

In This Section: |
The information here applies to the second Policy Layer, which is Application and URL Filtering.
You must have a contract for Application Control and URL Filtering for each Security Gateway on which these blades are enabled. This is in addition to the Security Gateway license. For clusters, make sure you have a contract and license for each cluster member.
New installations and upgraded installations include a 30 day trial license and contract. Contact your Check Point representative to get full licenses and contracts.
If you do not have a valid contract for a Security Gateway, the Application Control blade and the URL Filtering blade are disabled. When contracts are about to expire or are already expired, warnings show in:
You can enable the Application Control Software Blade, the URL Filtering Software Blade,or both of them, on each Security Gateway.
Note - For Application and URL Filtering to work properly, you must also enable Application and URL Filtering in the Access Control Policy.
To enable Application and URL Filtering on a Security Gateway:
The Gateway Properties window opens.
To see which Security Gateways enforce Application and URL Filtering:


After upgrading a Security Management Server from R77.x to R80, the Firewall Policy and the Application and URL Filtering Policy are converted to these Policy Layers:
For the Application Control Policy Layer to work, make sure that both - Firewall and Application and URL Filtering Software Blades are enabled in it.
To enable Application and URL Filtering in the Access Control Policy:
The Policy window opens.
To see logs for Application and URL Filtering:
The logs show how applications are used in your environment and help you create effective Rule Bases.
Create and manage the Policy for Application Control and URL Filtering in the Access Control Policy, in the Security Policies view of R80 SmartConsole. The Access Control Policy defines which users can use specified applications and sites from within your organization and what application and site usage is recorded in the logs.
Scenario: I want to monitor all Facebook traffic in my organization. How can I do this?
To monitor all Facebook application traffic:
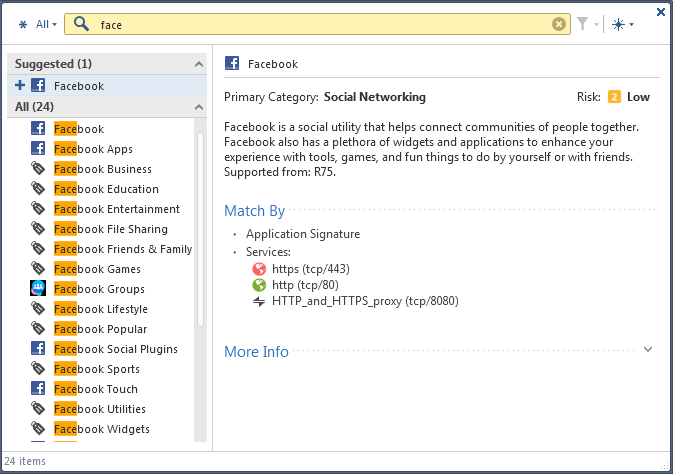
Note - Applications are matched on their Recommended services, where each service runs on a specific port, such as the default Application Control Web browsing services: http, https, HTTP_proxy, and HTTPS_proxy. To change this see Changing Services for Applications and Categories.
The rule allows all Facebook traffic but logs it. You can see the log data in the Logs & Monitor view, in the Logs tab. To monitor how people use Facebook in your organization, see the Access Control tab (SmartEvent Server required).
Scenario: I want to block YouTube in my organization. How can I do this?
To block an application or category of applications, such as YouTube, in your organization:
Note - Applications are matched on their Recommended services, where each service runs on a specific port, such as the default Application Control Web browsing services: http, https, HTTP_proxy, and HTTPS_proxy. To change this see Changing Services for Applications and Categories.
The message informs users that their actions are against company policy and can include a link to report if the website is included in an incorrect category.
Note: This Rule Base example contains only those columns that are applicable to this subject.
