039
CHECK POINT 2013 SECURITY REPORT
06
_ SUMMARY AND SECURITY STRATEGY
dynamic threats such as bots, trojans and Advanced
Persistent Threats (APTs). Current firewalls behave like
multi-function gateways, but not all companies want the
same level of security throughout their entire system.
Companies seek flexibility and control of their security
resources.
Software Blades are security applications or modules such
as: firewalls, Virtual Private Networks (VPN), Intrusion
Prevention Systems (IPS), or application controls, that
are independent, modular and centrally managed. They
allow organizations to customize a security configuration
that targets the right mix of protection and investment.
Software Blades can be quickly enabled and configured
on any gateway or management system with no
additional hardware, firmware or driver upgrades. As
needs evolve, additional Software Blades can be easily
activated to extend the security parameters of an existing
configuration running on the same security hardware.
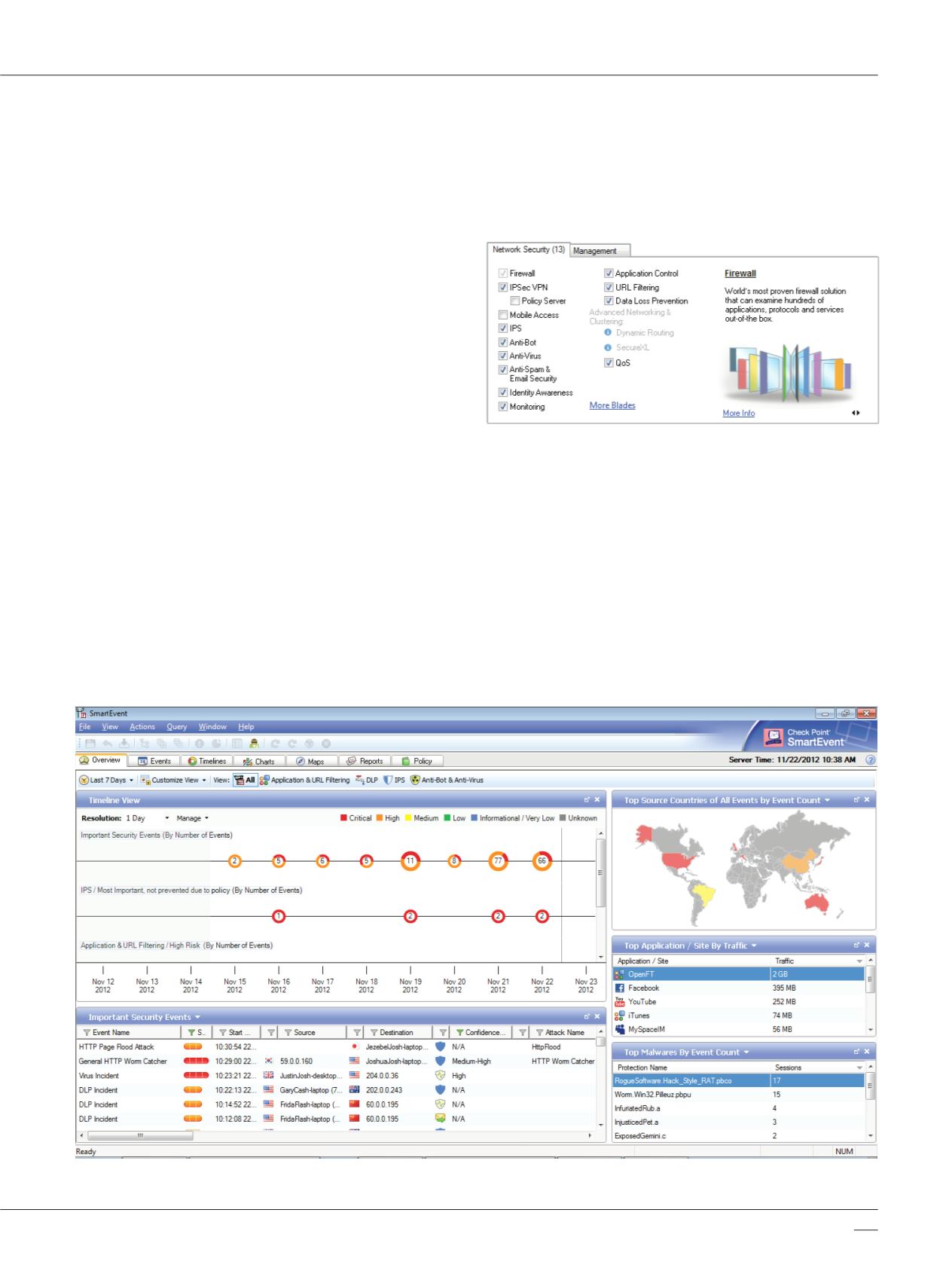
Check Point offers centralized event management
features for all Check Point products and third-party
devices. This provides real-time views of security events
as they take place, enables quick analysis of the security
situation, and allows for immediate mitigating actions,
all conducted via a single console. The ‘timeline view’
enables the visualization of trends and propagation of
attacks. The ‘charts view’ provides event statistics in
either a pie chart or a bar graph format. The ‘maps view’
shows potential threats by country.
Check Point Security Gateway
SmartDashboard. Software Blades
Activation Screen
Check Point SmartEvent Security Events Management. Real-time Overview


