Step 1.2 - Investigation of Phishing attack
Goal
Demonstrate an investigation of the Phishing attack on each of the Office 365 users.
Show Harmony Email & Collaboration analysis and response to each event.
Discussion points
-
Block sophisticated phishing attacks such as social engineering, Impersonation attempts and BEC-based threats using Harmony Email & Collaboration SmartPhish and ThreatCloud platforms.
-
Static and dynamic machine learning inspection in real-time that improves phishing detection accuracy and reduces false positives.
Phishing attack investigation
Instructions
|
Step |
Instructions |
|---|---|
|
1 |
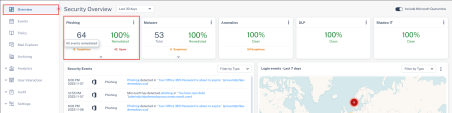
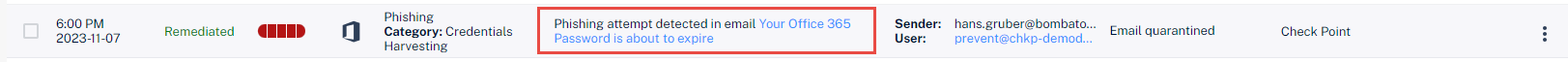
Click on the Phishing Events view. |
|
2 |
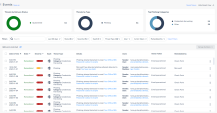
Review the existing events: |
|
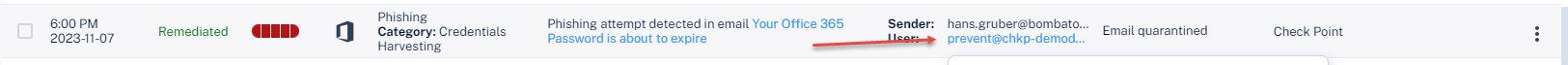
3 |
Click on the email in the event description to view user information, metadata, internal and external collaborators: |
|
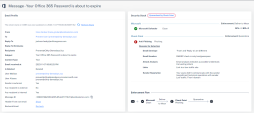
4 |
Return to the events filter and press on the Email subject in the event details to analyze the event further: |
|
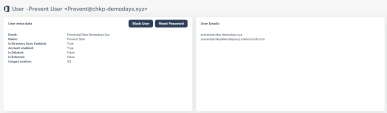
5 |
Start from the Email Profile section to better understand the email information, format and status. The following information is available:
|
|
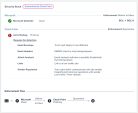
6 |
The second analysis part will be the Security Stack, where you can view all the Check Point inspection services verdicts. You will only see verdicts for services that inspected the email
|
|
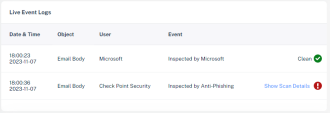
7 |
Live Event log – shows all the relevant logs regarding this event |