

The NAT Rule Base has two sections that specify how the IP addresses are translated:
Each section in the NAT Rule Base is divided into cells that define the Source, Destination, and Service for the traffic.
There are two types of NAT rules for network objects:
When you create manual NAT rules, it can be necessary to create the translated NAT objects for the rule.
You can enable automatic NAT rules for these SmartConsole objects:
SmartConsole creates two automatic rules for Static NAT, to translate the source and the destination of the packets.
For Hide NAT, one rule is created to translate the source of the packets.
For network and address range objects, SmartConsole creates a different rule to NOT translate intranet traffic. IP addresses for computers on the same object are not translated.
This table summarizes the NAT automatic rules:
Type of Traffic |
Static NAT |
Hide NAT |
|---|---|---|
Internal to external |
Rule translates source IP address |
Rule translates source IP address |
External to internal |
Rule translates destination IP address |
N/A (External connections are not allowed) |
Intranet (for network and address range objects) |
Rule does not translate IP address |
Rule does not translate IP address |
The Firewall enforces the NAT Rule Base in a sequential manner. Automatic and manual rules are enforced differently. Automatic rules can use bidirectional NAT to let two rules be enforced for a connection.
SmartConsole organizes the automatic NAT rules in this order:
Here are some sample automatic rules.
The Firewall does not apply rules 2 and 3 to traffic that matches rule 1.
The Firewall does not apply rule 2 to traffic that matches rule 1.
You can enable and configure NAT for SmartConsole objects.
Configuring Static NAT
When you enable Static NAT, each object is translated to a different IP address. SmartConsole can automatically create the NAT rules, or you can create them manually.
Configuring Hide NAT
Hide NAT uses different port numbers to identify the internal IP addresses. When you enable Hide NAT mode, the Firewall can translates the IP address to:
Note - You cannot use Hide NAT for these configurations:
SmartConsole can automatically create and configure the NAT rules for a network. Enable automatic NAT for every object, for which you are translating the IP address. Then configure the Access Control Rule Base to allow traffic to the applicable objects.
To enable automatic NAT:
The General Properties window of the gateway opens.
After you enable and configure NAT on all applicable gateways, install the policy.
For large and complex networks, it can be impractical to configure the Hide NAT settings for all the internal IP addresses. An easy alternative is to enable a Firewall to automatically Hide NAT for all traffic with external networks. The Firewall translates all traffic that goes through an external interface to the valid IP address of that interface.
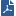
In this sample configuration, computers in internal networks open connections to external servers on the Internet. The source IP addresses of internal clients are translated to the IP address of an external interface.
Item |
Description |
|---|---|
1 |
Internal networks |
2 |
Security Gateway - Firewall is configured with automatic Hide NAT. |
2A and 2B |
Two external interfaces 192.0.2.1 and 192.0.2.100. |
1 -->3 |
External computers and servers on the Internet |
Source IP addresses are translated to the applicable external interface IP address: 192.0.2.1 or 192.0.2.100.
Note - If a connection matches a regular NAT rule and a NAT-for-internal-networks rule, the regular NAT rule takes precedence.
The General Properties window of the gateway opens.
For some deployments, it is necessary to manually define the NAT rules. Create SmartConsole objects that use the valid (NATed) IP addresses. Create NAT rules to translate the original IP addresses of the objects to valid IP addresses. Then configure the Firewall Rule Base to allow traffic to the applicable translated objects with these valid IP addresses.
Note - For manual NAT rules, it is necessary to configure Proxy ARP entries to associate the translated IP address.
These are some situations that must use manual NAT rules:
This procedure explains how to configure manual Static NAT for a web server. You can also configure manual Hide NAT for SmartConsole objects.
To enable manual Static NAT, follow this workflow:
To create a clone network object:
The General Properties window of the new object opens.
To add a NAT rule to the Rule Base:
To add Access Control rules:
These objects are the cloned objects that are called <name>_valid_address.
