Asset Details
This page contains all the details of a specific asset in your onboarded environment. Use tabs on the left to navigate between different types of information about the asset. The number and type of the asset tabs can differ based on the asset type.
The top of the screen shows the basic asset details, such as name, type, or ID. These parameters depend on the asset type. For some assets, this part shows information related to the asset's risks: business priority, risk score, or exposure.
Symbols
Based on the asset type, permissions, and connected services, asset details can have these symbols:
|
Icon |
Meaning |
Explanation |
|---|---|---|
|
|
Risk score |
Read more in Risk Calculation |
|
|
Read more in Entitlement Map |
|
|
|
Business priority |
Read more in Business Priority |
|
|
Network exposure |
Read more in Network Exposure and IAM Exposure |
|
|
Base Image |
Read more in Base Image |
|
|
Vendor Image |
Read more in Vendor Image |
The overview page displays important high-level information on the asset.
Risk Management
For assets supported in Risk Management, the Risk Management section shows the data considered for the calculation of the asset risk score, as well as the Context Graph and top remediation actions to mitigate the asset's risk.
Context Graph
The Context Graph is a graphical representation of the asset exposure to the Internet and to other assets in the network. It is applicable to AWS![]() Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. EC2
Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. EC2![]() Amazon EC2 - A web service for launching and managing Linux/UNIX and Windows Server instances in Amazon data centers. instances, Lambda functions, RDS
Amazon EC2 - A web service for launching and managing Linux/UNIX and Windows Server instances in Amazon data centers. instances, Lambda functions, RDS![]() Relational Database Service (RDS) - A web service that makes it easier to set up, operate, and scale a relational database in the cloud. It provides cost-efficient, resizable capacity for an industry-standard relational database and manages common database administration tasks., ECS
Relational Database Service (RDS) - A web service that makes it easier to set up, operate, and scale a relational database in the cloud. It provides cost-efficient, resizable capacity for an industry-standard relational database and manages common database administration tasks., ECS![]() Amazon Elastic Container Service (ECS) - a fully managed container orchestration service that helps you deploy, manage, and scale Docker containers running applications, services, and batch processes. service, and Azure
Amazon Elastic Container Service (ECS) - a fully managed container orchestration service that helps you deploy, manage, and scale Docker containers running applications, services, and batch processes. service, and Azure![]() Collection of integrated cloud services that developers and IT professionals use to build, deploy, and manage applications through a global network of data centers managed by Microsoft®. Virtual Machines.
Collection of integrated cloud services that developers and IT professionals use to build, deploy, and manage applications through a global network of data centers managed by Microsoft®. Virtual Machines.
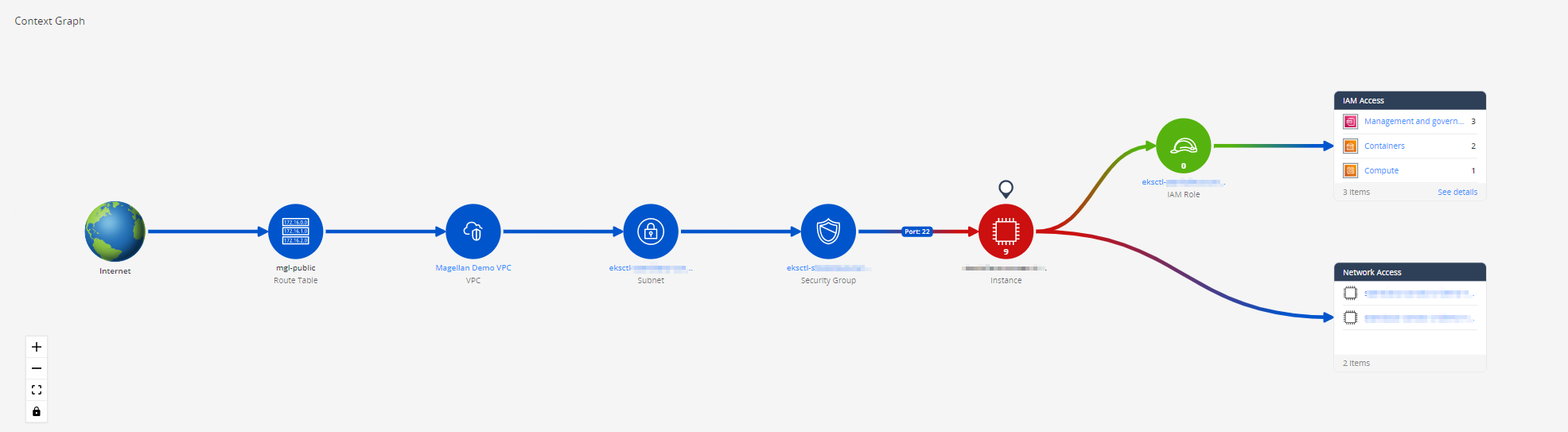
The Context Graph presents the configuration blocks that determine if the asset is exposed to the Internet or not (see Network Exposure).
