sam_alert
Description
For SAM v1, this utility executes Suspicious Activity Monitoring (SAM) actions according to the information received from the standard input.
For SAM v2, this utility executes Suspicious Activity Monitoring (SAM) actions with User Defined Alerts mechanism.
Notes:
- VSX Gateway does not support Suspicious Activity Monitoring (SAM) Rules. See sk79700.
- You must run this command from the Expert mode.
- See
fw sam and fw sam_policy.
Syntax for SAM v1
[Expert@MGMT:0]# sam_alert [-v] [-o] [-s <SAM Server>] [-t <Time>] [-f <Security Gateway>] [-C] {-n|-i|-I} {-src|-dst|-any|-srv}
|
Parameters for SAM v1
Parameter
|
Description
|
-v
|
Enables the verbose mode for the fw sam
|
-o
|
Specifies to print the input of this tool to the standard output (to use with pipes in a CLI syntax).
|
-s <>
|
Specifies the SAM Server to be contacted. Default is localhost.
|
-t <>
|
Specifies the time (in seconds), during which to enforce the action. The default is forever.
|
-f <>
|
Specifies the Security Gateway, on which to run the operation.
Important - If you do not specify the target Security Gateway explicitly, this command applies to all managed Security Gateways.
|
-C
|
Cancels the specified operation.
|
-n
|
Specifies to notify every time a connection, which matches the specified criteria, passes through the Security Gateway.
|
-i
|
Inhibits (drops or rejects) connections that match the specified criteria.
|
-I
|
Inhibits (drops or rejects) connections that match the specified criteria and closes all existing connections that match the specified criteria.
|
-src
|
Matches the source address of connections.
|
-dst
|
Matches the destination address of connections.
|
-any
|
Matches either the source or destination address of connections.
|
-srv
|
Matches specific source, destination, protocol and port.
|
Syntax for SAM v2
[Expert@MGMT:0]# sam_alert -v2 [-v] [-O] [-S <>
|
Parameters for SAM v2
Parameter
|
Description
|
-v2
|
Specifies to use SAM v2.
|
-v
|
Enables the verbose mode for the fw sam
|
-O
|
Specifies to print the input of this tool to the standard output (to use with pipes in a CLI syntax).
|
-S <>
|
the SAM server to be contacted. Default is localhost
|
-t <>
|
Specifies the time (in seconds), during which to enforce the action. The default is forever.
|
-f <>
|
Specifies the Security Gateway, on which to run the operation.
Important - If you do not specify the target Security Gateway explicitly, this command applies to all managed Security Gateways.
|
-n <>
|
Specifies the name for the SAM rule.
Default is empty.
|
-c "<>"
|
Specifies the comment for the SAM rule.
Default is empty.
You must enclose the text in the double quotes or single quotes.
|
-o <>
|
Specifies the originator for the SAM rule.
Default is sam_alert
|
-l {r | a}
|
Specifies the log type for connections that match the specified criteria:
Default is None
|
-a {d | r| n | b | q | i}
|
Specifies the action to apply on connections that match the specified criteria:
drnbqi
|
-C
|
Specifies to close all existing connections that match the criteria.
|
-ip
|
Specifies to use IP addresses as criteria parameters.
|
-eth
|
Specifies to use MAC addresses as criteria parameters.
|
-src
|
Matches the source address of connections.
|
-dst
|
Matches the destination address of connections.
|
-any
|
Matches either the source or destination address of connections.
|
-srv
|
Matches specific source, destination, protocol and port.
|
Example
See sk110873: How to configure Security Gateway to detect and prevent port scan.
Monitoring Suspicious Activity Rules
Suspicious Activity Monitoring (SAM) is a utility integrated in SmartView Monitor. It blocks activities that you see in the SmartView Monitor results and that appear to be suspicious. For example, you can block a user who tries several times to gain unauthorized access to a network or Internet resource.
A Security Gateway with SAM enabled has Firewall rules to block suspicious connections that are not restricted by the security policy. These rules are applied immediately (not required).
The Need for Suspicious Activity Rules
Connections between enterprise and public networks are a security challenge as they leave the network and its applications open to attack. You must be able to inspect and identify all inbound and outbound network activity and decide if it is suspicious.
Creating a Suspicious Activity Rule
SAM rules use CPU resources. Therefore, set an expiration time so you can inspect traffic but not negatively affect performance.
