

In This Section: |
Check Point's R80.20 secures your VoIP environment. Check Point Security Gateways secure VoIP traffic in SIP, H.323, MGCP, and SCCP environments. VoIP calls involve complex protocols, each of which can carry potentially threatening information through many ports.
The Check Point Security Gateways confirm that the caller and receiver addresses are located where they are supposed to be, and that the caller and receiver are allowed to make and receive VoIP calls. The Gateways examine the contents of the packets and confirm that they carry only allowed information. Full stateful inspection on SIP, H.323, MGCP, and SCCP commands ensure that all VoIP packets are structurally valid, and that they arrive in a valid sequence.
This guide explains how to configure the Check Point Security Gateway when VoIP passes through it.
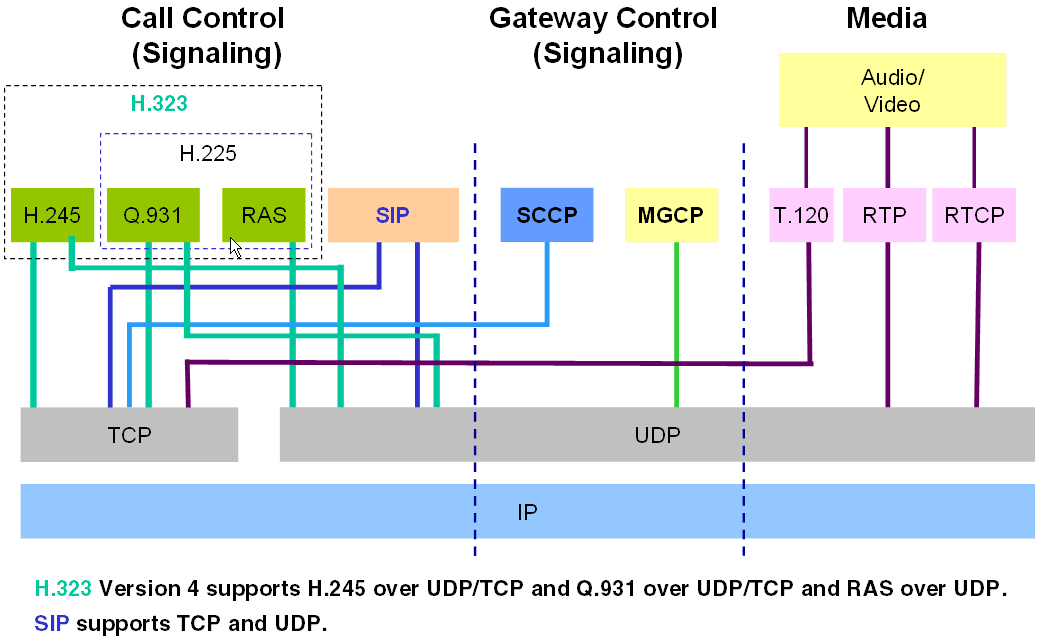
You can deploy VoIP over these protocols:
The Security Gateway secures VoIP traffic in SIP, MGCP, H.323, and SCCP environments.
VoIP calls use a series of complex protocols, each of which can transmit potentially malicious data through many ports.
The Security Gateway makes sure that:
In addition, the Security Gateway examines the contents of the packets passing through all allowed ports to make sure the packets contain the correct information.
Full stateful inspection on all protocols makes sure that: