Device Posture
Device Posture allows you to specify the posture and authentication requirements for the device. If the requirements fail, then the Harmony Connect Agenton the device gets disconnected and blocks the access to internet and your corporate network.
Desktop Device Posture
Desktop Device Posture allows you to specify a set of posture policies for the device (Windows and macOS). If any one of the policy requirements fail, then the Harmony Connect Agent on the device gets disconnected with the security state Your Device Has Compliance Issues and blocks the access to internet and your corporate network.
The system validates the specified posture policy requirements each time a user logs in to the Harmony Connect Agent and then at one hour intervals. To view the compliance status of devices, see Compliance Logs.
|
|
Notes:
|
Supported Posture Policy Checks
|
Posture Requirement |
Windows |
macOS |
|---|---|---|
|
Specific or any Anti-Virus |
Yes |
Yes |
|
Minimum OS version in running on the device. |
Yes |
Yes |
|
The device is compliant according to Check Point Harmony Endpoint Security client. |
Yes |
Yes |
|
Specific or any firewall is active and up to date on the device.* |
Yes |
No |
|
The device has the specific Windows OS patches installed. |
Yes |
N/A |
|
Check for required or banned specific files on the device. |
Yes |
Yes |
|
Check for required or banned registry keys and values on the device. |
Yes |
Yes |
|
Check for required or banned processes on the device. |
Yes |
Yes |
|
Hard drive on the device is encrypted. |
Yes |
Yes |
|
Valid device certificate is installed trusted by a CA. |
Yes |
Yes |
* The supported third-party Firewall and Anti-Virus software are:
|
Windows |
macOS |
|---|---|
| Avast | Avast |
| Bitdefender | AVG |
| Broadcom (Symantec) | Avira |
| Check Point Harmony Endpoint | Bitdefender |
| Cisco | Symantec Endpoint Protection |
| CrowdStrike | CrowdStrike |
| Cybereason | Dr.Web |
| Kaspersky | Check Point Harmony Endpoint |
|
McAfee |
Kaspersky |
|
Microsoft |
McAfee |
|
Norton 360 |
ESET |
|
SentinelOne |
Norton 360 |
|
Sophos |
PcProtect |
|
Trellix |
ScanGuard |
|
TrendMicro |
|
|
Vmware Carbon Black |
|
Simulation Mode
The Simulation mode allows you to simulate (test) your posture policy configuration before you enforce it. The simulation result illustrates the compliance status of the connected devices and allows you can decide whether to enforce the posture policy or modify it accordingly.
To simulate the device posture policy requirements:
-
Click Policy > Access Control > Device Posture > Desktop Device Posture.
-
Turn on the Simulation mode toggle button.

Notes
-
In the simulation mode, the system changes the settings to the default simulation settings.
-
Internet Access and Device Authentication are disabled for the simulation.
-
-
Specify the posture requirements. Refer to Specifying the Posture Policy.
-
Click Save & Simulate.
The systems takes few minutes to complete the simulation. When the simulation is complete, it sends an email with the compliance status and attaches the report in .csv format.
-
Turn off the Simulation mode toggle button.
The system reverts to the pre-simulation-mode posture settings.
Specifying the Posture Policy
|
|
Note - The characters / \ : ; & % * ? < > { } [ ] are not supported for all fields except Domain List > Domain Name and Required keys > Value. |
-
Click Policy > Access Control > Device Posture > Desktop Device Posture.
-
Toggle Enforce desktop device posture for users with Harmony Connect Agent to On.
-
If the device is non-compliant, then specify whether you want to allow or block the internet access to the device:
-
Allow secured internet access if the device is not compliant
-
Block internet access if the device is not complaint
-
-
To specify the domain requirements, under Domain List:
-
Select The device belongs to the following domains(s).
-
In the Domain List table, enter the domain address and click +. To add multiple domains, repeat the step.

Notes:
-
! @ # $ % ^ & * ( ) + = [space] characters are not supported.
-
Maximum character limit is 64.
-
Must be separated by '.'.
-
-
Click Apply Changes.
-
-
To specify the posture requirements for Windows-based endpoints, expand Windows Posture Policy:

Note - The characters / \ : ; & % * ? < > { } [ ] are not supported for all fields except Required keys > Value.
-
Toggle Enforce device posture for Windows OS to On.
-
To verify that the specified Anti-Virus software is installed, up-to-date and running on the endpoint. select the Antivirus is active and up-to-date checkbox and from the list below, select the Anti-Virus software products.

