Capsule Docs
The Capsule Docs![]() A component on Endpoint Security Windows clients. This component provides security classifications and lets organizations protect and share documents safely with various groups - internal and external. component, managed by an on-premises Security Management Server
A component on Endpoint Security Windows clients. This component provides security classifications and lets organizations protect and share documents safely with various groups - internal and external. component, managed by an on-premises Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server., lets organizations protect and share documents safely within the organization and with business partners, and manage the organizational Capsule Docs policy, monitoring, and deployment through SmartEndpoint
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server., lets organizations protect and share documents safely within the organization and with business partners, and manage the organizational Capsule Docs policy, monitoring, and deployment through SmartEndpoint![]() A Check Point GUI application which connects to the Endpoint Security Management Server, to manage your Endpoint Security environment - to deploy, monitor and configure Endpoint Security clients and policies..
A Check Point GUI application which connects to the Endpoint Security Management Server, to manage your Endpoint Security environment - to deploy, monitor and configure Endpoint Security clients and policies..
Overview of Capsule Docs
Check Point Capsule Docs provides these benefits:
Control the parties that can access the data
-
Restrict access to individuals, groups or entire organizations.
-
Use granular Classification model to assign different permissions for internal and external users.
-
Control data distribution (Forward, Copy/Paste, Print).
-
Choose contacts from your Outlook address book with whom you usually communicate.
-
Prevent unintentional data loss with the help of UserCheck.
-
Use Data Classification to classify documents without encryption.
-
Set a document expiration date to limit when documents can be accessed.
Protect data stored on untrusted servers and shared via untrusted channels
-
Each protected document remains protected even on untrusted servers.
-
Prevent forwarding to unauthorized parties.
-
Secure all created documents automatically.
-
Set a document expiration date
See full audit trail for data access
-
All actions on protected documents are logged and are available through the Logs view in SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on..
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on.. -
Follow paper trail for a single document.
-
Audit distribution patterns for documents in an organization.
-
Monitor access by external parties.
Access protected documents easily from your platform of choice
-
Seamless integration with Microsoft Office and Adobe Acrobat on Windows platforms.
-
Lightweight Windows Viewer that does not require administrative privileges or Microsoft Office or Adobe Acrobat clients installed.
-
Access protected documents from proprietary Apps on Android, and iOS mobile devices.
Full Integration with Organizational Active Directory
-
Users that are defined in the Active Directory are automatically provisioned to use Capsule Docs.
-
User's Active Directory account authentication is sufficient to access relevant protected documents.
-
Customize Capsule Docs policy for different Users, Organizational Units and Groups.
You must configure all prerequisites before you can work with Capsule Docs.
Prerequisites for Capsule Docs
This picture gives an overview of the different components required for a Capsule Docs deployment as part of an Endpoint Security environment:
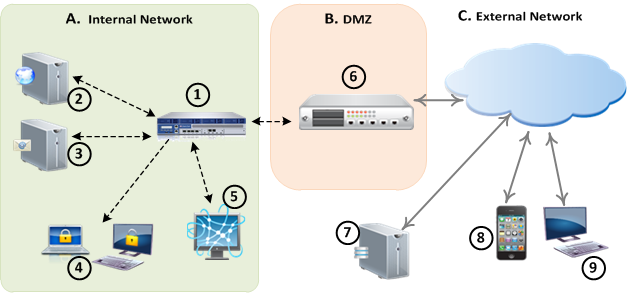
|
Item |
Description |
|
Item |
Description |
|---|---|---|---|---|
|
A |
|
B |
DMZ |
|
|
1 |
|
6 |
||
|
2 |
Active Directory Server |
|
C |
External Network |
|
3 |
SMTP Server |
|
7 |
Public-facing DNS Server |
|
4 |
Internal users |
|
8 |
Mobile users |
|
5 |
Management Console |
|
9 |
External users |
|
|
Notes:
|
To share protected documents externally, you must have an SMTP server and configure a Reverse Proxy.
