

In This Section: |
Hardware Security Module (HSM) is a device that is used to store cryptographic keys. HSM adds an extra layer of security to the network. HSM is designed to provide dedicated cryptographic functionality.
When Check Point Security Gateway uses an HSM, the HSM holds these objects for outbound HTTPS Inspection:
The administrator creates the CA certificate and key pair before configuring the Security Gateway to work with an HSM.
These keys are created during the initialization of the HTTPS Inspection daemon on the Security Gateway with 1024-bit, 2048-bit, or 4096-bit length.
You can use the Gemalto Luna SP SafeNet HSM to work with the Check Point Security Gateway. The SafeNet Cryptographic Engine enables the SafeNet Network HSM functionality by providing:
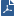
Item |
Description |
|---|---|
1 |
Internal computers that connect to HTTPS web sites through the Check Point Gateways & Servers. |
2 |
Check Point Security Gateway with HTTPS Inspection enabled. |
3 |
HTTPS web sites on the Internet. |
4 |
Check Point Security Management Server that manages the Check Point Security Gateway. |
5 |
Interconnecting Network. |
6 |
Gemalto HSM Appliance Server that stores and serves the SSL keys and certificates to the Check Point Security Gateway. |
7 |
Gemalto HSM Client workstation used for creating a CA certificate on the Gemalto HSM Appliance Server. |
Note - Check Point Security Gateway uses the Gemalto HSM Appliance Server only for outbound HTTPS Inspection.
Use this workflow to configure your Check Point Gateway to work with the HSM Appliance Server:
The Gemalto configuration documents have to be used to configure the Gemalto HSM environment.
Step |
Description |
|---|---|
1 |
Use a Windows-based computer. |
2 |
Download this package: Gemalto SafeNet HSM Help package Note - Software Subscription or Active Support plan is required to download this package. |
3 |
Extract the Gemalto HSM Help package to some folder. |
4 |
Open the extracted Gemalto HSM Help folder. |
5 |
Double-click The Gemalto SafeNet Network HSM 6.2.2 Product Documentation opens. |
Use the Gemalto Help documents to install and configure the HSM Appliance Server.
Procedure:
Step |
Description |
|---|---|
1 |
Install the HSM Appliance. From the Gemalto SafeNet Network HSM 6.2.2 Product Documentation, go to Installation Guide > SafeNet Network HSM Hardware Installation |
2 |
Do the initial configuration of the HSM Appliance and the HSM Appliance Server. From the Gemalto SafeNet Network HSM 6.2.2 Product Documentation, go to Configuration Guide > follow from [Step 1] to [Step 6] |
3 |
Run the From the Gemalto SafeNet Network HSM 6.2.2 Product Documentation, go to Configuration Guide > [Step 7] Create a trusted link and register Client and Appliance with each other |
4 |
Complete the configuration of your HSM Appliance Server to work with Check Point Security Gateway. Run these commands in LunaSH: |
4A |
Set the applicable partition to be active and auto-activated:
Note - If you do not set the partition to stay auto-activated, the partition does not stay activated when the machine is shut down for more than two hours. |
4B |
Disable the client source IP address validation by NTLS upon an NTLA client connection:
Note - This will allow HSM Appliance Server to accept traffic from Check Point Cluster members that is hidden behind Cluster VIP address, and from Check Point Security Gateways hidden behind NAT. |
You use the Gemalto HSM Client Workstation to create a CA Certificate on the Gemalto HSM Appliance Server.
Check Point Security Gateway uses this CA Certificate for HTTPS Inspection when storing and accessing SSL keys on the Gemalto HSM Appliance Server.