If you confirm that an activity is risky, edit the Security Policy, educate users, or handle the risk.
You can block suspicious activity based on source, destination, or service.
To block an activity:
- In the SmartView Monitor, click .
The window opens.
- Click.
The window opens.
- In and in , select or :
- To block all sources or destinations that match the other parameters, enter
Any - To block one suspicious source or destination, enter an IP and .
- In :
- To block all connections that fit the other parameters, enter
Any - To block one suspicious service or protocol, click the button and select a service from the window that opens.
- In ,set a time limit.
- Click .
To create an activity rule based on TCP or UDP use:
- In the window , click
The window opens.
- Click .
- Select or .
- Enter the port number.
- Click .
To define SmartView Monitor actions on rule match:
- In the window, click .
The window opens.
- In , select the Firewall action for SmartView Monitor to do on rule match:
- - Send a message about the activity, but do not block it.
- - Drop packets, but do not send a response. The connection will time out.
- - Send an RST packet to the source and close the connection.
- In Track, select , or .
- If the action is : To close the connection immediately on rule match, select .
- Click .
Creating a Suspicious Activity Rule from Results
If you monitor traffic, and see a suspicious result, you can create an SAM rule immediately from the results.
Note - You can only create a Suspicious Activity rule for Traffic views with data about the Source or Destination (Top Sources, Top P2P Users, and so on).
To create an SAM rule:
- In SmartView Monitor open a Traffic view.
The window opens.
- Select an object and click .
- In the Results, right-click the bar in the chart (or the row in the report), that represents the source, destination, or other traffic property to block.
- Select .
The window opens.
- Create the rule.
- Click .
For example:
Your corporate policy does not allow to share peer2peer file, and you see it in the > results.
- Right-click the result bar and select .
The SAM rule is set up automatically with the user IP address and the service.
- Click .
- For the next hour, while this traffic is dropped and logged, contact the user.
Managing Suspicious Activity Rules
The window shows the currently enforced rules. If you add a rule that conflicts with another rule, the conflicting rule remains hidden. For example, if you define a rule to drop http traffic, and a rule exists to reject http traffic, only the drop rule shows.
How SmartView Monitor Works
Data for the status of all gateways in the system is collected by the Security Management Server and viewed in SmartView Monitor. The data shows status for:
- Check Point Security Gateways
- OPSEC gateways
- Check Point Software Blades
Gateway Status is the SmartView Monitor view which shows all component status information. A Gateway Status view shows a snapshot of all Software Blades, such as VPN and ClusterXL, and third party products (for example, OPSEC-partner gateways).
Gateway Status is similar in operation to the SNMP daemon that provides a mechanism to get data about gateways in the system.
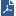
SIC is initialized between Security Gateways (3) (local and remote), and the Security Management Server (2). The Security Management Server then gets status data from the Software Blades with the AMON (Application Monitoring)protocol. SmartView Monitor (1) gets the data from the Security Management Server.
AMON
The Security Management Server acts as an AMON client. It collects data about installed Software Blades. Each Security Gateway, or any other OPSEC gateway which runs an AMON server, acts as the AMON server itself. The gateway requests status updates from other components, such as the Firewall kernel and network servers. Requests are fetched at a defined interval.
An alternate source for status collection can be any AMON client, such as an OPSEC partner, which uses the AMON protocol.
The AMON protocol is SIC- based. It can collect data only after SIC is initialized.
Defining Status Fetch Frequency
The Security Management Server collects status data from the Security Gateways on a defined interval. The default is 60 seconds.
To set the Status Fetching Interval:
- Open SmartConsole.
- Open > > .
- Enter the number of seconds in .
Configuring SmartView Monitor
System Alerts and Thresholds
You can set thresholds for selected gateways. When a threshold is passed, a system alert is sent.
To set System Alert thresholds:
- Open view.
- Right-click a network object and select .
The window opens.
- Set the thresholds for the selected object:
- - All objects get the same thresholds for system alerts.
- - The selected gateway object does not have thresholds for system alerts.
- - Change the thresholds for the selected object to be different than the global settings.
