Active Directory Authentication
Endpoint Security Active Directory Authentication
When an Endpoint Security client connects to the Endpoint Security Management Server![]() A Security Management Server that manages your Endpoint Security environment. Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data., an authentication process identifies the endpoint client and the user currently working on that computer.
A Security Management Server that manages your Endpoint Security environment. Includes the Endpoint Security policy management and databases. It communicates with endpoint clients to update their components, policies, and protection data., an authentication process identifies the endpoint client and the user currently working on that computer.
The Endpoint Security system can function in these authentication modes:
-
Unauthenticated mode - Client computers and the users on those computers are not authenticated when they connect to the Endpoint Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server.. They are trusted "by name". This operation mode is recommended for evaluation purposes only.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server.. They are trusted "by name". This operation mode is recommended for evaluation purposes only. -
Strong Authentication mode - Client computers and the users on those computers are authenticated with the Endpoint Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. when they connect to the Endpoint Security Management Server. The authentication is done by the Active Directory server using the industry-standard Kerberos
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. when they connect to the Endpoint Security Management Server. The authentication is done by the Active Directory server using the industry-standard Kerberos An authentication server for Microsoft Windows Active Directory Federation Services (ADFS). protocol. This option is only available for endpoints that are part of Active Directory.
An authentication server for Microsoft Windows Active Directory Federation Services (ADFS). protocol. This option is only available for endpoints that are part of Active Directory.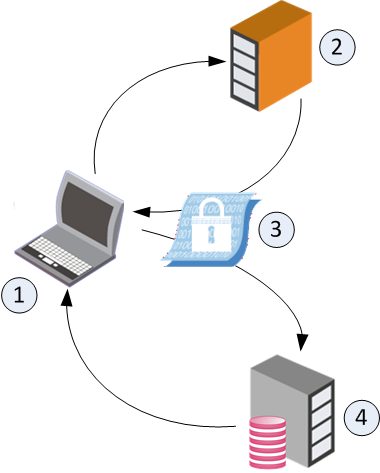
The authentication process:
-
The Endpoint Security client (1) requests an authentication ticket from the Active Directory server (2).
-
The Active Directory server sends the ticket (3) to the client (1).
-
The client sends the ticket to the Endpoint Security Management Server (4).
-
The Endpoint Security Management Server returns an acknowledgment of authentication to the Endpoint Security client (1).
The default behavior after Security Management Server installation is Unauthenticated mode. It is recommended that you use this mode when you are evaluating Endpoint Security, in a lab environment. Change to Strong Authentication mode just before moving to a production environment. It is not recommended to continue to work in Unauthenticated mode after moving to production in a live environment.
|
|
Important - If you use Active Directory Authentication, then Full Disk Encryption Note - If you have endpoint computers in your environment that are not part of Active Directory, Full Disk Encryption and Media Encryption & Port Protection will not work on them. |
Configuring Active Directory Authentication
Make sure you configure Strong Authentication for your production environment. Do not set up Strong Authentication before you are ready to move to production. When you are ready to move to production, follow this process.
Workflow for Configuring Strong Authentication:
Endpoint Security Strong Authentication uses the Kerberos network authentication protocol.
To enable the Active Directory server to validate the identity of clients that authenticate themselves through Kerberos, run the ktpass.exe command on the Active Directory Server. By running the ktpass command, you create a user that is mapped to the ktpass service. This creates a Principal Name for the AD server. The Principal Name must have the following format: ServiceName/realm@REALM
|
|
Important - After you create the user that is mapped to the |
To prepare the Active Directory Server for authentication:
-
On the Active Directory Server, run the
ktpass.exein this folder:C:\Windows\System32 -
Go to Start > All Programs > Administrative Tools > Active Directory Users and Computers.
-
Create a domain user and clear the User must change password at next logon option.
-
Run this command to map a service to a user:
Syntax:
ktpass princ ServiceName/realm@REALM mapuser <userName>@REALM pass <userPass> out <name of outFile>Example:
ktpass princ tst/nac1.com@NAC1.COM mapuser auth-user@NAC1.COM pass 123456 out outfile.keytabExplanations:
Syntax
Example value
Explanation
ServiceNametstName of the service.
realmnac1.comDomain name of the Active Directory server. The first instance is in lower case. The second in upper case.
<userName>auth-userThe Active Directory domain user.
<userPass>123456Password for user.
<name of outFile>outfile.keytabName of the encrypted keytab file.
