4. Backdoor Attack Leading to a Ransomware Attack
Goal
Demonstration of Harmony Endpoint Anti-Ransomware capabilities to detect according to the behavior of an unknown Ransomware followed by an automated remediation, analysis, triage and file restoration.
Discussion points
-
Harmony Endpoint Anti-Ransomware behavioral detection during runtime of a Ransomware attack focused on detecting any type of Ransomware attack.
-
Harmony Endpoint Anti-Ransomware automated remediation and files restoration protecting users data and allowing them to continue working without wasting organizations’, time, money and effort.
-
Multi-layered endpoint protection platform with automated EDR capabilities to fully recover from attacks.
Watch the Demonstration Video
For brevity, this video shows only the most important steps.
Instructions
The procedure below describes all steps to demonstrate the scenario.
|
Step |
Instructions |
|||
|---|---|---|---|---|
|
1 |
From the Jump server machine, on the desktop, use the Putty desktop link to connect to the kali attacker machine.
|
|||
|
2 |
Open a terminal window and navigate to /root/demo/backdoors/:
|
|||
|
3 |
Execute:
|
|||
|
4 |
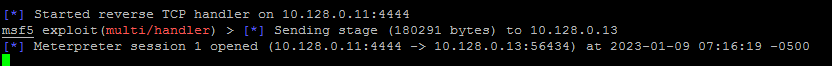
The process takes a few seconds and you will see the following : This will open a reverse TCP handler (listener) on the kali attacker machine for the backdoor. |
|||
|
5 |
Minimize the kali attacker Putty window and open a remote desktop connection to the windows server protected machine using the link on the Jump server desktop |
|||
|
6 |
Open My Documents folder, and execute the scvhost.exe file. This will open a meterpreter reverse TCP shell back to the kali attacker machine. |
|||
|
7 |
Minimize the windows server protected RDP window and navigate back to the kali attacker SSH session to the opened meterpreter session. |
|||
|
8 |
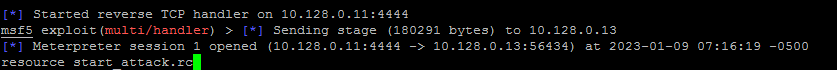
Type in the blank line and execute:
|
|||
|
9 |
This will load and execute a Ransomware attack on the window server protected machine. You have a 10 seconds delay to navigate back to the windows server protected machine to show the attack. |
|||
|
10 |
Minimize the kali attacker Putty window and open a remote desktop connection to the windows server protected machine from the link on the Jump server desktop. |
|||
|
11 |
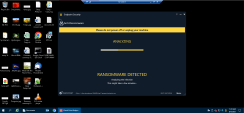
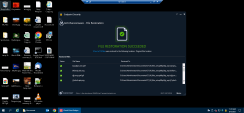
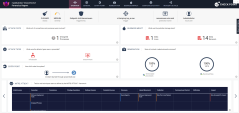
Demonstrate how Check Point Harmony Endpoint detects and remediates ransomware attacks in real time. Show that user files encrypted by the ransomware were automatically restored to their original state, ensuring minimal disruption. Then, walk through the Forensics Report to highlight key insights, including a detailed timeline of the attack, its business impact, alignment with the MITRE ATT&CK™ framework, and the remediation steps taken |
|||
|
12 |
Navigate back to the Jump server and login to the Infinity portal through the chrome browser (Environment Information). |
|||
|
13 |
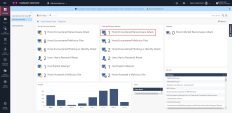
Navigate to the Security Overview screen to show to full scope of the attack, including the detailed and automated response, analysis and triage: |
|||
|
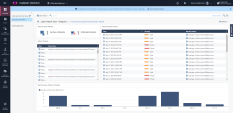
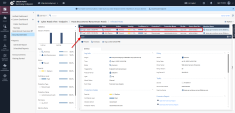
14 |
From the log open the forensics report to show the full and automated attack analysis, triage and response. Show the MITRE ATT&CK integration, entry point, remediation and suspicious activities. It is recommended to walkthrough the attack from the incident details tree view. |