Note - If you select Any, then the system verifies that any Anti-Virus software, regardless of the ones specified in the list, is installed, up-to-date and running on the endpoint.
-
To verify that the specified Windows OS version or higher is running on the endpoint, select the Windows OS minimum version, and from the list, and from the list, select the OS version.
-
To verify that the endpoint is compliant according to the Harmony Endpoint Security Client, then select the Device is compliant according to Check Point Harmony Endpoint checkbox.

Note - This applies only to endpoints with the Harmony Endpoint Security Client installed.
-
To verify that at least one of the specified firewall is installed and active on the endpoint, select the Firewall is active checkbox, and from the list below, select the firewall software products.
-
To verify that the endpoint has the specified Windows patches installed, select the Installed Windows patches checkbox, and in the Windows patches list table, enter the Windows patch name and click +. To add multiple Windows patches, repeat the step.
-
To verify that hard drives in the endpoint are encrypted, select the Check disk encryption checkbox, and select All disks should be encrypted or At least one disk should be encrypted.
-
To verify that certain files exist or do not exist (banned) in the specified path on the endpoint, select the Check files checkbox and click Required files or Banned files:
-
Click +.
-
In the Name field, enter the file name.
-
In the Path field, enter the path with forward slash. For example, C:/user/test.
-
Click Add.
-
Click OK to close the window.
-
-
To verify that certain registry keys exist or do not exist (banned) on the endpoint, select the Check registry keys checkbox and click Required keys or Banned keys:
-
Click +.
-
In the Name field, enter the registry key name. It must start with HKEY and must not end with \. For example, HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\Endpoint Security\Antex\InstallDir.
-
(Optional) In the Value field, enter the value of the registry key.
-
Click Add.
-
Click OK to close the window.
-
-
To verify that certain processes are running or not running (banned) on the endpoint, select the Check running processes checkbox and click Required processes or Banned processes:
-
Click +.
-
In the Name field, enter the process name with the extension .exe. For example, notepad.exe.

Note - To get the process name and path:
-
Open Task Manager.
-
Right-click the process.
-
Click Properties.
-
-
(Optional) In the Path field, enter the path with forward slash. For example, C:/Windows/System32.
-
Click Add.
-
Click OK to close the window.
-
-
Click Apply Changes.
-
-
To specify the posture requirements for macOS-based endpoints, expand Mac Posture Policy:

Note - The characters / \ : ; & % * ? < > { } [ ] are not supported for all fields except Required keys > Value.
-
Toggle Enforce device posture for Mac OS to On.
-
To verify that the specified Anti-Virus software is installed and running on the endpoint. select the Any of the following endpoint's antivirus products is active checkbox and from the list below, select the Anti-Virus software products.

Notes:
-
This is supported only with the Harmony Connect Agent version 1.5.0 or later.
-
If you select Any, then the system verifies that at least one of the specified Anti-Virus software in the list is installed and running on the endpoint.
-
-
To verify that the specified Windows OS version or higher is running on the endpoint, select the Mac OS minimum version, and from the list, and from the list, select the OS version.
-
To verify that the endpoint is compliant according to the Harmony Endpoint Security Client, then select the Device is compliant according to Check Point Harmony Endpoint checkbox.