Workflow in this section:
Step |
Description |
|---|---|
1 |
Install a Windows-based or Linux-based computer to use as an HSM Client workstation. |
2 |
Download and install this software package on the HSM Client workstation computer: SafeNet HSM Client for Workstation Note - Software Subscription or Active Support plan is required to download this package. From Gemalto SafeNet Network HSM 6.2.2 Product Documentation, go to the Installation Guide > SafeNet HSM Client Software Installation |
3 |
Establish a Trust Link between the HSM Client workstation and the HSM Appliance Server. On the HSM Client workstation, run in LunaCM:
From the Gemalto SafeNet Network HSM 6.2.2 Product Documentation, go to Configuration Guide > [Step 7] Create a trusted link and register Client and Appliance with each other Note - The configuration will not work on Linux OS with glibc version lower than 2.7 (for example: Red Hat 5 or lower, Gaia R77.20 or lower). In such case, follow the instructions in Establishing a Trust Link between the Check Point Security Gateway and the Gemalto HSM Appliance Server. |
Step |
Description |
|---|---|
1 |
On the HSM Client workstation computer, open a command prompt or a terminal window. |
2 |
Use the Example:
|
3 |
When prompted, enter a password: Example:
|
4 |
Select the RSA mechanism by entering the corresponding number:
|
5 |
Run the Example:
handle=17 label=CAPrivateKeyPairLabel handle=18 label=CAPublicKeyPairLabel |
6 |
Use the handle numbers from the previous Step 5 to create the CA certificate. Example:
|
7 |
Run the Example:
handle=13 label=www.myhsm.cp handle=17 label=CAPrivateKeyPairLabel handle=18 label=CAPublicKeyPairLabel Note - You use the numbers of these three handles later on the Check Point Security Gateway in the |
Workflow in this section:
Note - If you have a Check Point Cluster environment, do this procedure on each cluster member.
Step |
Description |
|---|---|
1 |
Download this software package: Gemalto SafeNet HSM Simplified Client for Check Point Security Gateway Note - Software Subscription or Active Support plan is required to download this package. |
2 |
Copy the software package to the Check Point Security Gateway to some directory. |
3 |
Connect to the command line on the Check Point Security Gateway. |
4 |
Log in to the Expert mode. |
5 |
Go to the directory, where you put the software package:
|
6 |
Extract the packages:
|
7 |
Install these packages:
Important - After you install these RPM packages, you do not need to reboot the Security Gateway. |
Step |
Description |
|---|---|
1 |
On the Check Point Security Gateway: |
1A |
Connect to the command line. |
1B |
Log in to the Expert mode. |
1C |
Go to the SafeNet HSM Simplified Client installation directory:
|
1D |
Import the HSM Appliance Server certificate, server.pem, from the HSM Appliance to the Security Gateway (the period at the end is part of the syntax):
|
1E |
Register the HSM Appliance Server certificate, server.pem, with the Check Point Security Gateway:
|
1F |
Create a certificate and private key for the Check Point Security Gateway:
Notes:
|
1G |
Copy the Check Point Security Gateway certificate file that you created to the HSM Appliance (the colon at the end is part of the syntax):
|
2 |
On the HSM Appliance, in LunaSH: |
2A |
Register the Check Point Security Gateway certificate with the HSM Appliance Server:
|
2B |
Restart the Network Trust Link service:
|
2C |
Confirm the Check Point Security Gateway registration:
|
2D |
Assign the Check Point Security Gateway to the applicable partition:
|
2E |
Examine the partition access:
|
3 |
On the Check Point Security Gateway: Examine the partition access:
|
Notes:
For information about establishing a Trust Link, go to Appliance Administration Guide > Configuration without One-step NTLS > [Step 7] Create a Network Trust Link Between the Client and the Appliance.
Important:
See Creating Shared Policies > Configuring HTTPS Inspection.
$FWDIR/conf/hsm_configuration.C file on Check Point Security Gateway, you must fetch or install the policy on Security Gateway.To resolve this, make sure that the Gemalto HSM Appliance Server is up and running, there is physical connectivity between Check Point Security Gateway and Gemalto HSM Appliance, the Trust Link is established with the Gemalto HSM Appliance Server, and then fetch or install the policy on Security Gateway.
In addition, see Disabling Communication from the Check Point Gateway to the Gemalto HSM Appliance Server.
Procedure:
Note - If you have a Check Point Cluster environment, do this procedure on each cluster member.
