Overcoming Restricted Internet Access
When a user connects to the organization from a remote location such as hotel or the offices of a customer, Internet connectivity may be limited to web browsing using the standard ports designated for HTTP, typically port 80 for HTTP and port 443 for HTTPS. Since the remote client needs to perform an IKE negotiation on port 500 or send IPsec packets (which are not the expected TCP packets; IPsec is a different protocol), a VPN tunnel cannot be established in the usual way. This issue is resolved using Visitor Mode, formally known as TCP Tunneling.
Visitor Mode
Visitor Mode tunnels all Client-to-Gateway communication through a regular TCP connection on port 443.

|
Item |
Description |
|---|---|
|
1 |
Host Server |
|
2 |
|
|
3 |
Internet |
|
4 |
Non-Check Point VPN peer that works with Visitor Mode to allow traffic to the client |
|
5 |
Remote Access Client |
All required VPN connectivity between the Client and the Server is tunneled inside this TCP connection. This means that the peer Security Gateway needs to run a Visitor Mode (TCP) server on port 443.
Number of Users
To obtain optimal performance of the Visitor Mode server:
-
Minimize the number of users allowed Visitor Mode if performance degrades
-
Increase the number of sockets available on the OS by editing the appropriate values, for example the socket descriptor on Linux systems
Allocating Customized Ports
The organization decides that it would like to use a customized port for the Visitor Mode Server other than the typically designated port 443. In this scenario, another port that is mutually agreed upon by all the remote locations and the home organization, can be used for Visitor Mode. This solution works well with business partners; the partner simply agrees to open a port for the visitor Mode connections. If the chosen port is not represented by a pre-defined service in SmartDashboard![]() Legacy Check Point GUI client used to create and manage the security settings in versions R77.30 and lower. In versions R80.X and higher is still used to configure specific legacy settings., this service must be created in order for the port to be used. If a port has been mutually agreed upon, and there is a proxy, configure the proxy to allow traffic destined to this port.
Legacy Check Point GUI client used to create and manage the security settings in versions R77.30 and lower. In versions R80.X and higher is still used to configure specific legacy settings., this service must be created in order for the port to be used. If a port has been mutually agreed upon, and there is a proxy, configure the proxy to allow traffic destined to this port.
|
|
Note - All partner Security Gateways must agree on the same allocated port, since the Visitor Mode server on the VPN peer will be listening on only one port. |
If you change the port for Visitor Mode, then in the Remote Access VPN![]() An encrypted tunnel between remote access clients (such as Endpoint Security VPN) and a Security Gateway. client, you must name the Remote Access VPNGateway site in this format:
An encrypted tunnel between remote access clients (such as Endpoint Security VPN) and a Security Gateway. client, you must name the Remote Access VPNGateway site in this format:
[Security Gateway's IP address or Hostname]:PORT
Example -example-gw.company.com:1720
For more information about creating a site in the Remote Access VPN client, see:
-
Remote Access VPN Clients for Windows Administration Guide > "Getting Started with Remote Access Clients" chapter > "Helping Users Create a Site" section
-
Endpoint Security VPN for macOS Administration Guide > "Helping Your Users" chapter > "Helping Users Create a Site" section
Visitor Mode and Proxy Servers
Visitor Mode can still be utilized in instances where the remote location runs a proxy server. In this scenario, the remote user enables Visitor Mode connections to pass through the proxy server.
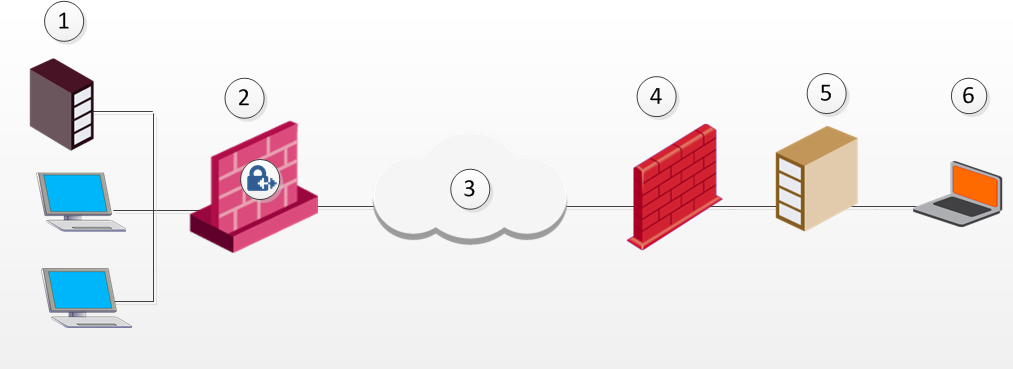
|
Item |
Description |
|---|---|
|
1 |
TCP Server |
|
2 |
Security Gateway |
|
3 |
Internet |
|
4 |
Non-Check Point VPN peer on a remote location |
|
5 |
Remote location's proxy server |
|
6 |
Remote Access Client |
Visitor Mode When the Port 443 is Occupied By an HTTPS Server
If the designated port is already in use, for example reserved for HTTPS connections by a Server at the organization's Security Gateway, a log is sent "Visitor Mode Server failed to bind to xxx.xxx.xxx.xxx:yy (either port was already taken or the IP address does not exist)" to Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server..
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server..
If the peer Security Gateway is already running a regular HTTP server that also listens on the standard HTTPS port 443, then it must be set up with two external interfaces, both of which have public IP addresses - one for the HTTP server, and one for the Visitor Mode server. This second routable address can be achieved in two ways:
-
installing an additional network interface for the Visitor Mode server, or
-
by utilizing a virtual IP on the same network interface which is blocking the port.
On the Security Gateway object running the Visitor Mode server, General Properties>Remote Access page> there is a setting for Allocated IP address. All the available IP addresses can be configured to listen on port 443 for Visitor Mode connections.
Visitor Mode in a MEP Environment
Visitor Mode also works in a MEP environment. For more information, see Visitor Mode and MEP.
Interface Resolution
For interface resolution in a Visitor Mode environment, it is recommended to use static IP resolution or dedicate a single interface for Visitor Mode.

