Test Plans and Resources
Testing Resources
Client Demo Page
To view the Harmony Endpoint client demo page in Windows OS:
-
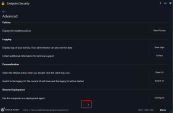
Open the Endpoint Security Client menu and go to Advanced.
-
Click > to go to the next screen.
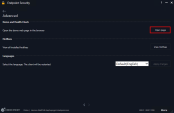
-
Go to Demo and Health Check > Open page.
Demo website: https://hep-demo.checkpoint.com/
To trigger a demo and health check for threat prevention blades:
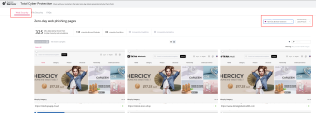
Total Cyber Security Portal on Partner MAP
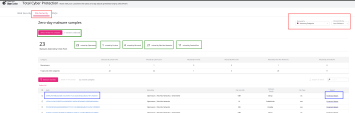
You can view the latest discovered zero-day malwares and zero-day phishing sites prevented by Harmony Endpoint on the total cyber security site (requires partner SE access and authentication). The website integrates Virus Total detection information, enabling users to compare and assess the effectiveness of Harmony Endpoint in relation to other security vendors.
On this page, you can also view the unique file hash of the malware, forensics reports created by Harmony Endpoint, and the Threat Emulation![]() Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. reports, if available.
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. reports, if available.
-
To view Zero-day phishing sites, go to Web Security > Harmony Browser extension and select the time period.
-
To view Zero-day malware, go to File Security > Harmony Browser extension and select the time period.
|
|
Notes:
|
CheckMe
CheckMe by Check Point is a proactive assessment that identifies security risks on your network, Endpoint, Cloud and Mobile environments. Based on this assessment, CheckMe instantly provides you with a detailed report that shows if your environments are vulnerable to ransomware, zero-day threats, malware infections, browser exploit, data leakage and more.
Use the Endpoint test to simulate attacks and trigger security responses. For more information on the tool and tests use, see sk115236.
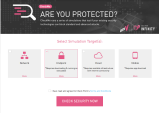
To use CheckMe checkup tool:
-
Visit the following URL:
-
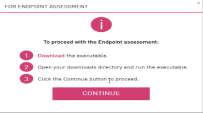
Select Simulation Target as Endpoint, accept the user agreement and click Check Security Now.
-
Download the executable and follow the instructions.
-
The test triggers these blades:
-
Threat Emulation
-
Anti-Exploit
-
Anti-Ransomware
The system creates a report and sends an email.
Other Free Third-Party POV Tools
-
Zero-day phishing sites: https://openphish.com/

Note - Some EDR/XDR competitors enforce OpenPhish feed and block all these sites by reputation. Emphasize the need of AI-based phishing protection in user browser.
-
Ransomware simulator by KnowBe4:
https://www.knowbe4.com/free-cybersecurity-tools/ransim

Note - Some exclusions might be required to avoid automatic quarantine of the simulation tool itself. See Testing Methodologies .
It is recommended to execute Ransim attacks one-by-one to generate dedicated detections and forensic reports.
|
|
Caution - Make sure to test third-party samples and tools in your lab with Harmony Endpoint prior to using them in POC with your customer. |
Test Plans
The following test plans provide instructions on how to demonstrate the main functionality of Harmony Endpoint. The proposed test plans will enable the verification of main functionalities, but they will not be based on actual malware.
