
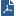

DLP rules have different action settings.
Action |
Description |
|---|---|
Detect |
The data transmission event is logged in the Logs & Monitor view. Administrators with permission can view the data that was sent. The traffic is passed. |
Inform User |
The transmission is passed, but the incident is logged and the user is notified. |
Ask User |
The transmission is held until the user verifies that it should be sent. A notification, usually with a remediation link to the Self Incident Handling portal, is sent to the user. The user decides whether the transmission should be completed or not. The decision is logged and can be viewed under the User Response category in a log entry. Administrators with full permissions or the View, Release, or Discard DLP messages permission can send or discard the message. |
Prevent |
The data transmission is blocked. |
Watermark |
Tracks outgoing Microsoft Office documents (Word, Excel, or PowerPoint files from Office 2007 and higher) by adding visible watermarks or invisible encrypted text. |
When you set Data Owners to be notified, a mail server becomes a required component of the DLP system.
The DLP gateway sends mail notifications to users and Data Owners, therefore it is necessary for the gateway to access the mail server as a client.
Important -
You can use the Data Loss Prevention Wizard to configure the settings for the mail relay. Use these procedures to configure these settings without the Wizard.
To open the DLP tab in SmartDashboard:
SmartConsole opens and shows the DLP tab.
To configure the mail relay for anonymous SMTP connections:
If the mail server object does not exist, create it.
To configure the mail server object for authenticated SMTP connections:
The Mail Server window opens.
To complete configuring the Mail Relay:
Configure the mail relay to accept anonymous connections from the DLP gateway. For details, consult the vendor documentation. For example, on Microsoft Exchange Servers, configure the permissions of the default receive connector (or other relevant connector that handles SMTP traffic) for anonymous users.
To configure the DLP and mail relay in the DMZ:
SmartConsole opens and shows the DLP tab.
The Networks and Hosts window opens.
Otherwise, click New > Host.
Item |
Description |
|---|---|
1 |
Internal mail server |
2 |
DLP gateway |
3 |
Mail relay in the DMZ |
Make sure that the DLP gateway does NOT scan emails as they pass from the mail relay to the target mail server in the Internet.
To deploy the internal mail relay behind a DMZ interface of the DLP gateway:
The gateway window opens and shows the General Properties page.
In the Topology page of the DLP gateway object, define the gateway interface that leads to the Mail relay as Internal and also as Interface leads to DMZ.
To configure the internal mail relay that is not behind a DMZ interface of the DLP gateway:
Note - If the DLP gateway interface leading to the internal mail relay is internal, and you cannot deploy the internal mail relay behind a DMZ interface of the DLP gateway.
SmartDashboard opens and shows the DLP tab.
A non-recommended deployment is to have the DLP gateway scan emails as they are sent from an internal mail relay that is in My Organization to the target mail server in the Internet. In this deployment, the DLP gateway communicates with the target mail servers on behalf of the mail relay. If the target mail server does not respond, some mail relays (such Mcafee IronMail, postfix 2.0 or earlier and qmail) will not try the next DNS MX record, and so will not try to resend the email to another SMTP mail server in the same domain.
Item |
Description |
|---|---|
1 |
Internal mail server |
2 |
Internal mail relay |
3 |
DLP gateway |
Why Some Mail Relays Will Not Resend Emails
If the mail relay does not succeed in sending an email because the target mail server does not respond, the mail relay resends the email to another SMTP server in the same domain. The relay does this by sending the mail to the next DNS MX record.
Most mail relays try the next MX record if the target is unreachable, or if the target server returns a 4xx SMTP error. However, other mail relays (such as Mcafee IronMail, postfix 2.0 or earlier and qmail) do not try the next MX if the target server returns a 4xx error. They will therefore not send the email.
In these deployments, the DLP gateway communicates with mail servers in the internet on behalf of the mail relay. If the target mail server does not respond, the DLP gateway sends a 4xx response to the mail relay in behalf of the mail server. Therefore, if your mail relay does not try the next MX when the target server returns a 4xx error, the email will not be sent.
Workarounds for the Non-Recommended Deployments
If Outlook does not trust the mail relay server, it fails to correctly render the Send and Discard buttons in the violation notification email. The buttons render correctly only after the mail relay is trusted and a new email sent.
To avoid this issue, instruct users to add the mail relay address to Outlook's safe senders list.
TLS-encrypted SMTP connections are not scanned by the DLP Software Blade. If an Exchange Server uses TLS to encrypt emails, you can use the Exchange Security Agent to inspect them.