Step |
Description |
|---|---|
1 |
Connect to the command line on the Security Gateway. |
2 |
Log in to the Expert mode. |
3 |
Edit the configuration file $FWDIR/conf/hsm_configuration.C:
|
4 |
Based on the output of the cmu list command from Step 4, add details of the CA certificate from the HSM Appliance Server to this configuration file. Example:
|
5 |
On the Security Gateway, fetch the local policy:
|
6 |
Confirm that HTTPS Inspection is activated successfully on outbound traffic. From an internal computer, connect to any HTTPS web site. On the internal computer, in the web browser, you should receive the signed CA certificate from the HSM Appliance Server. |
You can disable communication from the Check Point Gateway to an HSM Appliance. For example, when the HSM Appliance is under maintenance.
To disable communication from the Check Point Security Gateway to the HSM Appliance:
Step |
Description |
|---|---|
1 |
Connect to the command line on the Check Point Security Gateway. |
2 |
Log in to the Expert mode. |
3 |
Edit the configuration file $FWDIR/conf/hsm_configuration.C:
|
4 |
Set the value of the "
|
5 |
Save the changes in the file and exit the Vi editor. |
6 |
Fetch the local policy:
|
If you need to establish new Trust Link between a Check Point Security Gateway and an HSM Appliance Server, you have to delete the current Trust Link. For example, when you replace or reconfigure a Check Point Security Gateway, or an HSM Appliance Server.
Step |
Description |
|---|---|
1 |
Delete the current Trust Link on Check Point Security Gateway:
|
2 |
Delete the current Trust Link on the HSM Appliance:
|
Note - For more information, see Gemalto SafeNet Network HSM 6.2.2 Product Documentation.
Step |
Description |
|---|---|
1 |
Connect to the HSM Appliance over SSH. |
2 |
Examine all the configured interfaces:
|
3 |
Add a new interface:
|
4 |
Enable Network Trust Link Service (NTLS) on all the interfaces. |
Note - For more information, see Gemalto SafeNet Network HSM 6.2.2 Product Documentation > LunaSH Command Reference Guide > LunaSH Commands.
When HTTPS Inspection daemon wstlsd initializes on Check Point Gateway, it checks whether this Security Gateway is configured to with the Gemalto HSM Appliance Server.
cpstat https_inspection command on Security Gateway.Note - To see detailed information about wstlsd initialization, follow sk105559: How to debug WSTLSD daemon.
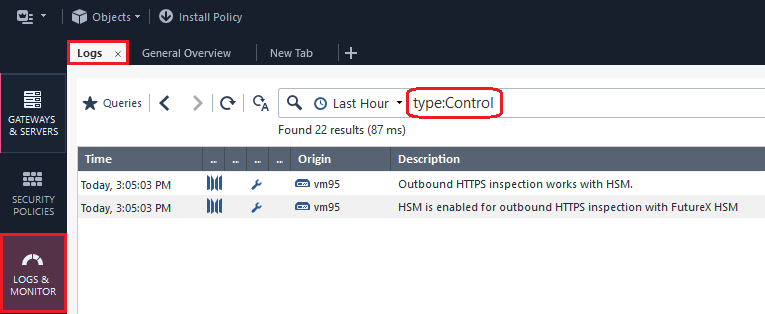
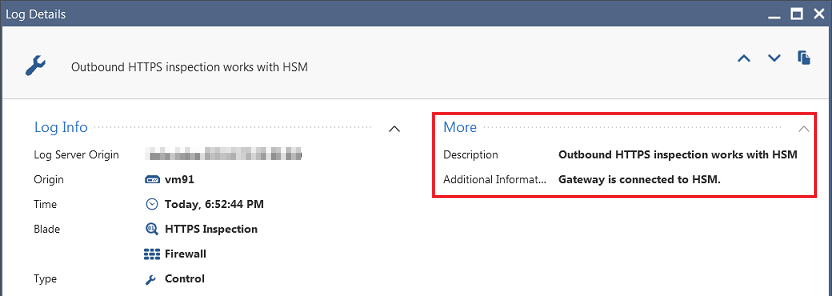
To see the HTTPS Inspection logs about the Gemalto HSM Appliance Server in SmartConsole:
Step |
Description |
|---|---|
1 |
Click Logs & Monitor > Logs tab. |
2 |
In the search field, enter:
|
3 |
Double-click on the log. |
4 |
In the log, refer to the More section. |
Possible logs are:
Log Description |
Log Additional Information |
Explanation |
|---|---|---|
|
|
The value of the |
|
|
One of these:
Important - In such cases, outbound HTTPS Inspection works without Gemalto HSM Appliance Server. |
|
|
All these conditions were met:
|
|
One of these strings:
|
See the Log Additional Information. |
Example:
You can query the HTTPS Inspection status and the status of connection to the Gemalto HSM Appliance Server on Security Gateway over SNMP:
OID .iso.org.dod.internet.private.enterprises.checkpoint.products.httpsInspection (.1.3.6.1.4.1.2620.1.54).
