Google Drive
Overview
Google Drive is a cloud storage system that allows file sharing and collaboration. Harmony Email & Collaboration adds security, privacy, and compliance to Google Drive by scanning files shared in Google Drive for malicious content and data loss prevention (DLP) and generates actionable events on malicious content.
How it works
Harmony Email & Collaboration adds a layer of security that provides these security features for Google Drive:
-
Data Leak Prevention (DLP): Protecting uploaded files containing sensitive data
-
Anti-Malware: Scanning of files for malicious content
-
Remediation: Quarantine malicious files and files containing sensitive data.
Harmony Email & Collaboration scans files in the following scenarios:
-
A new file is created
-
A file is uploaded
-
A file is modified (edited)
-
A file or directory is shared with new members
|
|
Note - Harmony Email & Collaboration starts scanning files from the time of installation. Files that existed prior to installation are not scanned retroactively. |
Required Permissions
The cloud state for Google Drive used by Harmony Email & Collaboration is composed of the following entities:
-
Users
-
Groups and Memberships
-
Tokens
-
Apps
-
Files and Folders
-
Permissions
Once the cloud state is saved, Harmony Email & Collaboration starts monitoring the changes for each user. To track changes for each user in the cloud, Harmony Email & Collaboration uses the following channels:
-
Subscribe each user to Google Push Notifications for changes (https://developers.google.com/drive/v3/web/push).
-
Fallback to polling each user every minute if push notifications fails (https://developers.google.com/drive/v3/web/manage-changes)
-
Subscribe each user to Google Reports API to get its activities related to permissions, authorization to external apps, and tokens. ( https://developers.google.com/admin-sdk/reports/v1/get-start/getting-started)
Harmony Email & Collaboration uses the following resources for Google Drive from the APIs:
-
Files and Folders metadata (not include file contents)
-
Users and Groups metadata
-
Permissions
-
Changes (not including the content of files changed)
-
Channels
-
Tokens
-
Applications
Activating Google Drive
For details about the procedure to activate Google Drive, see Activating Google Drive.
Deactivating Google Drive
To deactivate Google Drive:
Google Drive Security Settings
Customizing Quarantine
Administrators can customize the quarantine folder and location (email address).
Quarantine folder
The quarantine folder is used to quarantine malware-infected files and files containing sensitive information that does not comply with the organization's data-sharing policies. All these files will be quarantined to a single predefined quarantine folder.
|
|
Notes:
|
Configuring Google Drive Policy
Malware Policy
By default, the Google Drive malware policy scans the uploaded files for malicious content.
Supported Actions
Google Drive malware policy supports these actions:
-
Quarantine malware-infected files.
-
Alert owner: Sends an email notification to the user who uploaded a file that contains malicious content.
-
Alert admin(s): Sends an email notification to the admin(s) about the malicious files.
Configuring Malware Policy
To configure Malware policy:
-
Click Policy on the left panel of the Harmony Email & Collaboration Administrator Portal.
-
Click Add a New Policy Rule.
-
From the Choose SaaS drop-down list, select Google Drive.
-
From the Choose Security drop-down list, select Malware and click Next.
-
Select the desired protection mode (Detect and Remediate or Detect).
If required, you can change the Rule Name.
-
Choose Scope for the policy.
-
To apply the policy to specific users or groups, select the users and groups and click Add to Selected.
-
To apply the policy to all users and groups in your organization, enable All Users and Groups checkbox.
-
To exclude specific users or groups from the policy, select the users/groups and click Add to Excluded.
-
-
Under Blades, select the threat detection blades required for the policy.
Note - To select all the blades available for malware detection, enable All running threat detection blades checkbox.
-
Under Suspected malware workflow (Attachment) in Workflows, select the workflow required for the policy.
-
Quarantine. User is alerted and allowed to restore
-
Quarantine. User is alerted, allowed to request a restore (admin must approve)
-
Quarantine. User is not alerted (admin can restore)
-
Do nothing
Note - The Workflows are available only when Detect and Remediate protection mode is enabled.
-
-
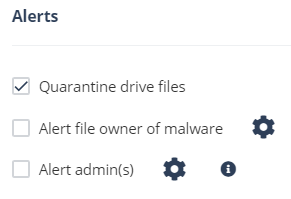
To quarantine malware-infected files, enable the Quarantine drive files checkbox.
Note - This option will be available only in Detect and Remediate protection mode.
-
Configure Alerts for the policy.
-
To send email alerts to the file owner of malware, enable the Alert file owner of malware checkbox.
-
To send email alerts to admin(s) about malware, enable the Alert admin(s) checkbox.
