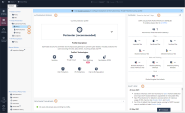
Autonomous Threat Prevention
Autonomous Threat Prevention is an innovative Threat Prevention management model that includes pre-defined security profiles. When you select a security profile, the Security Policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. is created automatically. Autonomous Threat Prevention:
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. is created automatically. Autonomous Threat Prevention:
-
Provides zero-maintenance protection from zero-day threats, and continuously and autonomously ensures that your protection is up-to-date with the latest cyber threats and prevention technologies.
-
Empowers administrators with a one-click classification of the gateway role using out-of-the-box policy profiles based on your business and IT security needs.
-
Streamlines configuration and deployment of policy profiles across your gateways.
-
Provides simple and powerful customizations to best serve your organization’s needs.
|
|
Note - For offline Threat Extraction |
If you prefer to create your Threat Prevention Security Policy manually, see Custom Threat Prevention.
Getting Started with Autonomous Threat Prevention
-
Enable Autonomous Threat Prevention in the Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. / Cluster
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. / Cluster Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. object (see .Configuring Autonomous Threat Prevention
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. object (see .Configuring Autonomous Threat Prevention -
Select the required Autonomous Threat Prevention profile which creates the policy (see Autonomous Threat Prevention Profiles andConfiguring Autonomous Threat Prevention).
-
Optional: Configure advanced Threat Prevention settings:
-
Security Gateway / Cluster object - Settings for Threat Prevention Software Blades and features.
-
Security Policies view > Threat Prevention >Autonomous Policy:
-
File Protections
-
Settings
-
-
Security Policies view > Threat Prevention > Exceptions
-
Security Policies view > Threat Prevention > click Autonomous Policy > refer to the Autonomous Policy Tools section
-
Security Policies view > HTTPS Inspection
-
Manage & Settings view > Blades > Threat Prevention > Advanced Settings
-
Security Gateway / each Cluster Member command line - Configuration commands and files (for example, for SSH Deep Inspection)
-
-
Install the Autonomous Threat Prevention policy (seeConfiguring Autonomous Threat Prevention).
Monitoring
Use the Logs & Events page to show logs related to Threat Prevention traffic. Use the data there to better understand the use of these Software Blades in your environment and create an effective Rule Base![]() All rules configured in a given Security Policy. Synonym: Rulebase.. You can also directly update the Rule
All rules configured in a given Security Policy. Synonym: Rulebase.. You can also directly update the Rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. Base from this page.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. Base from this page.
You can add more exceptions that prevent or detect specified protections or have different tracking settings.