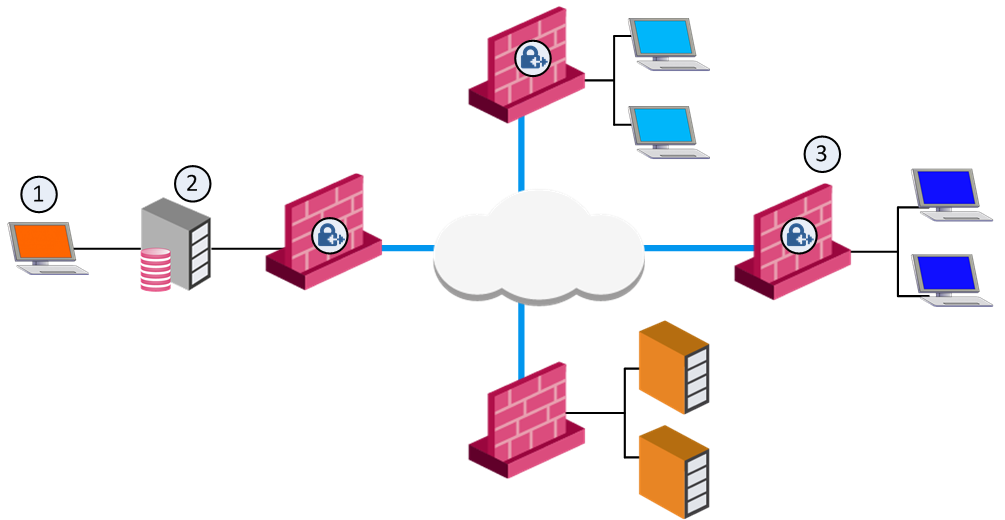
To change Global Threshold settings:
- In the window, click .
The window opens.
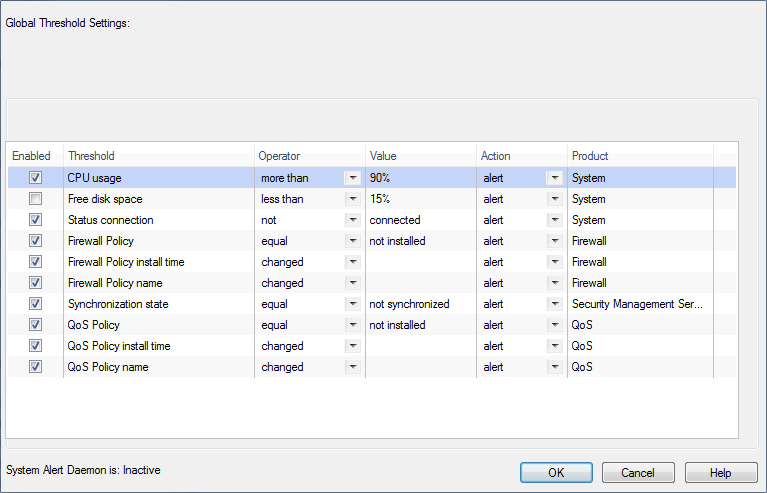
- Select thresholds.
- In , select:
- - No alert.
- - Sends a log entry to the database.
- - Opens a pop-up window to your desktop.
- - Sends a mail alert to your Inbox.
- - Sends an SNMP alert.
- - Runs a script. Make sure a user-defined action is available. Go to > > > .
To change custom threshold settings:
- In the window, select .
The global threshold settings show.
- Select thresholds to enable for this gateway or cluster member.
- Set defining values.
Working with SNMP Monitoring Thresholds
You can configure a variety of different SNMP thresholds that generate SNMP traps, or alerts. You can use these thresholds to monitor many system components automatically without requesting information from each object or device. The categories of thresholds that you can configure include:
- Hardware
- High Availability
- Networking
- Resources
- Log Server Connectivity
Some categories apply only to some machines or deployments.
Note - SNMP monitoring thresholds are supported from R75.20, R71.30, and higher.
In each category there are many individual thresholds that you can set. For example, the hardware category includes alerts for the state of the RAID disk, the state of the temperature sensor, the state of the fan speed sensor, and others. For each individual threshold, you can configure:
- If it is enabled or disabled
- How frequently alerts are sent
- The severity of the alert
- The threshold point (if necessary)
- Where the alerts are sent to
You can also configure some settings globally, such as how often alerts are send and where they are sent to.
Types of Alerts
- Active alerts are sent when a threshold point is passed or the status of a monitored component is problematic.
- Clear alerts are sent when the problem is resolved and the component has returned to its normal value. Clear alerts look like active alerts but the severity is set to 0.