Notes:
-
Even when the alerts are enabled here in the policy, the administrator only receives email alerts for security events when Receive Alerts role is enabled in the Specific Service Role. For more details about managing roles and permissions in the Infinity Portal, refer to Global Settings > Users in Infinity Portal Administration Guide.
-
To customize the email alert templates, click on the gear icon to the right of the alert.
-
-
Click Save and Apply.
DLP Policy
By default, the DLP policy scans the uploaded files to Google Drive for potentially leaked information, such as credit card number and Social Security Number (SSN).
Supported Actions
Google Drive DLP policy supports these actions:
-
Quarantine potentially leaked information files.
-
Alert owner: Sends an email notification to the user who uploaded a file that contains sensitive information.
-
Alert admin(s): Sends an email notification to the admin(s) about the files that contain sensitive information.
Configuring DLP Policy for Google Drive
To configure DLP policy:
-
Click Policy on the left panel of the Harmony Email & Collaboration Administrator Portal.
-
Click Add a New Policy Rule.
-
From the Choose SaaS drop-down list, select Google Drive.
-
From the Choose Security drop-down list, select DLP and click Next.
-
Select the desired protection mode (Detect and Remediate or Detect).
If required, you can change the Rule Name.
-
Choose Scope for the policy.
-
To apply the policy to specific users or groups, select the users and groups and click Add to Selected.
-
To apply the policy to all users and groups in your organization, enable All Users and Groups checkbox.
-
To exclude specific users or groups from the policy, select the users/groups and click Add to Excluded.
-
-
Under DLP Criteria, select the DLP categories required for the policy.
For more information about the DLP Data Types and categories, see Appendix E: DLP Built-in Data Types and Categories.
-
Select the sensitivity level required for the policy.
-
Very high (hit count > 0)
-
High (hit count > 2)
-
Medium (hit count > 5)
-
Low (hit count > 10)
-
Very Low (hit count > 20)
-
-
To exclude DLP policy for the messages and files shared only with the internal users, enable the Skip Internal items checkbox.
-
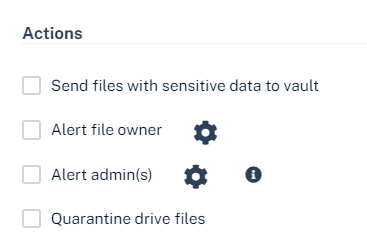
Configure the Actions required for the policy.
-
To send files with sensitive data to vault, select the Send files with sensitive data to vault checkbox.
-
To send email alerts to admins about DLP, select the Alert admin(s) checkbox.
-
To send email alerts to the file owner about DLP, select the Alert file owner(s) checkbox.
-
To send a detected file with sensitive data to quarantine (no access for the file owner), select the Quarantine drive files checkbox.
Notes:
-
Even when the alerts are enabled here in the policy, the administrator only receives email alerts for security events when Receive Alerts role is enabled in the Specific Service Role. For more details about managing roles and permissions in the Infinity Portal, refer to Global Settings > Users in Infinity Portal Administration Guide.
-
To customize the email alert templates, click on the gear icon to the right of the alert.
-
-
Click Save and Apply.
Viewing Google Drive Security Events
Harmony Email & Collaboration records the Google Drive detections as security events. The event type depends on the type of policy that created the event. You can handle the security events in different ways, whether they are detected/prevented automatically or discovered by the administrators after not being prevented.
The Events screen shows a detailed view of all the security events.
Action on Files Placed in Vault
When a data leak is detected in a file, Harmony Email & Collaboration takes these steps:
-
Revokes the file permissions.
-
Moves the file to a secure Vault folder.
Harmony Email & Collaboration stores this vault folder on the user's local drive and cannot be shared with others.
Vault Action in Externally Shared Drives
For files stored in My Drive, access is managed by the file owner unless the file or folder is specifically shared with others.
For shared drives, when the drive is shared externally, the permissions set on the drive apply to all files within it.
|
|
Note - If a drive is shared externally, the standard Vault process may not function as expected. It is not possible to revoke access from individual files as they inherit permissions from the shared drive. |
To restrict external access, the permissions of the entire drive must be modified. However, customers often prefer to limit access to a specific files flagged by a Data Loss Prevention (DLP) policy without impacting the entire drive.
Handling DLP Detections on Externally Shared Drives
To manage DLP detections on externally shared drives, these configuration options are available to control the Vault:
-
Use Vault Folder (Default): Removes direct permissions (not inherited from the shared drive) from the file and moves it to a Vault folder at the root of the drive. This ensures the file remains accessible internally while preventing external access.
-
Use Quarantine as Vault: Transfers the file to a quarantine location within Check Point's infrastructure.
-
Fail Vault Action: If a DLP detection occurs on an externally shared drive, selecting this option causes the Vault action to fail, returning an error and ensuring no changes are made if that is the preferred behavior.