5. Vulnerability and Patch Management
Goal
Demonstration of Harmony Endpoint Vulnerability Management: This feature identifies flaws in operating systems or applications that could allow attackers to gain unauthorized access to a system or network. It includes automatic scanning of all devices to detect new vulnerabilities and offers Patch Management capabilities with detailed scan policies and automatic patching.
Discussion points
-
Proactive Threat Detection: automatic scanning feature helps in identifying vulnerabilities before they can be exploited by attackers. Highlight the importance of proactive threat detection in maintaining the security posture of the organization..
-
Granular Control and Customization: Granular scan policy options available, allowing customers to tailor the scanning and patching processes to their specific needs. This can include setting different policies for various device groups or scheduling scans during off-peak hours to minimize disruption.
-
Efficiency and Automation: Emphasize the automatic patching capabilities, which reduce the manual effort required to keep systems up to date. Discuss how this automation can lead to significant time savings and ensure that critical patches are applied promptly, reducing the window of vulnerability.
* Vulnerability and Patch Management capabilities are part of the Harmony Endpoint Compliance blade and included with Harmony Endpoint Elite package or dedicated Harmony Endpoint Add-Ons. Refer to Check Point pricing catalogue for additional details.
Instructions
The procedure below describes all steps to demonstrate the scenario.
|
Step |
Instructions |
|---|---|
|
1 |
From the Jump server machine, open a connection to the Windows 10 Protected machine, use the remote desktop link from the desktop to connect. |
|
2 |
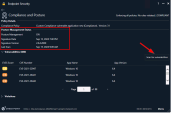
Launch the Harmony Endpoint client and click on Compliance and Posture blade |
|
|
|
|
3 |
Note the Posture Management status and last scan date. You can manually initiate the Posture Scan by clicking on Scan for Vulnerabilities button |
|
4 |
Navigate back to the Jump server and login to the Infinity portal through the chrome browser (Environment Information). *Note, some of the options shown below are grayed out for the Read-Only users used in this scenario (i.e. ability to click’Patch’) |
|
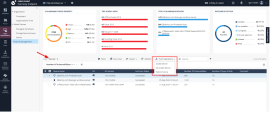
5 |
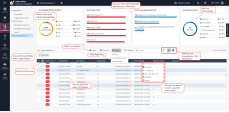
Navigate to the Asset Management->Posture Management screen to see the dashboard. Take some time to understand the information and capabilities of Harmony Endpoint. |
|
6 |
Selecting a specific CVE and clicking 'Patch' gives the option to instantly patch the vulnerable devices. |
|
7 |
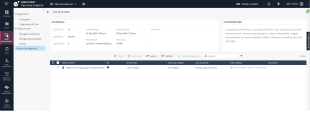
Switching to Device oriented view gives the option to use Push Operations for Device remediation |
|
8 |
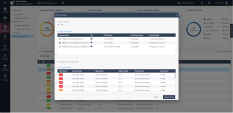
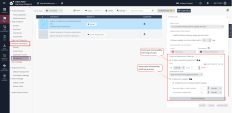
Navigate to Policy->Access & Compliance->Compliance tab and scroll the options down to Posture Assessment Settings. Note the options available for vulnerability scanning and patching processes. |
|
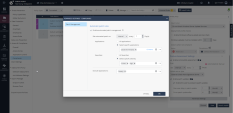
9 |
Click the Advanced Settings and note the automatic patching configuration options. |