When you put the cursor on a graph node, its tooltip shows important high-level information about the asset.
The Context Graph presents the potential impact that the asset exploit can have on the cloud environment, from a network and IAM perspective. The IAM impact is determined by CIEM, which analyzes the permissions granted to the asset. The network impact is based on an analysis of security groups.
The node color on the graph aligns with the risk level. Assets in blue are not supported in Risk Management and therefore do not have a risk score.
The assets with the highest business priority (Business Priority), Crown Jewels, have a little crown symbol.
Open Ports
For AWS EC2 instances, the Context Graph shows the open ports of the security group connected to the instance and their categories, such as Web Server, Database, or Checkpoint Service.
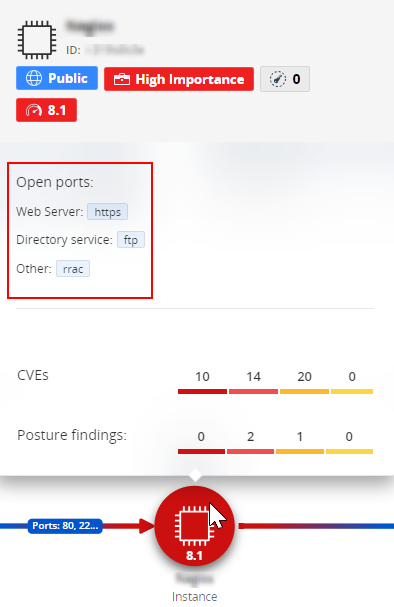
For the port details, put the cursor on the port number to see its tooltip.
Top 5 Remediations
This section shows the top 5 actions that you need to do to reduce the risk score of the asset. Click one of them to open a relevant tab with more details.
Events
This widget shows the number of critical and high-severity security events and posture findings the asset has.
Images
-
Policy status - Shows if the image meets your organization standards (compliant / non-compliant)
-
Risk score - Calculated risk score of the image
-
Vulnerability by severity - Statistics for severity level of Image Assurance findings
-
Vulnerability by category - Statistics for categories of Image Assurance findings
-
Workloads - The list of workloads that use this image
-
Kubernetes
 Kubernetes, often abbreviated as “K8s”, orchestrates containerized applications to run on a cluster of hosts. image shows workloads in the environment that uses it
Kubernetes, often abbreviated as “K8s”, orchestrates containerized applications to run on a cluster of hosts. image shows workloads in the environment that uses it -
Container Registry
 A collection of repositories used to store and access container images. image shows workloads from all Kubernetes environments
A collection of repositories used to store and access container images. image shows workloads from all Kubernetes environments
-
-
Scan status - Shows the results of scanning the image by CloudGuard agents. For more information, see Image Scan Status.
Software Bill of Materials (SBOM) is a list of all licenses that govern the components, the versions of the components used in the code, and their patch status. This list helps you quickly identify any security or license risk.
Supported Assets
CloudGuard shows SBOM for:
-
Virtual Machines
-
EC2 instances
-
Function apps
|
|
Note - SBOM is available only for assets scanned with Agentless Workload Posture and Scan Engine V2. |
SBOM Export
On the asset page, go to the SBOM tab to see information about all the packages in the applicable asset.
To see the information in a file, click the SBOM Export button and select the export format. It can take some time for CloudGuard to generate the requested file.
This page shows the CVEs, threats, and secrets received through the asset scanning. The Remediation Summary page contains information that a specific scanner finds.
Scanner examples:
To search for a specific CVE![]() The Common Vulnerabilities and Exposures (CVE) system provides a reference-method for publicly known information-security vulnerabilities and exposures., click Search CVE and go to the Vulnerability Search page.
The Common Vulnerabilities and Exposures (CVE) system provides a reference-method for publicly known information-security vulnerabilities and exposures., click Search CVE and go to the Vulnerability Search page.
For more information, see Entitlement Map.
This page presents the part of the Posture Findings related to this asset.
For more information, see All Events.
This page presents the part of the Threat & Security Events related to this asset.
For more information, see All Events.
This page shows the asset properties based on the asset type.
This page shows part of the traffic logs for the asset.
For more information, see Traffic Explorer.
This page shows part of the account activity logs for the asset.
For more information, see Activity Explorer.