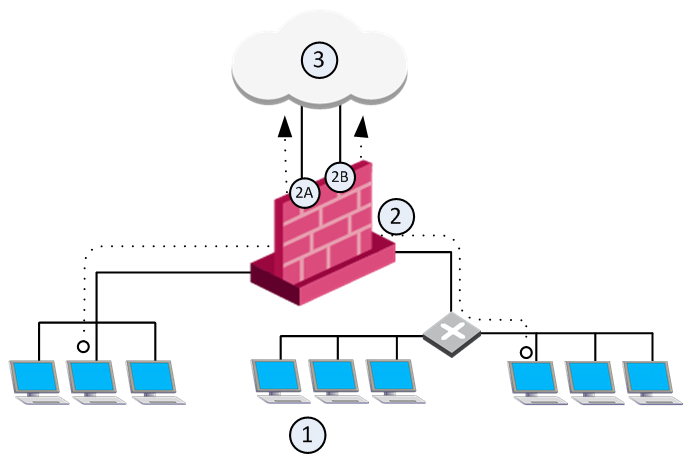
The goal for this sample deployment is to configure:
Item |
Description |
|---|---|
1 |
Internal computers (Alaska_LAN 2001:db8::/64) |
2 |
Web server (Alaska.Web 2001:db8:0:10::5 translated to 2001:db8:0:a::5) |
3 |
Mail server (Alaska.Mail 2001:db8:0:10::6 translated to 2001:db8:0:a::6) |
4 |
Security Gateway (External interface 2001:db8:0:a::1) |
5 |
External computers and servers in the Internet |
To configure NAT for the network:
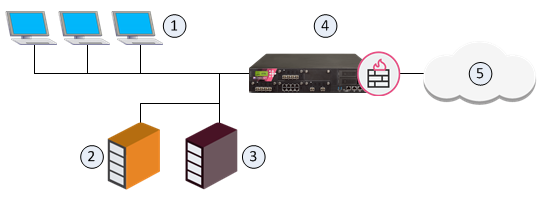
The goal for this sample configuration is to let external computers access a web and mail server in a DMZ network from one IP address. Configure Hide NAT for the DMZ network object and create manual NAT rules for the servers.
Item |
Description |
|---|---|
1 |
External computers and servers in the Internet |
2 |
Security Gateway (Alaska_GW external interface 2001:db8:0:c::1) |
3 |
DMZ network (Alaska_DMZ 2001:db8:a::/128) |
4 |
Web server (Alaska_DMZ_Web 2001:db8:a::35:5 translated to 2001:db8:0:c::1) |
5 |
Mail server (Alaska_DMZ_Mail 2001:db8:a::35:6 translated to 2001:db8:0:c::1) |
To configure NAT for the DMZ servers:
NAT Rule Base for Manual Rules for Port Translation Sample Deployment
No. |
Original Source |
Original Destination |
Original Services |
Translated Source |
Translated Destination |
Translated Services |
Install On |
Comments |
1 |
Alaska_DMZ |
Alaska_DMZ |
Any |
Original |
Original |
Original |
All |
Automatic rule |
2 |
Alaska_DMZ |
Any |
Any |
H Alaska_DMZ (Hiding Address) |
Original |
Original |
All |
Automatic rule |
3 |
Any |
Alaska_GW |
http |
Original |
S Alaska_DMZ_Web |
Original |
Policy Targets |
|
4 |
Any |
Alaska_GW |
smtp |
Original |
S Alaska_DMZ_Mail |
Original |
Policy Targets |
|
R80.20 supports NAT64 rules.
Background:
NAT64 translation (RFC 6146) lets IPv6-only client communicate with IPv4-only server using unicast UDP, TCP, or ICMP.
IPv6-only client is one of these:
IPv4-only server is one of these:
The translation of IP addresses is done by translating the packet headers according to the IP/ICMP Translation Algorithm defined in RFC 6145. The IPv4 addresses of IPv4 hosts are translated to and from IPv6 addresses using the algorithm defined in RFC 6052, and an IPv6 prefix assigned to the stateful NAT64 for this specific purpose.