Threat Prevention
|
Harmony Endpoint Engine |
Description |
Test Objective |
How to check |
|---|---|---|---|
|
Client Threat Prevention blades |
|||
|
Anti-Malware |
The Harmony Endpoint’s Anti-Malware blade effectively mitigates various malware threats, including worms, Trojans, adware, and keystroke loggers. |
Block file based on signature |
Use the following link to download an Eicar sample test files: |
|
Threat Emulation |
All files written on the file system are monitored and statically analyzed by Harmony Endpoint. If found as potentially malicious, the files will be emulated by sandboxing and quarantined if found as malicious. |
Block file based on sandboxing |
Use the Threat Emulation download on the Harmony Endpoint demo page:
|
|
Anti-Bot |
Harmony Endpoint identifies and blocks out-going communication to malicious C&C sites. |
Prevent connection to C&C servers |
Click the following link to simulate a bot site blocked by the endpoint:
|
|
Anti-Ransomware |
The Harmony Endpoint's Anti-Ransomware protection backups up user documents if a suspicious change is detected. In the event a detection occurs, all backed up files can be automatically restored. |
Prevent a ransomware attack and restore files that were harmed |
|
|
Forensics |
Harmony Endpoint automatically creates an incident analysis for every detection/prevention that occurs. This analysis should include process execution trees even across bots, if relevant. |
Analyze an attack |
|
|
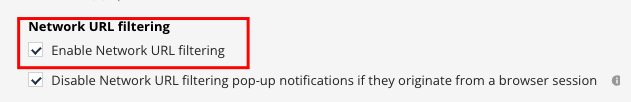
Harmony Endpoint provides URL filtering based on categories with additional block/allow listing. |
Utilize URLF to block sites based on categorization. |
|
|
|
Browser Protection |
|||
|
Zero-Phishing |
The Harmony Endpoint browser extension identifies every site that has user credentials in it. If it identifies such a site, the Harmony Endpoint browser extension uses a machine learning model to check the characteristics of the site, and determine whether the site is a phishing site. The technology is agnostic to the fact that site is a zero-day site, even new zero-days sites will be identified, assuming they are malicious phishing sites. |
Show and block a malicious credentials request |
|
|
Threat Emulation |
Every file downloaded by the user is sent to Check Point Sandboxing services, and is checked for any potentially malicious activity or content. If the file is found malicious, it will not be accessible to the user. |
|
|
|
The Harmony Endpoint browser extension is able to extract potentially malicious files from any active content, leaving the file clean from any potentially harmful content. The file can be either converted to a PDF format or left in its original format. |
|
||
|
Password Reuse |
The Harmony Endpoint browser extension prevents users from entering their corporate passwords on websites that do not belong to the corporate domain. |
|
Enter the demo trigger theft123 to any password field. Set password reuse protection policy:
|
Data Protection
The suggested use case outlines the main basic use cases for data protection. For support on advanced topics, contact the local Harmony expert.
|
Harmony Endpoint Engine |
Description |
Objective |
How to check |
|---|---|---|---|
|
Data protection |
|||
|
Port protection |
Harmony Endpoint’s Port Protection offers the ability to control the peripherals (keyboards, mice, DVDs, printers, USB storage devices, SmartPhones) that can be connected to the endpoint, with granular read / write / and encryption permissions based on device type, device_ID, and users/groups. |
|
|
|
Media Encryption |
Harmony Endpoint’s Media Encryption protects sensitive information by encrypting data and requiring authorization to access to storage devices, removable media and other input/output devices. |
Block writing and reading to an attached storage device for a user group |
|
|
Media Encryption |
Monitor file operations on external storage. |
Monitor the file that was copied, its location, the time of the copy, and the user responsible for the copy. Additionally, determine if the file was encrypted. |
|
|
|
Encrypt the internal drives and add pre-boot |
For additional guides, see sk112693. |
|
Access and Compliance
|
Harmony Endpoint Engine |
Description |
Objective |
How to check |
|---|---|---|---|
|
Access and Compliance |
|||
|
|
Block an application from running |
|
|
|
Application Control |
|
Block applications from a specific signer from running |
Create a new custom app rule and add only the signer to the rule. For example, google: |
|
Firewall |
|
Block a connection attempt to an IP or URL based on port\service. |
In Management:
In Endpoint: Open a connection with an FTP request. |
DLP and Gen AI Control
|
Harmony Endpoint Engine |
Description |
Objective |
How to check |
|---|---|---|---|
|
DLP and Gen AI |
|||
|
Paste event |
|
Block pasting data in AI domains |
In Management:
In Endpoint: Open an AI platform and try to paste an IP address. Paste will be blocked. |
|
Text Control (Send event) |
|
Block sending data in AI domains |
In Management:
In Endpoint: Open an AI platform and try to paste an IP address. Send will be blocked. |
