Deploying the Harmony Mobile Protect app automatically (Zero Touch Deployment)
This section is optional.
UEM![]() Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point. solutions traditionally prompt the mobile device user to install the application once it is registered. In addition, to get full protection, the user needs to approve the required permissions and profiles. Many users are vigilant about installing new mobile applications or granting different permissions, and as a Security company, Check Point even encourages that. Most of them do not know that the Harmony Mobile Protect App is focused on device characteristics and behaviors and not the content stored on or flowing through the device. Furthermore, some users are incompliant with the company’s security policy
Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point. solutions traditionally prompt the mobile device user to install the application once it is registered. In addition, to get full protection, the user needs to approve the required permissions and profiles. Many users are vigilant about installing new mobile applications or granting different permissions, and as a Security company, Check Point even encourages that. Most of them do not know that the Harmony Mobile Protect App is focused on device characteristics and behaviors and not the content stored on or flowing through the device. Furthermore, some users are incompliant with the company’s security policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., especially when they use their own devices. Therefore, users often decide not to install the app or approve the required configuration. On top of that, users who do agree to install and accept the configurations will often not do it immediately, delaying the application activation. As a result, many devices remain exposed to potential cyber-attacks.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., especially when they use their own devices. Therefore, users often decide not to install the app or approve the required configuration. On top of that, users who do agree to install and accept the configurations will often not do it immediately, delaying the application activation. As a result, many devices remain exposed to potential cyber-attacks.
Harmony Mobile’s innovative zero-touch technology lets the Harmony Mobile Protect App to be installed and activated automatically without any user interaction.
The solution uses a VPN profile that is pushed automatically by Intune to the device and used by the Harmony Mobile protect app. When deployed, it runs the activation flow automatically, and the device becomes active and shows in the Harmony Mobile dashboard without the user opening the app on the device.
|
|
Note - If you selected Automatic integration in Configuring UEM Integration Settings, skip the procedures below and go to Deploying SSL Certificate (Zero Touch SSL). |
-
To set the zero touch flow you should create four new empty Security groups (See Creating Security Group for your Devices) with these names:
-
sbm_unregistered_ANDROID
-
sbm_registered_ANDROID
-
sbm_unregistered_IOS
-
sbm_registered_IOS
 Note - The group name is important here. So it is recommended to copy the group names from this document.
Note - The group name is important here. So it is recommended to copy the group names from this document.
-
-
For each group, assign Check Point application as the owner. In the New Group screen of the relevant group, select Owners and then choose Harmony Mobile application as the owner.
 Note - To find the Harmony Mobile application, enter Check Point Harmony Mobile. Intune does not search partial application names, for example, Harmony or Mobile.
Note - To find the Harmony Mobile application, enter Check Point Harmony Mobile. Intune does not search partial application names, for example, Harmony or Mobile.
Zero Touch Deployment for Android Enterprise devices
-
Add new Configuration Profile. Go to Devices > Configuration profiles > Create profile.
Platform type: Android Enterprise.
Profile: Device restrictions.
Give the profile a name, for example: Harmony_zero_touch_AE
-
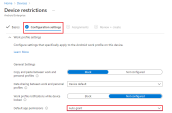
Under Configuration Settings tab > work profile settings > Default app permissions: Select Auto grant
-
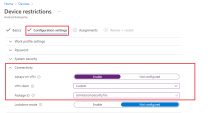
Under Configuration Settings > Connectivity pane configure:
-
Always-on VPN > Enable
-
VPN client > Custom
-
Package ID > com.lacoon.security.fox
-
-
Assign the profile to sbm_unregistered_ANDROID group that you created in the previous section, and exclude it from sbm_registered_ANDROID group.
Zero Touch Deployment for iOS devices
-
Add new Configuration Profile. Go to Devices > Configuration profiles > Create profile.
-
In Configuration settings enter the following:
-
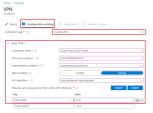
Connection type: Custom VPN
-
Connection name: Check Point Local Tunnel
-
VPN server address: www.checkpoint.com
-
Authentication method: Username and password
-
Split tunneling: Disable
-
VPN identifier: com.checkpoint.capsuleprotect
-
Custom VPN attributes: zero_touch = true
-
-
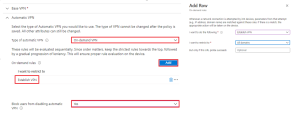
In Automatic VPN > Type of automatic VPN: On-demand VPN
-
On-demand rules > Add:
-
I want to do the following: Establish VPN
-
I want to restrict to: All domains
-
Block users from disabling automatic VPN: Yes
-
-
In iOS, you do not need to set the profile to the sbm_unregistered_iOS as you set in Android to sbm_unregistered_Android.