Configuring SNMP Monitoring
Configure the SNMP monitoring thresholds in the command line of the Security Management Server. When you install the policy on the gateways the SNMP monitoring thresholds are applied globally to all gateways.
Configuring in Multi-Domain Security Management
In a Multi-Domain Security Management environment, you can configure thresholds on the Multi-Domain Server and on each individual Domain Management Server. Thresholds that you configure on the Multi-Domain Server are for the Multi-Domain Server only. Thresholds that you configure for a Domain Management Server are for that Domain Management Server and its gateways. If a threshold applies to the Multi-Domain Server and the Domain Management Server gateways, set it on the Multi-Domain Server and Domain Management Server. But in this situation you can only get alerts from the Multi-Domain Server if the threshold passed.
For example, because the Multi-Domain Server and Domain Management Server are on the same machine, if the CPU threshold is passed, it applies to both of them. But only the Multi-Domain Server generates alerts.
You can see the for each threshold with the threshold_config
- If the Multi-Domain Security Management level for a threshold is : Alerts are generated for the Multi-Domain Server when the threshold point is passed.
- If the Multi-Domain Security Management level for a threshold is and : Alerts are generated for the Multi-Domain Server and Domain Management Servers separately when the threshold point is passed.
Configuring a Local Gateway Policy
You can configure SNMP thresholds locally on a gateway with the same procedure that you do on a Security Management Server. But each time you install a policy on the gateway, the local settings are erased and it reverts to the global SNMP threshold settings.
You can use the threshold_config
On SecurePlatform and Linux, the configuration file that you can back up is: $FWDIR/conf/thresholds.conf
On Windows, the configuration file that you can back up is: %FWDIR%\conf\thresholds.conf
Configuration Procedures
There is one primary command to configure the thresholds in the command line, threshold_configthreshold_config,
When you run threshold_config
- - Shows you the name configured for the threshold policy.
- - Lets you set a name for the threshold policy.
- - Lets you save the policy.
- - Lets you export the policy to a file.
- - Lets you import a threshold policy from a file.
- - Lets you configure global settings for how frequently alerts are sent and how many alerts are sent.
- - Lets you configure a location or locations where the SNMP alerts are sent.
- - Shows a list of all thresholds that you can set including: the category of the threshold, if it is active or disabled, the threshold point (if relevant), and a short description of what it monitors.
- - Opens the list of threshold categories to let you select thresholds to configure.
Configure Global Alert Settings
If you select , you can configure global settings for how frequently alerts are sent and how many alerts are sent. You can configure these settings for each threshold. If a threshold does not have its own alert settings, it uses the global settings by default.
You can configure these options:
- - How many alerts are sent when an active alert is triggered. If you enter 0, alerts are sent until the problem is fixed.
- - How long the system waits between it sends active alerts.
- - How many clear alerts are sent after a threshold returns to a regular value.
- - How long the system waits between it sends clear alerts.
Configure Alert Destinations
If you select Configure Alert Destinations, you can add and remove destinations for where the alerts are sent. You can see a list of the configured destinations. A destination is usually an NMS (Network Management System) or a Check Point Log Server.
After you enter the details for a destination, the CLI asks if the destination applies to all thresholds.
- If you enter , alerts for all thresholds are sent to that destination, unless you remove the destination from an individual threshold.
- If you enter , no alerts are sent to that destination by default. But for each individual threshold, you can configure the destinations and you can add destinations that were not applied to all thresholds.
For each threshold, you can choose to which of the alert destinations its alerts are sent. If you do not define alert destination settings for a threshold, it sends alerts to all of the destinations that you applied to all thresholds.
For each alert destination enter:
- - An identifying name.
- - The IP address of the destination.
- - Through which port it is accessed
- - The version on SNMP that it uses
- - Some versions of SNMP require more data. Enter the data that is supplied for that SNMP version.
Configure Thresholds
If you select Configure thresholds, you see a list of the categories of thresholds, including:
- Hardware
- High Availability
- Networking
- Resources
- Log Server Connectivity
Some categories apply only to some machines or deployments. For example, Hardware applies only to Check Point appliances and High Availability applies only to clusters or High Availability deployments.
Select a category to see the thresholds in it. Each threshold can have these options:
- - If the threshold is enabled, the system sends alerts when there is a problem. If it is disabled it does not generate alerts.
- - You can give each threshold a severity setting. The options are: Low, Medium, High, and Critical. The severity level shows in the alerts and in SmartView Monitor. It lets you know quickly how important the alert is.