Note - For information about DNS64, see RFC 6147.
Properties of Stateful NAT64:
NAT64 use case scenarios:
Common use case for Content Providers. DNS64 is not needed.
Common use case for Carriers, ISPs, Enterprises. DNS64 is required.
Common use case for Enterprises. DNS64 is required.
R80.20 supports these standards for NAT64:
R80.20 does not support these features for NAT64:
Workflow for configuring NAT64 rules:
To prepare a Security Gateway for NAT64:
Note - In cluster, do these steps on each cluster member.
Step |
Instructions |
|---|---|
1 |
Make sure that an IPv6 address is assigned to the interface that connects to the destination IPv4 network, and the IPv6 network prefix length is equal to, or less than 96. Note - This can be any valid IPv6 address with the IPv6 network prefix length equal to, or less than 96.
If such IPv6 address is not assigned yet, assign it now. For details, see R80.20 Gaia Administration Guide - Chapter Network Management - Section Network Interfaces - Section Physical Interfaces. |
2 |
Make sure that the IPv6 routing is configured to send the traffic that is destined to the NATed IPv6 addresses (defined in the Original Destination column in the NAT64 rule) through the interface that connects to the destination IPv4 network.
If such route does not already exist, add it in Gaia Clish. For details, see R80.20 Gaia Administration Guide. Run these commands in Gaia Clish:
|
3 |
Make sure that the number of IPv6 CoreXL FW instances is equal to the number of IPv4 CoreXL FW instances.
Example output: [Expert@GW:0]# fw6 ctl multik stat ID | Active | CPU | Connections | Peak ---------------------------------------------- 0 | Yes | 3 | 0 | 0 1 | Yes | 2 | 0 | 4 2 | Yes | 1 | 0 | 2 [Expert@GW:0]# [Expert@GW:0]# fw ctl multik stat ID | Active | CPU | Connections | Peak ---------------------------------------------- 0 | Yes | 3 | 10 | 14 1 | Yes | 2 | 6 | 15 2 | Yes | 1 | 7 | 15 [Expert@GW:0]# |
Define NAT64 rules as Manual NAT rules in the Access Policy. Make sure that you add access rules that allow this NAT traffic.
Do these steps in SmartConsole to define NAT64 rules:
This object represents the source IPv6 addresses, which you translate to source IPv4 addresses.
This object represents the translated destination IPv6 address, to which the IPv6 sources connect.
This object represents the translated source IPv4 addresses, to which you translate the original source IPv6 addresses.
To define a source IPv6 Network object that represents the source IPv6 address, which you translate to source IPv4 addresses:
Do not enter anything.
Do not configure anything.
To define a translated destination IPv6 Network object with IPv4-embedded IPv6 address that represents the IPv6 addresses, to which the IPv6 sources connect:
Do not enter anything.
Such IPv6 address contains (from left to right) 80 "zero" bits, followed by 16 "one" bits, and then the 32 bits of the IPv4 address - 0:0:0:0:0:FFFF:X.Y.Z.W, where X.Y.Z.W are the four octets of the destination IPv4 address.
For example, for IPv4 network 192.168.3.0, the IPv4-embedded IPv6 address is 0:0:0:0:0:FFFF:192.168.3.0, or 0:0:0:0:0:FFFF:C0A8:0300. For more information, see RFC 6052.
These IPv4-embedded IPv6 addresses are published by an external DNS64 server.
Note - You can define IPv4-embedded IPv6 addresses only for these object types: Address Range, Network, and Host.
Do not configure anything.
To define a translated destination IPv6 Host object with static IPv6 address that represents the IPv6 address, to which the IPv6 sources connect:
Do not enter anything.
In the Network address field, enter the destination static IPv6 address, to which the IPv6 sources connect.
Do not configure anything.
To define a translated source IPv4 Address Range object that represents the IPv4 addresses, to which you translate the source IPv6 addresses:
Notes:
Do not enter anything.
