Introduction to CloudGuard CNAPP
Check Point CloudGuard Cloud Native Application Protection Platform (CNAPP) is a SaaS platform that provides unified cloud-native security across your applications, workloads, and network. You can use it to automate security, prevent threats, get compliance and manage posture for all of your cloud environments: from Amazon AWS![]() Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. and Microsoft Azure
Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. and Microsoft Azure![]() Collection of integrated cloud services that developers and IT professionals use to build, deploy, and manage applications through a global network of data centers managed by Microsoft®. to GCP
Collection of integrated cloud services that developers and IT professionals use to build, deploy, and manage applications through a global network of data centers managed by Microsoft®. to GCP![]() Google® Cloud Platform - a suite of cloud computing services that runs on the same infrastructure that Google uses internally for its end-user products, such as Google Search, Gmail, Google Drive, and YouTube., Kubernetes
Google® Cloud Platform - a suite of cloud computing services that runs on the same infrastructure that Google uses internally for its end-user products, such as Google Search, Gmail, Google Drive, and YouTube., Kubernetes![]() Kubernetes, often abbreviated as “K8s”, orchestrates containerized applications to run on a cluster of hosts., and more.
Kubernetes, often abbreviated as “K8s”, orchestrates containerized applications to run on a cluster of hosts., and more.
Protect your Private and Public Clouds
CloudGuard CNAPP![]() Cloud-Native Application Protection Platform - a cloud-native security model that encompasses Cloud Security Posture Management (CSPM), Cloud Service Network Security (CSNS), and Cloud Workload Protection Platform (CWPP) in a single holistic platform. ensures network security and enforces security policy, prevents changes not approved, and enforces the previously defined configuration. Regardless if you use public or private clouds, CloudGuard CNAPP facilitates server configuration management. Its flexible security management tools ensure compliance and decreases configuration errors and possible breaches.
Cloud-Native Application Protection Platform - a cloud-native security model that encompasses Cloud Security Posture Management (CSPM), Cloud Service Network Security (CSNS), and Cloud Workload Protection Platform (CWPP) in a single holistic platform. ensures network security and enforces security policy, prevents changes not approved, and enforces the previously defined configuration. Regardless if you use public or private clouds, CloudGuard CNAPP facilitates server configuration management. Its flexible security management tools ensure compliance and decreases configuration errors and possible breaches.
Its powerful layer of Threat Intelligence transforms cloud big data into high-definition, actionable security logic. Customize alerts and built-in queries, quarantine threats, and stop attacks in progress.
Secure Kubernetes Containers
CloudGuard CNAPP offers a depth of coverage for all container types, rich visualization of cloud assets, and an assessment of security posture to quickly identify misconfiguration issues and threats. Understand at a glance what is running in your container environment and how it is configured. Visualize Kubernetes data flows and get visibility of container misconfigurations and anomalies.
Create and Manage Custom Compliance Rules
Create custom compliance rules with intuitive GSL language, and align with NIS and CIS security benchmarks, with the largest number of rulesets and compliance frameworks across cloud environments.
The main menu along the left side of the main screen provides navigation to the CloudGuard pages and features. You can search through the menu items with the search bar located above the menu (Search Navigation). Start to enter the name of the page, and CloudGuard offers you a list of menu items with this name.
The menu options appear as sections in this Administration Guide.
