
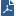

The following table summarizes the capabilities and differences between the two management models. The capacity figures shown for Multi-Domain Server represent estimated, practical limits that will sustain acceptable performance levels under normal conditions. Actual performance is dependent on many factors, including deployed hardware, network topology, traffic load and security requirements.
Feature |
Security Management Server |
Multi-Domain Server (Practical Limit) |
|---|---|---|
Management Domains |
1 |
250 |
Concurrent Administrators |
1 |
250 |
Object Databases |
1 |
250 |
Policies |
250 |
250 |
Certificate Authorities |
1 |
250 |
Virtual Systems |
25 (recommended) |
250 |
All communication between the Management Server and the VSX Gateway is accomplished by means of Secure Internal Communication (SIC), a certificate based channel that authenticates communication between Check Point components. The Management Server uses SIC for provisioning Virtual Devices, policy installation, logging, and status monitoring.
SIC trust is initially established using a one-time password during configuration of the VSX Gateway or VSX Cluster Members. For Multi-Domain Security Management deployments, SIC trust is established between the Domain Management Server associated with the VSX Gateway or VSX Cluster (Main Domain Management Server).
The Virtual Devices establish trust in a different manner than their physical counterparts. When creating a Virtual Device, VSX automatically establishes SIC trust using the secure communication channel defined between the Management Server and the VSX Gateway. The VSX Gateway uses its management interface for Secure Internal Communication between the Management Server and all Virtual Devices.