Configuring Capsule Docs
Before you configure Capsule Docs policy in SmartEndpoint:
-
 Enable Endpoint Policy Management
Enable Endpoint Policy Management
Enable the Endpoint Policy Management
 Check Point Software Blade on a Management Server to manage an on-premises Harmony Endpoint Security environment. component on the Endpoint Security Management Server
Check Point Software Blade on a Management Server to manage an on-premises Harmony Endpoint Security environment. component on the Endpoint Security Management Server A Security Management Server that manages your Endpoint Security environment. Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data..
A Security Management Server that manages your Endpoint Security environment. Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data.. -
 Configure the Active Directory server as the Primary DNS server
Configure the Active Directory server as the Primary DNS server
To configure the Active Directory server as the primary DNS server in Gaia:
-
In the Portal, Network Management navigation tree menu, select Hosts and DNS.
-
Enter the IP address of the Active Directory server as the Primary DNS Server.
-
Click Apply.
To configure the Active Directory server as the primary DNS server in Windows:
-
In the Control Panel window, go to Network and Internet > Network and Sharing Center > Change adapter settings.
-
Right-click the server network interface and select Properties.
The Connection Properties window opens.
-
Select Internet Protocol Version 4 (TCP/IPv4) and click Properties.
-
In the window that opens, enter the IP address of the Active Directory server as the Preferred DNS server.
-
Click OK.
-
Click Close.
-
-
 Prepare the Reverse Proxy
Prepare the Reverse Proxy
The Reverse Proxy makes sure that requests from mobile devices and Capsule Docs clients that do not have internal network access reach the Endpoint Security Server.
If you use a Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. as the Capsule Docs Reverse Proxy, do the procedures in this section. Alternatively, you can configure a third party server, for example an Apache Server, as a Reverse Proxy Server. See sk102973 to use a third party server as a Reverse Proxy Server.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. as the Capsule Docs Reverse Proxy, do the procedures in this section. Alternatively, you can configure a third party server, for example an Apache Server, as a Reverse Proxy Server. See sk102973 to use a third party server as a Reverse Proxy Server.To prepare the Security Gateway for the Capsule Docs Reverse Proxy you must:
-
Enable the Mobile Access
 Check Point Software Blade on a Security Gateway that provides a Remote Access VPN access for managed and unmanaged clients. Acronym: MAB. component on the Security Gateway.
Check Point Software Blade on a Security Gateway that provides a Remote Access VPN access for managed and unmanaged clients. Acronym: MAB. component on the Security Gateway. -
Configure the Reverse Proxy on the Security Gateway or server to point to the Endpoint Security Management Server.
Note - Make sure the name of the Endpoint Security Management Server resolves correctly in DNS.
-
For Gaia
 Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems.: If the Gaia Portal
Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems.: If the Gaia Portal Web interface for the Check Point Gaia operating system. of the Mobile Access Security Gateway is on https://<IP Address of Security Gateway>/ with a "/" at the end and on TCP port 443, you must change the URL or port.
Web interface for the Check Point Gaia operating system. of the Mobile Access Security Gateway is on https://<IP Address of Security Gateway>/ with a "/" at the end and on TCP port 443, you must change the URL or port.For example, change the URL to https://<IP Address of Security Gateway>/gaia or change the TCP port to 4434.
Change the URL in the Gateway Properties tree select Platform Portal and change the Main URL.
This change requires a policy installation.
If you do not make this change, the Gaia Portal is not accessible.
To enable the Mobile Access component on the Security Gateway:
-
In SmartConsole, double click the Security Gateway object.
-
In the properties window that opens, select Mobile Access in the components section.
The Mobile Access Configuration wizard opens.
-
Click Cancel, if you want to use the Security Gateway as a reverse proxy only.
The Mobile Access Policy is created, but has no rules in it.
-
Click OK.
-
In the main menu, go to Policy > Install.
-
Select the Security Gateway to install policy only on the Security Gateway.
During policy installation, a warning shows: The Mobile Access Policy does not contain any rules. You can ignore this.
-
Click OK.
