Reviewing Phishing Events
Phishing events are triggered by the Anti-Phishing and Click-Time Protection security engines.
The Anti-Phishing security engine prevents the most sophisticated phishing and spam emails from being delivered to the end users' mailboxes.
The Click-Time Protection security engine re-writes the links in emails, emulates and checks the reputation of websites behind the links every time an end user clicks on them.
Acting on Phishing Events
|
|
Note - When a user reports a phishing email, the reported email is moved to the Deleted folder in the user's mailbox. If the phishing report is later declined, the email remains in the Deleted folder. |
To review and investigate the phishing event:
-
To see reasons for the detection of an event as phishing, under Security Stack, click More Info for Anti-Phishing.
-
To investigate the header of the raw email, under Email Profile, click Show for Header from raw email.
-
To investigate the body of the raw email, under Email Profile, click Show for Show body from raw email.
-
To download the raw email, under Email Profile, click Download for Download this email.

Note - You must have View All Sensitive Data or View Sensitive Data only if Threats are Found Specific Service Roles assigned to you to see or download the raw emails. For information about roles, see Managing Users, Roles and their Permissions.
-
To send the original email to the end-user, under Email Profile, click Send for Send Original Email.
Note - This option appears only when there are links that were re-written by the Click-Time Protection security engine.
-
To recheck the email for phishing, under Email Profile, click Recheck for Recheck email.
To filter emails similar to the event generated:
-
Under Security Stack, select Similar Emails / Create Rules.
-
Under Filters, define the criteria for filtering the emails.
-
Click Search.
|
|
Note - After filtering the emails, you can create Anti-Phishing Allow-List and Block-List. See Anti-Phishing Exceptions. |
To report mis-classification of an event:
-
Under Security Stack in the event profile, click Report mis-classification for Anti-Phishing.
-
Under Report this email as, select how you want to classify the event:
-
Legit Marketing Email
-
Clean Email
-
Spam
-
Phishing
-
-
Under How confident are you, select how confident you are about the classification you selected:
-
Not so sure
-
Medium confidence
-
High confidence
-
-
Click OK.
Post-delivery Email Recheck
Sometimes emails are rechecked after delivering to the end user mailbox, which may result in emails being removed from the user mailbox.
Post-delivery email recheck can be initiated in these cases:
-
Recheck initiated by the inputs from the end users (reported phishing, malicious url clicks) and other sources.
-
Emails are processed by the Anti-Phishing security engine and when needed by the Check Point security analysts.
-
When a global block action is issued. The block action includes all emails that match the relevant match criteria, across all protected mailboxes.
-
Emails processed by the relevant policy workflows.
When a policy is configured to block emails, the emails are removed from the mailbox and placed in quarantine. Harmony Email & Collaboration generates the relevant security events and sends the email notifications.
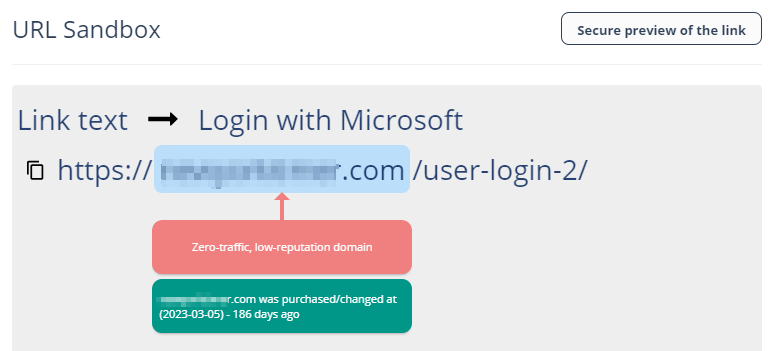
Reviewing Malicious Links
Link Analysis card on the Email Profile page shows the reasons why Harmony Email & Collaboration flagged links and QR codes as malicious or not. It also shows a secure preview (image) of the link.
For information about the malicious QR codes, see Detecting Malicious QR Codes.
To review and investigate the malicious links: