Introduction to ClusterXL
The Need for Clusters
Security Gateways and VPN connections are business critical devices. The failure![]() A hardware or software problem that causes a Security Gateway to be unable to serve as a Cluster Member (for example, one of cluster interface has failed, or one of the monitored daemon has crashed). Cluster Member that suffered from a failure is declared as failed, and its state is changed to Down (a physical interface is considered Down only if all configured VLANs on that physical interface are Down). of a Security Gateway
A hardware or software problem that causes a Security Gateway to be unable to serve as a Cluster Member (for example, one of cluster interface has failed, or one of the monitored daemon has crashed). Cluster Member that suffered from a failure is declared as failed, and its state is changed to Down (a physical interface is considered Down only if all configured VLANs on that physical interface are Down). of a Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. or VPN connection can result in the loss of active
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. or VPN connection can result in the loss of active![]() State of a Cluster Member that is fully operational: (1) In ClusterXL, this applies to the state of the Security Gateway component (2) In 3rd-party / OPSEC cluster, this applies to the state of the cluster State Synchronization mechanism. connections and access to critical data. The Security Gateway between the organization and the world must remain open under all circumstances.
State of a Cluster Member that is fully operational: (1) In ClusterXL, this applies to the state of the Security Gateway component (2) In 3rd-party / OPSEC cluster, this applies to the state of the cluster State Synchronization mechanism. connections and access to critical data. The Security Gateway between the organization and the world must remain open under all circumstances.
ClusterXL Solution
ClusterXL![]() Cluster of Check Point Security Gateways that work together in a redundant configuration. The ClusterXL both handles the traffic and performs State Synchronization. These Check Point Security Gateways are installed on Gaia OS: (1) ClusterXL supports up to 5 Cluster Members, (2) VRRP Cluster supports up to 2 Cluster Members, (3) VSX VSLS cluster supports up to 13 Cluster Members. Note: In ClusterXL Load Sharing mode, configuring more than 4 Cluster Members significantly decreases the cluster performance due to amount of Delta Sync traffic. is a Check Point software-based cluster
Cluster of Check Point Security Gateways that work together in a redundant configuration. The ClusterXL both handles the traffic and performs State Synchronization. These Check Point Security Gateways are installed on Gaia OS: (1) ClusterXL supports up to 5 Cluster Members, (2) VRRP Cluster supports up to 2 Cluster Members, (3) VSX VSLS cluster supports up to 13 Cluster Members. Note: In ClusterXL Load Sharing mode, configuring more than 4 Cluster Members significantly decreases the cluster performance due to amount of Delta Sync traffic. is a Check Point software-based cluster![]() Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. solution for Security Gateway redundancy and Load Sharing
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. solution for Security Gateway redundancy and Load Sharing![]() A redundant cluster mode, where all Cluster Members process all incoming traffic in parallel. For more information, see "Load Sharing Multicast Mode" and "Load Sharing Unicast Mode". Synonyms: Active/Active, Load Balancing mode. Acronym: LS.. A ClusterXL Security Cluster contains identical Check Point Security Gateways.
A redundant cluster mode, where all Cluster Members process all incoming traffic in parallel. For more information, see "Load Sharing Multicast Mode" and "Load Sharing Unicast Mode". Synonyms: Active/Active, Load Balancing mode. Acronym: LS.. A ClusterXL Security Cluster contains identical Check Point Security Gateways.
-
A High Availability
 A redundant cluster mode, where only one Cluster Member (Active member) processes all the traffic, while other Cluster Members (Standby members) are ready to be promoted to Active state if the current Active member fails. In the High Availability mode, the Cluster Virtual IP address (that represents the cluster on that network) is associated: (1) With physical MAC Address of Active member (2) With virtual MAC Address. Synonym: Active/Standby. Acronym: HA. Security Cluster ensures Security Gateway and VPN connection redundancy by providing transparent failover
A redundant cluster mode, where only one Cluster Member (Active member) processes all the traffic, while other Cluster Members (Standby members) are ready to be promoted to Active state if the current Active member fails. In the High Availability mode, the Cluster Virtual IP address (that represents the cluster on that network) is associated: (1) With physical MAC Address of Active member (2) With virtual MAC Address. Synonym: Active/Standby. Acronym: HA. Security Cluster ensures Security Gateway and VPN connection redundancy by providing transparent failover Transferring of a control over traffic (packet filtering) from a Cluster Member that suffered a failure to another Cluster Member (based on internal cluster algorithms). Synonym: Fail-over. to a backup
Transferring of a control over traffic (packet filtering) from a Cluster Member that suffered a failure to another Cluster Member (based on internal cluster algorithms). Synonym: Fail-over. to a backup (1) In VRRP Cluster on Gaia OS - State of a Cluster Member that is ready to be promoted to Master state (if Master member fails). (2) In VSX Cluster configured in Virtual System Load Sharing mode with three or more Cluster Members - State of a Virtual System on a third (and so on) VSX Cluster Member. (3) A Cluster Member or Virtual System in this state does not process any traffic passing through cluster. Security Gateway in the event of failure.