To configure the Capsule Docs proxy on the Security Gateway:
-
On the Security Gateway, run:
ReverseProxyCLI add application capsule_docs <public_server_name> <capsule_docs_server>Where:
-
<public_server_name>is the Capsule Docs Server public name, configured in SmartEndpoint. This hostname should be resolved to the Reverse Proxy Gateway (for example:capsuledocs.externalsite.com). -
<capsule_docs_server>is the Capsule Docs Server internal hostname OR IP address(for example:capsuledocs.internalsite.com OR 1.1.1.1).
-
-
Follow the on-screen instructions.
Make sure that the output of Please wait.. Calculating your internal Host (host) IP addresses is the IP address of the internal server and that no warnings are shown.
-
Run:
ReverseProxyCLI apply configMake sure the command output is: Finished applying configuration successfully.
If warnings are shown you must resolve the problems before you continue.
You can also enable Single Sign-On for Capsule Workspace with Capsule Docs users.
To enable Single Sign-On for Capsule Workspace Capsule Docs users:
-
In SmartConsole, click Security Policies.
-
Click Shared Policies > Mobile Access.
-
Click Open Mobile Access Policy in SmartDashboard.
-
In the SmartDashboard
 Legacy Check Point GUI client used to create and manage the security settings in versions R77.30 and lower. In versions R80.X and higher is still used to configure specific legacy settings. Mobile Access tab, from the navigation tree, select Applications > Web Applications.
Legacy Check Point GUI client used to create and manage the security settings in versions R77.30 and lower. In versions R80.X and higher is still used to configure specific legacy settings. Mobile Access tab, from the navigation tree, select Applications > Web Applications.The list of all Web Applications shows.
-
Click New.
The Web Application window opens.
-
In the General Properties screen, enter the Name of the new Capsule Docs Web Application
-
In the Authorized Locations screen, select the Host name or the DNS name of the Endpoint Security Management Server.
If it does not show in the drop-down menu, click Manage > New, select Host or DNS Name, and configure the new Endpoint Security Management Server.
-
In the Directories section of the Authorized Locations screen, select Allow access to specific directories, and add new directories:
-
Click New.
-
In the window that opens, type in the directory path.
The new directories are:
-
/eps/client/services/DirectoryService -
/eps/client/services/EpsCommonService -
/eps/mobile/getDocumentcKey -
/eps/mobile/login -
/policy
-
-
Click OK.
-
-
In Services section of the Authorized Locations screen:
-
Select https as the Default.
-
Clear http.
-
-
In the Link in Portal screen, configure these settings:
-
Select Add a link to this Web application in the Mobile Access Portal.
-
In the Link text field, enter a label for the link. This does not affect users.
-
Enter the URL:
https://<Host or DNS Name of Endpoint Security Management Server> -
In the Tooltip field, enter the external name of the Endpoint Security Management Server exactly as it is configured on the Endpoint Security Management Server.
-
-
In the Additional Settings > Single Sign-On screen, configure these settings:
-
Select Turn on Single Sign-On for this application.
-
Select Advanced for When a user signs in to this application.
-
Click Edit.
-
In the window that opens, select This application reuses the portal credentials.
If authentication fails, Mobile Access prompts users and stores their credentials.
-
Click OK.
-
Click Edit in the Login Settings section.
-
In the window that opens, select The users of this application belong to the following Windows domain, and enter the users' domain name.
-
Click OK.
-
-
In the Additional Settings > Link Translation screen, select Using the following method and Path Translation.
Note - In Security Gateway objects, Path Translation is supported by default.
-
Click OK.
-
Install Policy.

Note - To grant access to an application for the Capsule Workspace users, you must add a Single Sign-On access rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. to the Capsule Workspace policy.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. to the Capsule Workspace policy.
-
-
 Configure an email server
Configure an email server
To send protected documents to external users, you must configure your email server. Two types of email servers are supported:
-
SMTP (default)
-
FileSystem
To configure the email server:
-
In SmartEndpoint, select Manage > Email Server Settings > Configure Settings.
-
In the Email Server Settings window, enter the email server host name or IP address.
-
Select the Port number for the email server (default = 25).
-
If the email server requires an SSL connection, select Enable SSL Encryption.
-
If email server authentication is necessary, select User authentication is required and enter the credentials.
