

In This Section: |
When an Endpoint Security client connects to the Endpoint Security Management Server, an authentication process identifies the endpoint client and the user currently working on that computer.
The system can function in different modes:
This option is only available for endpoints that are part of Active Directory.
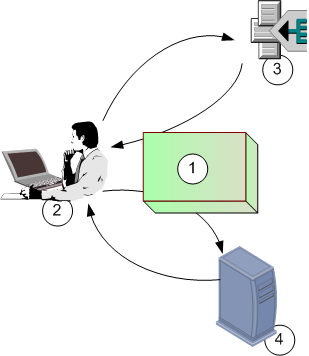
The authentication process:
The default behavior after Security Management Server installation is Unauthenticated mode. It is recommended that you use this mode while you are evaluating Endpoint Security, in a lab environment; and that you change to Strong Authentication just before moving to a production environment. It is not recommended to continue to work in Unauthenticated mode after moving to production in a live environment.
|
Important - If you use Active Directory Authentication, Full Disk Encryption and Media Encryption & Port Protection are only supported on endpoint computers that are part of Active Directory. If you have endpoint computers in your environment that are not part of Active Directory, Full Disk Encryption and Media Encryption & Port Protection will not work on them. |
When you are ready to move to production and to set up Strong Authentication follow this process. Do not set up authentication before you are ready to move to production, and do not leave your production environment without authentication.
To efficiently move to Strong Authentication:
The server communicates to clients that they now work in Authenticated mode.
Endpoint Security Strong Authentication uses the Kerberos network authentication protocol. To configure this service, run ktpass.exe from C:\Windows\System32.
ktpass is included by default.
|
Important - In the procedure below you create a user that is mapped to the ktpass service. After you create this user, do not make changes to it, for example, do not change the password. If you do change the user, the key version increases and you must update the Key version number in the Active Directory SSO Configuration window in the SmartEndpoint. |
To prepare the Active Directory Server for authentication:
ktpass.exe.Syntax: ktpass princ ServiceName/realm@REALM mapuser <userName>@REALM pass <userPass> out <name of outFile>
Example:
Where:
|
Sample output:
WARNING: pType and account type do not match. This might cause problems. Key created. Output keytab to outfile.log: Keytab version: 0x502 keysize 74 tst/nac1.com@NAC1.COM ptype 0 (KRB5_NT_UNKNOWN) vno 7 etype 0x17 (RC4-H |
|||
|
Important - We recommend that you do not use DES-based encryption for the Active Directory Domain Controller server, as it is not secure. If you choose to use DES encryption and your environment has Windows 7 clients, see sk64300. |
||
|
Notes -
|
||
You can configure the Authentication Settings for deployment packages.
|
Important - Use the Unauthenticated mode only for evaluation purposes. Never use this mode for production environments. Configure the authentication settings before moving to production. |
To configure authentication settings:
The Active Directory SSO Configuration window opens.
ktpass, the Active Directory map service command.Field |
Description |
|---|---|
Domain name |
Active Directory domain name. |
Principle Name |
Authentication service name in the format: This value must match what was done in Active Directory > New Object. |
Password |
Enter (and confirm) the password of the Active Directory Domain Admin user you created for Endpoint Security use. |
Ticket encryption method |
Select the encryption method according to the Active Directory output in the |
Key version number |
Enter the version number according to the Active Directory output in the |
When you configure client package profiles, you will have to choose an authentication account. The SSO Configuration details will be included in the client package, allowing the server to authenticate the client.
|
Important - After turning on Strong Authentication, wait one minute before initiating any client operations. It will take time for the clients and the Endpoint Security Management Server to synchronize. During this time, the environment will remain unauthenticated, and some operations will fail. The exact amount of time depends on the synchronization interval. |
By default Active Directory authentication uses the LDAP protocol and simple authentication method. You can change this to LDAPS with or without GSSAPI (Kerberos v5) authentication.
To change the authentication protocol to LDAPS, GSSAPI, or both:
$UEPMDIR/engine/conf/ldap.utils.properties file.use.ssl=false to use.ssl=trueuse.gssapi=false to use.gssapi=trueBoth LDAPS and GSSAPI can be set to true.
For GSSAPI, no additional configuration is necessary.
Additional steps for LDAPS:
To import a certificate to the Endpoint Security Management Servers (Primary and Secondary in High Availability):
certutil -store -v MYThe output of this command is a list of certificates. The certificates are separated by a line like this:
================ Certificate 0 ================, where 0 is the index number of the certificate.
|
certutil -store MY <certificate index> <file name>
For example: certutil -store MY 0 C:\certificates\DCCert.cer
cd $CPDIR/jre_64
./bin/keytool -import -keystore ./lib/security/cacert -file <cert file name> -alias <alias>
For example: ./bin/keytool -import -keystore ./lib/security/cacert -file /certif/DCCert.cer -alias DCSSLCert
uepm_stop, uepm_start.To troubleshoot problems related to Active Directory Authentication, use the Authentication log on the Endpoint Security Management Server or Endpoint Policy Server in $UEPMDIR/logs/Authentication.log.
To see full debugging information in the Authentication.log file on a Gaia server:
export TDERROR_ALL_KERBEROS_SERVER=5.Results in Authentication.log
ERROR: Config file contains no principals. |
The database was cleaned or the process to include authentication in the client package was faulty. To fix:
Permission denied in replay cache code |
Restart the Endpoint Security server.
Clock skew too great |
To ensure that authentication occurs even if the clocks of the client, the Endpoint Security Management Server and the Active Directory server are out of synch, define an acceptable skew. By default, the authentication clock skew is 3600 seconds. You can change the Endpoint Security settings. In $UEPMDIR/engine/conf/global.properties, add this line:authentication.clockSkew.secs=<seconds>, where you replace <seconds> with the clock skew in seconds that you want to allow.
Key version number for principal in key table is incorrect |
Update the Key version number in the Active Directory SSO Configuration window. You might have changed the user that is mapped to the ktpass service.
The Authentication.log file for each Endpoint Security client is on the client computer at %DADIR%/logs.
A normal log is:
[KERBEROS_CLIENT(KerberosLogger_Events)] : Credentials acquired for |
If the Authentication.log file on the client shows:
No authority could be contacted for authentication. |
The Endpoint Agent cannot find a Domain Controller to supply credentials. To fix this:
To authenticate with device credentials, restart the computer.
If the Authentication.log file on the client shows:
The specified target is unknown or unreachable. |
Check the service name. Make sure that there are no typing errors and that the format is correct. If there was an error, correct it in the Check Point Endpoint Security Management.