Step 1.1 - Investigation of Malware attack
Goal
Demonstrate an investigation of the Malware attack on each of the Office 365 users.
Show Harmony Email & Collaboration analysis and response to each event.
Discussion points
-
Check Point ThreatCloud, SmartPhish and Sandblast engines that block malicious messages, including attachments and malicious links before they reach users’ mailboxes.
-
Content Disarm and Reconstruction (Threat Extraction) that instantly delivers sanitized files to users.
-
Advanced Malware protection for cloud email and productivity suites without impacting business productivity.
Malware attack investigation
Instructions
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
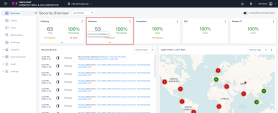
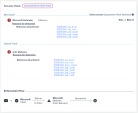
Click on the Malware Events view. |
||
|
2 |
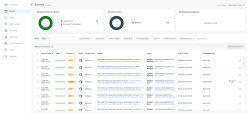
Review the existing events: |
||
|
3 |
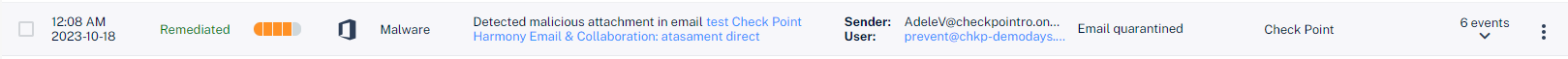
Click on one of the Remediated event to analyze the event: |
||
|
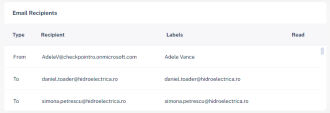
4 |
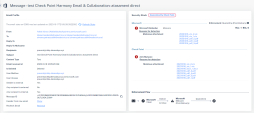
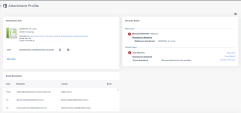
Start from the Email Profile section to better understand the email information, format and status. The following information is available:
|
||
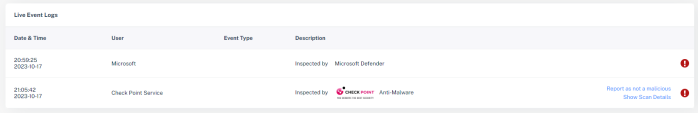
|
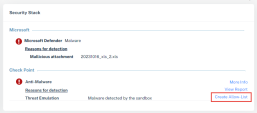
5 |
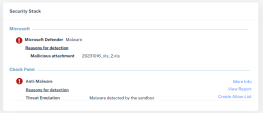
Second analysis part will be the Security Stack, Where you can view all the Check Point inspection services verdicts. You will only see verdicts for services that inspected the email: |
||
|
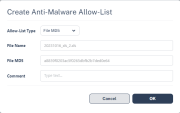
6 |
Click on the malicious files from this section or on any file from the Email attachments section will allow to further analyze the attachment detection results.
|
||
|
7 |
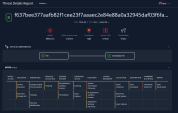
We will now analyze the malicious attachment file.
|
||
|
8 |
Attachment Analysis shows different type of information including:
|
||
|
9 |
You can continue to review the event and related information. |