-
Click Send Test Email to make sure that you can successfully access the email server.
-
In the window that opens, enter an email address that the test will be sent to and click Send.
-
If the verification succeeds, an email is sent to the email address entered and a Success message shows in the Email Server Settings window.
-
If the verification fails, an Error message shows in the Email Server Settings window. Correct the parameters errors or resolve network connectivity issues. Stand on the Error message to see a description of the issue.
-
-
Click OK to save the email server settings and close the window.
Troubleshooting issues with email settings
If the email server does not send alerts and email server authentication is not necessary do these steps:
-
In SmartEndpoint, select Manage > Email Server Settings > Configure Settings.
-
In the Email Server Settings window select User authentication is required.
Configure these parameters:
-
Port - Leave the default (25).
-
User Name -Enter a fictitious email address. This address will show as the sender of email alerts.
-
Password -Enter a fictitious password. This is not used.
-
-
Optional: Trigger an alert to test the email server.
-
-
 Configure Single Sign-On with Active Directory
Configure Single Sign-On with Active Directory
For managed clients to seamlessly authenticate to Capsule Docs with users' AD credentials, enable Single Sign-On with Active Directory authentication.
The default setting is Do not allow Single Sign-On with Active Directory.
To enable Single Sign-On with Active Directory:
-
Prepare the Active Directory server for authentication. Use the instructions in Configuring Active Directory Authentication.
-
Configure the authentication settings in SmartEndpoint. Use the instructions in Step 2 of 3: Configuring Authentication Settings.
To enable Capsule Docs Single Sign-On, it is not necessary to select Work in authenticated mode.
 >
>
Best Practice - We recommended that you do not select this option during the evaluation and lab stage.
-
Save.
-
In SmartEndpoint, Policy tab, in the Capsule Docs policy rules, select Allow Single Sign-On with Active Directory.
-
Install policy in SmartEndpoint.
-
Using Capsule Docs
When users create a new document in a supported application, the protection settings of their default Capsule Docs community are applied to the document. Users can change the settings through the Capsule Docs menu.
In some MS Office versions, the menu shows in the upper-right corner of documents. In others it shows in the Home tab.
Based on the Capsule Docs policy that you configure, users can:
-
Change document Classification
-
Change Community
-
Remove protection
-
Add or remove users and groups
-
Set a document expiration date (only document Authors can do this)
-
Create Favorites lists of users and groups.

Note - The Favorites lists can be used across the supported applications, to share the documents with different sets of users.
To learn more, see the Capsule Docs User Guide for your client release in sk117536.
Configuring Capsule Docs Policy Rules
For each Action in a rule, select an option, which defines the Action behavior. You can select a predefined Action option or select New to define a custom Action option.
Right-click an Action and select Edit or Edit Shared Action to change the Action behavior.
Changes to policy rules are enforced only after you install the policy.
Actions with the ![]() icon apply to all of the organization.
icon apply to all of the organization.
Organization Settings
The Organization Settings define the name of the organization and the name of the Public or External Server. This is the domain name that leads to the reverse proxy server or Security Gateway.
|
|
Note - The Public Server Name should be configured one time and not changed. |
Active Classifications
Define the Capsule Docs classifications in use and the permissions associated with them.
Also define the permissions of document Authors. By default the permissions are set to be based on the classifications assigned to individual documents or higher. However, you can change them as necessary. A document can have multiple authors. Classification based means that the setting for the Author is the same as what is defined for the Classification.
To create a new classification:
-
Click Create Classification.
To delete a classification:
-
Click Revoke Classification.