|
|
Note - The search of the Code Security menu items is not supported. |
|
Menu Icon |
Section in this Guide |
Description |
|---|---|---|
|
|
|
Get to know CloudGuard:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Use Intelligence to hunt for and visualize threats and anomalous behavior in your environments through cloud log files |
|
|
|
Build the Code Security functionality into your CI/CD pipeline to detect and prevent risk in cloud deployments |
|
|
|
Generate reports that show summaries, trends, and insights based on data that CloudGuard collects. |
|
|
|
Enable seamless integration with internal and external third-party applications, APIs, and services. |
|
|
|
|
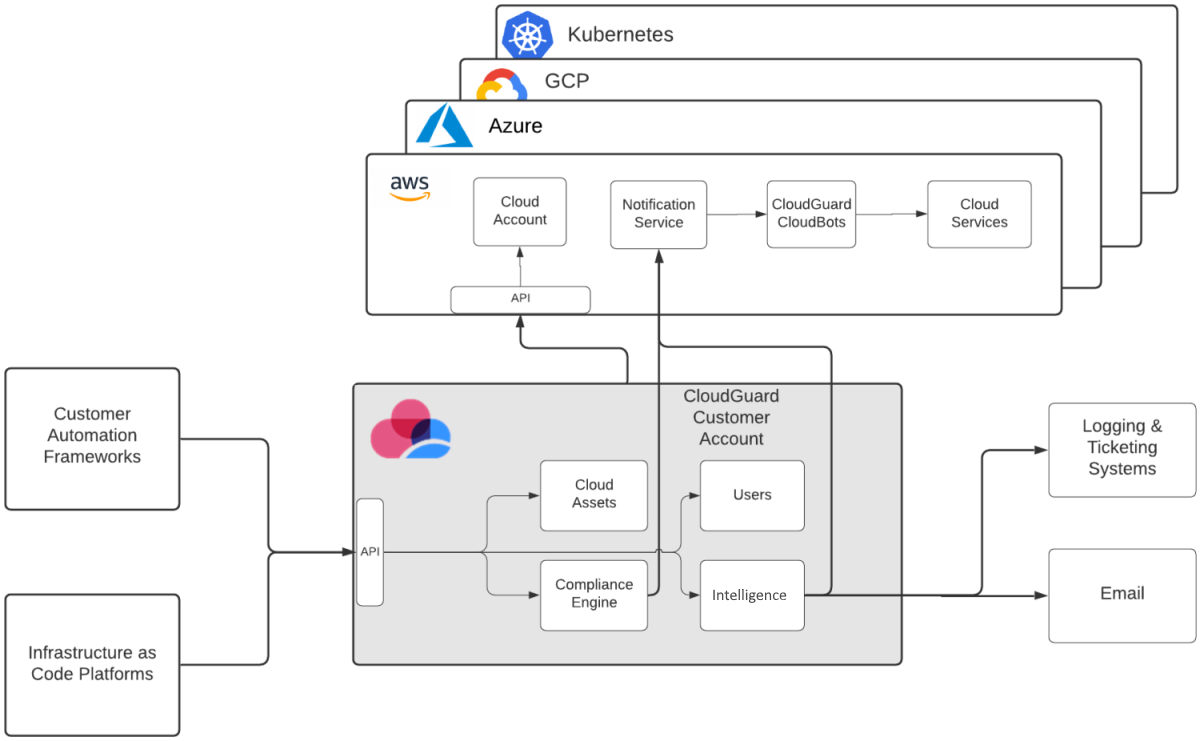
The diagram below shows the architecture for the CloudGuard portal.
CloudGuard is connected to cloud platforms with the correct platform APIs and platform notification services, such as SNS for AWS. In addition, CloudGuard can connect to logging, ticketing, and email systems, such as ServiceNow and PagerDuty, to forward CloudGuard alerts.
Upstream, corporate systems can connect to CloudGuard with its REST API![]() Also known as RESTful API - an application programming interface (API or web API) that conforms to the constraints of REST architectural style and allows for interaction with RESTful web services., to implement automation processes to manage activities on CloudGuard. Moreover, users can use Infrastructure as Code systems, such as Terraform
Also known as RESTful API - an application programming interface (API or web API) that conforms to the constraints of REST architectural style and allows for interaction with RESTful web services., to implement automation processes to manage activities on CloudGuard. Moreover, users can use Infrastructure as Code systems, such as Terraform![]() An infrastructure as code tool that lets you define both cloud and on-prem resources in human-readable configuration files that you can version, reuse, and share. or AWS CloudFormation, to connect to CloudGuard.
An infrastructure as code tool that lets you define both cloud and on-prem resources in human-readable configuration files that you can version, reuse, and share. or AWS CloudFormation, to connect to CloudGuard.