(1) In VRRP Cluster on Gaia OS - State of a Cluster Member that is ready to be promoted to Master state (if Master member fails). (2) In VSX Cluster configured in Virtual System Load Sharing mode with three or more Cluster Members - State of a Virtual System on a third (and so on) VSX Cluster Member. (3) A Cluster Member or Virtual System in this state does not process any traffic passing through cluster. Security Gateway in the event of failure. -
A Load Sharing Security Cluster provides reliability and also increases performance, as all members are active.
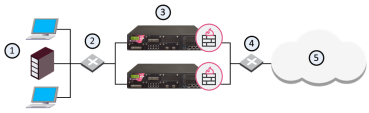
|
Item |
Description |
|---|---|
|
1 |
Internal network |
|
2 |
Switch for internal network |
|
3 |
Security Gateways with ClusterXL Software Blade |
|
4 |
Switch for external networks |
|
5 |
Internet |
How ClusterXL Works
ClusterXL uses State Synchronization to keep active connections alive and prevent data loss when a Cluster Member![]() Security Gateway that is part of a cluster. fails. With State Synchronization
Security Gateway that is part of a cluster. fails. With State Synchronization![]() Technology that synchronizes the relevant information about the current connections (stored in various kernel tables on Check Point Security Gateways) among all Cluster Members over Synchronization Network. Due to State Synchronization, the current connections are not cut off during cluster failover., each Cluster Member "knows" about connections that go through other Cluster Members.
Technology that synchronizes the relevant information about the current connections (stored in various kernel tables on Check Point Security Gateways) among all Cluster Members over Synchronization Network. Due to State Synchronization, the current connections are not cut off during cluster failover., each Cluster Member "knows" about connections that go through other Cluster Members.
ClusterXL uses virtual IP addresses for the cluster itself and unique physical IP and MAC addresses for the Cluster Members. Virtual IP addresses do not belong to physical interfaces.
|
|
Note - This guide contains information only for Security Gateway clusters. For additional information about the use of ClusterXL with VSX |
The Cluster Control Protocol
The Cluster Control Protocol![]() Proprietary Check Point protocol that runs between Cluster Members on UDP port 8116, and has the following roles: (1) State Synchronization (Delta Sync), (2) Health checks (state of Cluster Members and of cluster interfaces): Health-status Reports, Cluster-member Probing, State-change Commands, Querying for cluster membership. Note: CCP is located between the Check Point Firewall kernel and the network interface (therefore, only TCPdump should be used for capturing this traffic). Acronym: CCP. (CCP) packets are the glue that links together the members in the Security Cluster.
Proprietary Check Point protocol that runs between Cluster Members on UDP port 8116, and has the following roles: (1) State Synchronization (Delta Sync), (2) Health checks (state of Cluster Members and of cluster interfaces): Health-status Reports, Cluster-member Probing, State-change Commands, Querying for cluster membership. Note: CCP is located between the Check Point Firewall kernel and the network interface (therefore, only TCPdump should be used for capturing this traffic). Acronym: CCP. (CCP) packets are the glue that links together the members in the Security Cluster.
CCP traffic is distinct from ordinary network traffic and can be viewed using any network sniffer.
CCP runs on UDP port 8116 between the Cluster Members, and has the following roles:
-
It allows Cluster Members to report their own states and learn about the states of other members by sending keep-alive packets (this only applies to ClusterXL clusters).
The Check Point CCP is used by all ClusterXL modes.
For more information, see Configuring the Cluster Control Protocol (CCP) Settings.