign-On (SSO) - A session/user authentication process that permits a user to enter one name and password in order to access multiple applications. authentication with Ping Identity.
To configure Ping Identity as your Identity Provider:
-
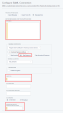
In the Infinity Portal, go to
 > Identity & Access and click the plus icon.
> Identity & Access and click the plus icon. -
Enter a name for the Integration Title and select Ping Identity.
-
To continue, click Next.
In this step of the IdP Integration Wizard, you can configure SSO authentication for Infinity Portal administrators and for end users of Check Point services.
-
Select Enable Administrators to log in to the portal using this IdP.
-
Select one of these options:
-
Login based on domain verification - Infinity Portal Administrators can log in to this Infinity Portal account with SSO from the Identity Provider
 A system entity that creates, maintains, and manages identity information for principals and also provides authentication services to relying applications within a federation or distributed network. Acronym: IdP or IDP.. Administrators log in through the Infinity Portal login page.
A system entity that creates, maintains, and manages identity information for principals and also provides authentication services to relying applications within a federation or distributed network. Acronym: IdP or IDP.. Administrators log in through the Infinity Portal login page. -
Login with a unique URL - Infinity Portal Administrators can log in to multiple Infinity Portal accounts with SSO from the Identity Provider. Administrators log in using the URL that appears at the bottom of the Login with a unique URL button. Copy this URL and keep it in a safe place.
-
-
In the Service(s) Integration section, select one of these options:
-
No Services - End users of Infinity Portal services cannot authenticate with SSO from the Identity Provider. This is the default configuration.
-
All Services - End users can log in with SSO from the Identity Provider to all Check Point services that support SSO.
-
Specific Service(s) - From the list of services, select service(s) to allow end users to log into with SSO from the Identity Provider. Available services:
-
Harmony Connect
-
Quantum Gateways
-
-
-
Click Next (or, if you are editing a configuration, Apply) to complete the Integration Type configuration.
|
|
Note - If for Integration Type you selected "Login with a Unique URL", the Verify Domain step is not necessary. |
-
Connect to your DNS server.
-
Copy the DNS Value from the Infinity Portal IdP Integration wizard > Verify Domain step.
-
On your DNS server, enter the Value as a
TXTrecord. -
In the Infinity Portal > Domain(s) section, enter a public DNS domain server name and click the plus icon.
Check Point makes a DNS query to verify your domain's configuration.
-
Optional - add more DNS domain servers.
-
Click Next.

Note - Wait until the DNS record is propagated and can be resolved.
In this step, you create a SAML![]() Security Assertion Markup Language. An XML-based, open-standard data format for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. application in the Ping Identity Portal.
Security Assertion Markup Language. An XML-based, open-standard data format for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. application in the Ping Identity Portal.
Before you start, in the Infinity Portal, copy and save the Entity ID and the Reply URL.
First, create a new environment in the Ping Identity Portal.
-
Log in to your Ping Identity Portal.
-
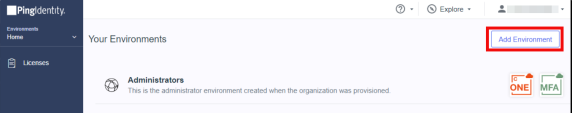
Go to the Home page and click Add Environment.
-
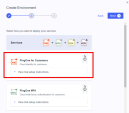
Select Customer solution and click Next.
-
Make sure PingOne for Customers is available. Click Next.
-
Enter all relevant information in the form.
-
Click Finish. Ping Identity redirects you to the Home page.
In the new environment, create a web application.
-
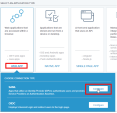
Navigate to Connections > Applications and click Add Application.
-
Click WEB APP, then select SAML and click Configure.
-
A new Create App Profile page opens.
-
Enter the application details. For example, set the application name to Check Point Infinity Portal.
-
Click Next. The Configure SAML Connection page opens.
-
Under Provide Meta Data, select Manually Enter.
-
Configure SAML Connection:
-
Click Save and Continue.
-
In the Map Attributes page, configure SAML attributes. The User ID attribute = saml_subject appears by default. Change User ID to Email Address.
-
Click Add Attribute and select PingOneAttribute to add a new attribute:
-
For User Attribute, select Group Names.
-
For Application Attribute, enter memberOf.
-
Select the Required option.
-
-
Click Add Attribute and select PingOneAttribute to add a new attribute:
-
For User Attribute, select Given Name.
-
For Application Attribute, enter firstName.
-
Select the Required option.
-
-
Click Add Attribute and select PingOneAttribute to add a new attribute:
-
For User Attribute, select Family Name.
-
For Application Attribute, enter lastName.
-
Select the Required option.
-
-
Click Add Attribute and select PingOneAttribute to add a new attribute:
-
For User Attribute, select Email Address.
-
For Application Attribute, enter email.
-
Select the Required option.
-
-
Click Add Attribute and select PingOneAttribute to add a new attribute:
-
For User Attribute, select User Id.
-
For Application Attribute, enter userid.
-
Select the Required option.
-
-
Click Save and Close.
-
Ping Identity redirects you to the Applications page. In your newly created application, go to the Configuration tab and click Download under Connection Details > Download Metadata.
-
Download the SAML Metadata file to your computer.
IdP Initiated lets you connect directly to the Infinity Portal from your Ping Identity admin console. To do this, you must create an Infinity Portal app card in your Ping Identity admin console. See the Ping Identity documentation for the Application portal.
Step 1: In Infinity Portal, enable IdP Initiated flow:
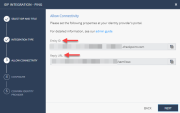
In the Infinity Portal > IdP Integration Allow Connectivity step, select the checkbox Enable IDP initiated flow.
The Relay State field appears.
Step 2: In your Ping Identity account, configure the IdP Settings:
-
Navigate to your Ping Identity admin console.
-
From the left toolbar, click Connections > Applications.
-
Open the application object for the SAML connection to Infinity Portal.
-
From the top navigation toolbar, click Overview.
-
Click the Protocol SAML button.
The Edit Configuration menu opens for the application object.
-
In the Edit Configuration menu > Target Application URL field, enter the Relay State from Infinity Portal.
-
Click Save.
|
|
Important - Before you can test the connectivity between Ping Identity and Infinity Portal, you must complete all of the IdP integration steps in Infinity Portal. |
In this step, you upload the federation metadata XML file.
-
On the Infinity Portal, Identity Provider Wizard > Configure Metadata page, upload the Federation Metadata XML that you downloaded from the Ping Identity Portal.

