Machine Certificate
Authentication with a machine certificate is supported for Endpoint Security clients connecting to a Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources..
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources..
Machine certificate authentication supports these modes:
-
User and machine authentication - Authenticate with a machine certificate and a user authentication method.
-
Machine-only authentication - Authenticate with a machine certificate only. This mode is available before and after the user logs in to Windows.

|
Note - Machine certificate authentication works with the Endpoint Client only. For more details on how to configure this feature on the client side, see the "Machine Authentication" section in these Administration Guides: |
Limitations:
-
The machine must be defined on a Microsoft AD server.
-
The Subject field of a machine certificate must not be empty.
The hostname must be the first value.
For example:
CN = DESKTOP-12345, OU= Computers, DC = example, DC = com
-
Machine-only authenticated tunnels require the Security Gateway authentication method to be “Defined on user record (Legacy authentication)” or a certificate based realm.
-
Check Point Desktop Policy with Machine Groups is not supported.
-
The Check Point Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. does not provide machine certificate enrollment or distribution functionality.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. does not provide machine certificate enrollment or distribution functionality. -
You must use Access Roles for the machine entity. Objects such as machine@location are not supported.
Feature Configuration Steps
-
 Adding the root CA on the LDAP Server to the Trusted CA in Management
Adding the root CA on the LDAP Server to the Trusted CA in Management
Refer to sk149253.
This CA is necessary for the machine authentication procedure.
-
 Creating LDAP Account Unit
Creating LDAP Account Unit
Refer to sk31841.
-
 Setting up the Authentication enforcement
Setting up the Authentication enforcement
Feature status definitions
-
Disabled - The feature is off. Machine certificate authentication does not occur.
-
When available - Clients are allowed to connect with or without a machine certificate. If the Gateway receives a machine certificate, it tries to authenticate the machine.
Note: If the machine certificate is not valid, the connection fails.
-
Mandatory - Clients can not connect without a machine certificate.
Set the Status of the Machine Certificate Authentication
-
Enable the Identity Awareness
 Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Software Blade
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Software Blade Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. and walk through the Wizard.
Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. and walk through the Wizard. -
Apply the basic Remote Access configuration (community, office mode, and visitor mode).
-
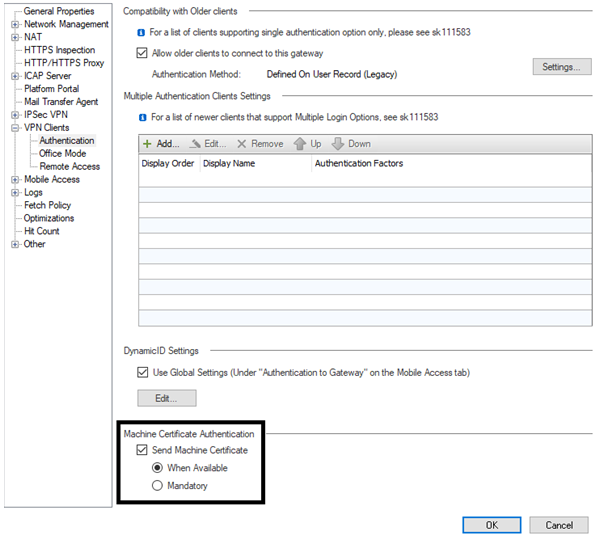
Go to VPN Clients > Authentication.
-
At the bottom of the screen, check Send Machine Certificate.
-
Choose When Available or Mandatory.
-
Click OK.
-
-
 Policy configuration for Users and Machines
Policy configuration for Users and Machines
Install the Access Control Policy
-
Connect with SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to the Management Server.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to the Management Server. -
Go to the Objects .
-
Left-click on New.
-
Select More > User > Access Role.
-
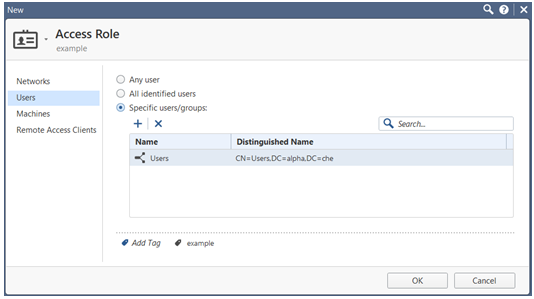
From the left tree, click the Users pane.
-
On the Users pane, select one of these:
-
Any user
-
All identified users - This includes any user identified by a supported authentication method (internal users, Active Directory users, or LDAP users).
-
Specific users/groups - For each user or user group, click to select the user or the group from the list.
-
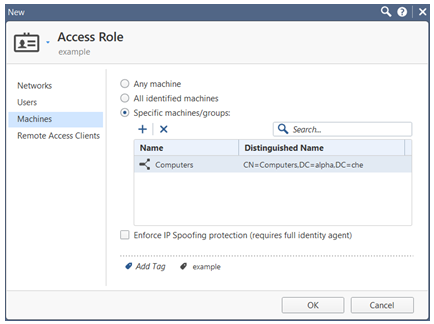
From the left tree, click the Machines pane.