Do not configure anything.
To create a Manual NAT64 rule:
Important - Some combinations of object types are not supported in the Original Source and Original Destination columns. See the summary table with the supported NAT rules at the bottom of this section.
In this rule column, NAT64 rules support only these types of objects:
*AnyIn this rule column, NAT64 rules support only these types of objects:
In this rule column, NAT64 rules support only these types of objects:
In this rule column, NAT64 rule supports only these types of objects:
To summarize, you must configure only these Manual NAT64 rules (rule numbers are for convenience only):
# |
Original |
Original |
Original |
Translated |
Translated |
Translated |
|---|---|---|---|---|---|---|
1 |
|
IPv6 |
|
IPv4 |
IPv4 |
|
2 |
|
IPv6 |
|
IPv4 |
|
|
3 |
|
IPv6 |
|
IPv4 |
|
|
4 |
IPv6 |
IPv6 |
|
IPv4 |
IPv4 |
|
5 |
IPv6 |
IPv6 |
|
IPv4 |
|
|
6 |
IPv6 |
IPv6 |
|
IPv4 |
|
|
7 |
IPv6 |
IPv6 |
|
IPv4 |
IPv4 |
|
8 |
IPv6 |
IPv6 |
|
IPv4 |
|
|
9 |
IPv6 |
IPv6 |
|
IPv4 |
|
|
10 |
IPv6 |
IPv6 |
|
IPv4 |
IPv4 |
|
11 |
IPv6 |
IPv6 |
|
IPv4 |
|
|
12 |
IPv6 |
IPv6 |
|
IPv4 |
|
|
You can configure the additional settings that control the NAT64 translation mechanism. These settings are compliant with RFC 6145.
Note - We recommend that you change the default settings only if you are familiar with the technology.
nat64_add_UDP_checksumnat64_avoid_PMTUD_blackholenat64_copy_type_of_servicenat64_error_message_on_dropped_packetsField Name |
Description |
|---|---|
|
This setting controls whether the translator should calculate and add a valid UDP checksum value to a packet, if the packet checksum value is zero. This is important because, by default, an IPv4 UDP packet with a checksum value of zero is dropped on the IPv6 side. Default: false |
|
This setting controls whether to allow packet fragmentation on the IPv4 (destination) side during PMTU discovery. Enable this setting if some equipment combinations cause PMTU discovery to fail. Default: false |
|
This setting controls whether to copy the traffic Class Field to the Type Of Service field, and set the Type Of Service field in the translated packet to zero. Default: true |
|
This setting controls whether to generate an audit log after a connection is closed. For each closed connection, the log shows:
Default: true |
In the Security Gateway log for NAT64 connection, the source and destination IPv6 addresses show in their original IPv6 format. To identify a NAT64 entry, look in the More section of the Log Details window.
