Configuring Mirror and Decrypt in Gateway mode
Example topology:
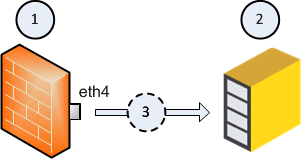
|
Item |
Description |
|---|---|
|
1 |
Security Gateway |
|
2 |
Recorder, or Packet-Broker that works in a monitor (promiscuous) mode. |
|
3 |
Flow of the decrypted and mirrored traffic from the Security Gateway (1) to the Recorder, or Packet-Broker (2). |
|
eth4 |
Designated physical interface on the Security Gateway (1). |
Workflow for configuring Mirror and Decrypt in Gateway mode:
|
Step |
Instructions |
|---|---|
|
1 |
Read and follow the Mirror and Decrypt Requirements. |
|
2 |
Prepare the Security Gateway / each Cluster Member See Preparing the Security Gateway, each Cluster Member, Security Group. |
|
3 |
Configure the Mirror and Decrypt in the Security Gateway / Cluster See Configuring Mirror and Decrypt in SmartConsole for Gateway Mode. |