To get HTTPS Inspection status, query this SNMP object:
SNMP OID |
Returned strings |
Explanation |
|---|---|---|
.1.3.6.1.4.1.2620.1.54.1 |
|
HTTPS Inspection feature is configured on Security Gateway. |
|
|
HTTPS Inspection feature is not configured on Security Gateway. |
To get HTTPS Inspection status description, query this SNMP object:
SNMP OID |
Returned strings |
Explanation |
|---|---|---|
.1.3.6.1.4.1.2620.1.54.2 |
|
HTTPS Inspection feature is configured on Security Gateway. |
|
|
HTTPS Inspection feature is not configured on Security Gateway. |
To get HSM configuration status, query this SNMP object:
SNMP OID |
Returned strings |
Explanation |
|---|---|---|
.1.3.6.1.4.1.2620.1.54.3.1 |
|
The value of the |
|
|
One of these:
Important - In such cases, outbound HTTPS Inspection works without Gemalto HSM Appliance Server, and SSL keys are stored on Security Gateway. |
To get HSM configuration status description, query this SNMP object:
SNMP OID |
Returned strings |
Explanation |
|---|---|---|
.1.3.6.1.4.1.2620.1.54.3.2 |
|
The value of the |
|
|
One of these:
Important - In such cases, outbound HTTPS Inspection works without Gemalto HSM Appliance Server, and SSL keys are stored on Security Gateway. |
To get HSM partition access status, query this SNMP object:
SNMP OID |
Returned strings |
Explanation |
|---|---|---|
.1.3.6.1.4.1.2620.1.54.3.3 |
|
Security Gateway could not check access its partition on HSM Appliance Server. |
|
|
Security Gateway was able to access its partition on HSM Appliance Server. |
|
|
Security Gateway was not able to access its partition on HSM Appliance Server due to an error. |
To get HSM partition access status description, query this SNMP object:
SNMP OID |
Returned strings |
Explanation |
|---|---|---|
.1.3.6.1.4.1.2620.1.54.3.4 |
|
Security Gateway could not check access its partition on HSM Appliance Server. |
|
|
Security Gateway was able to access its partition on HSM Appliance Server. |
|
Possible errors are:
|
Security Gateway was not able to access its partition on HSM Appliance Server due to an error. |
To get Outbound HTTPS Inspection status, query this SNMP object:
SNMP OID |
Returned strings |
Explanation |
|---|---|---|
.1.3.6.1.4.1.2620.1.54.3.5 |
|
All these conditions were met: 1. The value of the 2. Security Gateway was able to connect to the HSM Appliance Server. |
|
|
One of these: The value of the Gemalto HSM Simplified Client software packages are not installed on Security Gateway. The The Important - In such cases, outbound HTTPS Inspection works without Gemalto HSM Appliance Server, and SSL keys are stored on Security Gateway. |
|
|
All these conditions were met: 1. The value of the 2. An error occurred. Important - In such case, outbound HTTPS Inspection will not work, and HTTPS traffic will not pass. |
Note - The conditions for the returned strings are calculated on Security Gateway during the start of the HTTPS Inspection daemon wstlsd, or during policy installation. For example, you can get "hsmStatus.hsmEnabled = HSM enabled" and "hsmStatus.outboundStatus = HSM off", because when the wstlsd daemon started, or during last policy installation, the HSM configuration was disabled.
