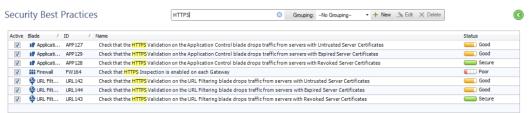
The Security Best Practices Compliance View
The Security Best Practices Compliance![]() Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. view displays status information for each best practice.
Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. view displays status information for each best practice.
The top table shows these details related to the best practice:
-
Active - Select to activate the best practice test. Clear to deactivate it.
-
Blade - Blade related to this best practice.
-
ID - Check Point Compliance ID assigned to the best practice.
-
Name - Name and brief description of the regulatory requirement related to the best practice.
-
Status - Poor, Medium, Good, Secure, or N/A. We recommend that you resolve "Poor" status items immediately.
The bottom section shows these items for the selected best practice test:
-
Description - Detailed description of the best practice test.
-
Action Item - Steps required to become compliant, including alternative scenarios.
-
Dependency - Shows when the selected best practice is dependent on another best practice. This test is only performed if the other best practice is compliant.
-
Relevant Objects - Objects related to the selected best practice test and their status. You can activate or deactivate the selected best practice test for specified objects (this section shows only when the best practice is applicable to specific objects.)
-
Relevant Regulatory Requirements - Link to a list of all the regulatory standards which are applicable to the best practice.
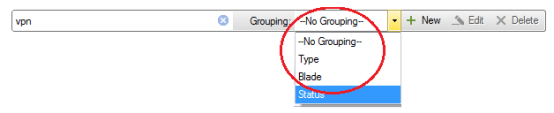
To search for a certain value, enter a string in the search box:
To search for a certain parameter in a specific field, enter: field name:string
To group results, select Blade or Status in the grouping field;
To sort search results by a certain field, click the field header.
Creating User-Defined Best Practices
You can define your own, custom Security Best Practices based on organizational security requirements.
-
In the 'Compliance tab > Security Best Practices pane .> click See All.
-
Click New, and select Firewall Best Practice.
The New Firewall Best Practice window opens.
-
Enter the Name and Description for this best practice.
-
Enter the Action Item generated by this best practice.
-
In the Best Practice Rule Definition section, enter the rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. matching criteria in the table cells. A Security Best Practice match occurs when all table cells match one or more rules in the Rule Base
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. matching criteria in the table cells. A Security Best Practice match occurs when all table cells match one or more rules in the Rule Base All rules configured in a given Security Policy. Synonym: Rulebase. (Logical AND).
All rules configured in a given Security Policy. Synonym: Rulebase. (Logical AND).-
Hit Count - Select a hit count level. A match occurs when the hit count for a rule is equal to or exceeds the specified hit count level. For example: To check the Rule Base for unused rules, you can select Hit Count Zero.
-
Name
-
Source - Select one or more source objects.
-
Destination - Select one or more destination objects.
-
VPN - Select one or more VPN communities.
-
Services & Applications - Select one or more services or applications.
-
Action - The action which the rule triggers.
-
Track - The tracking method for the rule.
-
Install On - Security Gateways / Security Cluster
 Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing.s to which the rule applies.
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing.s to which the rule applies. -
Time - Select the times at which the rule applies.
-
Comment - Enter a comment if necessary.
-
Optional: click Advanced Settings to select the percentage of the Rule Base to scan and the direction of scan (Top or Bottom). For example, select Bottom 30% to scan 30% of the Rule Base starting from the bottom (last rule in the Rule Base).

Note - You can right-click a cell, and select Negate Cell to exclude the cell from matching. This feature is not available in the Name and Comment cells.
-
-
In the Best Practice Scoring section configure these settings:
-
Violation Definition - Define if a match occurs when the best practice is matched by a rule or not. Select one of these options:
-
Rule found - A match occurs when the best practice is matched by a rule in the Rule Base.
-
Rule not found - A match occurs when the best practice is not matched by a rule in the Rule Base.
Select the level of Tolerance - A violation occurs when there are more than the specified number of matches (Default = 0). For example, if the tolerance is set to 0, the Compliance Blade creates a violation when the first match occurs. If the tolerance is set to 3, the Compliance Blade creates a violation when the fourth match occurs. The Tolerance option applies only to the Rule found option.
-
-
Rule Index Display Criteria - Define when the Rule Index (rule number) shows in the Relevant Objects pane in the Security Best Practices view. This lets you easily see which rules cause or prevent violations:
-
Display rules that match - Shows rules that match the criteria specified in a Security Best Practice.
-
Display rules that don't match - Shows rules that do not match the criteria specified in a Security Best Practice.
-
Don't display rules - Does not show the rule.
-
-
-
Click OK.
The new best practice is added to the list of best practices.
-
Publish your changes.
-
In the 'Compliance tab > Security Best Practices pane .> click See All.
-
Click New, and select Gaia OS Best Practice.
The new Gaia OS Best Practice window opens.
-
Enter the Name and Description for this best practice.
-
Enter the Action Item generated by this best practice.
-
Enter the Practice Script to run on the Security Gateways or load the script from a file.
-
Enter the Expected Output - If the script output is equal to the Expected Output, the best practice status is secure.
-
Click OK.
The new best practice is added to the list of best practices.
-
Publish your changes.
|
|
Best Practice - We recommend that you run a manual scan after you create a new Security Best Practice. The scan reevaluates the Compliance status, to reflect any configuration changes. To do a manual scan . go to the Manage & Settings view > Blades > Compliance > Settings > click the Rescan button. You cannot perform any actions in the Compliance tab while the scan runs. |
Activating and Deactivating Best Practice Tests
You can activate or deactivate enforcement of best practices by test, by Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., by Software Blade
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., by Software Blade![]() Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. or by other objects. Activation changes are applied after the next scan.
Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. or by other objects. Activation changes are applied after the next scan.
By default, all best practice tests are active.
-
Go to the Security Best Practices view > and select a best practice.
-
Right-click and select Deactivate.
The Expiration Details window opens.
-
Select Never or enter an expiration date. If you select an expiration date, the best practice test is automatically activated on that date.
-
In the Comment box, explain why it is necessary to deactivate this Compliance test.
-
Go to the Security Best Practices view, select a best practice, right-click and select Activate.
Or
-
Go to the Manage & Settings > view > Blades > Compliance > Inactive Objects > Inactive Security Best Practices > select the applicable security best practice and click Remove.
-
Go to the Manage & Settings > view > Blades > Compliance > Inactive Objects.
-
In the Inactive Gateways section, click Add.
-
Enter or select a Security Gateway or a Security Cluster.
|
|
Note - To activate the best practice for the Security Gateway, select the Security Gatewayand click Remove. When prompted, click Yes. |
-
Go to the Manage & Settings > view > Blades > Compliance > Inactive Security Best Practices on Specific Objects.
-
In the Inactive Gateways section, click Add.
-
Enter or select a Security Gateway or a Security Cluster.
|
|
Best Practice - We recommend that you run a manual scan after you activate or deactivate best practice tests. The scan reevaluates the compliance status, to reflect any configuration changes. To do a manual scan, go to the Manage & Settings view > Blades > Compliance > Settings > click the Rescan button. You cannot perform any actions in the Compliance tab while the scan runs. |