

In This Section: |
Identity Awareness uses the source and/or destination IP addresses of network traffic to identify users and computers. You can use these data elements as matching criteria in the Source and Destination fields of your policy rules:
You can define a policy rule for specified users who send traffic from specified computers or from any computer. Likewise, you can create a policy rule for any user on specified computers.
Identity Awareness shows the user and computer name together with the IP address in the logs and reports.
You can see the logs based on user and computer name, and not just IP addresses, in the Logs & Monitor > Logs tab. You can see events in the Logs & Monitor Access Control views.
Identity Awareness gets identities from these acquisition sources. You must enable them on the Gateway, from the Identity Awareness page of the Gateway object:
Identity Awareness Security Gateways can share the identity information that they acquire with Identity Awareness Security Gateways. In this way, users that need to pass through many Security Gateways are only identified once. See Advanced Deployment for more information.
James Wilson is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the Security Gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
He received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets James Wilson access the HR Web Server from his laptop with a static IP (10.0.0.19).
Name |
Source |
Destination |
VPN |
Service |
Action |
Track |
|---|---|---|---|---|---|---|
Jadams to HR Server |
Jadams_PC |
HR_Web_Server |
Any Traffic |
Any |
accept |
Log |
He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator does these steps:
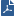
The logs in the Logs & Monitor view of R80 SmartConsole show that the system recognizes James Wilson as the user behind IP 10.0.0.19. This log entry shows that the system maps the source IP to the user James Wilson from CORP.ACME.COM. This uses the identity acquired from AD Query.
|
Note - AD Query maps the users based on AD activity. This can take some time and depends on user activity. If James Wilson is not identified (the IT administrator does not see the log), he should lock and unlock the computer. |
Guests frequently come to the ACME company. While they visit, the CEO wants to let them access the Internet on their own laptops.
Amy, the IT administrator configures the Captive Portal to let unregistered guests log in to the portal to get network access. She makes a rule in the Rule Base to let unauthenticated guests access the Internet only.
When guests browse to the Internet, the Captive Portal opens. Guests enter their name, company, email address, and phone number in the portal. They then agree to the terms and conditions written in a network access agreement. Afterwards they are given access to the Internet for a specified period of time.
To make this scenario work, the IT administrator must:
The CEO of ACME recently bought her own personal iPad. She wants to access the internal Finance Web server from her iPad. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the Firewall Rule Base.
To make this scenario work, the IT administrator must:
The Action Settings window opens.
The Access Role is added to the rule.
Name |
Source |
Destination |
VPN |
Service |
Action |
Track |
|---|---|---|---|---|---|---|
CEO Access |
Daniel David |
Finance_Server |
Any Traffic |
http |
Accept (Enable Identity Captive Portal) |
Log |
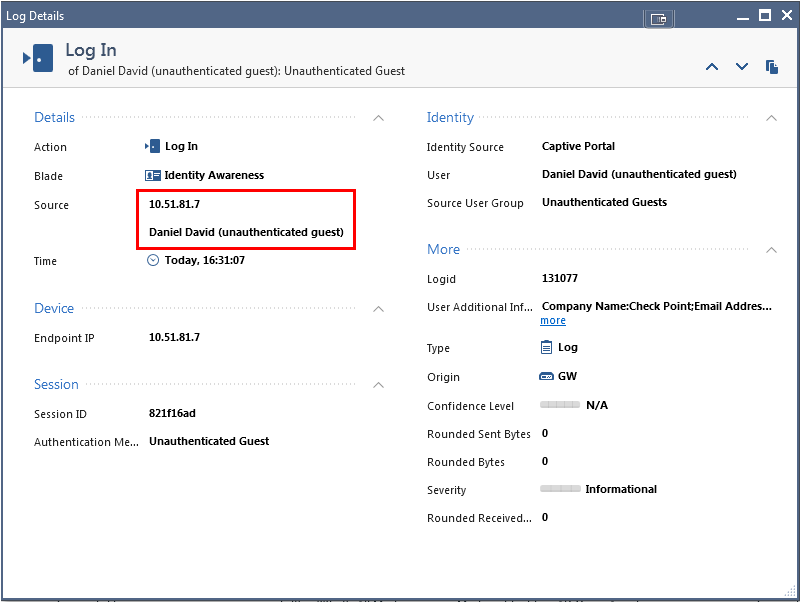
The log entry in the Logs tab of the Logs & Monitor view shows how the system recognizes Daniel David from his iPad. This uses the identity acquired from Captive Portal.
The ACME organization wants to make sure that only the Finance department can access the Finance Web server. The current Rule Base uses static IP addresses to define access for the Finance department.
Amy, the IT administrator wants to leverage the use of Endpoint Identity Agents so:
Amy wants Finance users to download the Endpoint Identity Agent from the Captive Portal. She needs to configure:
After configuration and policy install, users that browse to the Finance Web server will get the Captive Portal and can download the Endpoint Identity Agent.
The ACME organization wants to use Identity Awareness to monitor outbound application traffic and learn what their employees are doing. To do this, the IT administrator must enable Application Control and Identity Awareness. Identity information for the traffic then shows in the logs and events. See the logs in the Logs & Monitor > Logs tab. See the events in the Logs & Monitor views, in the Access Control categories.
Next, the IT department can add rules to block specific applications or track them differently in the Application Control and URL Filtering Layer of the policy to make it even more effective. See the R80 Application Control and URL Filtering Administration Guide.
You can see data for identified users in the Logs and Events that relate to application traffic. See Logs in the Logs & Monitor view Logs tab. See Events in the Logs & Monitor Access Control views, and in the SmartEvent GUI client.
The log entry shows that the system maps the source IP address with the user identity. It also shows Application Control data.