-
On the Machines pane, select one of these:
-
Any machine
-
All identified machines - Includes machines identified by a supported authentication method (Active Directory).
-
Specific machines - For each machine, click to select the machine from the list.
-
Click OK.
-
From the left navigation panel, click Security Polices.
-
Choose your network policy tab.
-
In Access Control, select Policy.
-
Right-click in the Source column > Add new items… .
-
Left-click on the Access Role.
-
Right-click in the VPN column > Specific VPN communities….
-
Add RemoteAccess community.
-
Install the Access Control policy on the Security Gateway / Cluster
 Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing..
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing..
The New Access Role window will open.
-
-
 Policy Examples
Policy Examples
 Example 1
Example 1
The Source field contains the object
Machines_Access_Role.In the access role, choose Specific machines/groups on the Machines pane and add LDAP machine/machines group (leave Any user and Any Network on corresponding panes).
If a client connects with the machine authentication (Machine only or Machine and User), this rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. matches if the Machine matches the LDAP Machine group.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. matches if the Machine matches the LDAP Machine group.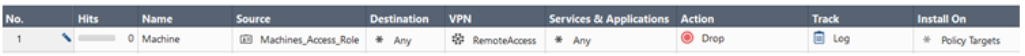
 Example 2
Example 2
The Source field contains the object
Users_Access_Role.In the access role, choose Specific users/groups on the Users pane and add LDAP user/users group. Leave Any machine and Any Network in the corresponding panes.
If a client connects with user authentication (User only or Machine and User), this rule matches if the User matches the LDAP User group.

 Example 3
Example 3
The Source field contains the object
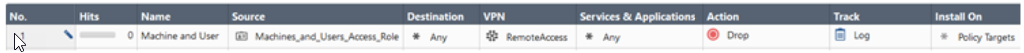
Machines_and_Users_Access_Role.In the access role you should choose Specific machines/groups on the Machines pane and Specific users/groups in the Users pane. Leave Any Network in the corresponding pane.
A connection with Machine and User authentication can match this rule if the Machine and User both match the appropriate LDAP groups.
 Example 4
Example 4
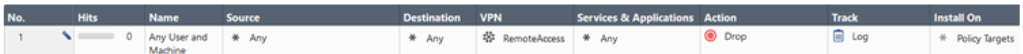
Policy Source field contains the object
Any.If a client connects with User (User only or Machine and User), this rule matches.
-
 Optional - UPN with Machine Certificate
Optional - UPN with Machine Certificate
To use the UserPrincipalName as the User Login Attribute instead of DN, create a machine_certificate realm.
-
This makes it possible to configure different realms for machines and users.
-
Users can log in with their UPN without an impact on the machine authentication.
-
The user realm must still have one authentication factor.
-
After you create the realm, you can change the LDAP lookup type of the user-selected realm to UPN instead of DN.
To create the machine_certificate realm:
-
Back up the Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. / applicable Domain Management Server.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. / applicable Domain Management Server.Refer to:
-
Close all SmartConsole windows.
Note - To make sure there are no active sessions, run the "
cpstat mg" command in the Expert mode on the Security Management Server / in the context of eachDomain Management Server. -
Connect with Database Tool (GuiDBEdit Tool) to the Security Management Server / applicable Domain Management Server.
-
In the top left pane, go to Table > Network Objects > network_objects.
-
In the top right pane, select the Machine_Cert_GW object.
-
Press the CTRL+F keys (or go to the Search menu > click Find) > paste realms_for_blades > click Find Next.
-
In the lower pane, right-click on the realms_for_blades object > select New...
The Add/Edit Owned Object window opens.
-
In the Add/Edit Owned Object window:
-
In the Name field, enter machine_certificate.
-
In the Value field, select realm_blade_entry.
-
Click OK.
The Add/Edit Owned Object window closes.
-
-
Press the CTRL+F keys (or go to the Search menu > click Find) > paste auth_schemes > click Find Next.
-
In the lower pane, right-click on the auth_schemes object > select Add...
The Element Add/Edit window opens.
-
In the Element Add/Edit window:
-
In the Index field, enter 0.
-
Leave the Name field empty.
-
In the Object field, select realm_auth_scheme.
-
Click OK.
The Element Add/Edit window closes.
-
-
Press the CTRL+F keys (or go to the Search menu > click Find) > paste display_string > click Find Next.
-
In the lower pane, right-click on the display_string object > select Edit...
The Edit window opens.
-
In the Edit window:
-
In the Value field, enter machine_certificate.
-
Click OK.
The Edit window closes.
-
-
Save the changes: go to the File menu > click Save All.
-
Close the Database Tool (GuiDBEdit Tool).
-
Connect with SmartConsole to the Security Management Server / applicable Domain Management Server.
-
Install the Access Control Policy on the applicable Security Gateway / Cluster / VSX
 Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts.Virtual System object.
Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts.Virtual System object.
-