Note - This applies only to endpoints with the Harmony Endpoint Security Client installed.
-
To verify that hard drives in the endpoint are encrypted, select the Check disk encryption checkbox, and select All disks should be encrypted or At least one disk should be encrypted.
-
To verify that certain files exist or do not exist (banned) in the specified path on the endpoint, select the Check files checkbox and click Required files or Banned files:
-
Click +.
-
In the Name field, enter the file name.
-
In the Path field, enter the path with forward slash. For example, C:/user/test.
-
Click Add.
-
Click OK to close the window.
-
-
To verify that certain processes are running or not running on the endpoint, select the Check running processes checkbox and click Required processes or Banned processes:
-
Click +.
-
In the Name field, enter the process name.
-
(Optional) In the Path field, enter the path with forward slash. For example, C:/Windows/System32.
-
Click Add.
-
Click OK to close the window.
-
-
Click Apply Changes.
-
-
To view a log of changes made to the Desktop Device Posture settings, go to Global Settings > Audit Logs.
-
To view the compliance status of all devices in the organization, go to Assets > Users > View > Trusted Devices and view the Device Posture column:
-
Compliant
-
Not Compliant – Click
 to view the reasons and fix them.
to view the reasons and fix them. -
Not Required - If the Desktop Device Posture feature is disabled.
-
Device Authentication
Device Authentication authenticates a device by verifying the valid certificate installed on it by a trusted Certificate Authority (CA) uploaded by you. The verification happens each time Harmony Connect Agent connects to the Harmony Connect cloud![]() An administrator approved Harmony Connect cloud location that processes the internet and corporate traffic. or when you upload or modify CA certificates. If the verification fails, then the agent disconnects and the security state warning appears: Your Device Has Compliance Issues.
An administrator approved Harmony Connect cloud location that processes the internet and corporate traffic. or when you upload or modify CA certificates. If the verification fails, then the agent disconnects and the security state warning appears: Your Device Has Compliance Issues.
|
|
Notes:
|
Uploading the CA Certificate
-
Go to Policy > Access Control > Access Conditions.
-
Under Device Authentication:
-
Select the A valid device certificate is installed on the device which is trusted by the following CA checkbox.
-
Click
 to browse and upload the certificate.
to browse and upload the certificate. The system adds the certificate to the table. The table shows the issuer and the validity period of the certificate
-
To download a certificate, select the certificate in the table, and click
 .
. -
To delete a certificate, select the certificate in the table, and click
 .
.
-
Installing a Valid Certificate on the Device
On the device, install a valid certificate with a private key that is trusted by any one of the Certificate Authority (CA) issued certificates uploaded.
|
|
Note - The device certificate must be of the type base-64-encoded x.509. |
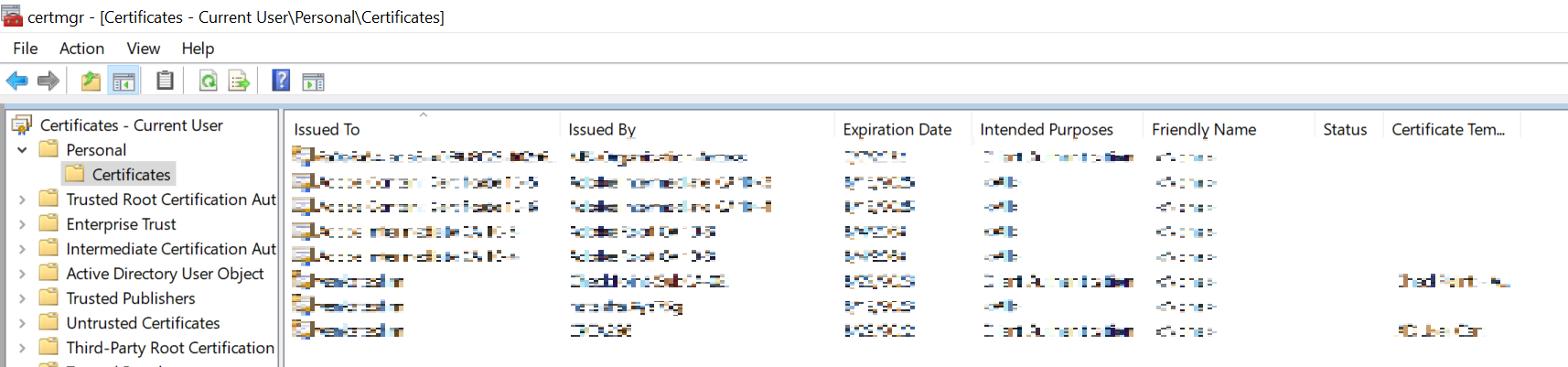
For Windows, open Manage user certificates and install the certificate with a private key under Certificates > Personal.
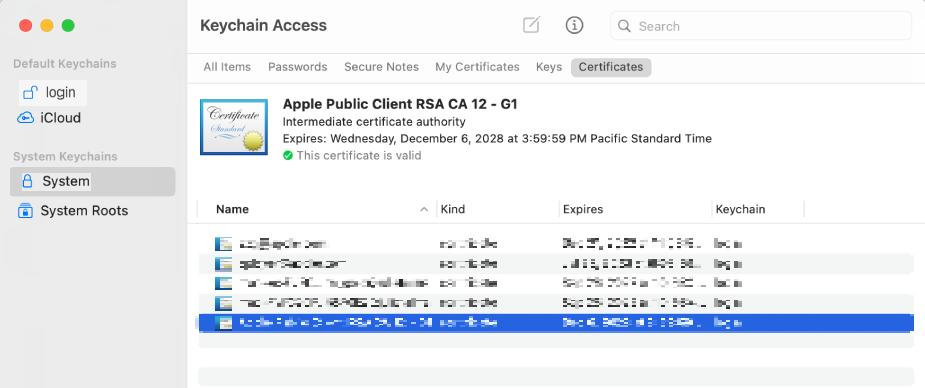
For macOS, open the Keychain Access app and install the certificate with a private key under System Keychains > System > Certificates.