1. Exploit Attack (DejaBlue)
Goal
Demonstration of Harmony Endpoint exploit prevention capabilities by preventing a DejaBlue attempt on a windows 10 protected machine.
Discussion points
-
Harmony Endpoint Anti-Exploit behavioral capabilities to prevent the exploit attempt before any damage is done.
-
Check Point was the first to prevent the BlueKeep and DejaBlue exploits.
-
Multi-layered endpoint protection platform preventing attacks before execution.
|
|
Note - DejaBlue represents set of Remote Code Execution exploits similar to that of BlueKeep. |
Watch the Demonstration Video
For brevity, this video shows only the most important steps.
Instructions
The procedure below describes all steps to demonstrate the scenario.
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
From the Jump server machine, on the desktop, use the remote desktop link to connect to the Windows attacker machine.
|
||
|
2 |
Minimize the window and open connection to the Kali attacker machine, use the Putty desktop link from the desktop to connect.
|
||
|
3 |
Optional – perform a real time nmap scan on the targeted machine - Windows 10 protected |
||
|
4 |
Navigate back to the Windows attacker machine through the open remote desktop connection. |
||
|
5 |
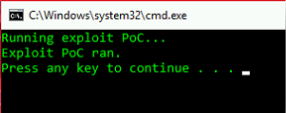
Open the Attack Resources folder on the desktop, and under the DejaBlue-POC folder, Execute the Run-Exploit-PoC.bat
|
||
|
6 |
Navigate to the Windows 10 Protected machine through the open remote desktop connection.
|
||
|
7 |
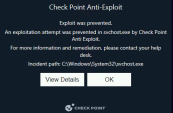
View the Anti-Exploit prevention pop up that indicates that the DejaBlue exploit was prevented:
|
||
|
8 |
Navigate back to the Jump server and login to the Infinity portal through the chrome browser (Environment Information). |
||
|
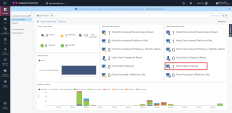
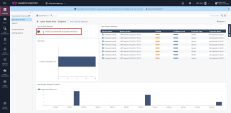
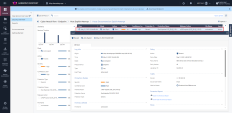
9 |
Browse to the Security Overview tab under the Overview section and show the Anti-Exploit event, logs and forensics report. It is recommended to drill down from Host Exploit Attempt under the Clean/Blocked Attacks section. |