To change the order of the classifications that end-users see in the Capsule Docs menu:
-
Select a classification from the table and click the up and down arrows
For each Classification, define its properties and permissions in the table. For more details about the options see sk105076.
|
Column |
Description |
|---|---|
|
Icon |
Select the icon that users see in protected documents. |
|
Classification Name |
Give the classification a descriptive name. |
|
Applied On |
|
|
Encrypted |
|
|
Edit |
Can users edit the document: Yes or No. |
|
Modify Users |
Can users add or remove users and groups: Yes or No. |
|
Change Classification |
Can users change the classification of a document: Yes or No. |
|
Unprotect |
Can users make a document unprotected: Ask, Yes, or No. If Ask is selected, users must give a reason if they choose to unprotect a document. |
|
Mobile Access |
Can the document be accessed through Capsule Docs on mobile devices: Yes or No. |
|
|
Can users print the document: Yes or No. |
|
Screen Capture |
Can users take screenshots of the document: Ask, Yes, or No. If Ask is selected, users must give a reason that they require screenshots. |
|
Copy Paste |
Can users copy from the document and paste in their device: Yes or No. |
|
Markings |
Double-click to change the selection. Select a header, footer, or watermark with the Classification Name to include in the document. Different markings are supported for different document types. |
Email Domains for Sharing Documents
Email Domains for sharing documents Defines permissions for new user registration, based on email domains. Each domain can be defined as either Internal or External. There are two default domains that cannot be edited or deleted:
-
AD Scanned Domains - Defined as Internal and contains users added by the Active Directory scanner.
-
Non AD Scanned Domains - Defined as External and contains users that are not configured in the Domain Configuration window.
You can add more Internal or External Non AD Scanned Domains, and set the permissions to add New Users from them:
-
Can register after explicitly added to a document
-
Can register without being explicitly added to a document
-
Not allowed
Automatic Protection
Define the default encryption behavior for new documents:
-
Enforce automatic protection for new documents
-
Do not enforce automatic protection
-
Suggest document protection when saving document
You can also manually select or clear these options in the Properties of the Action:
-
Protect new documents created by internal users
-
Suggest to protect when user saves document
-
Suggest to protect when user performs Save As
Initial Protection Configuration
Define the default protection settings that are assigned to newly protected documents. Users with the required permissions can edit these settings from the document.
The settings are:
-
Select the classification, for example, Restricted or Highly Restricted.
The classifications and permissions shown are those configured in the Classifications and Permissions Action. You cannot edit them from this Action.
-
Add and remove user groups that show in newly protected documents.
-
Configure which users or groups have Author permissions. The Document Protector is the person who first protects the document. This person can have Author permissions but it is not required. One or more entities must have Author permissions.
To add and remove user groups that show in newly protected documents:
-
Click the arrow and select Manage Groups to open the organizational tree and select one or more groups to add to the list.
-
Select one or more groups from the list. These groups are added to the initial protection list that is automatically assigned to a document.
All groups that show in the Protection Setting window are assigned to the document.
-
To remove a group or user, select it from the list and click the X.
To configure which users or groups have Author permissions:
-
Right-click the Document Protector or a different user or group and select an option:
-
Remove as Document Author
-
Mark as Document Author
-
If the default classification does not have encryption:
All users can access it and the users and groups selected here only apply if the classification is changed to one with encryption.
Inviting Users
Set permissions for the ability to add new users to a document if they are not yet invited or registered. By default, all users in the internal domains have permission to the documents and do not require invitations.
The options are:
-
Allow inviting users from any domain
-
Do not allow inviting users
If you select Allow inviting users from any domains, you can also limit the users who can be invited to those from specified domains.
To limit the users who can be invited to a document:
-
In a Capsule Docs rule, right-click the Inviting Users Action and select Edit Shared Action.
-
In the bottom part of the Properties window, in the Permission to invite new users list, select Allow only from the following domains.
-
Click Add to add domains to the list. Only users in domains on the list can be invited.
Client Access Settings
Configure Client access to protected documents.
Set the period of downtime, after which if the client does not get updated, the access to protected documents becomes blocked. You can also configure how often the client checks for updates.
Single Sign-On with Active Directory
This Action defines permissions for Single Sign-On with Active Directory. The default is Do not allow Single Sign-On with Active Directory.
Working with External Users
You can add external users who can access Capsule Docs protected documents in these ways:
-
A user adds an external user to a document.
-
An external user downloads the Capsule Docs client and registers.
-
An administrator adds a user or domain in SmartEndpoint. The administrator can add individual users or import users from a .csv file.