Note - Check Point uses the service URL and the name of your Certificate to identify your users behind the site.
-
Click Next. Check Point verifies the metadata of your Identity Provider.
To use Ping Identity for SSO authentication only, select the checkbox I want to skip this step and use this IdP for SSO authentication only.
Directory Integration gets information about users and groups for the services you selected in the Integration Type step > Service(s) Integration section.
Directory Integration does not apply to Users and User Groups in the Infinity Portal.
|
|
Important - After you create a Directory Integration, you cannot change it. To create a different Directory Integration, you must create a new Identity Provider (IdP) Integration. |
You can manage user identity data with Manual API Sync or with System for Cross-Domain Identity Management (SCIM).
|
Directory Integration Method |
How it Works |
Which Users and Groups are Synced |
|---|---|---|
|
Manual Sync |
Allows Check Point services to query for any change in Ping Identity users and groups. The Infinity Portal pulls users and groups from Ping Identity. |
All users and groups in Ping Identity. Nested groups in Ping Identity are supported. |
|
SCIM (Automatic Sync) |
Allows Ping Identity to push any change in the user and group directory to Check Point services. |
Only users and groups in Ping Identity that are assigned to the SCIM connection you created from Ping Identity to the Infinity Portal. |
Step 1 - Set up Users and Groups Synchronization:
To start, create a Worker application and then you can set up permissions for users and groups.
Step 2 - Create a Worker application in the Ping Identity Portal:
-
In the Ping Identity Portal, from the left menu, expand Applications > click Add Application.
The Applications page opens.
-
At the top of the page click the "+" icon to the right of the word Applications.
The Add Application window opens.
-
In the Application Name field, enter a name for the application.
-
In the Application Type section, select Worker.
-
Click Save.
Ping Identity creates an application object.
Step 3 - Set up Users and Groups Permissions:
Set up permissions to allow the selection of users and user groups from your Ping Identity for the Infinity PortalSSO.
-
In the application object, open the Configuration tab.
-
In the upper right, click the edit button (pencil icon).
-
In the Grant Type section, select Client Credentials.
-
In the Token Endpoint Authentication Method field, select Client Secret Post.
-
Click Save.
-
Open the Roles tab.
-
Click Identity Data Read Only > Select All.
-
Click Save.
-
On the Applications page:
-
Move the slider for the Web App SAML application you created for the Infinity Portal to the on position.
-
Move the slider for the Worker application you created for the Infinity Portal to the on position.
-
Step 4 - Copy the relevant values to the Infinity Portal Wizard:
-
Environment ID - In Ping Identity Portal, from the left toolbar, click Settings > Environment Properties and copy the value of Environment ID.
-
Region - In Ping Identity Portal, from the left toolbar, click, Settings > Environment Properties and view the region. In the Wizard, enter EU for Europe, COM for the United States, and ASIA for the Asian Pacific.
-
Client ID and Shared Secret - In Ping Identity Portal, from the left toolbar, click Applications and open your Worker application. Open the Overview tab and copy these values: Client ID and Client Secret.