You need to set it to the Security Group which represents your Harmony Mobile users in Intune.
Select Platform: iOS/ iPadOS and from custom > select Profile type: VPN.
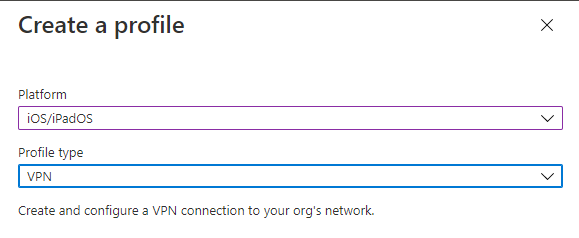
In Basics tab enter a name, for example: harmony_zero_touch_iOS
Zero Touch Notification Permissions for iOS
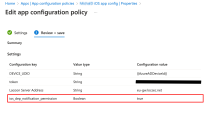
This feature automatically grants notification permission to Harmony Mobile Protect App when you install the app through UEM, without user interaction.
|
|
Important:
|
To enable Zero Touch notification permissions for iOS devices:
-
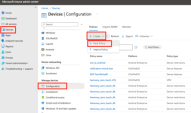
Go to Devices > Configuration and click Create > New Policy.
-
On the side panel:
-
In the Basics tab, enter a name for your profile and then click Next.
-
In the Configuration settings tab, click App Notifications and then click Add.
-
Do these:
-
Click Next.
-
In the Assignments tab, under Included groups, click Add groups and add your relevant groups.
-
Click Next.
-
Review the settings and then click Create.
Deploying SSL Certificate (Zero Touch SSL)
This section is relevant if you use the On device Network Protection (ONP) feature with the https inspection option turned on.
First, you need to create a certificate in Harmony Mobile Administrator Portal and then set the configuration on the UEM to push it to the devices. This certificate is used for the ONP SSL![]() Secure Sockets Layer. The standard security technology for establishing an encrypted link between a web server and a browser. Inspection.
Secure Sockets Layer. The standard security technology for establishing an encrypted link between a web server and a browser. Inspection.
Creating the certificate in the Harmony Mobile Administrator Portal
-
In the Harmony Mobile Administrator Portal, go to the Policy tab and expand your policy profile.
-
Click any one of these:
-
Device
-
Application
-
File
-
Network
-
-
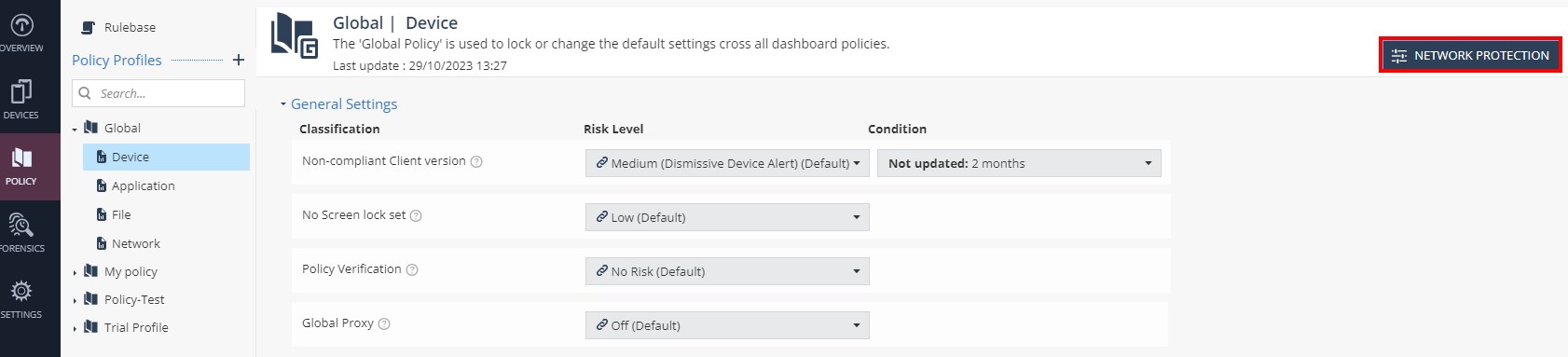
Click Network Protection.