- - Set how frequently and how many alerts will be sent when the threshold is passed. If you do not configure this, it uses the global alert settings.
- - Enter the value that will cause active alerts when it is passed. Enter the number only, without a unit of measurement.
- - See all of the configured alert destinations. By default, active alerts and clear alerts are sent to the destinations. You can change this for each destination. When you select the destination you see these options:
- - If you select this, alerts for this threshold are not sent to the selected destination.
- - If you configured a destination in the global alert destinations but did not apply it to all thresholds, you can add it to the threshold.
- - Cleared alerts for this threshold are not sent to the selected destination. Active alerts are sent.
Completing the Configuration
You can complete threshold configuration and activate the settings.
To complete configuration and activate the settings:
- On the Security Management Server, install the policy on all Security Gateways.
- For a local Security Gateway threshold policy or a Multi-Domain Security Management Multi-Domain Server environment, use the
cpwd_admin- Run:
cpwd_admin stop -name CPD -path "$CPDIR/bin/cpd_admin" -command "cpd_admin stop" - Run:
cpwd_admin start -name CPD -path "$CPDIR/bin/cpd" -command "cpd"
Monitoring SNMP Thresholds
You can see an overview of the SNMP thresholds that you configure in SmartView Monitor.
To see an overview of the SNMP thresholds:
- Open SmartView Monitor and select a Security Gateway.
- In the summary of the Security Gateway data that open in the bottom pane, click .
- In the new pane that opens, click .
In the pane that opens, you can see these details:
- - A summary of the total SNMP Threshold policy.
- - The name that you set for the policy in the CLI.
- - If the policy is enabled or disabled.
- - How many thresholds are enabled.
- - How many thresholds are currently sending alerts.
- - How many not active thresholds became active since the policy was installed.
- - Details for the thresholds that are currently sending alerts.
- - The name of the alert (given in the CLI).
- - The category of the alert (given in the CLI), for example, Hardware or Resources.
- - The name of the object as recorded in the MIB file.
- - The value of the object when the threshold became active, as recorded in the MIB file.
- - The status of the object: active or clearing (passed the threshold but returns to usual value).
- - The severity of that threshold, as you configured for it in the CLI.
- - When was the alert first sent.
- - A list of the destinations that alerts are sent to.
- - The name of the location.
- - The type of location. For example, a Log Server or NMS.
- - If logs are sent from the gateway or Security Management Server to the destination machine.
- - How many alerts were sent to the destination from when the policy started.
- - Shows thresholds that cannot be monitored. For example, the Security Gateway cannot monitor RAID sensors on a machine that does not have RAID sensors. Therefore it shows an error for the RAID Sensor Threshold.
- - The name of the threshold with an error.
- - A description of the error.
- - When the error first occurred.
Customizing Results
You can create Custom Views, to change the fields that show in the results.
Editing a Custom View
The changes you make to a view are not automatically saved. You can use this procedure to save a predefined view as a new Custom view.
To save a new view with changes:
- Right-click the results of the view and select .
Note - For some of the views, this option is or .
- Add or remove fields and other options for the view.
- Click .
- For some of the views, select the gateway.
- In the Results toolbar, click the button.
- In the window that opens, enter a name for the new view.
- Click .
Creating a Custom Gateway Status View
To create a custom Gateway status view:
- In the , right-click and select .
The window opens.
- In , select the source of the data.
- In , double-click the data to add to SmartView Monitor.
- Open the tab to remove gateways from the results of this view.
- Click .
- Right-click the new view and select .
- Enter a name for the view.
Creating a Custom Traffic View
To creating a custom traffic view:
- In the , right-click and select .
The window opens.
- Select or .
- If you select , select what you want to see:
- Select the gateway.
- If you often need results for on gateway, select it in .
- If you have a small number of gateways, you can create a custom view for each one.
- If not, select .
- Open the next tabs.
The tabs that show depend on the you selected.
- If you select , the next tab is , where you select the and type of report.
- If you select , the next tabs let you set services or objects to monitor, gateways or specified IP addresses to monitor, update interval, result type, and chart settings.
- Click .
- Right-click the new view and select .
- Enter a name for the view.
Creating a Custom Counters View
To create a custom counters view:
- In the , right-click and select .
The window opens.
- Select or .
- Select the gateway.
- If results for one gateway are frequently necessary, select it in .