-
Save the console output to a text file. See the version number (
vno) and encryption type (etype).Sample output:
Targeting domain controller: nac1-dc.nac1.comSuccessfully mapped tst/nac1.com to auth-user.WARNING: pType and account type do not match. This might cause problems.Key created.Output keytab to outfile.log:Keytab version: 0x502keysize 74 tst/nac1.com@NAC1.COM ptype 0 (KRB5_NT_UNKNOWN) vno 7 etype 0x17 (RC4-HMAC) keylength 16 (0x32ed87bdb5fdc5e9cba88547376818d4)
Important - We recommend that you do not use DES-based encryption for the Active Directory Domain Controller server, as it is not secure. If you choose to use DES encryption and your environment has Windows 7 clients, see sk64300.

Notes -
-
Make sure that the clock times on the Endpoint Security servers and the Kerberos server are less than 5 minutes apart. If difference in the clock times is more than 5 minutes, a runtime exception shows and Active Directory authentication fails. On Gaia
 Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems., use NTP or a similar service.
Check Point security operating system that combines the strengths of both SecurePlatform and IPSO operating systems., use NTP or a similar service. -
To use Capsule Docs
 A component on Endpoint Security Windows clients. This component provides security classifications and lets organizations protect and share documents safely with various groups - internal and external. with Single Sign-On, disable User Access Control on Windows Active Directory Servers.
A component on Endpoint Security Windows clients. This component provides security classifications and lets organizations protect and share documents safely with various groups - internal and external. with Single Sign-On, disable User Access Control on Windows Active Directory Servers.
-
Configure the settings in SmartEndpoint for client to server authentication.
|
|
Important - Use the Unauthenticated mode only for evaluation purposes. Never use this mode for production environments. Configure the authentication settings before moving to production. |
How the Authentication Settings are Used in Deployment Packages
When you configure client package profiles, you choose an authentication account. The SSO Configuration details are included in the client deployment package, allowing the server to authenticate the client.
To configure authentication settings:
-
In SmartEndpoint open Manage > Endpoints Authentication Settings.
The Authentication Settings Properties window opens.
-
Click Add.
The New Authentication Principal Properties window opens.
-
Enter the details from the output of
ktpass.exethat you configured in Step 1 of 3: Configuring the Active Directory Server for Authentication:Field
Description
Domain name
Active Directory domain name.
For example:
nac1.comPrinciple Name
Authentication service name in the format:
ServiceName/realm@REALMThis value must match the name that was configured in Active Directory > New Object.
For example:
tst/nac1.com@NAC1.COMVersion Key
Enter the version number according to the Active Directory output in the
vnofield.For example:
7Encryption method
Select the encryption method according to the Active Directory output in the
etypefield.For example:
RC4-HMACPassword
Enter (and confirm) the password of the Active Directory Domain Admin user you created for Endpoint Security use.
For example:
123456 -
Click OK.
-
When you are ready to work in Strong Authentication mode, select Work in authenticated mode in the Authentication Settings Properties window.
-
Click OK.
|
|
Important - After turning on Strong Authentication, wait one minute before initiating any client operations. It will take time for the clients and the Endpoint Security Management Server to synchronize. During this time, the environment will remain unauthenticated, and some operations will fail. The exact amount of time depends on the synchronization interval (see Active Directory Scanner). |
After you have finished configuring strong authentication for Active Directory, save your changes.
-
Go to the Policy tab of SmartEndpoint.
-
In the Policy Toolbar, click Save
 .
.
UPN Suffixes and Domain Names
The User Principal Name (UPN) is the username in "email format" for use in Windows Active Directory (AD). The user's personal username is separated from a domain name by the "@" sign.
UPN suffixes are part of AD logon names. For example, if the logon name is administrator@ad.example.com, the part of the name to the right of the ampersand is known as the UPN suffix. In this case ad.example.com
When you configure a new user account in AD, you are given the option to select a UPN suffix, which by default will be the DNS name for your AD domain. It can be useful to have a selection of UPN suffixes available. If your AD domain name is ad.example.com, it might be more convenient to assign users a UPN suffix of example.com. To make additional UPN suffixes available, you need to add them to AD.
Configuring Alternative Domain Names
When configuring Strong Authentication for Active Directory communication between the Endpoint Security client and the Endpoint Security Management Server, you can configure multiple UPN suffixes for the Active Directory domain name.
To Configure Additional UPN Suffixes for Active Directory Authentication
-
In SmartEndpoint open Manage > Endpoints Authentication Settings.