|
Upload |
|
Block uploading data in domains of your choice. |
In Management:
In Endpoint: Open a cloud service (such as Dropbox, Google Drive or WhatsApp Web) and try to upload a document consisting of IP Addresses. Upload will be blocked. |
Posture Management
|
Harmony Endpoint Engine |
Description |
Objective |
How to check |
|---|---|---|---|
|
Vulnerabilities and Posture Management |
|||
|
Posture Management |
Harmony Endpoint provides the identification of vulnerabilities of operating systems and applications and classify them by levels of criticality based on real CVEs. |
Identify existing OS and applications vulnerabilities and provide the ability to patch them. |
In Management:
Once the scan is complete, the system displays a list of vulnerabilities to patch. Select the desired patches and click Patch. Make sure the endpoint is connected to the internet. The status of the patch is displayed as Complete. |
|
Patch Management |
Harmony Endpoint provides automatic patching of high and critical severity vulnerabilities of operating systems and selected applications. |
Automatically deploy available patches for identified vulnerabilities according to the policy based on vulnerability severity and included/excluded applications. |
In Management:
|
Threat Hunting
|
Harmony Endpoint Engine |
Description |
Objective |
How to check |
|---|---|---|---|
|
Threat Hunting |
|||
|
Basic Hunting: scripts |
Use Threat Hunting investigation tools for searching IoC. |
Use a pre-defined query for searching scripted process execution. |
|
|
Basic Hunting: cmd commands |
UseThreat Hunting investigation tools for searching IoC. |
Use a manual query to explore the usage of cmd command prompts. |
Use PROCESS record type > Process Name > Is > cmd.exe |
|
Security investigation based on Harmony Endpoint detection |
Use Threat Hunting investigation tools for searching Harmony Endpoint security events. |
Use a manual query to explore Harmony Endpoint detections. |
Use DETECTION EVENT record type > Detection Triggered By > Is > <Required blade> |
|
MITRE Att&CK |
Use Threat Hunting investigation tools for searching MITRE Attack techniques. |
Investigate the occurrence of attack techniques, as outlined in the MITRE ATT&CK Metrix. |
Query for common daily actions that can be classified to a known MITRE Att&ck technique. |
|
Incident Response Actions |
Threat Hunting provides incident remediation tools such as host isolation, process termination and forensics report. |
Use Threat Hunting incident remediation tools for initiating a host isolation, kill the process, quarantine file, generate a complete forensic report to investigate. |
Host Firewall Harmony Endpoint blade is mandatory for machine isolation.
Once initiated, the host will only communicate with Harmony Endpoint cloud management.
To release, use the release client Push Operation.
Use other response operations under Threat Hunting log context menu. They will create Push Operations which can be monitored under the relevant tab. Forensic report can be generated with or without attack remediation. |
|
Email alert on a defined bookmark |
You can save Threat Hunting queries as bookmarks. Once saved, it will send email notifications to users if Threat Hunting activity matches the query. |
Use any of the above use case to bookmark. |
To save a query as a bookmark, follow these instructions. |
|
Custom XDR detection rules |
Threat Hunting queries can be saved as custom XDR detection rules |
Create custom behavior-based detection and prevention rules |
Infinity XDR/XPR subscription is a must (also included into Harmony Endpoint Elite package).
|
IOC Management
|
Harmony Endpoint Engine |
Description |
Objective |
How to check |
|---|---|---|---|
|
IOC Management |
|||
|
Manual IOC Import |
You can add custom IoCs to trigger detection and prevention. |
Demonstrate import of custom IOCs and EPP+EDR enforcement |
|
|
Subscription to IOC feeds |
EDR and XDR can subscribe to third-party IoC feeds. |
Demonstrate capability to import live third-party IoCfeeds. |
|
Alerts and Notifications
|
Harmony Endpoint Engine |
Description |
Objective |
How to check |
|---|---|---|---|
|
Alerts and notifications |
|||
|
Basic Alerts |
Basic alerts allow you to receive email notifications for events.
|
Get an email alert for the following issues:
|
Use the following steps to configure |
|
Advanced Alerts |
Advanced alerts allows you to receive notifications for security and operational events. The notification is sent through preferred communication channels configured in Infinity Playblocks:
|
Receive a notification on a defined security event. |
Available on Infinity Portal only. (Powered by Playblocks – Notification automations are included in all Harmony Endpoint packages). Use the following steps to configure Advanced Alerts. |
|
Threat Hunting Bookmarked events |
You can add filters to a query and save it as a bookmark. You can also send email notifications to user if Threat Hunting activity matches the query. |
Receive an email alert on a defined query. |
Use the following instructions to save a query as a bookmark |