- If you have a small number of gateways, you can create a custom view for each one.
- If not, select .
- Open the tab.
- Select a category and the counters to add.
You can add counters from different categories to one view.
- In the Query Type:
- If the Query Type is : Select the and click .
- If the Query Type is
- Open the tab.
- Set the update interval and chart type.
- Click .
- Right-click the new view and select .
- Enter a name for the view.
Creating a Custom Tunnel View
To create a custom tunnel view:
- In the SmartView Monitor client, select > > .
The window shows.
- Select to generate a report about a specified Tunnel, Community or Gateway.
: When you run the view, you will be asked for the specified Tunnel, Community or Gateway on which to base your view.
Important - Do not select if your view is not about one of these three.
- Select or .
shows a more accurate status because the report provides the status for the tunnels in both directions.
- In the column, select the filter to be related to this view
- In the column, click the corresponding Any(*) link.
- Select the related objects to edit the selected filters.
- Click the button.
- Set a limit in the window for the number of lines that show in the report.
- Enter a record limitation.
- Click .
A view shows in the branch of the .
- Enter the name of the new view.
- Click .
Creating a Custom Users View
To create a custom users view:
- In SmartView Monitor, select > > .
The window shows.
- Select to generate a user report about a specified user or Gateway.
: When you decide to run the view, you will be asked for the specified User DN or Gateway on which to base your view.
Important - Do not select if your view is not about one of these two.
- In the column, select the filter to be related with this view.
- In the column, click the corresponding Any(*) link.
- Select the related objects to edit the selected filters.
- Click the button to set a limit (in the window) to the number of lines that show in the report.
- Enter a record limitation.
- Click .
A view shows in the branch of the .
- Enter a name for the new view.
- Click .
Custom View Example
For example purposes, we create a real-time view for .
To create a real-time traffic view:
- Double-click the view to change and select the gateway for which you create the view.
- Select the button on the view toolbar.
The window shows.
- Select .
provides information about currently monitored traffic or system counters.
- Select for information that was logged before.
- Select the topic about which you want to create a traffic view in the drop-down list provided. For example, for purposes select .
Note - The remaining tabs in the window change according to the type of view you create and the selection you made in the drop-down list.
- Select the of this view.
is the gateway for which you monitor traffic.
- Click the tab.
- Select and the for which you want to create a custom view.
- Click the tab.
- Make the necessary selections.
- Click the tab.
- Make the necessary selections.
- Click when you are done with your selections.
The window shows.
- Select the gateway or interface for which you want to create or run this new view.
- Click the button on the toolbar.
- Enter a name for the new view.
- Click .
The new view is saved in the branch.
Exporting a Custom View
You can back up a custom view before you install an upgrade. You can share a custom view with other SmartView Monitor GUI clients and other users.
To export a custom view:
- Right-click the view and select .
- In the window that opens, enter a pathname for the export file.
- Click .
A file with an svm_setting extension is created.
Setting Your Default View
You can set which view to see when SmartView Monitor starts.
In the Tree, right-click the view and select .
Refreshing Views
Results are automatically refreshed every 60 seconds.
To refresh the view earlier, right-click the view name in the and select .
To refresh data about an object in the current view, right-click the object in the results and select .
Monitoring Gateway Status
Gateway Status
Status updates show for Security Gateways and Software Blades. The status of a gateway is the most serious status of its Software Blades. For example, if all the statuses are except for the SmartEvent blade, which has a status, the status is .
Status Icon
|
Description
|

|
The gateway and all its Software Blades work properly.
|

|
At least one Software Blade has a minor issue, but the gateway works.
|

|
At least one Software Blade reported a malfunction, or an enabled Software Blade is not installed.
|

|
SmartView Monitor waits for the Security Management Server to send data from Security Gateways.
|

|
Cannot reach the Security Gateway.
|

|
Cannot make Secure Internal Communication between the Security Management Server and the gateway.
|
Displaying Gateway Data
Gateway Status data shows for each Check Point or OPSEC gateway.
To see data about a gateway, click the gateway in the view. Details about the gateway show in the pane.
System Data
- Unified Package - The version number.
- OS Information - The name, the version name/number, the build number, the service pack, and any additional information about the Operating System in use.
- CPU - The specific CPU parameters (for example, Idle, User, Kernel, and Total) for each CPU.
