Configuring Mirror and Decrypt in VSX mode
Example topology for one Virtual System:
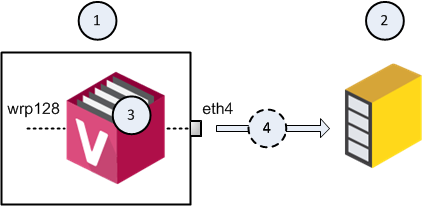
|
Item |
Description |
|---|---|
|
1 |
|
|
2 |
Recorder, or Packet-Broker that works in a monitor (promiscuous) mode. |
|
3 |
Virtual System, through which your networks send and receive their traffic. |
|
4 |
Flow of the decrypted and mirrored traffic from the VSX |
|
eth4 |
Designated physical interface on the VSX Gateway (1). Virtual System (3) connects directly to this physical interface. |
|
wrp128 |
One of the virtual interfaces on the Virtual System (3). |
Example topology for several Virtual Systems:
|
|
Note - This topology requires you to configure a VLAN Trunk on the Recorder or Packet-Broker. The VLAN Trunk on the Recorder or Packet-Broker must accept all VLAN IDs that you configure in the objects of the applicable Virtual Systems in SmartConsole |
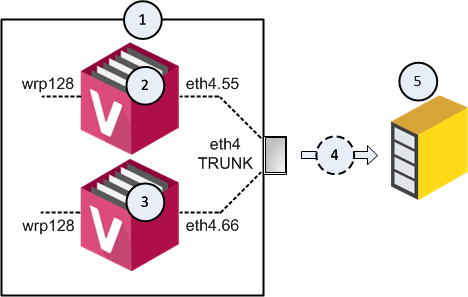
|
Item |
Description |
|---|---|
|
1 |
VSX Gateway. |
|
2 |
First Virtual System, through which your networks send and receive their traffic. |
|
3 |
Second Virtual System, through which your networks send and receive their traffic. |
|
4 |
Flow of the decrypted and mirrored traffic from the VSX Gateway (1) to the Recorder, or Packet-Broker (5). |
|
5 |
Recorder, or Packet-Broker. |
|
eth4 |
Designated physical interface on the VSX Gateway (1). This interface is configured as VLAN Trunk in the VSX Gateway object in SmartConsole. Virtual Systems (2 and 3) connect to this VLAN Trunk interface with VLAN interfaces. |
|
eth4.55 |
VLAN interface on the first Virtual System (2). |
|
eth4.66 |
VLAN interface on the second Virtual System (3). |
|
wrp128 |
One of the virtual interfaces on the Virtual Systems (2 and 3). |
|
|
Important - It is not supported to change the designated physical interface with the " |
Workflow for configuring Mirror and Decrypt in VSX mode:
|
Step |
Instructions |
|---|---|
|
1 |
Read and follow the Mirror and Decrypt Requirements. |
|
2 |
Prepare the VSX Gateway, or each VSX Cluster Member |
|
3 |
Configure the Mirror and Decrypt in the Virtual System object in SmartConsole. See: |


