2. Social Engineering, Phishing and Credential Theft Targeted Attack
Goal
Demonstration of Harmony Endpoint advanced real time phishing prevention capabilities and runtime detection and automated response.
Discussion points
-
Harmony Endpoint zero-phishing real time scanning and prevention capabilities protecting organizations from the most common attack vector.
-
Harmony Endpoint behavioral guard runtime detection of credential scraping attack with automated response, analysis and triage.
-
Multi-layered endpoint protection platform preventing multi-vector credential stealing attacks.
-
Credential reuse protection, alerting from potential corporate credential theft.
Watch the Demonstration Video
For brevity, this video shows only the most important steps.
Instructions
The procedure below describes all steps to demonstrate the scenario.
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
From the Jump server machine, on the desktop, use the remote desktop link to connect to the windows attacker machine. |
||
|
2 |
Minimize the window and open a connection to the Windows 10 Protected machine, use the remote desktop link from the desktop to connect. |
||
|
3 |
Minimize the window and connection to the kali attacker machine, use the Putty link from the desktop to connect.
|
||
|
4 |
Open 2 SSH session to kali attacker machine (side by side). |
||
|
5 |
On the first session window execute /root/demo/serve-phish.sh to launch the attacker zero-day phishing website and view the connections. |
||
|
6 |
On the second session window execute /root/demo/follow-phish-dump.sh to view the credentials that will be phished from the user. |
||
|
7 |
Navigate to the windows attacker machine. |
||
|
8 |
Open the Outlook client from the taskbar and send the targeted credential theft email for Bruce Morgan the CFO. The email is at the drafts folder of the SBlab IT Department section. |
||
|
9 |
Minimize the windows attacker RDP window and navigate to the Windows 10 Protected machine. |
||
|
10 |
Open the outlook client from the taskbar and review the targeted email…… looks legitimate, right?. This is how easy it is to perform a social engineering and credential theft attack, and this scenario demonstrates why it is so successful and the critical need for real-time phishing prevention. |
||
|
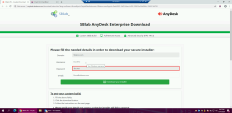
11 |
Click the download AnyDesk Installer link, and it will open in the chrome browser. |
||
|
12 |
Notice that Bruce’s details are already filled in to build trust with the user, and all that is left for him is to fill in his (Bruce’s) password. |
||
|
13 |
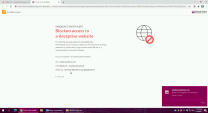
Press the password textbox to fill in any password you would like and notice that zero-phishing scans and detects the site as a phishing site preventing the user from exposing their credentials to the attacker. |
||
|
14 |
Don’t close the the user notification tab, and move back to the previous tab to show that the user is now blocked from handing his credentials to the attacker. |
||
|
15 |
We have added in the policy the ability for the user to proceed even after phishing prevention is done in order to progress the scenario and show what happens in case zero-phishing is not implemented. |
||
|
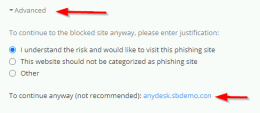
16 |
Go back to the user notification tab, click Advanced and then choos 'I understand the risk and would like to visit this phishing site' option |
||
|
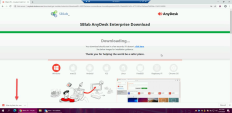
17 |
Now you will be able to fill in any password you want and click download your installer. Suggestion: use a funny password like “WhereIsMyPassword” or “PhishingRulz”. Notice that now the attack proceeds, and we have excluded multiple engines that would have stopped the file from downloading or executing. This is the place to briefly mention the following engines before progressing the attack.
|
||
|
18 |
Click Keep |
||
|
19 |
Before executing the fake SBlab AnyDesk Enterprise.exe zero-day malware. Navigate back to the Jump Server machine to demonstrate that Bruce’s password was successfully stolen and can be used to launch a large scale attack on that organization. This is a good place to explore the ramifications of a successful phishing attack to an organization |
||
|
20 |
Navigate back to the Windows 10 Protected machine to resume the attack scenario. |
||
|
21 |
Execute the SBlab AnyDesk Enterprise.exe and click Run. Refer back to the email and the website to show the full extent of the social engineering attack showing that exact screen, building trust with the user to click on Run. |
||
|
22 |
The credential scraping attack will now execute.
An AnyDesk application window will now open with a popup window indicating that it was installed successfully, making sure the user believes everything is successful. Another important part of a good social engineering attack. Notice that at this time, Harmony Endpoint Behavioral guard detected the attack during runtime and automatically remediated it.
Show that the application window was terminated and the malware was quarantined as part of the automated remediation process. (It may take about 1-2 minutes for Behavioral Guard pop-up to appear). |
||
|
23 |
Navigate back to the Jump server and login to the Infinity portal through the chrome browser (Environment Information). |
||
|
24 |
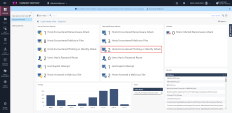
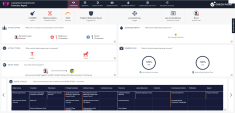
Navigate to the Security Overview screen to show to full scope of the attack, including the detailed and automated response, analysis and triage: Start from the phishing attack prevention and the user choosing to visit the infected site and getting their credential stolen. Continue with the behavioral guard runtime detection and full attack remediation. |
||
|
25 |
You can show the logs tab in the Harmony Endpoint management platform or from the security overview screen and search for anydesk to show the behavioral guard log for the maximize detection. |
||
|
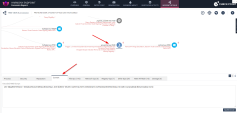
26 |
Run the following search from the log open the forensics report to show the full and automated attack analysis, triage and response:
Show the MITRE ATT&CK integration, entry point, remediation and suspicious activities. It is recommended to walkthrough the attack from the incident details tree view. Note that attack was stopped at an early stage by detecting the malicious PowerShell execution before Mimikatz was able to steal the user’s credentials. |
||
|
27 |
Navigating through the forensics report can be easier from SmartView or from the Harmony Endpoint on the Windows 10 Protected machine. |
Demonstration of Credential reuse protection
Watch the Demonstration Video
For brevity, this video shows only the most important steps.
Instructions
The procedure below describes all steps to demonstrate the scenario.
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
From the Jump server machine use the remote desktop link to connect to the windows-server-protected machine. |
||
|
2 |
|
||
|
3 |
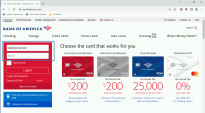
You will see a notification that alerts the users that their corporate password might be exposed to hackers and that they need to change it immediately.
|