Note - In the Gateways Results view the Average CPU indicates the average total CPU usage of all existing CPOS. - Memory - The total amount of virtual memory, what percentage of this total is used. The total amount of real memory, what percentage of this total is used, and the amount of real memory available for use.
- Disk - Shows all the disk partitions and their specific details (for example, capacity, used, and free).
Note - In the Gateways Results view the percentage/total of free space in the hard disk on which the Firewall is installed. For example, if there are two hard drives C and D and the Firewall is on C, the Disk Free percentage represents the free space in C and not D.
To view the status of Check Point applications on the local server or another appliance, the cpstat command.
Firewall
- Policy information - The name of the Security Policy installed on the gateway, and the date and time that this policy was installed.
- Packets - The number of packets accepted, dropped and logged by the gateway.
- UFP Cache performance - The hit ratio percentage and the total number of hits handled by the cache, the number of connections inspected by the UFP Server.
- Hash Kernel Memory (the memory status) and System Kernel Memory (the OS memory) - The total amount of memory allocated and used. The total amount of memory blocks used. The number of memory allocations, and those allocation operations which failed. The number of times that the memory allocation freed up, or failed to free up. The NAT Cache, including the total amount of hits and misses.
Virtual Private Networks
The Virtual Private Networks (VPN) is divided into these main statuses:
- Current represents the current number of active output.
- High Watermark represents the maximum number of current output
- Accumulative data represents the total number of the output.
This includes:
- Active Tunnels - All types of active VPN peers to which there is currently an open IPsec tunnel. This is useful to track the activity level of the VPN gateway. High Watermark includes the maximum number of VPN peers for which there was an open IPsec tunnel since the gateway was restarted.
- Remote Access - All types of Remote Access VPN users with which there is currently an open IPsec tunnel. This is useful to track the activity level and load patterns of VPN gateways that serve as a remote access server. High Watermark includes the maximum number of Remote Access VPN users with which there was an open IPsec tunnel since the gateway was restarted.
- Tunnels Establishment Negotiation - The current rate of successful Phase I IKE Negotiations (measured in Negotiations per second). This is useful to track the activity level and load patterns of a VPN gateway that serve as a remote access server. High Watermark includes the highest rate of successful Phase I IKE Negotiations since the Policy was installed (measured in Negotiations per second). Accumulative data includes the total number of successful Phase I IKE negotiations since the Policy was installed.
- Failed - The current failure rate of Phase I IKE Negotiations can be used to troubleshoot (for instance, denial of service) or for a heavy load of VPN remote access connections. High Watermark includes the highest rate of failed Phase I IKE negotiations since the Policy was installed. Accumulative is the total number of failed Phase I IKE negotiations since the Policy was installed.
- Concurrent - The current number of concurrent IKE negotiations. This is useful to track the behavior of VPN connection initiation, especially in large deployments of remote access VPN scenarios. High Watermark includes the maximum number of concurrent IKE negotiations since the Policy was installed.
- Encrypted and Decrypted throughput - The current rate of encrypted or decrypted traffic (measured in Mbps). Encrypted or decrypted throughput is useful (in conjunction with encrypted or decrypted packet rate) to track VPN usage and VPN performance of the gateway. High Watermark includes the maximum rate of encrypted or decrypted traffic (measured in Mbps) since the gateway was restarted. Accumulative includes the total encrypted or decrypted traffic since the gateway was restarted (measured in Mbps).
- Encrypted and Decrypted packets - The current rate of encrypted or decrypted packets (measured in packets per second). Encrypted or decrypted packet rate is useful (in conjunction with encrypted/decrypted throughput) to track VPN usage and VPN performance of the gateway. High Watermark includes the maximum rate of encrypted or decrypted packets since the gateway was restarted, and Accumulative, the total number of encrypted packets since the gateway was restarted.
- Encryption and Decryption errors - The current rate at which errors are encountered by the gateway (measured in errors per second). This is useful to troubleshoot VPN connectivity issues. High Watermark includes the maximum rate at which errors are encountered by the gateway (measured in errors per second) since the gateway was restarted, and the total number of errors encountered by the gateway since the gateway was restarted.
- Hardware - The name of the VPN Accelerator Vendor, and the status of the Accelerator. General errors such as the current rate at which VPN Accelerator general errors are encountered by the gateway (measured in errors per second). The High Watermark includes the maximum rate at which VPN Accelerator general errors are encountered by the gateway (measured in errors per second) since the gateway was restarted. The total number of VPN Accelerator general errors encountered by the gateway since it was restarted.
