

In This Section: |
To manage the Security Policies for Endpoint Security, use the Policy tab of the SmartEndpoint console.
![]()
The Policy tab contains the Policy Management Toolbar and the Policy Rule Base.
The Policy Rule Base contains a policy for each of the Endpoint Security components (formerly known as a Blades). These policies enforce protections on endpoint computers.
The policy for each component is made up of rules. This shows some example of rules in the Policy tab:
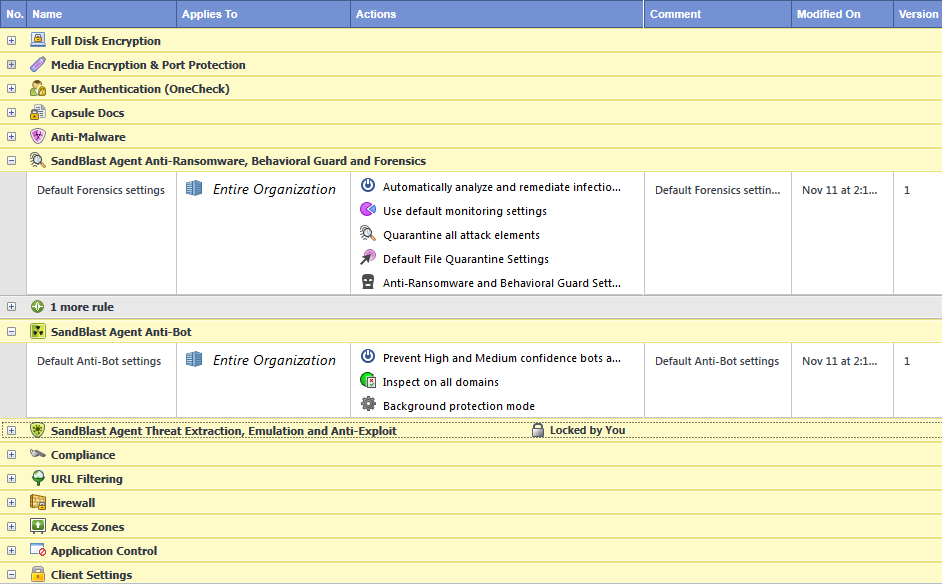
Each rule applies to a specific component, and to a specific part of the organization. Each rule has a set of actions.
The policy for each component has a default rule that applies to the entire organization.
You can change the default rules, and add rules that apply to specific parts of the organization. You cannot delete the default rule.
These are the columns in a policy rule:
Column |
Description |
|---|---|
|
Rule Number |
|
Rule Name |
|
The part of the organization (the entity) to which the rule applies |
|
The configurations that apply to the Endpoint Security component |
|
Informational fields. Right-click a column to select the fields to show. You can also show:
|
The Policy tab contains the Policy Toolbar and the Policy Rule Base.
This is the Policy Toolbar:
![]()
To do this |
Click this |
|---|---|
Add and delete rules |
|
Save, refresh and install policy changes |
|
Show only the actions that are different than the default rule for that component |
|
Change the order of the rules for the component. Re-order the rules to define the assignment priority of rules for a specific component |
|
Search for text and highlight it in the Endpoint Security policy |
|
Show the policy for a specific part of the organization |
|
One user may have multiple computers. Some computers may have multiple users.
One user with multiple computers: |
|
One computer with multiple users: |
|---|---|---|
|
|
|
The policies for some Endpoint Security components are enforced for each user. Other policies are enforced for each computer.
Endpoint Security can enforce policy rules on computers and users based on their connection and compliance state.
When you create a policy rule, you select the connection and compliance states for which the rule is enforced. You can define rules with these states:
The table shows if the policy for each Endpoint Security component is enforced for each user or for each computer (the Rule Type).
The table also shows that you can define a Connected policy for all components. For some components you can also define Disconnected and Restricted policies.
Note - Deployment Rules are defined for computers, not for users.
|
Component |
Rule Type |
Connected |
Disconnected |
Restricted |
|---|---|---|---|---|---|
|
Full Disk Encryption |
Computer |
|
|
|
|
Media Encryption & Port Protection |
User |
|
|
|
|
OneCheck User Settings |
User |
|
|
|
|
Capsule Docs |
User |
|
|
|
|
Anti-Malware |
User |
|
|
|
|
SandBlast Agent Anti-Ransomware, Behavioral Guard and Forensics |
Computer |
|
|
|
|
SandBlast Agent Anti-Bot |
User |
|
|
|
|
SandBlast Agent Threat Extraction, Emulation and Anti-Exploit |
User |
|
|
|
|
Compliance |
User |
|
|
|
|
URL Filtering |
Computer |
|
|
|
|
Firewall |
User |
|
|
|
|
Access Zones |
User |
|
|
|
|
Application Control |
User |
|
|
|
|
Client Settings |
User |
|
|
|
When you configure a rule, you specify the entities that the rule Applies To.
These are some of the entities you can specify:
These components can be installed on supported servers in the same way that they are installed on workstations:
|
Important - Application Control is not supported on all versions of Windows Server. Do not deploy this component on clients that run operating systems that are not supported. You can also disable it in the policy. To disable components on operating systems that are not supported:
|
If you install Anti-Malware and Firewall policies on servers, it is best for the policies to be machine-based and not user-based. In machine-based policy, the policies assigned to the machine have priority over the policies assigned to users who connect to the machine.
To enforce machine-based policies, we strongly recommend that you put all servers in a server virtual group.
For supported servers, see the Release Notes for your Endpoint Security client version.