The Authentication Settings Properties window opens.
-
Click Add.
The New Authentication Principal Properties window opens.
-
In the Domain name field, enter the alternative Active Directory domain name. For example, if the previously configured domain name is
nac1.comadd an alternative domain name such asad.nac1.com -
Configure the other fields with the same values as the previously configured authentication settings:
-
Principle Name
-
Version Key
-
Encryption Method
-
Password
-
-
Click OK.
-
Save the changes. Go to the Policy tab of SmartEndpoint, and in the Policy Toolbar, click Save

Troubleshooting Authentication in Server Logs
To troubleshoot problems related to Active Directory Authentication, use the Authentication log on the Endpoint Security Management Server or Endpoint Policy Server![]() Endpoint Policy Server improves performance in large environments by managing most communication with the Endpoint Security clients. Managing the Endpoint Security client communication decreases the load on the Endpoint Security Management Server, and reduces the bandwidth required between sites. The Endpoint Policy Server handles heartbeat and synchronization requests, Policy downloads, Anti-Malware updates, and Endpoint Security client logs. in the
Endpoint Policy Server improves performance in large environments by managing most communication with the Endpoint Security clients. Managing the Endpoint Security client communication decreases the load on the Endpoint Security Management Server, and reduces the bandwidth required between sites. The Endpoint Policy Server handles heartbeat and synchronization requests, Policy downloads, Anti-Malware updates, and Endpoint Security client logs. in the $UEPMDIR/logs/Authentication.log file.
To see full debugging information in the Authentication.log file on an Endpoint Security server:
-
On the Endpoint Security server, run:
export TDERROR_ALL_KERBEROS_SERVER=5 -
Restart the Endpoint Security server. Run:
uepm_stop ; uepm_start
Results in Authentication.log
-
If the Authentication.log file on the server shows:
ERROR: Config file contains no principals
The database was cleaned or the process to include authentication in the client package was faulty. To fix:
-
Repeat the process to configure Active Directory authentication (See Configuring Active Directory Authentication).
-
Make a new client package.
-
Restart the Endpoint Security server:
reboot
-
-
If the Authentication.log file on the server shows:
Permission denied in replay cache code
Restart the Endpoint Security server:
reboot -
If the Authentication.log file on the server shows:
Clock skew too great
-
Make sure that the Endpoint Security Management Server and all clients are synchronized with the Active Directory server.
-
Make sure that in the Windows Date and Time Properties window, the Automatically adjust clock for daylight saving changes option has the same value (selected or cleared) for all computers in the system, including the Active Directory server.
-
The following workaround is not recommended, for security reasons, but is offered if you cannot fix the clock skew error with synchronization changes.
To ensure that authentication occurs even if the clocks of the client, the Endpoint Security Management Server and the Active Directory server are out of synch, define an acceptable skew. By default, the authentication clock skew is 3600 seconds. You can change the Endpoint Security settings. In the
$UEPMDIR/engine/conf/global.propertiesfile, add this line:authentication.clockSkew.secs=<seconds>, where you replace<seconds>with the clock skew in seconds that you want to allow.
-
-
If the Authentication.log file on the server shows:
Key version number for principal in key table is incorrect
Update the Key version number in the Active Directory SSO Configuration window.
You might have changed the user that is mapped to the
ktpassservice (see Step 1 of 3: Configuring the Active Directory Server for Authentication.
To turn off full debugging information on the Endpoint Security server:
-
On the Endpoint Security server, unset the debug variable:
unset TDERROR_ALL_KERBEROS_SERVER -
Make sure that the output is empty:
echo $TDERROR_ALL_KERBEROS_SERVER -
Restart the Endpoint Security server. Run:
uepm_stop ; uepm_start
Troubleshooting Authentication in Client Logs
The Authentication.log file for each Endpoint Security client is on the client computer at %DADIR%/logs.
A normal log is:
|
|
If the Authentication.log file on the client shows:
|
|
The Endpoint Agent cannot find a Domain Controller to supply credentials.
To fix this:
-
Make sure that the client is in the domain and has connectivity to your Domain Controller.
-
To authenticate with user credentials, log off and then log in again.
To authenticate with device credentials, restart the computer.
If the Authentication.log file on the client shows:
|
|
Check the service name. Make sure that there are no typing errors and that the format is correct.
If there was an error, correct it on the Check Point Endpoint Security Management Server.