- IP Compression - Compressed/Decompressed packets statistics and errors.
QoS
- Policy information - The name of the QoS Policy and the date and time that it was installed.
- Number of interfaces - The number of interfaces on the Check Point QoS gateway. Information about the interfaces applies to both inbound and outbound traffic. This includes the maximum and average amount of bytes that pass per second, and the total number of conversations, where conversations are active connections and connections that are anticipated as a result of prior inspection. Examples are data connections in FTP, and the "second half" of UDP connections.
- Packet and Byte information - The number of packets and bytes in Check Point QoS queues.
ClusterXL
- gateway working mode - The gateway working mode as a cluster member, active or not, and its place in the priority sequence. Working modes are: ClusterXL, Load Sharing, Sync only. Running modes: active, standby, ready and down.
- Interfaces - Interfaces recognized by the gateway. The interface data includes the IP Address and status of the specified interface, if the connection that passes through the interface is verified, trusted or shared.
- Problem Notes - Descriptions of the problem notification device such as its status, priority and when the status was last verified.
OPSEC
- The version name or number, and build number of the Check Point OPSEC SDK and OPSEC product. The time it takes (in seconds) since the OPSEC gateway is up and running.
- The OPSEC vendor can add fields to their OPSEC Application gateway details.
Check Point Security Management
- The synchronization status indicates the status of the peer Security Management Servers in relation to that of the selected Security Management Server. View this status in the window, if you are connected to the Active or Standby Security Management Server. The possible synchronization statuses are:
- - Immediately after the Secondary Security Management Server was installed, it did not undergo with the first manual synchronization. This synchronization brings it up to date with the Primary Management.
- - The peer is synchronized correctly and has the same database information and installed Security Policy.
- - The active Security Management Server and its peer have different installed policies and databases. The administrator must do manual synchronization and decide which of the Security Management Servers to overwrite.
- Clients - The number of connected clients on the Security Management Server, the name of the SmartConsole, the administrator that manages the SmartConsole, the name of the SmartConsole host, the name of the locked database, and the type of SmartConsole application.
SmartConsole Server
The number of users that are currently connected.
Log Server
Indicates the number of licensed users that are currently connected, and if the Security Management Server is active or not. The Log Server includes elaborate details about the named connected client, the name of the administrator, managing the selected Log Server, the host of the Log Server, and the name of the database if it is locked. The Log Server indicates the type of application that the Log Server can track.
SmartEvent Correlation Unit and the SmartEvent Server
SmartView Monitor reads statuses from the SmartEvent Correlation Unit and SmartEvent Server.
SmartEvent Correlation Unit status examples:
- Is the SmartEvent Correlation Unit active or inactive
- Is the SmartEvent Correlation Unit connected to the SmartEvent Server
- Is the SmartEvent Correlation Unit connected to the Log Server
- SmartEvent Correlation Unit and Log Server connection status
- Offline job status
- Lack of disk space status
SmartEvent Server status examples:
- Last handle event time
- Is the SmartEvent Server active or inactive
- A list of SmartEvent Correlation Unit the SmartEvent Server is connected to
- How many events arrived in a specified time period
Connect the SmartEvent Correlation Unit to the Log Server or the Log Server to let it read logs. Connect it to the SmartEvent Server to send events to it. If problems occur in the SmartEvent Correlation Unit connection to other components (for example, SIC problems) the problems are reported in the SmartEvent Correlation Unit status.
For the same reasons, the SmartEvent Server contains statuses that provide information about connections to all SmartEvent Correlation Units.
Anti-Virus and URL Filtering
SmartView Monitor can now provide statuses and counters for gateways with Anti-Virus and URL Filtering.
The statuses are divided into these categories:
- Current Status
- Update Status (for example, when was the signature update last checked)
Anti-Virus statuses are associated with signature checks and URL Filtering statuses are associated with URLs and categories.
In addition, SmartView Monitor can now run Anti-Virus and URL Filtering counters.
For example:
- Top five attacks in the last hour
- Top 10 attacks since last reset
- Top 10 http attacks in the last hour
- HTTP attacks general info
Multi-Domain Security Management
SmartView Monitor can be used to monitor Multi-Domain Servers. This information can be viewed in the Gateway Status view. In this view you can see Multi-Domain Security Management counter information (for example, CPU or Overall Status).