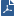
Multiple Entry Point for Site to Site VPN
Configuring Explicit MEP
Explicit MEP is only available in Site-to-Site Star VPN communities where multiple central Security Gateways are defined.
To configure MEP:
- Open the object and go to the page.
- Select .
- Select an entry point mechanism:
- First to respond
- By VPN domain
- Random selection
- Manual priority list
If you select or , in the , section choose or to resolve how more than one Security Gateway with equal priority should be selected.
If you select , click to create a series of MEP rules.
- Select a option, if required.
Configuring Implicit First to Respond
When more than one Security Gateway leads to the same (overlapping) VPN domain, they are in a MEP configuration. The first Security Gateway to respond is chosen. To configure first to respond, define that part of the network that is shared by all the Security Gateways into a single group and assign that group as the VPN domain.
Before you start, make sure that is not enabled:
- In R80 SmartConsole, go to > > > .
- Clear the option.
To configure First to Respond MEP:
- For each Security Gateway in the VPN domain, run
vpn overlap_encdom. - In R80 SmartConsole, create a host group and assign all these Security Gateways to it.
- In each Security Gateway object go to the > page,
- Select .
- Select the host group of MEP gateways that you defined in step 2.
- Click .
- Install the Access Control Policy on all Security Gateways.
Configuring Implicit Primary-Backup
Configure the VPN Domain that includes the Primary gateway and another domain that includes only the backup gateway. Configure each gateway as either the Primary gateway or a backup gateway.
To configure the primary gateway:
- Open Global Properties window > VPN > Advanced, select Enable Backup Gateway.
- In the Object Explorer, click > and create a group of gateways to act as backup gateways.
- Edit the Primary gateway object and open the page.
- Select Use Backup Gateways, and select the group of backup gateways.
This gateway is the primary gateway for this VPN domain.
- For each backup gateway, make a VPN domain that does not include IP addresses that are in the Primary VPN domain or the other backup domains.
If the backup gateway already has a VPN domain, you must make sure that its IP addresses do not overlap with the other VPN domains.
- Create a group of IP addresses not in the other domains, or a group that consists of only the backup gateway.
- In the backup network object, go to the > section, select Manually defined.
- Select the group.
- Click OK.
- Install the policy.
Configuring Implicit Load Distribution
To configure implicit MEP for random gateway selection:
- Click > .
- Open the > page.
- Select .
- Define the same VPN domain for all the gateways:
- Create a group of the gateways.
- In each gateway network object, go to the > page, and select .
- Select the group.
- Click .
- Install the Access Control Policy.
Routing Return Packets
To make sure return packets are routed correctly, the MEP Security Gateway can make use of either:
• IP pool NAT (static NAT) or
• Route Injection Mechanism. For more information on RIM, see Configuring RIM in a Star Community
Configuring IP Pool NAT
To configure IP pool NAT for site to site VPN:
- In Menu > , open the page, and click .
- Set tracking options for address exhaustion and for address allocation and release.
- For each Security Gateway, create a network object that represents the IP pool NAT addresses for that Security Gateway. The IP pool can be a network, group, or address range. For example:
- Open the (Ctrl+E) and click > > > . The window opens.
- On the General tab, enter the first IP and last IP of the address range.
- Click .
- On the Security Gateway object where IP pool NAT translation is performed, in the NAT > IP Pool NAT page, select either
- Allocate IP Addresses from, and select the address range you created, OR
- Define IP Pool addresses on Security Gateway interfaces. If you choose this option, you need to define the IP Pool on each required interface, in the Interface Properties window, IP Pool NAT tab.
- In the IP Pool NAT page, select either (or all):
- Use IP Pool NAT for VPN clients connections
- Use IP Pool NAT for Security Gateway to Security Gateway connections
- Prefer IP Pool NAT over Hide NAT
- Click Advanced...
- Decide after how many minutes unused addressees are returned to the IP pool.
- Click OK twice.
- Edit the routing table for each internal router, so that packets with an IP address assigned from the NAT pool are routed to the appropriate Security Gateway.