Testing Methodologies
POC Type - Common Testing Methodologies
The most common testing methodologies are:
-
Penetration testing lab
-
Limited production deployment
-
Use cases test lab
Test Lab
The main objective is to demonstrate security value (POV) of Harmony Endpoint by executing test attack scenarios on several protected virtual machines with internet access but isolated from customer production environment.
Harmony Endpoint agents should enforce following best practice security policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection.:
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection.:
-
Anti-Malware
 A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. is mandatory and must be enabled for any penetration testing. Third-party signature Anti-Virus
A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. is mandatory and must be enabled for any penetration testing. Third-party signature Anti-Virus Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. can be used along with Harmony Endpoint, if Check Point's Anti-Malware blade is not chosen for the POC.
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. can be used along with Harmony Endpoint, if Check Point's Anti-Malware blade is not chosen for the POC. -
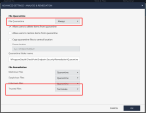
Use the predefined Optimized policy profile and then use the following setting to harden the Harmony Endpoint configuration:
-
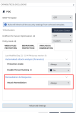
Set Attack Remediation to Always.
-
Go to Advanced Settings - Analysis and Remediation and select:
To maximize Harmony Endpoint’s catch rate in pentests or attack simulations, you can apply advanced custom settings. For more information, see Appendix A - Maximizing Harmony Endpoint Catch Rate in Pentests or Attack Simulations.
-
Limited Production Deployment
For production deployment, our aim is to provide maximum prevention while minimizing false positives and user impact with the following steps:

Deploy
See Installation and Deployment.
Tune
The default Threat Prevention policy mode, Optimized, is most suitable for maximizing prevention configuration and should be employed in production environments once the necessary exclusions have been defined.
As a best practice, we recommend using the Tuning mode profile for the on-boarding period in which the environment's unique software and network traffic is examined with the aim to create custom exclusions list based on detect logs.
Exclusions
-
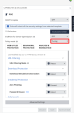
Go to Policy > Threat Prevention > Policy Capabilities > Global Exclusions and verify whether Smart Exclusions are enabled. If not, click Go to Smart Exclusions.
-
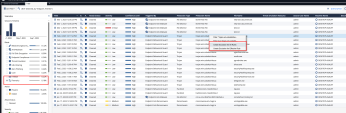
Once deployed in Detect or Tuning mode, review ongoing detections daily by filtering Forensics logs and excluding false positives.
-
Manually, based on the target’s attributes. For example, file hash/path, process path/signer, network destinations by IP/domain/FQDN/URL
-
Automatically by doing a right-click on the detection log:
-
Exclude only trusted software by digital signature CN. Refrain from excluding Microsoft, Oracle and other vulnerable software by certificates.
-
Do not exclude from forensic monitoring in case of false positives because relevant process activities will not be recorded in forensic logs and will be missing in forensic reports and Threat Hunting.
-
Exclude selected trusted applications from forensic monitoring only for client performance optimization with caution.
-
-
Exclusions can be added on Global or specific Threat Protection rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. level depending on the usage of excluded items.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. level depending on the usage of excluded items. -
Once all necessary exclusions are added, switch to Optimized security profile to stay protected in Prevent mode with automatic attack remediation.
For more information on Smart Exclusions, see Smart Exclusions.