Field in Log |
Description |
|---|---|
Xlate (NAT) Source IP |
Shows the translated source IPv4 address, to which the Security Gateway translated the original source IPv6 address |
Xlate (NAT ) Destination IP |
Shows the translated destination IPv4 address, to which the Security Gateway translated the original destination IPv6 address |
More |
Identifies the entry as NAT64 traffic ( |
Example topology:
[IPv6 Client] --- (interface) [Security Gateway] (internal) --- [IPv4 Server]
Where:
Item |
Description |
|---|---|
IPv6 Client |
IPv6 real address is 1111:1111::0100/96 |
Security Gateway |
IPv6 address is 1111:1111::1/96 |
Security Gateway |
IPv4 address is 10.0.0.1/24 IPv6 address is 3333:4444::1/96 |
IPv4 Server |
IPv4 real address is 10.0.0.100/24 IPv6 NATed address is 1111:2222::0A00:0064/96 |
IPv6 NATed network |
IPv6 address of the network on the external Security Gateway side is 1111:2222::/96 These IPv6 addresses are used to translate the IPv4 address of the IPv4 Server to the IPv6 address |
IPv4 NATed network |
IPv4 address of the network on the internal Security Gateway side is 1.1.1.0/24 These IPv4 addresses are used to translate the IPv6 address of the IPv6 Client to the IPv4 address |
Traffic flow:
From the IPv6 Client's IPv6 real address 1111:1111::0100 to the IPv4 Server's NATed IPv6 address 1111:2222::0A00:0064
Where:
The "1111:2222::" part is the NATed IPv6 subnet
The "0A00:0064" part is 10.0.0.100
Where:
The "0064:FF9B::" part is a well-known prefix reserved for NAT64 (as defined by the RFC)
The "0101:01XX" part is 1.1.1.X
Where:
The "64:FF9B::" part is a well-known prefix reserved for NAT64 (as defined by the RFC)
The "0101:01XX" part is 1.1.1.X
To summarize:
Field in packet |
Original IPv6 packet |
NATed IPv4 packet |
|---|---|---|
Source IP |
1111:1111::0100 / 96 |
1.1.1.X / 24 |
Destination IP |
1111:2222::0A00:0064 / 96 |
10.0.0.100 / 24 |
Field in packet |
Original IPv4 packet |
NATed IPv6 packet |
|---|---|---|
Source IP |
10.0.0.100 / 24 |
1111:2222::0A00:0064 / 96 |
Destination IP |
1.1.1.X / 24 |
1111:1111::0100 / 96 |
NAT46 rules are only supported on R80.20 gateways.
Background:
NAT46 translation lets an IPv4 network communicate with an IPv6 network without maintaining any session information on Security Gateway.
Properties of Stateless NAT46:
NAT46 use case scenarios:
Common use case for Content Providers.
Common use case for Enterprises.
R80.20 does not support these features not for NAT46:
Workflow for configuring NAT46 rules:
To prepare a Security Gateway for NAT46:
Note - In cluster, do these steps on each cluster member.
Step |
Instructions |
|---|---|
1 |
Make sure that an IPv6 address is assigned to the interface that connects to the destination IPv6 network, and the IPv6 network prefix length is equal to 96. Note - This can be any valid IPv6 address with the IPv6 network prefix length equal to 96.
If such IPv6 address is not assigned yet, assign it now. For details, see R80.20 Gaia Administration Guide - Chapter Network Management - Section Network Interfaces - Section Physical Interfaces. |
2 |
Make sure that the routing is configured to send the traffic that is destined to the NATed IPv4 addresses (defined in the Translated Destination column in the NAT46 rule) through the interface that connects to the destination IPv6 network.
If such route does not already exist, add it in Gaia Clish. For details, see R80.20 Gaia Administration Guide. Run these commands in Gaia Clish:
|
3 |
Make sure that the number of IPv6 CoreXL FW instances is equal to the number of IPv4 CoreXL FW instances.
Example output: [Expert@GW:0]# fw6 ctl multik stat ID | Active | CPU | Connections | Peak ---------------------------------------------- 0 | Yes | 3 | 0 | 0 1 | Yes | 2 | 0 | 4 2 | Yes | 1 | 0 | 2 [Expert@GW:0]# [Expert@GW:0]# fw ctl multik stat ID | Active | CPU | Connections | Peak ---------------------------------------------- 0 | Yes | 3 | 10 | 14 1 | Yes | 2 | 6 | 15 2 | Yes | 1 | 7 | 15 [Expert@GW:0]# |
Define NAT46 rules as Manual NAT rules in the Access Policy. Make sure that you add access rules that allow this NAT traffic.
Do these steps in SmartConsole to define NAT46 rules:
This object represents the destination IPv4 address, to which the IPv4 sources connect.
This object represents the translated source IPv6 addresses, to which you translate the source IPv4 addresses.
This object represents the translated destination IPv6 address, to which the translated IPv4 sources connect.
To define a source IPv4 Host object:
Do not enter anything
Do not configure anything.
To define a source IPv4 Network object:
Do not enter anything.