-
In the Advanced Network Protection settings section, enable HTTPS Inspection.
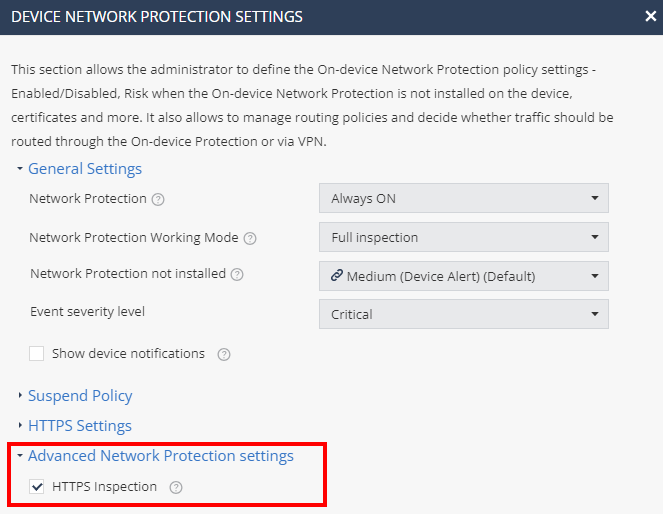
-
In the HTTPS Settings section:
-
Select Central CA for MDM deployment.
-
Click Generate CA Certificate.
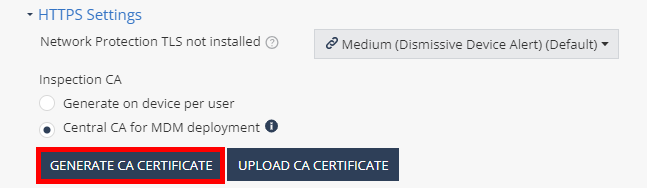
-
-
Click OK.
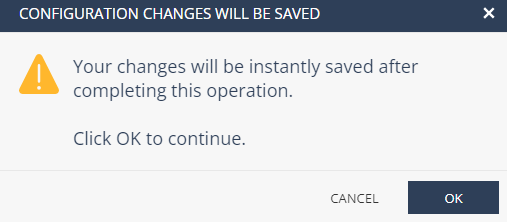
-
Enter the certificate name and click Add.
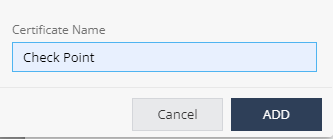
The system generates the CA certificate.
-
Click Download Certificate.
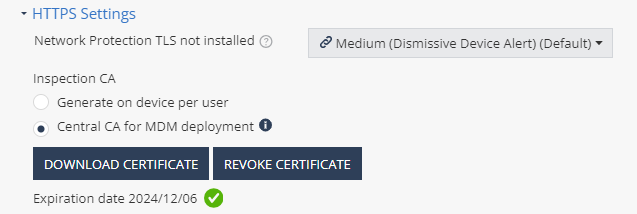
The system downloads the certificate to your computer.
|
|
Note - If you use different policies for device groups, the enforcement of the certificate pushed by the UEM may take up to 24 hours on iOS devices. This limitation is not relevant if the entire fleet of devices use the Global policy. |
Creating a certificate profile on the UEM:
-
For Android Enterprise devices:
-
Add new Configuration Profile. Go to Devices > Configuration profiles > Create profile.
-
Platform: Android Enterprise.
-
Profile: Trusted certificate
-
-
Upload the certificate that was downloaded from the policy in the Harmony Mobile dashboard

Note - After the download, the CA certificate is in crt format. Convert it to *.cer format before the upload. This is the format Intune requires.
-
Assign the Profile to your security group.
-
-
For iOS devices:
-
Add new Configuration Profile. Go to Devices > Configuration profiles > Create profile.
-
Platform: iOS.
-
Profile: Select Template and Trusted certificate
-
-
In Configuration Settings - upload the certificate that was downloaded from the policy in Harmony Mobile dashboard.

Note - After the download, the CA certificate is in crt format. Convert it to *.cer format before the upload. This is the format Intune requires.
-
In Assignment - Assign the Profile to your security group.
-
Review the profile and click Create.
-