Name |
Source |
Destination |
Services & Applications |
Action |
Track |
Install On |
|---|---|---|---|---|---|---|
Block Porn |
Any |
Internet |
YouTube |
Drop |
Log |
Policy Targets |
The rule blocks traffic to YouTube and logs attempts to access sites that are in the pornography category. Users who violate the rule receive a UserCheck message that informs them that the application is blocked according to company security policy. The message can include a link to report if the website is included in an incorrect category.
|
Important - A rule that blocks traffic, with the Source and Destination parameters defined as Any, also blocks traffic to and from the Captive Portal. |
Scenario: I want to limit my employees' access to streaming media so that it does not impede business tasks.
If you do not want to block an application or category, there are different ways to set limits for employee access:
The example rule below:
To create a rule that allows streaming media with time and bandwidth limits:
Note - Applications are matched on their Recommended services, where each service runs on a specific port, such as the default Application Control Web browsing services: http, https, HTTP_proxy, and HTTPS_proxy. To change this see Changing Services for Applications and Categories.
Note - The Time column is not shown by default in the Rule Base table. To see it, right-click on the table header and select Time.
Name |
Source |
Destination |
Services and Applications |
Action |
Track |
Install On |
Time |
||
|---|---|---|---|---|---|---|---|---|---|
Limit Streaming Media |
Any |
Internet |
Media Streams |
Allow |
Log |
All |
Off-Work |
||
|
Note - In a cluster environment, the specified bandwidth limit is divided between all defined cluster members, whether active or not. For example, if a rule sets 1Gbps limit in a three member cluster, each member has a fixed limit of 333 Mbps. |
||||||||
Scenario: I want to allow a Remote Access application for a specified group of users and block the same application for other users. I also want to block other Remote Access applications for everyone. How can I do this?
If you enable Identity Awareness on a Security Gateway, you can use it together with Application Control to make rules that apply to an access role. Use access role objects to define users, machines, and network locations as one object.
In this example:
To do this, add two new rules to the Rule Base:
Name |
Source |
Destination |
Services & Applications |
Action |
Track |
Install On |
|---|---|---|---|---|---|---|
Allow Radmin to Identified Users |
Identified_Users |
Internet |
Radmin |
Allow |
Log |
All |
Block other Remote Admins |
Any |
Internet |
Remote Administration |
Block |
Log |
All |
Notes on these rules:
http, https, HTTP_proxy, and HTTPS_proxy. To change this see Changing Services for Applications and Categories.Scenario: I want to block sites that are associated with categories that can cause liability issues. Most of these categories exist in the Application and URL Filtering Database but there is also a custom defined site that must be included. How can I do this?
You can do this by creating a custom group and adding all applicable categories and the site to it. If you enable Identity Awareness on a Security Gateway, you can use it together with URL Filtering to make rules that apply to an access role. Use access role objects to define users, machines, and network locations as one object.
In this example:
To create a custom group:
You can now use the group in the Access Control Rule Base.
In the Rule Base, add a rule similar to this:
In the Security Policies view of R80 SmartConsole, go to the Access Control Policy.
Note - Applications are matched on their Recommended services, where each service runs on a specific port, such as the default Application Control Web browsing services: http, https, HTTP_proxy, and HTTPS_proxy. To change this see Changing Services for Applications and Categories.
Name |
Source |
Destination |
Services & Applications |
Action |
Track |
|---|---|---|---|---|---|
Block sites that may cause a liability |
Identified_Users |
Internet |
Liability_Sites |
Drop |
Log |
Scenario: I want to block pornographic sites. How can I do this?
You can do this by creating a rule that blocks all sites with pornographic material with the Pornography category. If you enable Identity Awareness on a Security Gateway, you can use it together with URL Filtering to make rules that apply to an access role. Use access role objects to define users, machines, and network locations as one object.
In this example:
In the Rule Base, add a rule similar to this:
Note - Categories are matched on their Recommended services, where each service runs on a specific port, such as the default Application Control Web browsing services: http, https, HTTP_proxy, and HTTPS_proxy. To change this see Changing Services for Applications and Categories.
After an upgrade to R80 management, all applications and categories use the recommended services. To change this see Changing Services for Applications and Categories.