-
Right-click the External Users folder in the Users and Computers tree and select Capsule Docs > Add External Users.
-
In the Global Actions pane, select Add External Users.
-
The first time that an external user from a new domain is added to the system, a new folder is created for the domain in the Users and Computers tree under External Users.
External users are in one of these states, shown in the User Details:
-
Invited - A user added the external user to a document but the new user did not register yet.
-
Registered - The user downloaded the Capsule Docs client and registered with an email address.
-
Revoked - The administrator revoked the user and the user cannot log in to Capsule Docs or see documents. Revoked users are in the Revoked Users folder. Administrators can Restore or Delete users from there.
An administrator can give an external user or domain internal permissions.
To give an external user the same permissions as an internal user:
Right-click on a user or domain from the Users and Computers tree and select Grant internal permission (for document use).
External users who have internal permissions are shown in the Capsule Docs internal users Virtual Group.
To revoke an external user:
Right-click on a user or domain from the Users and Computers tree and select Revoke user. The user is moved to the Revoked Users folder. You cannot delete external users.
Troubleshooting Capsule Docs Reverse Proxy
Traffic Logs
You can configure the Reverse Proxy to send traffic logs, which then can be reviewed in SmartLog, under Mobile Access logs.
To configure the Reverse Proxy to send traffic logs:
-
In SmartConsole, click Security Policies.
-
Click Shared Policies > Mobile Access.
-
Click Open Mobile Access Policy in SmartDashboard.
-
In SmartDashboard Mobile Access tab, go to Additional Settings > Logging.
-
In the Tracking section of the configuration screen, select Log Access for Web Applications, and select events to log:
-
Unsuccessful access events
-
All access events
-
-
Install Policy.
Identify Reverse Proxy logs by these criteria:
-
Category: Mobile Access
-
Application: Reverse Proxy
The Access section of the log can show:
-
Allowed - Authorized URL - The Reverse Proxy allowed the URL request (only shows if the All access events logging option is configured)
-
Denied - Unauthorized URL -The Reverse Proxy blocked the URL request. If this is a mistake, you can allow the URL.
To allow a blocked URL:
-
On the command line, run:
ReverseProxyCLI show applications -
Under
capsule_docs appin the Paths column, find the path that is unauthorized in the log.
-
-
Failed - The Reverse Proxy failed to forward the request for the EPS with one of these messages:
-
Internal Server Error - The Endpoint Security Management Server aborted the connection with the Security Gateway. Make sure the Endpoint Security Management Server is working.
-
Proxy not found -The given proxy host could not be resolved.
-
Can't resolve host name - The
<capsule_docs_server>is theinternal_hostyou configured in yourcapsule_docsapplication, you can see it underReverseProxyCLI show applicationsin theInternal Server Namecolumn.Your Endpoint Security Management Server is configured as a DNS name. Make sure that this hostname can be resolved from the Security Gateway. To do this run
nslookupon the host to see that the Security Gateway can resolve it. -
Internal host connection failed - Failed to connect to the internal server, make sure the server is up and running.
-
Invalid URL - The URL from the Security Gateway to the Endpoint Security Management Server was not properly formatted.
-
SSL handshake failed -A problem occurred somewhere in the SSL/TLS handshake between the Security Gateway and the Endpoint Security Management Server.
-
Server response was too slow - Operation timeout.
-
Page not found
-
-
Action that the Reverse Proxy took in relationship to this URL - Allowed, Denied, or Failed
Capsule Docs Recovery
The Capsule Docs Recovery Tool generates a master key that can open all documents in a situation of disaster recovery.
A new master key is valid for one year. Therefore we recommend that you generate a new master key every year. A notification shows in the SmartEndpoint Overview page when the master key is close to its expiration date. A new master key can open all documents that were created before its creation and up to one year afterwards.
To get the Capsule Docs Recovery Tool:
-
In the SmartEndpoint, select Tools > Capsule Docs Recovery Tool.
-
In the window that opens, create a Recovery Key Password and enter it twice.
-
Click Save As and select a location where the Tool is saved in a zip file.
-
If necessary, extract the tool and use the included instructions.