Do not configure anything.
To define a source IPv4 Address Range object:
Do not enter anything.
Do not configure anything.
To define a translated destination IPv4 Host object:
Do not enter anything.
Do not configure anything.
To define a translated source IPv6 Network object with an IPv6 address defined with the 96-bit prefix:
Do not enter anything.
Do not configure anything.
To define a translated destination IPv6 Host object:
Do not enter anything.
In the Network address field, enter the destination static IPv6 address.
Do not configure anything.
To create a Manual NAT46 rule:
Original |
Original |
Original |
Translated |
Translated |
Translated |
|---|---|---|---|---|---|
*Any or Source or Source or Source |
IPv4 |
*Any |
IPv6 |
IPv6 |
= Original |
Do these steps:
In this rule column, NAT46 rules support only these types of objects:
*AnyIn this rule column, NAT46 rules support only IPv4 Host objects.
In this rule column, NAT64 rules support only IPv6 Network objects with an IPv6 address defined with the 96-bit prefix.
The 46 icon shows in the Translated Source column.
In this rule column, NAT46 rule supports only an IPv6 Host objects.
To summarize, you must configure only these NAT46 rules (rule numbers are for convenience only):
# |
Original |
Original |
Original Services |
Translated |
Translated |
Translated Services |
|---|---|---|---|---|---|---|
1 |
|
IPv4 |
|
IPv6 |
IPv6 |
|
2 |
IPv4 |
IPv4 |
|
IPv6 |
IPv6 |
|
3 |
IPv4 |
IPv4 |
|
IPv6 |
IPv6 |
|
4 |
IPv4 |
IPv4 |
|
IPv6 |
IPv6 |
|
In the Security Gateway log for NAT64 connection, the source and destination IPv6 addresses show in their original IPv6 format. To identify a NAT46 entry, look in the More section of the Log Details window.
Field in Log |
Description |
|---|---|
Xlate (NAT) Source IP |
Shows the translated source IPv6 address, to which the Security Gateway translated the original source IPv4 address |
Xlate (NAT ) Destination IP |
Shows the translated destination IPv6 address, to which the Security Gateway translated the original destination IPv4 address |
More |
Identifies the entry as NAT46 traffic ( |
Example topology:
[IPv4 Client] --- (internal) [Security Gateway] (external) --- [IPv6 Server]
Where:
Item |
Description |
|---|---|
IPv4 Client |
IPv4 real address is 192.168.2.55 IPv6 NATed address is 2001:DB8:90::192.168.2.55/96 |
Security Gateway internal interface |
IPv4 address is 192.168.2.1/24 |
Security Gateway external interface |
IPv6 address is 2001:DB8:5001::1/96 |
IPv6 Server |
IPv6 real address is 2001:DB8:5001::30/96 IPv4 NATed address is 1.1.1.66/24 |
IPv6 NATed network |
IPv6 address of the network on the external Security Gateway side is 2001:DB8:90::/96 These IPv6 addresses are used to translate the IPv4 address of the IPv4 Client to IPv6 address |
IPv4 NATed network |
IPv4 address of the network on the internal Security Gateway side is 1.1.1.0/24 These IPv4 addresses are used to translate the IPv6 address of the IPv6 Server to IPv4 address |
Traffic flow:
From IPv4 address 192.168.2.55 to IPv4 address 1.1.1.66
To summarize:
Field in packet |
Original IPv4 packet |
NATed IPv6 packet |
|---|---|---|
Source IP |
192.168.2.55 / 24 |
2001:DB8:90::192.168.2.55 / 96 |
Destination IP |
1.1.1.66 / 24 |
2001:DB8:5001::30 / 96 |
Field in packet |
Original IPv6 packet |
NATed IPv4 packet |
|---|---|---|
Source IP |
2001:DB8:5001::30 / 96 |
192.168.2.55 / 24 |
Destination IP |
2001:DB8:90::192.168.2.55 / 96 |
1.1.1.66 / 24 |