Best Practice - Check Point recommends that you save the ‘Client Secret’ value in a separate secured file to retrieve it when it is required.
Step 5 - Verify that all fields in Directory Integration are correct:
-
To test the users and group synchronization between the Infinity Portal and the Identity Provider, click Test Connectivity.
-
If the test is unsuccessful, repeat the Set Directory Integration step to configure the user and group synchronization parameters.
-
Click Next.
Prerequisites:
-
In the Infinity Portal create a user group with an Admin global role. See Users.
-
You must have Administrator permissions for the Ping Identity account.
Step 1 - In the Infinity Portal, copy values and finish the IDP Integration Wizard:
-
In the Infinity Portal > Directory Integration step, select Automatic Sync (SCIM).
-
Copy these values and keep them in a safe place:
-
SCIM API Token
-
URL
-
-
Click Next.
The Confirm Identity Provider step opens.
-
Click Submit.
Ping Identity is now integrated with the Infinity Portal. The Ping Identity integration appears in the gallery in the Infinity Portal. Finish configuring SCIM (Automatic Sync) in the Ping Identity Portal.
Step 2 - In the Ping Identity Portal, create a new Connection:
-
In the Ping Identity Portal, from the left menu, expand Integrations > click Provisioning.
-
Next to Provisioning, click the + button.
The Create a New Connection wizard opens.
-
To the right of Identity Store, click Select.
-
Search "
scim". -
Select SCIM Outbound.
-
Wizard Step 1:
-
Enter a name for the integration. Example: "Infinity Portal SCIM".
-
Click Next.
-
-
Wizard Step 2:
-
In the Configure Authentication section > SCIM BASE URL field, paste the URL you copied from the Infinity Portal.
-
For Authentication Method select OAuth2 Bearer Token.
-
In the Oauth Access Token field, paste the SCIM API Token you copied from the Infinity Portal.
-
Click Test Connection.
If the test is successful, a confirmation message appears. If the test fails, make sure that you copied and pasted the values correctly from the Infinity Portal to the Ping Identity Portal.
-
In the Ping Identity Portal, click Next.
-
-
Wizard Step 3:
-
In the Configure Parameters section, select Deprovision on Rule Deletion.

Important - Do not change the default values of other parameters.
-
Click Save.
The wizard closes. The new connection you created for the Infinity Portal appears in the Provisioning menu > Connections tab. By default, this connection is not active.
-
In the top right, move the slider to the "on" position to activate the connection.
-
Step 3 - In the Ping Identity Portal, create a rule for the connection:
-
In the Provisioning menu, open the Rules tab.
-
Click the + button > New Rule.
The Create a New Rule window opens.
-
Enter a name for the rule.
-
Click Create Rule.
-
In the Available Connections section, to the right of the name of the connection you created for the Infinity Portal, click the + button.
-
Click Save.
Step 4 - In the Ping Identity Portal, add users to the rule:
-
Click the User Filter icon.
-
Next to User Filter, click the edit (pencil) button.
-
Create user filters. For more information, see Ping Identity documentation.
-
Click Save.
Step 5 - In the Ping Identity Portal, add attributes to the rule:
-
Click the Attribute Mapping icon.
-
Next to Attribute Mapping, click the edit (pencil) button.
-
Add these attributes:
PingOne Directory
myScim
Enabled
activeGiven Name
displayNameUser ID
externalIDUsername
userNamePrimary Phone
workPhone -
Click Save.
Step 6: In the Ping Identity Portal, add groups to the rule:
-
Click the Global Provisioning icon.
-
Click Add Groups.
-
Select groups to add to the rule.

Note - If groups are in a hierarchy, you must select the parent and the child group individually. Example: Group A is the parent of Group B. To add Group B to the rule, you must select Group A and Group B.
-
Click Save.
Step 7: In the Ping Identity Portal, apply the rule to the connection:
-
In the Configuration tab, make sure all of the values are correct.
-
In the top right, move the slider to the "on" position to apply the rules.
Review the details of the SSO configuration and click Submit.
|
|
Important - Create a user group with the applicable roles and assign it to the related IdP group name or ID. This depends on the applicable identity provider before you log out. For more information, see User Groups. |