To get Outbound HTTPS Inspection status description, query this SNMP object:
SNMP OID |
Returned strings |
Explanation |
|---|---|---|
.1.3.6.1.4.1.2620.1.54.3.6 |
|
All these conditions were met: 1. The value of the 2. Security Gateway was able to connect to the HSM Appliance Server. |
|
|
The value of the |
|
Possible errors are:
|
All these conditions were met: 1. The value of the 2. An error occurred. Important - In such case, outbound HTTPS Inspection will not work, and HTTPS traffic will not pass. |
Note - The conditions for the returned strings are calculated on Security Gateway during the start of the HTTPS Inspection daemon wstlsd, or during policy installation. For example, you can get "hsmStatus.hsmEnabledDescription = HSM is enabled for HTTPS inspection" and "hsmStatus.outboundStatusDescription = Outbound HTTPS inspection works without HSM", because when the wstlsd daemon started, or during last policy installation, the HSM configuration was disabled.
Examples:
# snmpwalk -m $CPDIR/lib/snmp/chkpnt.mib -On -v 2c -c public localhost 1.3.6.1.4.1.2620.1.54
.1.3.6.1.4.1.2620.1.54.1.0 = STRING: On .1.3.6.1.4.1.2620.1.54.2.0 = STRING: HTTPS Inspection is on .1.3.6.1.4.1.2620.1.54.3.1.0 = STRING: Enabled .1.3.6.1.4.1.2620.1.54.3.2.0 = STRING: HSM is enabled for HTTPS inspection .1.3.6.1.4.1.2620.1.54.3.3.0 = STRING: Accessible .1.3.6.1.4.1.2620.1.54.3.4.0 = STRING: Gateway can access HSM partition for HTTPS inspection .1.3.6.1.4.1.2620.1.54.3.5.0 = STRING: HSM on .1.3.6.1.4.1.2620.1.54.3.6.0 = STRING: Outbound HTTPS inspection works with HSM
# snmpwalk -m $CPDIR/lib/snmp/chkpnt.mib -Oa -v 2c -c public localhost 1.3.6.1.4.1.2620.1.54
CHECKPOINT-MIB::httpsInspectionStatus.0 = STRING: On CHECKPOINT-MIB::httpsInspectionStatusDescription.0 = STRING: HTTPS Inspection is on CHECKPOINT-MIB::hsmEnabled.0 = STRING: Enabled CHECKPOINT-MIB::hsmEnabledDescription.0 = STRING: HSM is enabled for HTTPS inspection CHECKPOINT-MIB::hsmPartitionAccess.0 = STRING: Accessible CHECKPOINT-MIB::hsmPartitionAccessDescription.0 = STRING: Gateway can access HSM partition for HTTPS inspection CHECKPOINT-MIB::outboundStatus.0 = STRING: HSM on CHECKPOINT-MIB::outboundStatusDescription.0 = STRING: Outbound HTTPS inspection works with HSM |
For more information about SNMP on Gaia OS, see sk90860: How to configure SNMP on Gaia OS.
You can see the HTTPS Inspection status and the status of connection to the HSM Appliance Server using the cpstat https_inspection command on the Security Gateway.
