041
CHECK POINT 2013 SECURITY REPORT
06
_ SUMMARY AND SECURITY STRATEGY
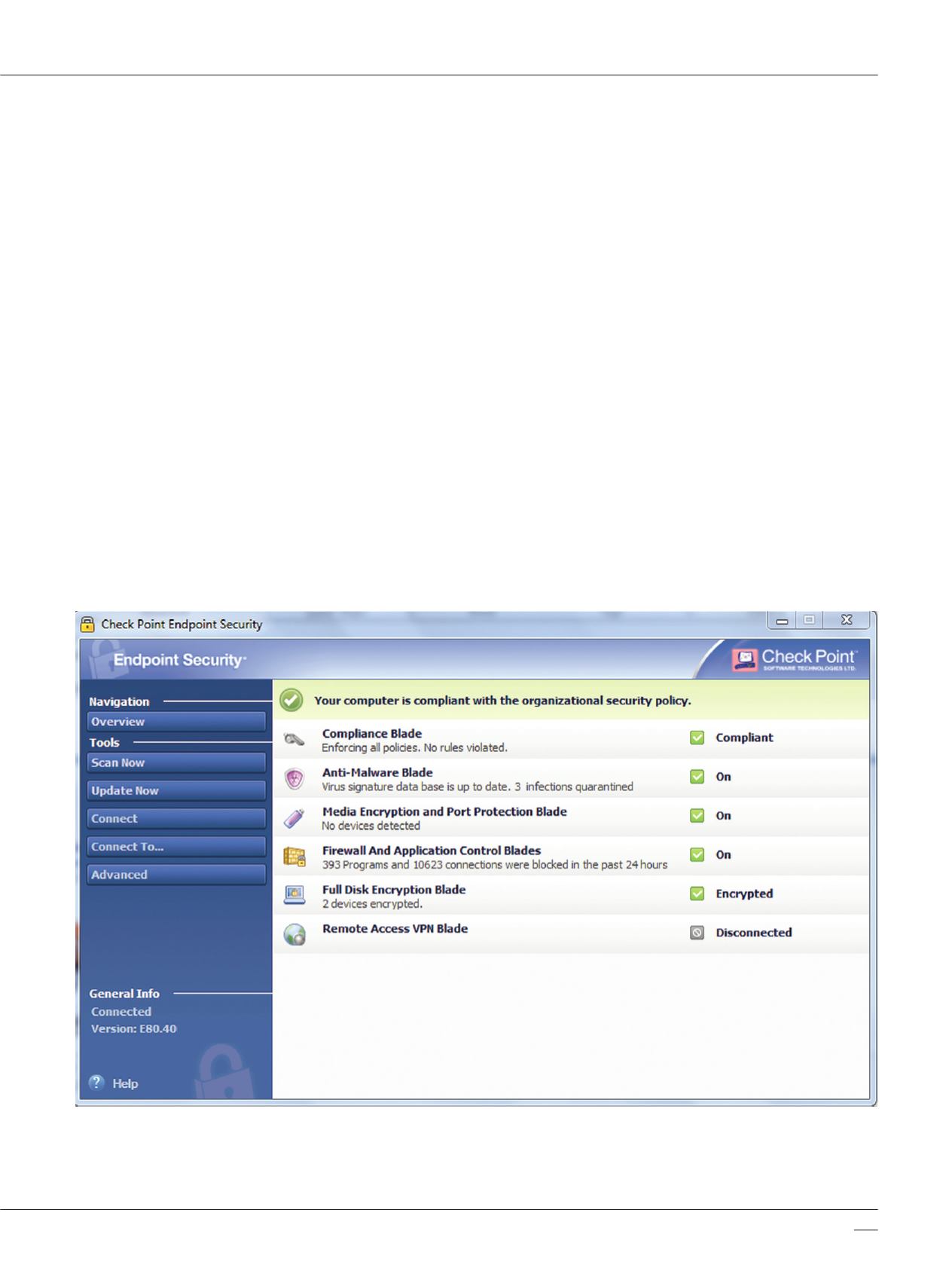
Check Point Endpoint Security
Check Point Endpoint Security Software Blades bring
unprecedented flexibility, control and efficiency to the
management and deployment of endpoint security. IT
managers can choose from six Endpoint Software Blades
and deploy only what’s necessary to fulfill their existing
protection requirements. As needs evolve, the option
to increase security at any time is always available.
Full
Disk Encryption Software Blade
automatically and
transparently secures all information on endpoint hard
drives. Multi-factor pre-boot authentication ensures
user identity.
Media Encryption Software Blade
provides centrally enforceable encryption of removable
storage media, with the granularity to encrypt only
business-related data while engaging and educating
the end user.
Remote Access VPN Software Blade
provides users with secure, seamless access to corporate
networks and resources when working remotely.
Anti-
Malware and Program Control Software Blade
efficiently detects and removes malware from endpoints
with a single scan. Program Control assures that only
legitimate and approved programs run on endpoints.
Firewall and Security Compliance Verification
Software Blade
proactively protects inbound and
outbound traffic by preventing malware from infecting
endpoint systems, blocking target attacks and stopping
unwanted traffic. The Security Compliance Verification
assures that corporate endpoints will always meet the
organization’s security policy requirements.
WebCheck
Secure Browsing Software Blade
protects against the
latest web-based threats including drive-by downloads,
phishing sites and zero-day attacks. It also enables
browser sessions to run in a secure virtual environment.
Check Point Endpoint Security Client