Syntax:
|
|
Example outputs:
[Expert@GW:0]# cpstat https_inspection -f default
HTTPS inspection status (On/Off): On HTTPS inspection status description: HTTPS Inspection is on
[Expert@GW:0]#
[Expert@GW:0]# cpstat https_inspection -f hsm_status
HSM enabled (Enabled/Disabled): Enabled HSM enabled description: HSM is enabled for HTTPS inspection HSM partition access (Accessible/Not Accessible): Accessible HSM partition access description: Gateway can access to HSM partition for HTTPS inspection Outbound status (HSM on/HSM off/HSM error): HSM on Outbound status description: Outbound HTTPS inspection works with HSM
[Expert@GW:0]#
[Expert@GW:0]# cpstat https_inspection -f all
HTTPS inspection status (On/Off): On HTTPS inspection status description: HTTPS Inspection is on HSM enabled (Enabled/Disabled): Enabled HSM enabled description: HSM is enabled for HTTPS inspection HSM partition access (Accessible/Not Accessible): Accessible HSM partition access description: Gateway can access to HSM partition for HTTPS inspection Outbound status (HSM on/HSM off/HSM error): HSM on Outbound status description: Outbound HTTPS inspection works with HSM
[Expert@GW:0]# |
Explanation about HTTPS Inspection status:
Item |
Possible returned strings |
Explanation |
|---|---|---|
|
|
HTTPS Inspection feature is configured on the Security Gateway. |
|
|
HTTPS Inspection feature is not configured on the Security Gateway. |
Explanation about HTTPS Inspection status description:
Item |
Possible returned strings |
Explanation |
|---|---|---|
|
|
HTTPS Inspection feature is configured on the Security Gateway. |
|
|
HTTPS Inspection feature is not configured on the Security Gateway. |
Explanation about HSM configuration status:
Item |
Possible returned strings |
Explanation |
|---|---|---|
|
|
The value of the |
|
|
One of these:
Important - In such cases, outbound HTTPS Inspection works without the HSM Appliance Server, and SSL keys are stored on the Security Gateway. |
Explanation about HSM configuration status description:
Item |
Possible returned strings |
Explanation |
|---|---|---|
|
|
The value of the |
|
|
One of these:
Important - In such cases, outbound HTTPS Inspection works without the HSM Appliance Server, and SSL keys are stored on the Security Gateway. |
Explanation about HSM partition access status:
Item |
Possible returned strings |
Explanation |
|---|---|---|
|
|
The Security Gateway could not check access its partition on the HSM Appliance Server. |
|
|
The Security Gateway was able to access its partition on the HSM Appliance Server. |
|
|
The Security Gateway was not able to access its partition on the HSM Appliance Server due to an error. Important - In such case, outbound HTTPS Inspection will not work, and HTTPS traffic will not pass. |
Explanation about HSM partition access status description:
Item |
Possible returned strings |
Explanation |
|---|---|---|
|
|
The Security Gateway could not check access its partition on the HSM Appliance Server. |
|
|
The Security Gateway was able to access its partition on the HSM Appliance Server. |
|
Possible errors are:
|
The Security Gateway was not able to access its partition on the HSM Appliance Server due to an error. All these conditions were met: 1. The value of the 2. An error occurred. Important - In such case, outbound HTTPS Inspection will not work, and HTTPS traffic will not pass. |
Explanation about Outbound HTTPS Inspection status:
Item |
Possible returned strings |
Explanation |
|---|---|---|
|
|
All these conditions were met: 1. The value of the 2. The Security Gateway was able to connect to the HSM Appliance Server. |
|
|
One of these:
Important - In such cases, outbound HTTPS Inspection works without the HSM Appliance Server, and SSL keys are stored on the Security Gateway. |
|
|
All these conditions were met: 1. The value of the 2. An error occurred. Important - In such case, outbound HTTPS Inspection will not work, and HTTPS traffic will not pass. |
Note - The conditions for the returned strings are calculated on the Security Gateway during the start of the HTTPS Inspection daemon wstlsd, or during policy installation. For example, you can get "HSM enabled (Enabled/Disabled) = Enabled" and "Outbound status (HSM on/HSM off/HSM error) = HSM off", because when the wstlsd daemon started, or during last policy installation, the HSM configuration was disabled.
Explanation about Outbound HTTPS Inspection status description:
Item |
Possible returned strings |
Explanation |
|---|---|---|
|
|
All these conditions were met: 1. The value of the 2. The Security Gateway was able to connect to the HSM Appliance Server. |
|
|
The value of the |
|
Possible errors are:
|
All these conditions were met: 1. The value of the 2. An error occurred. Important - In such case, outbound HTTPS Inspection will not work, and HTTPS traffic will not pass. |
Note - The conditions for the returned strings are calculated on the Security Gateway during the start of the HTTPS Inspection daemon wstlsd, or during policy installation. For example, you can get "HSM enabled (Enabled/Disabled) = Enabled" and "Outbound status description = Outbound HTTPS inspection works without the HSM", because when the wstlsd daemon started, or during last policy installation, the HSM configuration was disabled.